An intermittent outage at Cloudflare on Tuesday briefly knocked many of the Internet’s top destinations offline. Some affected Cloudflare customers were able to pivot away from the platform temporarily so that visitors could still access their websites. But security experts say doing so may have also triggered an impromptu network penetration test for organizations that … Read More “The Cloudflare Outage May Be a Security Roadmap – Krebs on Security” »
WrtHug Exploits Six ASUS WRT Flaws to Hijack Tens of Thousands of EoL Routers Worldwide – The Hacker News
A newly discovered campaign has compromised tens of thousands of outdated or end-of-life (EoL) ASUS routers worldwide, predominantly in Taiwan, the U.S., and Russia, to rope them into a massive network. The router hijacking activity has been codenamed Operation WrtHug by SecurityScorecard’s STRIKE team. Southeast Asia and European countries are some of the other regions … Read More “WrtHug Exploits Six ASUS WRT Flaws to Hijack Tens of Thousands of EoL Routers Worldwide – The Hacker News” »
SecurityMetrics Wins “Data Leak Detection Solution of the Year” in 2025 CyberSecurity Breakthrough Awards Program – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Orem, United States, November 18th, 2025, CyberNewsWire SecurityMetrics, a leading innovator in compliance and cybersecurity, today announced that… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Application Containment: How to Use Ringfencing to Prevent the Weaponization of Trusted Software – The Hacker News

The challenge facing security leaders is monumental: Securing environments where failure is not an option. Reliance on traditional security postures, such as Endpoint Detection and Response (EDR) to chase threats after they have already entered the network, is fundamentally risky and contributes significantly to the half-trillion-dollar annual cost of cybercrime. Zero Trust fundamentally shifts – … Read More “Application Containment: How to Use Ringfencing to Prevent the Weaponization of Trusted Software – The Hacker News” »
Cline Bot AI Agent Vulnerable to Data Theft and Code Execution – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Mindgard reveals 4 critical security flaws in the popular Cline Bot AI coding agent. Learn how prompt injection can hijack the tool for API key theft and remote code execution. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
The cyber espionage group uses a previously undocumented network implant to drop two downloaders, LittleDaemon and DaemonLogistics, which deliver a backdoor – Read More –
How to Achieve Ultra-Fast Response Time in Your SOC – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

ANY.RUN shows how early clarity, automation and shared data help SOC teams cut delays and speed up response during heavy alert loads. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
ServiceNow AI Agents Can Be Tricked Into Acting Against Each Other via Second-Order Prompts – The Hacker News

Malicious actors can exploit default configurations in ServiceNow’s Now Assist generative artificial intelligence (AI) platform and leverage its agentic capabilities to conduct prompt injection attacks. The second-order prompt injection, according to AppOmni, makes use of Now Assist’s agent-to-agent discovery to execute unauthorized actions, enabling attackers to copy and exfiltrate sensitive – Read More – The … Read More “ServiceNow AI Agents Can Be Tricked Into Acting Against Each Other via Second-Order Prompts – The Hacker News” »
EdgeStepper Implant Reroutes DNS Queries to Deploy Malware via Hijacked Software Updates – The Hacker News
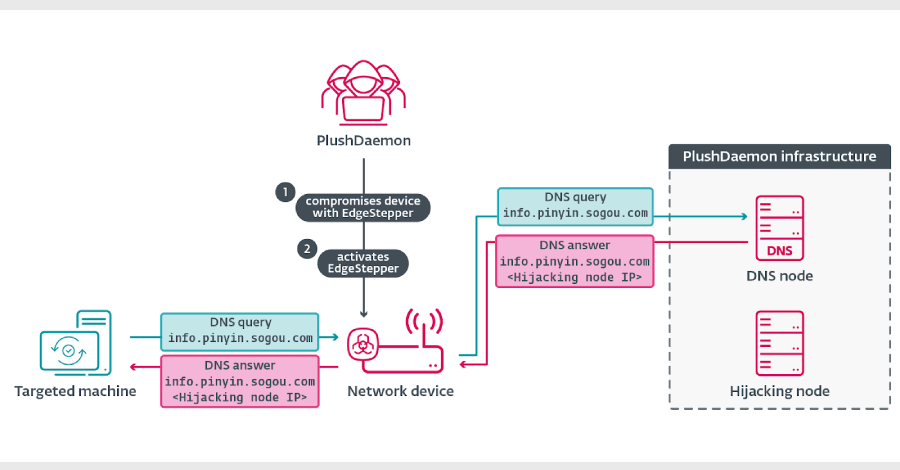
The threat actor known as PlushDaemon has been observed using a previously undocumented Go-based network backdoor codenamed EdgeStepper to facilitate adversary-in-the-middle (AitM) attacks. EdgeStepper “redirects all DNS queries to an external, malicious hijacking node, effectively rerouting the traffic from legitimate infrastructure used for software updates to attacker-controlled infrastructure – Read More – The Hacker News
SecurityScorecard has revealed a new Chinese campaign targeting thousands of ASUS routers globally – Read More –
Beazley Security data finds the top cause of initial access for ransomware in Q3 was compromised VPN credentials – Read More –
CredShields Joins Forces with Checkmarx to Bring Smart Contract Security to Enterprise AppSec Programs – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Singapore, Singapore, 19th November 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
In 2025, the conversation around data breaches has shifted from “if” to “how often and how bad.” Boards and… The post The True Cost of Data Breaches in 2025 appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
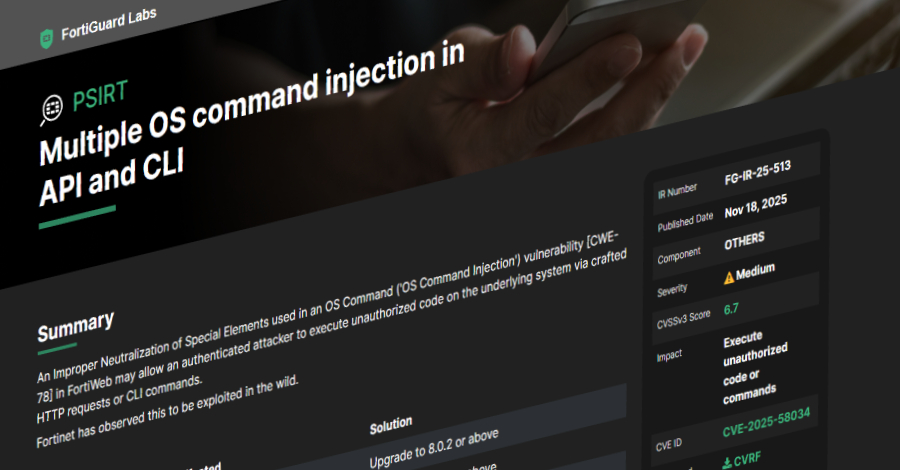
Fortinet has warned of a new security flaw in FortiWeb that it said has been exploited in the wild. The medium-severity vulnerability, tracked as CVE-2025-58034, carries a CVSS score of 6.7 out of a maximum of 10.0. “An Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) vulnerability [CWE-78] in FortiWeb … Read More “Fortinet Warns of New FortiWeb CVE-2025-58034 Vulnerability Exploited in the Wild – The Hacker News” »
Multiple vulnerabilities have been discovered in Fortinet products, the most severe of which could allow for arbitrary code execution. FortiClient for Windows is a unified endpoint security solution that provides a range of security features, including a VPN client for secure remote access to corporate networks, antivirus protection, web filtering, and vulnerability assessment. FortiExtender is a device … Read More “Multiple Vulnerabilities in Fortinet Products Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
Malicious hackers have been attacking the development environment of an open-source AI framework, twisting its functions into a global cryptojacking bot for profit, according to researchers at cybersecurity firm Oligo. The flaw exists in an Application Programming Interface for Ray, an open-source framework for automating, scaling and optimizing compute resources that Oligo researchers called “Kubernetes … Read More “Hackers turn open-source AI framework into global cryptojacking operation – CyberScoop” »
Information sharing law’s expiration could squander government vulnerability hunting efforts, senator says – CyberScoop
Letting a cyber threat data sharing law expire could waste government efforts to find vulnerabilities, since companies would no longer be able to discuss these issues without fear of legal repercussions, a top senator said Tuesday. Sen. Mike Rounds, R-S.D., made his remarks less than a week after the hotly contested legislation to end a … Read More “Information sharing law’s expiration could squander government vulnerability hunting efforts, senator says – CyberScoop” »
Iranian Hackers Use DEEPROOT and TWOSTROKE Malware in Aerospace and Defense Attacks – The Hacker News

Suspected espionage-driven threat actors from Iran have been observed deploying backdoors like TWOSTROKE and DEEPROOT as part of continued attacks aimed at aerospace, aviation, and defense industries in the Middle East. The activity has been attributed by Google-owned Mandiant to a threat cluster tracked as UNC1549 (aka Nimbus Manticore or Subtle Snail), which was first … Read More “Iranian Hackers Use DEEPROOT and TWOSTROKE Malware in Aerospace and Defense Attacks – The Hacker News” »
Cloudflare Outage Jolts the Internet – What Happened, and Who Was Hit – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Cloudflare outage causes slow sites, login trouble and dashboard errors as users report problems even after the company says service is restored. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Sneaky 2FA Phishing Kit Adds BitB Pop-ups Designed to Mimic the Browser Address Bar – The Hacker News

The malware authors associated with a Phishing-as-a-Service (PhaaS) kit known as Sneaky 2FA have incorporated Browser-in-the-Browser (BitB) functionality into their arsenal, underscoring the continued evolution of such offerings and further making it easier for less-skilled threat actors to mount attacks at scale. Push Security, in a report shared with The Hacker News, said it observed … Read More “Sneaky 2FA Phishing Kit Adds BitB Pop-ups Designed to Mimic the Browser Address Bar – The Hacker News” »
The malware authors associated with a Phishing-as-a-Service (PhaaS) kit known as Sneaky 2FA have incorporated Browser-in-the-Browser (BitB) functionality into their arsenal, underscoring the continued evolution of such offerings and further making it easier for less-skilled threat actors to mount attacks at scale. Push Security, in a report shared with The Hacker News, said it observed … Read More “Sneaky 2FA Phishing Kit Adds BitB Pop-ups Designed to Mimic the Browser Address Bar – The Hacker News” »
A forthcoming Trump administration cyber strategy will have six pillars, two of which will be deterring malicious hackers and partnering with industry, executive branch officials said Tuesday. Top figures in the administration have been slowly unveiling details of the strategy, with a draft being currently reviewed by agencies. It reportedly is taking shape earlier in … Read More “Completed draft of cyber strategy emphasizes imposing costs, industry partnership – CyberScoop” »
In episode 77 of The AI Fix, a language model trained on genomes that creates a super-virus, Graham wonders whether AI should be allowed to decide if we live or die, and a woman marries ChatGPT (and calls it “Klaus”). Also in this episode: In Russia a robot staggers, falls over, and breaks; MIT quietly … Read More “The AI Fix #77: Genome LLM makes a super-virus, and should AI decide if you live? – Graham Cluley” »
Meta Expands WhatsApp Security Research with New Proxy Tool and $4M in Bounties This Year – The Hacker News

Meta on Tuesday said it has made available a tool called WhatsApp Research Proxy to some of its long-time bug bounty researchers to help improve the program and more effectively research the messaging platform’s network protocol. The idea is to make it easier to delve into WhatsApp-specific technologies as the application continues to be a … Read More “Meta Expands WhatsApp Security Research with New Proxy Tool and $4M in Bounties This Year – The Hacker News” »
One US cybersecurity leader described the short-term extension of the Cybersecurity Information Sharing Act as a “temporary patch” and called for a long-term solution – Read More –
A new malware campaign has been observed built on seven npm packages and using cloaking techniques and fake CAPTCHAs, operated by threat actor dino_reborn – Read More –
Austin, TX/USA, 18th November 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Researchers Detail Tuoni C2’s Role in an Attempted 2025 Real-Estate Cyber Intrusion – The Hacker News
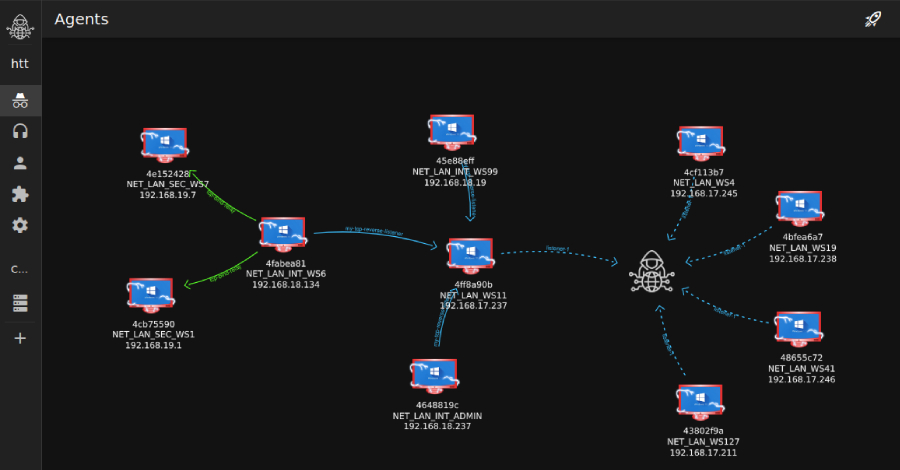
Cybersecurity researchers have disclosed details of a cyber attack targeting a major U.S.-based real-estate company that involved the use of a nascent command-and-control (C2) and red teaming framework known as Tuoni. “The campaign leveraged the emerging Tuoni C2 framework, a relatively new, command-and-control (C2) tool (with a free license) that delivers stealthy, in-memory payloads,” – … Read More “Researchers Detail Tuoni C2’s Role in an Attempted 2025 Real-Estate Cyber Intrusion – The Hacker News” »
A major US real estate firm has been targeted with an advanced intrusion attempt using Tuoni C2, combining social engineering, steganography and in-memory attacks – Read More –
DoorDash has confirmed an October 2025 data breach that exposed customer names, phone numbers, addresses and email details – Read More –
Cybersecurity researchers have discovered a set of seven npm packages published by a single threat actor that leverages a cloaking service called Adspect to differentiate between real victims and security researchers to ultimately redirect them to sketchy crypto-themed sites. The malicious npm packages, published by a threat actor named “dino_reborn” between September and November 2025, … Read More “Seven npm Packages Use Adspect Cloaking to Trick Victims Into Crypto Scam Pages – The Hacker News” »
Beyond IAM Silos: Why the Identity Security Fabric is Essential for Securing AI and Non-Human Identities – The Hacker News

Identity security fabric (ISF) is a unified architectural framework that brings together disparate identity capabilities. Through ISF, identity governance and administration (IGA), access management (AM), privileged access management (PAM), and identity threat detection and response (ITDR) are all integrated into a single, cohesive control plane. Building on Gartner’s definition of “identity – Read More – … Read More “Beyond IAM Silos: Why the Identity Security Fabric is Essential for Securing AI and Non-Human Identities – The Hacker News” »
You’ve probably already moved some of your business to the cloud—or you’re planning to. That’s a smart move. It helps you work faster, serve your customers better, and stay ahead. But as your cloud setup grows, it gets harder to control who can access what. Even one small mistake—like the wrong person getting access—can lead … Read More “Learn How Leading Companies Secure Cloud Workloads and Infrastructure at Scale – The Hacker News” »
A miracle: A company says sorry after a cyber attack – and donates the ransom to cybersecurity research – Graham Cluley
One of the sad truths about this world of seemingly endless hacks and data breaches is that companies just won’t apologise. Even when customers, partners, and employees are left wondering when their data will be published by malicious hackers on the dark web, breached organisations will seemingly do everything they can to avoid saying what … Read More “A miracle: A company says sorry after a cyber attack – and donates the ransom to cybersecurity research – Graham Cluley” »
CISOs are facing unprecedented challenges to their mental health due to today’s rapidly evolving threat landscape. They are often held accountable if a breach or disruption occurs, and the average tenure for a CISO tends to decrease significantly after such incidents. This constant pressure makes it difficult for them to find peace, let alone get … Read More “The realities of CISO burnout and exhaustion – CyberScoop” »
Entrust says AI is helping fraudsters open new accounts and bypass biometric checks – Read More –
Socura finds 460,000 compromised credentials belonging to FTSE 100 company employees – Read More –
Microsoft Azure Blocks 15.72 Tbps Aisuru Botnet DDoS Attack – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Microsoft Azure halted a record 15.72 Tbps DDoS attack from the Aisuru botnet exposing risks created by exposed home devices exploited in large-scale cyber attacks. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Microsoft on Monday disclosed that it automatically detected and neutralized a distributed denial-of-service (DDoS) attack targeting a single endpoint in Australia that measured 5.72 terabits per second (Tbps) and nearly 3.64 billion packets per second (pps). The tech giant said it was the largest DDoS attack ever observed in the cloud, and that it originated … Read More “Microsoft Mitigates Record 5.72 Tbps DDoS Attack Driven by AISURU Botnet – The Hacker News” »
Google Issues Security Fix for Actively Exploited Chrome V8 Zero-Day Vulnerability – The Hacker News

Google on Monday released security updates for its Chrome browser to address two security flaws, including one that has come under active exploitation in the wild. The vulnerability in question is CVE-2025-13223 (CVSS score: 8.8), a type confusion vulnerability in the V8 JavaScript and WebAssembly engine that could be exploited to achieve arbitrary code execution … Read More “Google Issues Security Fix for Actively Exploited Chrome V8 Zero-Day Vulnerability – The Hacker News” »
Alice Blue Partners with AccuKnox for Regulatory Compliance – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Menlo Park, CA, November 17th, 2025, CyberNewsWire. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Bitsgap vs HaasOnline: Advanced Features vs Smart Simplicity – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Power vs Practicality in Crypto Automation – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Federal authorities and researchers alerted organizations Friday to a massively exploited vulnerability in Fortinet’s web application firewall. While the actively exploited critical defect poses significant risk to Fortinet’s customers, researchers are particularly agitated about the vendor’s delayed communications and, ultimately, post-exploitation warnings about the vulnerability. Fortinet addressed CVE-2025-64446 in a software update pushed Oct. 28, … Read More “Fortinet’s delayed alert on actively exploited defect put defenders at a disadvantage – CyberScoop” »
On Monday, more than 60 digital commerce and trade groups called on governments around the globe to reject efforts or requests to weaken or bypass encryption, saying strong encrypted communications provides critical protections for user privacy, secure data protection and trust that underpin some of society’s most important interactions. “Encryption is a vital tool for … Read More “Dozens of groups call for governments to protect encryption – CyberScoop” »
Everest Ransomware Says It Stole Data of Millions of Under Armour Users – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Everest ransomware claims to have breached Under Armour, stealing 343GB of data, including customer info, product records, and internal company files. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Cybersecurity researchers have discovered malware campaigns using the now-prevalent ClickFix social engineering tactic to deploy Amatera Stealer and NetSupport RAT. The activity, observed this month, is being tracked by eSentire under the moniker EVALUSION. First spotted in June 2025, Amatera is assessed to be an evolution of ACR (short for “AcridRain”) Stealer, which was available … Read More “New EVALUSION ClickFix Campaign Delivers Amatera Stealer and NetSupport RAT – The Hacker News” »
Cisco Talos has observed overlaps between Kraken and the earlier HelloKitty cartel through attack tactics using SMB flaws for big-game hunting and double extortion – Read More –
Europol’s Referral Action Day removed extremist links across gaming and gaming-adjacent platforms, targeting radical content – Read More –
EchoGram Flaw Bypasses Guardrails in Major LLMs – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

HiddenLayer reveals the EchoGram vulnerability, which bypasses safety guardrails on GPT-5.1 and other major LLMs, giving security teams just a 3-month head start. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Frentree Partners with AccuKnox to Expand Zero Trust CNAPP Security in South Korea – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Menlo Park, California, USA, 17th November 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More