Researchers at BlackFrog have uncovered Matrix Push C2, a malicious command-and-control system that abuses web browser push notifications to deliver malware – Read More –
Google Brings AirDrop Compatibility to Android’s Quick Share Using Rust-Hardened Security – The Hacker News
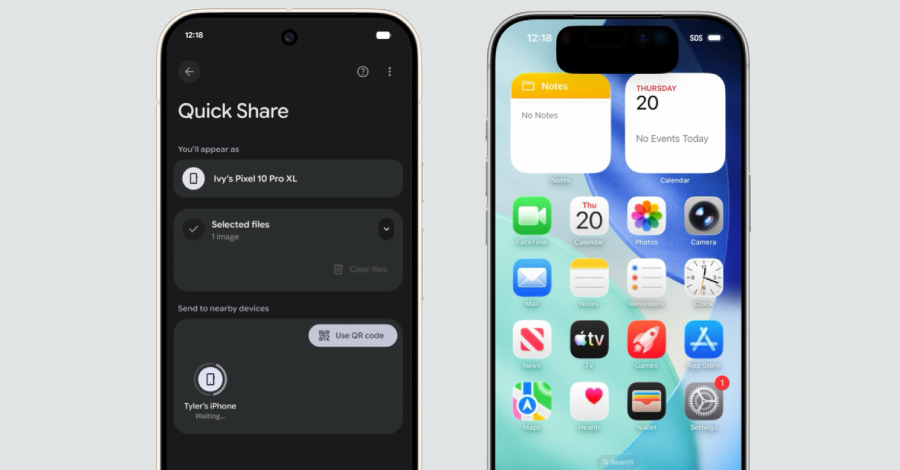
In a surprise move, Google on Thursday announced that it has updated Quick Share, its peer-to-peer file transfer service, to work with Apple’s equipment AirDrop, allowing users to more easily share files and photos between Android and iPhone devices. The cross-platform sharing feature is currently limited to the Pixel 10 lineup and works with iPhone, … Read More “Google Brings AirDrop Compatibility to Android’s Quick Share Using Rust-Hardened Security – The Hacker News” »
A China-nexus threat actor known as APT24 has been observed using a previously undocumented malware dubbed BADAUDIO to establish persistent remote access to compromised networks as part of a nearly three-year campaign. “While earlier operations relied on broad strategic web compromises to compromise legitimate websites, APT24 has recently pivoted to using more sophisticated vectors targeting … Read More “APT24 Deploys BADAUDIO in Years-Long Espionage Hitting Taiwan and 1,000+ Domains – The Hacker News” »
Ever wonder how some IT teams keep corporate data safe without slowing down employees? Of course you have. Mobile devices are essential for modern work—but with mobility comes risk. IT admins, like you, juggle protecting sensitive data while keeping teams productive. That’s why more enterprises are turning to Samsung for mobile security. Hey—you’re busy, so … Read More “Why IT Admins Choose Samsung for Mobile Security – The Hacker News” »
Federal, state, and local government agencies face a critical vulnerability hiding in plain sight: outdated web forms collecting citizen data through insecure channels. While agencies invest in perimeter security and threat detection, many continue using legacy forms built years ago without modern encryption, authentication, or compliance capabilities. These aging systems collect Social Security numbers, financial … Read More “Legacy web forms are the weakest link in government data security – CyberScoop” »
Federal, state, and local government agencies face a critical vulnerability hiding in plain sight: outdated web forms collecting citizen data through insecure channels. While agencies invest in perimeter security and threat detection, many continue using legacy forms built years ago without modern encryption, authentication, or compliance capabilities. These aging systems collect Social Security numbers, financial … Read More “Legacy web forms are the weakest link in government data security – CyberScoop” »
Salesforce believes there has been unauthorized access to its customers’ data through the Gainsight app’s connection to its platform – Read More –
The U.S. Securities and Exchange Commission (SEC) has abandoned its lawsuit against SolarWinds and its chief information security officer, alleging that the company had misled investors about the security practices that led to the 2020 supply chain attack. In a joint motion filed November 20, 2025, the SEC, along with SolarWinds and its CISO Timothy … Read More “SEC Drops SolarWinds Case After Years of High-Stakes Cybersecurity Scrutiny – The Hacker News” »
The race toward quantum computing supremacy is no longer confined to research labs, it’s entering boardrooms, policy discussions, and… The post Quantum-Ready HSM: Is Your Business Prepared? appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Salesforce has warned of detected “unusual activity” related to Gainsight-published applications connected to the platform. “Our investigation indicates this activity may have enabled unauthorized access to certain customers’ Salesforce data through the app’s connection,” the company said in an advisory. The cloud services firm said it has taken the step of revoking all active access … Read More “Salesforce Flags Unauthorized Data Access via Gainsight-Linked OAuth Activity – The Hacker News” »
NSO Group argued in a court filing this week that the court should pause the permanent injunction preventing it from targeting WhatsApp with its spyware while the company appeals the decision. According to the company, enforcing the injunction would cause irreparable harm to its business and prevent the U.S. government from using its products. Those … Read More “NSO Group argues WhatsApp injunction threatens existence, future U.S. government work – CyberScoop” »
Salesforce said yet another breach involving a third-party vendor has compromised customers’ data, warning in a security advisory late Wednesday that it detected unusual activity in Gainsight applications connected to Salesforce customer environments. “Google Threat Intelligence Group is aware of more than 200 potentially affected Salesforce instances,” Austin Larsen, principal analyst at GTIG, told CyberScoop. … Read More “Hundreds of Salesforce customers hit by yet another third-party vendor breach – CyberScoop” »
The Securities and Exchange Commission on Thursday dropped its case against SolarWinds and its chief information security officer over its handling of an alleged Russian cyberespionage campaign uncovered in 2020, an incident that penetrated at least nine federal agencies and hundreds of companies. The SEC’s decision brings to a halt one of the more divisive … Read More “SEC drops case against SolarWinds tied to monumental breach – CyberScoop” »
In March 2024, Mozilla said it was winding down its collaboration with Onerep — an identity protection service offered with the Firefox web browser that promises to remove users from hundreds of people-search sites — after KrebsOnSecurity revealed Onerep’s founder had created dozens of people-search services and was continuing to operate at least one of … Read More “Mozilla Says It’s Finally Done With Two-Faced Onerep – Krebs on Security” »
After years of delays, the UK government has finally introduced landmark cybersecurity legislation that could reshape how British organisations defend against digital attacks. Read more in my article on the Fortra blog. – Read More – Graham Cluley
Everest Ransomware Says It Breached Brazilian Energy Giant Petrobras – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Everest ransomware claims to have stolen over 180GB of seismic survey data from Petrobras, demanding contact through qTox with a countdown in place. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Top Senate Intel Dem warns of ‘catastrophic’ cyber consequences of Trump admin national security firings, politicization – CyberScoop

Politicization of intelligence in the Trump administration, as well as the “hollowing out” of government expertise, is leaving the United States dangerously vulnerable to cyberattacks and other threats, the top Democrat on the Senate Intelligence Committee said in a floor speech Thursday. Mark Warner of Virginia chastised the president over what he called the politically-motivated … Read More “Top Senate Intel Dem warns of ‘catastrophic’ cyber consequences of Trump admin national security firings, politicization – CyberScoop” »
Cybersecurity researchers have disclosed details of a new Android banking trojan called Sturnus that enables credential theft and full device takeover to conduct financial fraud. “A key differentiator is its ability to bypass encrypted messaging,” ThreatFabric said in a report shared with The Hacker News. “By capturing content directly from the device screen after decryption, … Read More “New Sturnus Android Trojan Quietly Captures Encrypted Chats and Hijacks Devices – The Hacker News” »
Cybersecurity researchers have warned of an actively expanding botnet dubbed Tsundere that’s targeting Windows users. Active since mid-2025, the threat is designed to execute arbitrary JavaScript code retrieved from a command-and-control (C2) server, Kaspersky researcher Lisandro Ubiedo said in an analysis published today. There are currently no details on how the botnet malware is propagated; … Read More “Tsundere Botnet Expands Using Game Lures and Ethereum-Based C2 on Windows – The Hacker News” »
ShadowRay 2.0 Exploits Unpatched Ray Flaw to Build Self-Spreading GPU Cryptomining Botnet – The Hacker News

Oligo Security has warned of ongoing attacks exploiting a two-year-old security flaw in the Ray open-source artificial intelligence (AI) framework to turn infected clusters with NVIDIA GPUs into a self-replicating cryptocurrency mining botnet. The activity, codenamed ShadowRay 2.0, is an evolution of a prior wave that was observed between September 2023 and March 2024. The … Read More “ShadowRay 2.0 Exploits Unpatched Ray Flaw to Build Self-Spreading GPU Cryptomining Botnet – The Hacker News” »
A multi-year ATM fraud campaign by UNC2891 targeted two Indonesian banks, cloning cards, recruiting money mules and coordinating cash withdrawals – Read More –
CISA launches guide to combat cybercrime via bulletproof hosting, recommending measures for ISPs – Read More –
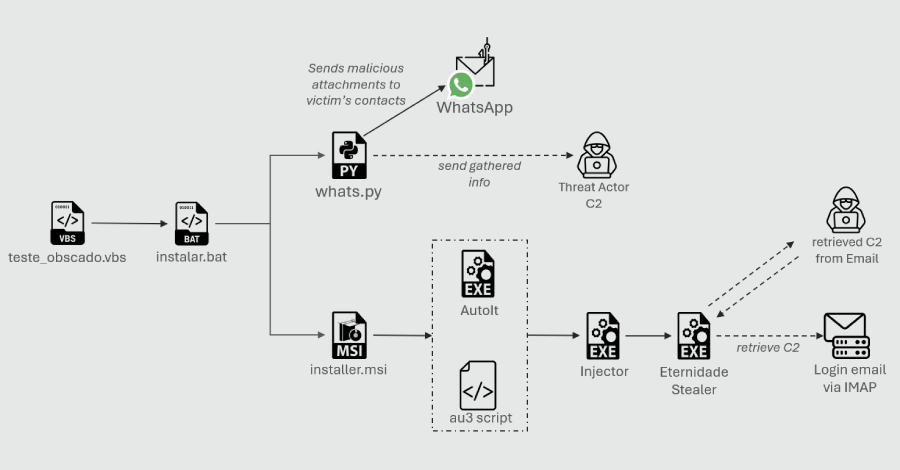
New Eternidade Stealer Uses WhatsApp to Steal Banking Data – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Trustwave SpiderLabs warns of Eternidade Stealer, a new banking trojan spreading via personalised WhatsApp messages. Find out how this malicious software bypasses security checks and deploys fake login screens for major banks and wallets. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Despite a growing maturity of third-party risk management programs, supply chain attacks impacted more organizations in 2025 than in previous years – Read More –
The Federal Communications Commission is set to vote Thursday on whether to rescind a set of last-minute Biden administration regulations following a massive Chinese compromise of U.S. telecommunications infrastructure last year. Chair Brendan Carr has called the rule ineffective and unlawful, and with the likely support of newly confirmed commissioner Olivia Trusty, there is a … Read More “Why Anna Gomez believes the FCC is letting telecoms off easy after Salt Typhoon – CyberScoop” »
Comet Browser Flaw Lets Hidden API Run Commands on Users’ Devices – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

SquareX warns Perplexity’s Comet AI browser contains a hidden MCP API that bypasses security, allowing attackers to install malware and seize full device control. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
ThreatsDay Bulletin: 0-Days, LinkedIn Spies, Crypto Crimes, IoT Flaws and New Malware Waves – The Hacker News

This week has been crazy in the world of hacking and online security. From Thailand to London to the US, we’ve seen arrests, spies at work, and big power moves online. Hackers are getting caught. Spies are getting better at their jobs. Even simple things like browser add-ons and smart home gadgets are being used … Read More “ThreatsDay Bulletin: 0-Days, LinkedIn Spies, Crypto Crimes, IoT Flaws and New Malware Waves – The Hacker News” »
CTM360 has identified a rapidly expanding WhatsApp account-hacking campaign targeting users worldwide via a network of deceptive authentication portals and impersonation pages. The campaign, internally dubbed HackOnChat, abuses WhatsApp’s familiar web interface, using social engineering tactics to trick users into compromising their accounts. Investigators identified thousands of malicious URLs – Read More – The Hacker … Read More “CTM360 Exposes a Global WhatsApp Hijacking Campaign: HackOnChat – The Hacker News” »
Stop the press – a company has actually said “sorry” after a data breach, and hotels are helping hackers phish their own guests. We examine a refreshingly honest breach response (and why legacy systems are still going to ruin your week), dig into a nasty hotel-booking malware campaign that abuses trust in apps and CAPTCHAs, … Read More “Smashing Security podcast #444: We’re sorry. Wait, did a company actually say that? – Graham Cluley” »
A technical manager at a Dutch wind farm operator has been sentenced after it was discovered he had secretly installed cryptocurrency mining rigs at two wind farm sites – just as the company was recovering from a ransomware attack. Read more in my article on the Hot for Security blog. – Read More – Graham … Read More “Wind farm worker sentenced after turning turbines into a secret crypto mine – Graham Cluley” »
Gartner predicts that two-fifths of organizations will suffer security and compliance incidents due to shadow AI by 2030 – Read More –
Allies sanction bulletproof hoster Media Land and four executives – Read More –
Iran-Linked Hackers Mapped Ship AIS Data Days Before Real-World Missile Strike Attempt – The Hacker News

Threat actors with ties to Iran engaged in cyber warfare as part of efforts to facilitate and enhance physical, real-world attacks, a trend that Amazon has called cyber-enabled kinetic targeting. The development is a sign that the lines between state-sponsored cyber attacks and kinetic warfare are increasingly blurring, necessitating the need for a new category … Read More “Iran-Linked Hackers Mapped Ship AIS Data Days Before Real-World Missile Strike Attempt – The Hacker News” »
TamperedChef Malware Spreads via Fake Software Installers in Ongoing Global Campaign – The Hacker News

Threat actors are leveraging bogus installers masquerading as popular software to trick users into installing malware as part of a global malvertising campaign dubbed TamperedChef. The end goal of the attacks is to establish persistence and deliver JavaScript malware that facilitates remote access and control, per a new report from Acronis Threat Research Unit (TRU). … Read More “TamperedChef Malware Spreads via Fake Software Installers in Ongoing Global Campaign – The Hacker News” »
Palo Alto Networks announced Wednesday it will acquire Chronosphere, a cloud observability platform, for $3.35 billion in cash and equity, marking the cybersecurity company’s latest move to expand beyond its traditional security perimeter into adjacent infrastructure monitoring capabilities. The acquisition represents a significant bet on the convergence of security and operational observability as organizations grapple … Read More “Palo Alto Networks to acquire observability firm Chronosphere for $3.35 billion – CyberScoop” »
The Treasury Department, along with officials from the United Kingdom and Australia, imposed sanctions Wednesday against two bulletproof hosting providers and key people involved in their operations, in a globally coordinated effort aimed at thwarting the role these services have in enabling ransomware, phishing operations, and data extortion campaigns around the world. Authorities sanctioned Media … Read More “Five Eyes just made life harder for bulletproof hosting providers – CyberScoop” »
Posted by Micha Borrmann via Fulldisclosure on Nov 19 Advisory ID: SYSS-2025-059 Product: Dell computer Manufacturer: Dell Affected Version(s): Probably all Dell computers Tested Version(s): Latitude 5431 (BIOS 1.33.1), Latitude 7320 (BIOS 1.44.1), Latitude 7400 (BIOS 1.41.1), Latitude 7480 (BIOS 1.41.3), Latitude 9430 (BIOS… – Read More – Full Disclosure
Posted by Matteo Beccati on Nov 19 ======================================================================== Revive Adserver Security Advisory REVIVE-SA-2025-003 ———————————————————————— https://www.revive-adserver.com/security/revive-sa-2025-003 ———————————————————————— Date: 2025-11-05 Risk Level: High Applications affected: Revive… – Read More – Full Disclosure
Posted by Matteo Beccati on Nov 19 ======================================================================== Revive Adserver Security Advisory REVIVE-SA-2025-004 ———————————————————————— https://www.revive-adserver.com/security/revive-sa-2025-004 ———————————————————————— Date: 2025-11-19 Risk Level: Medium Applications affected: Revive… – Read More – Full Disclosure
UK Exposes Bulletproof Hosting Operator Linked to LockBit and Evil Corp – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

The operator, Alexander Volosovik, also known as “Yalishanda”, “Downlow” and “Stas_vl,” ran a long-running bulletproof hosting operation used by top ransomware groups. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Amazon said the lines between cyberattacks and physical, real-world attacks are blurring quickly — prompting the tech giant to call for a new category of warfare: cyber-enabled kinetic targeting. Nation-states have combined and understood how logical systems and the physical world interact for a long time, but more non-traditional attackers are showcasing expertise in using … Read More “Amazon warns of global rise in specialized cyber-enabled kinetic targeting – CyberScoop” »
Hacker Selling Alleged Samsung Medison Data Stolen In 3rd Party Breach – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Hacker using the alias 888, claims to be selling Samsung Medison data taken through a third party breach, including internal files, keys and user info. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Hackers Actively Exploiting 7-Zip Symbolic Link–Based RCE Vulnerability (CVE-2025-11001) – The Hacker News

A recently disclosed security flaw impacting 7-Zip has come under active exploitation in the wild, according to an advisory issued by the U.K. NHS England Digital on Tuesday. The vulnerability in question is CVE-2025-11001 (CVSS score: 7.0), which allows remote attackers to execute arbitrary code. It has been addressed in 7-Zip version 25.00 released in … Read More “Hackers Actively Exploiting 7-Zip Symbolic Link–Based RCE Vulnerability (CVE-2025-11001) – The Hacker News” »
Europe-wide Cyber-Patrol Week targeted IP violations, flagging 69 sites and disrupting $55m in crypto services – Read More –
Fortinet Issues Fixes as FortiWeb Takeover Flaw Sees Active Attacks – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Two FortiWeb vulnerabilities, including a critical unauthenticated bypass (CVE-2025-64446), are under attack. Check logs for rogue admin accounts and upgrade immediately. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Seraphic Becomes the First and Only Secure Enterprise Browser Solution to Protect Electron-Based Applications – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Tel Aviv, Israel, 19th November 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Cybersecurity researchers have disclosed details of a new campaign that leverages a combination of social engineering and WhatsApp hijacking to distribute a Delphi-based banking trojan named Eternidade Stealer as part of attacks targeting users in Brazil. “It uses Internet Message Access Protocol (IMAP) to dynamically retrieve command-and-control (C2) addresses, allowing the threat actor to – … Read More “Python-Based WhatsApp Worm Spreads Eternidade Stealer Across Brazilian Devices – The Hacker News” »
Trustwave SpiderLabs has observed new banking Trojan Eternidade Stealer targeting Brazil using WhatsApp for propagation and data theft – Read More –
Obscure MCP API in Comet Browser Breaches User Trust, Enabling Full Device Control via AI Browsers – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Palo Alto, California, 19th November 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
An intermittent outage at Cloudflare on Tuesday briefly knocked many of the Internet’s top destinations offline. Some affected Cloudflare customers were able to pivot away from the platform temporarily so that visitors could still access their websites. But security experts say doing so may have also triggered an impromptu network penetration test for organizations that … Read More “The Cloudflare Outage May Be a Security Roadmap – Krebs on Security” »




























![[SYSS-2025-059]: Dell computer UEFI boot protection bypass [SYSS-2025-059]: Dell computer UEFI boot protection bypass – Full Disclosure](https://attackfeed.com/wp-content/uploads/2025/11/fulldisclosure-img-fDAcDK.webp)
![[REVIVE-SA-2025-003] Revive Adserver Vulnerabilities [REVIVE-SA-2025-003] Revive Adserver Vulnerabilities – Full Disclosure](https://attackfeed.com/wp-content/uploads/2025/11/fulldisclosure-img-hNezSQ.webp)
![[REVIVE-SA-2025-004] Revive Adserver Vulnerabilities [REVIVE-SA-2025-004] Revive Adserver Vulnerabilities – Full Disclosure](https://attackfeed.com/wp-content/uploads/2025/11/fulldisclosure-img-W4d2Et.webp)