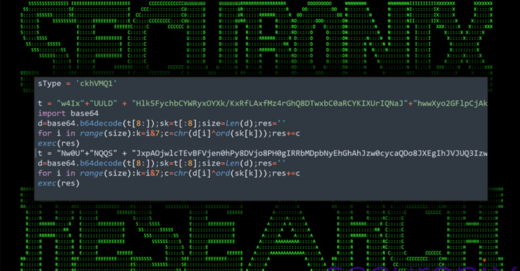
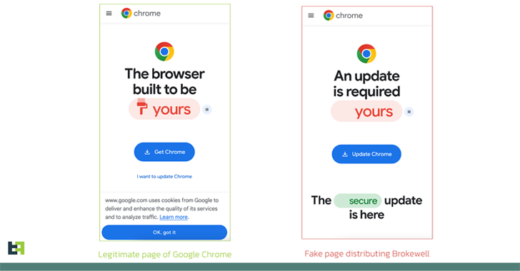
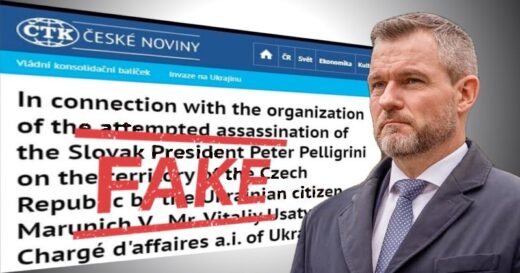
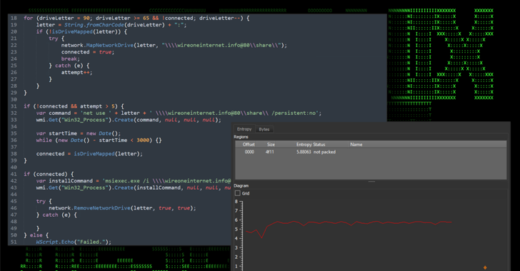
Okta Warns of Unprecedented Surge in Proxy-Driven Credential Stuffing Attacks – [email protected] (The Hacker News)
– [[{“value”:”Identity and access management (IAM) services provider Okta has warned of a spike in the “frequency and scale” of credential stuffing attacks aimed at online services. These unprecedented attacks, observed over the last month, are said to be facilitated by “the broad availability of residential proxy services, lists of previously stolen credentials (‘combo lists’), and scripting tools,” the”}]] –...