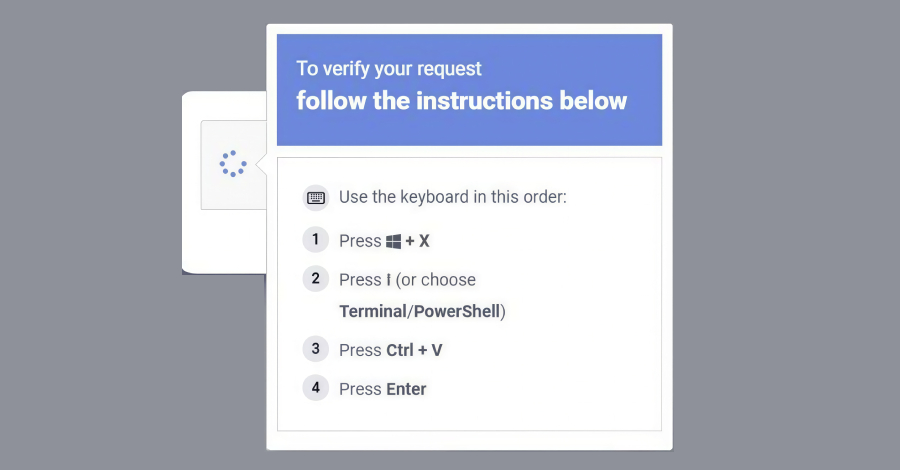
Threat Actors Mass-Scan Salesforce Experience Cloud via Modified AuraInspector Tool – The Hacker News

Salesforce has warned of an increase in threat actor activity that’s aimed at exploiting misconfigurations in publicly accessible Experience Cloud sites by making use of a customized version of an open-source tool called AuraInspector. The activity, per the company, involves the exploitation of customers’ overly permissive Experience Cloud guest user configurations to obtain access to … Read More “Threat Actors Mass-Scan Salesforce Experience Cloud via Modified AuraInspector Tool – The Hacker News” »