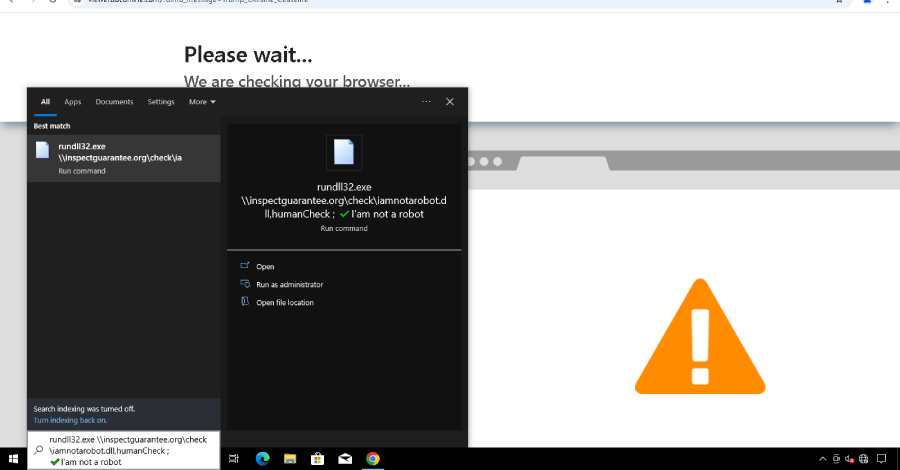
Recorded Future highlighted the vast capabilities of state actors to rapidly weaponize newly disclosed vulnerabilities for geopolitical purposes – Read More –
The Sangoma FreePBX Security Team has issued an advisory warning about an actively exploited FreePBX zero-day vulnerability that impacts systems with an administrator control panel (ACP) exposed to the public internet. FreePBX is an open-source private branch exchange (PBX) platform widely used by businesses, call centers, and service providers to manage voice communications. It’s built … Read More “FreePBX Servers Targeted by Zero-Day Flaw, Emergency Patch Now Available – The Hacker News” »
Click Studios Patches Passwordstate Authentication Bypass Vulnerability in Emergency Access Page – The Hacker News

Click Studios, the developer of enterprise-focused password management solution Passwordstate, said it has released security updates to address an authentication bypass vulnerability in its software. The issue, which is yet to be assigned a CVE identifier, has been addressed in Passwordstate 9.9 (Build 9972), released August 28, 2025. The Australian company said it fixed a … Read More “Click Studios Patches Passwordstate Authentication Bypass Vulnerability in Emergency Access Page – The Hacker News” »
Feds Seize $6.4M VerifTools Fake-ID Marketplace, but Operators Relaunch on New Domain – The Hacker News
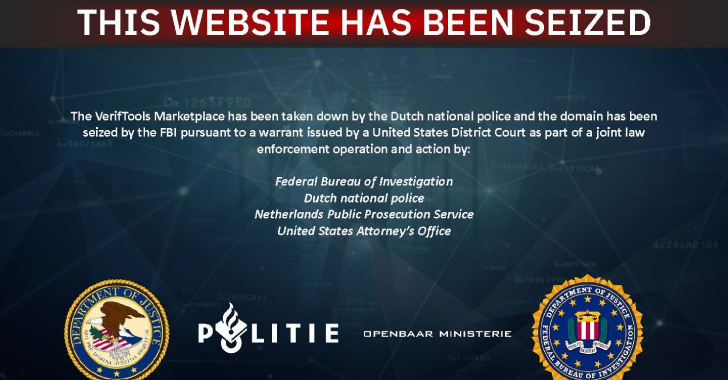
Authorities from the Netherlands and the United States have announced the dismantling of an illicit marketplace called VerifTools that peddled fraudulent identity documents to cybercriminals across the world. To that end, two marketplace domains (verif[.]tools and veriftools[.]net) and one blog have been taken down, redirecting site visitors to a splash page stating the action was … Read More “Feds Seize $6.4M VerifTools Fake-ID Marketplace, but Operators Relaunch on New Domain – The Hacker News” »
The credit rating giant revealed that the breach, which occurred on July 28, was caused by unauthorized access to a third-party application – Read More –
Southeast Asia’s Hidden Crisis – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.

The UN Reveals Widespread Trafficking into Online Scam Operations Every day, thousands of lives are torn apart in the shadows of Southeast Asia. A harrowing UN Human Rights Office (OHCHR) report from 29 August 2023 reveals that hundreds of thousands of individuals have been trafficked and forced into online scam operations, often under brutal and … Read More “Southeast Asia’s Hidden Crisis – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.” »
Google Warns Salesloft OAuth Breach Extends Beyond Salesforce, Impacting All Integrations – The Hacker News

Google has revealed that the recent wave of attacks targeting Salesforce instances via Salesloft Drift is much broader in scope than previously thought, stating it impacts all integrations. “We now advise all Salesloft Drift customers to treat any and all authentication tokens stored in or connected to the Drift platform as potentially compromised,” Google Threat … Read More “Google Warns Salesloft OAuth Breach Extends Beyond Salesforce, Impacting All Integrations – The Hacker News” »
The semiconductor industry has become the throbbing heart of the current technology, and the tech ecosystem runs on it… The post Building Cyber Resilience in the Semiconductor Ecosystem appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Cybersecurity researchers have discovered a cybercrime campaign that’s using malvertising tricks to direct victims to fraudulent sites to deliver a new information stealer called TamperedChef. “The objective is to lure victims into downloading and installing a trojanized PDF editor, which includes an information-stealing malware dubbed TamperedChef,” Truesec researchers Mattias Wåhlén, Nicklas – Read More – … Read More “TamperedChef Malware Disguised as Fake PDF Editors Steals Credentials and Cookies – The Hacker News” »
CISA Adds Citrix and Git Flaws to KEV Catalogue Amid Active Exploitation – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

CISA has added three actively exploited vulnerabilities in Citrix and Git to its KEV Catalogue. Federal agencies must… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Salesloft Drift customers are compromised in a much more expansive downstream attack spree than previously thought, potentially ensnaring any user that integrated the AI chat agent platform to another service. “We’re telling organizations to treat any Drift integration into any platform as potentially compromised, so that increases the scope of victims,” Mandiant Consulting CTO Charles … Read More “Salesloft Drift compromised en masse, impacting all third-party integrations – CyberScoop” »
Researchers Find VS Code Flaw Allowing Attackers to Republish Deleted Extensions Under Same Names – The Hacker News

Cybersecurity researchers have discovered a loophole in the Visual Studio Code Marketplace that allows threat actors to reuse names of previously removed extensions. Software supply chain security outfit ReversingLabs said it made the discovery after it identified a malicious extension named “ahbanC.shiba” that functioned similarly to two other extensions – ahban.shiba and ahban.cychelloworld – – … Read More “Researchers Find VS Code Flaw Allowing Attackers to Republish Deleted Extensions Under Same Names – The Hacker News” »
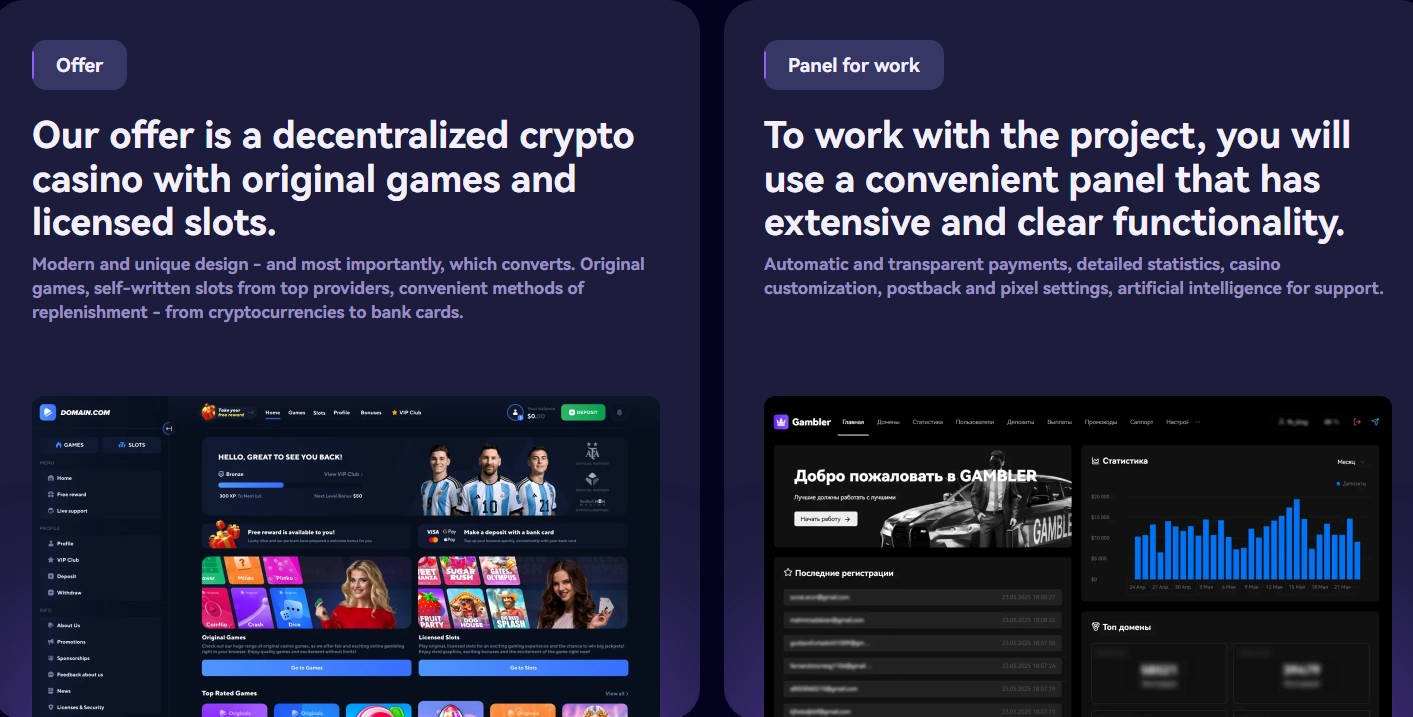
Last month, KrebsOnSecurity tracked the sudden emergence of hundreds of polished online gaming and wagering websites that lure people with free credits and eventually abscond with any cryptocurrency funds deposited by players. We’ve since learned that these scam gambling sites have proliferated thanks to a new Russian affiliate program called “Gambler Panel” that bills itself … Read More “Affiliates Flock to ‘Soulless’ Scam Gambling Machine – Krebs on Security” »
Halo Security Enhances Platform with Custom Dashboards and Reports – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
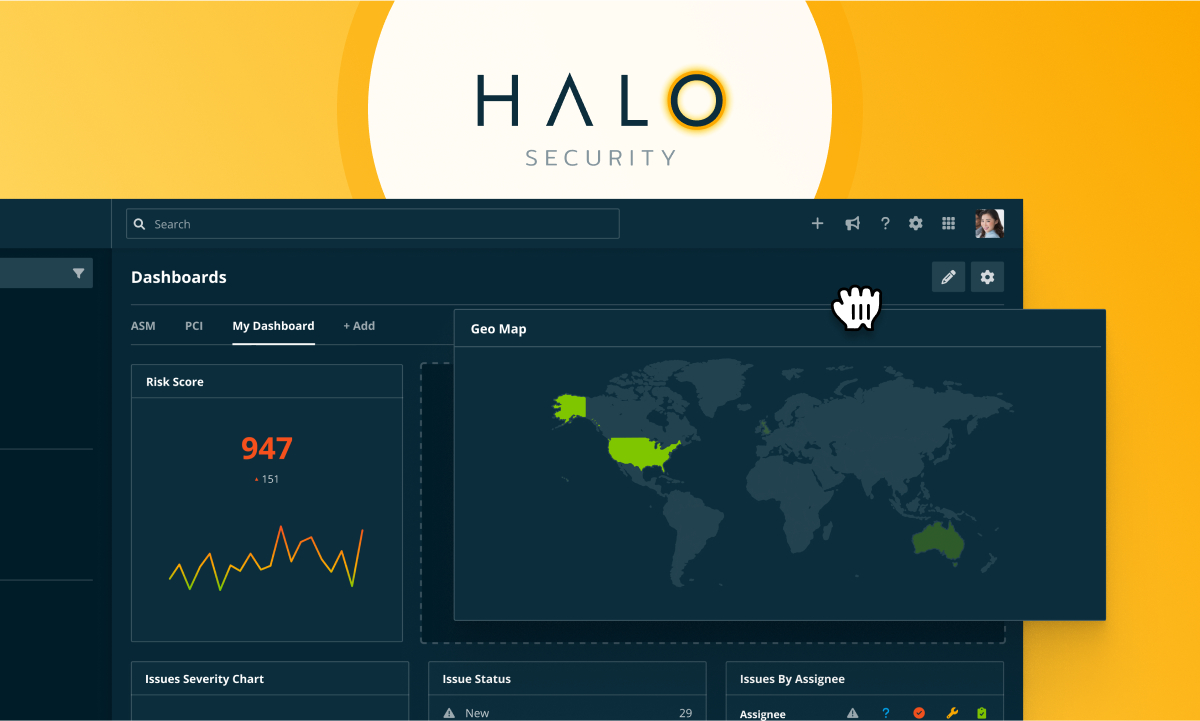
Miami, United States, 28th August 2025, CyberNewsWire – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Thousands of Developer Credentials Stolen in macOS “s1ngularity” Attack – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

A supply chain attack called “s1ngularity” on Nx versions 20.9.0-21.8.0 stole thousands of developer credentials. The attack targeted… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Trump administration setting the stage for elections power grab, voting rights group warns – CyberScoop

Election officials should brace for direct attacks from the Trump administration and its state GOP allies on the integrity of U.S. elections — and plan for the possibility that federal agencies once charged with protecting elections will leverage their authorities to interfere in the process, a voting rights nonprofit warned. In a report released Wednesday, … Read More “Trump administration setting the stage for elections power grab, voting rights group warns – CyberScoop” »
Election officials should brace for direct attacks from the Trump administration and its state GOP allies on the integrity of U.S. elections — and plan for the possibility that federal agencies once charged with protecting elections will leverage their authorities to interfere in the process, a voting rights nonprofit warned. In a report released Wednesday, … Read More “Trump administration setting the stage for elections power grab, voting rights group warns – CyberScoop” »
Fake IT support lures are being used to trick employees into installing remote‑access tools via Microsoft Teams – Read More –
Salt Typhoon Exploits Cisco, Ivanti, Palo Alto Flaws to Breach 600 Organizations Worldwide – The Hacker News

The China-linked advanced persistent threat (APT) actor known as Salt Typhoon has continued its attacks targeting networks across the world, including organizations in the telecommunications, government, transportation, lodging, and military infrastructure sectors. “While these actors focus on large backbone routers of major telecommunications providers, as well as provider edge (PE) and – Read More – … Read More “Salt Typhoon Exploits Cisco, Ivanti, Palo Alto Flaws to Breach 600 Organizations Worldwide – The Hacker News” »
UK and US Blame Three Chinese Tech Firms for Global Cyberattacks – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

A coalition of international cybersecurity agencies led by the UK’s National Cyber Security Centre (NCSC) has publicly linked… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Salt Typhoon’s primary Dutch targets were small internet service providers and hosting providers – Read More –
Picture this: Your team rolls out some new code, thinking everything’s fine. But hidden in there is a tiny flaw that explodes into a huge problem once it hits the cloud. Next thing you know, hackers are in, and your company is dealing with a mess that costs millions. Scary, right? In 2025, the average … Read More “Webinar: Why Top Teams Are Prioritizing Code-to-Cloud Mapping in Our 2025 AppSec – The Hacker News” »
Visual Studio Code extensions have been identified exploiting a loophole that allows reuse of names from removed packages – Read More –
The Role of Enterprise Email Security in Modern Cybersecurity Strategies – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Email has always been a double-edged sword in the world of business. On one hand, it’s the fastest,… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Google Big Sleep AI Tool Finds Critical Chrome Vulnerability – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Make sure your Chrome browser is updated to the latest version to stay protected. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Nevada’s CIO confirmed in a press conference that ransomware actors had exfiltrated data from state networks, amid an ongoing incident investigation – Read More –
Hidden Vulnerabilities of Project Management Tools & How FluentPro Backup Secures Them – The Hacker News

Every day, businesses, teams, and project managers trust platforms like Trello, Asana, etc., to collaborate and manage tasks. But what happens when that trust is broken? According to a recent report by Statista, the average cost of a data breach worldwide was about $4.88 million. Also, in 2024, the private data of over 15 million … Read More “Hidden Vulnerabilities of Project Management Tools & How FluentPro Backup Secures Them – The Hacker News” »
Malicious Nx Packages in ‘s1ngularity’ Attack Leaked 2,349 GitHub, Cloud, and AI Credentials – The Hacker News

The maintainers of the nx build system have alerted users to a supply chain attack that allowed attackers to publish malicious versions of the popular npm package and other auxiliary plugins with data-gathering capabilities. “Malicious versions of the nx package, as well as some supporting plugin packages, were published to npm, containing code that scans … Read More “Malicious Nx Packages in ‘s1ngularity’ Attack Leaked 2,349 GitHub, Cloud, and AI Credentials – The Hacker News” »
The US, UK and allies have called out China’s “commercial cyber ecosystem” for enabling large-scale Salt Typhoon campaigns – Read More –
U.S. Treasury Sanctions DPRK IT-Worker Scheme, Exposing $600K Crypto Transfers and $1M+ Profits – The Hacker News

The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) announced a fresh round of sanctions against two individuals and two entities for their role in the North Korean remote information technology (IT) worker scheme to generate illicit revenue for the regime’s weapons of mass destruction and ballistic missile programs. “The North Korean … Read More “U.S. Treasury Sanctions DPRK IT-Worker Scheme, Exposing $600K Crypto Transfers and $1M+ Profits – The Hacker News” »
Chainalysis, OKX, Binance and Tether have managed to stop nearly $50m reaching romance baiting fraudsters – Read More –
Microsoft observed Storm-0501 pivot to the victim’s cloud environment to exfiltrate data rapidly and prevent the victim’s recovery – Read More –
By 2025, nothing about enterprise security will be characterized by firewalls, VPN, or conventional endpoint security measures. The actual… The post Secrets sprawl & credential abuse: What enterprises must fix in 2025 appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd