New Immersive report finds cyber resilience and decision making are flatlining – Read More –
Phishing attacks are no longer confined to the email inbox, with 1 in 3 phishing attacks now taking place over non-email channels like social media, search engines, and messaging apps. LinkedIn in particular has become a hotbed for phishing attacks, and for good reason. Attackers are running sophisticated spear-phishing attacks against company executives, with recent … Read More “5 Reasons Why Attackers Are Phishing Over LinkedIn – The Hacker News” »
This week showed just how fast things can go wrong when no one’s watching. Some attacks were silent and sneaky. Others used tools we trust every day — like AI, VPNs, or app stores — to cause damage without setting off alarms. It’s not just about hacking anymore. Criminals are building systems to make money, … Read More “⚡ Weekly Recap: Fortinet Exploited, China’s AI Hacks, PhaaS Empire Falls & More – The Hacker News” »
The threat actor known as Dragon Breath has been observed making use of a multi-stage loader codenamed RONINGLOADER to deliver a modified variant of a remote access trojan called Gh0st RAT. The campaign, which is primarily aimed at Chinese-speaking users, employs trojanized NSIS installers masquerading as legitimate like Google Chrome and Microsoft Teams, according to … Read More “Dragon Breath Uses RONINGLOADER to Disable Security Tools and Deploy Gh0st RAT – The Hacker News” »
The five defendants allegedly assisted North Korean hackers with obtaining remote IT employment with US companies – Read More –
Carmaker JLR has posted $639m Q2 losses and a one-off $258m hit after a major ransomware attack – Read More –
Google has disclosed that the company’s continued adoption of the Rust programming language in Android has resulted in the number of memory safety vulnerabilities falling below 20% for the first time. “We adopted Rust for its security and are seeing a 1000x reduction in memory safety vulnerability density compared to Android’s C and C++ code. … Read More “Rust Adoption Drives Android Memory Safety Bugs Below 20% for First Time – The Hacker News” »
AIPAC Discloses Data Breach, Says Hundreds Affected – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

AIPAC reports data breach after external system access, hundreds affected, investigation ongoing with added security steps. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Microsoft this week pushed security updates to fix more than 60 vulnerabilities in its Windows operating systems and supported software, including at least one zero-day bug that is already being exploited. Microsoft also fixed a glitch that prevented some Windows 10 users from taking advantage of an extra year of security updates, which is nice … Read More “Microsoft Patch Tuesday, November 2025 Edition – Krebs on Security” »
DoorDash hit by data breach after an employee falls for social engineering scam – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Food delivery giant DoorDash confirms a data breach on Oct 25, 2025, where an employee fell for a social engineering scam. User names, emails, and home addresses were stolen. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
A vulnerability has been discovered FortiWeb, which could allow for remote code execution. FortiWeb is a web application firewall (WAF) developed by Fortinet. It’s designed to protect web applications and APIs from a wide range of attacks, including those targeting known vulnerabilities and zero-day exploits. Successful exploitation of this vulnerability could allow an attacker to execute … Read More “A Vulnerability in FortiWeb Could Allow for Remote Code Execution – Cyber Security Advisories – MS-ISAC” »
The botnet malware known as RondoDox has been observed targeting unpatched XWiki instances against a critical security flaw that could allow attackers to achieve arbitrary code execution. The vulnerability in question is CVE-2025-24893 (CVSS score: 9.8), an eval injection bug that could allow any guest user to perform arbitrary remote code execution through a request … Read More “RondoDox Exploits Unpatched XWiki Servers to Pull More Devices Into Its Botnet – The Hacker News” »
Five U.S. Citizens Plead Guilty to Helping North Korean IT Workers Infiltrate 136 Companies – The Hacker News

The U.S. Department of Justice (DoJ) on Friday announced that five individuals have pleaded guilty to assisting North Korea’s illicit revenue generation schemes by enabling information technology (IT) worker fraud in violation of international sanctions. The five individuals are listed below – Audricus Phagnasay, 24 Jason Salazar, 30 Alexander Paul Travis, 34 Oleksandr Didenko, 28, … Read More “Five U.S. Citizens Plead Guilty to Helping North Korean IT Workers Infiltrate 136 Companies – The Hacker News” »
The Justice Department notched a few more wins in the fight against North Korean cryptocurrency heists and the regime’s expansive scheme to get remote IT workers hired at U.S. businesses. Officials’ countermeasures to these schemes, which ultimately launder ill-gotten money to North Korea’s government, involve the targeting of U.S.-based facilitators who provide forged or stolen … Read More “DOJ lauds series of gains against North Korean IT worker scheme, crypto thefts – CyberScoop” »
Anthropic made headlines Thursday when it released research claiming that a previously unknown Chinese state-sponsored hacking group used the company’s Claude AI generative AI product to breach at least 30 different organizations. According to Anthropic’s report, the threat actor was able to bypass Claude’s security guardrails using two methods: breaking up the work into discrete … Read More “China’s ‘autonomous’ AI-powered hacking campaign still required a ton of human work – CyberScoop” »
CISA Warns of Active Attacks on Cisco ASA and Firepower Flaws – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

CISA issues an urgent directive for all organizations to patch Cisco ASA and Firepower devices against CVE-2025-20362 and CVE-2025-20333, exploited in the ArcaneDoor campaign. Verify the correct version now! – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
The North Korean threat actors behind the Contagious Interview campaign have once again tweaked their tactics by using JSON storage services to stage malicious payloads. “The threat actors have recently resorted to utilizing JSON storage services like JSON Keeper, JSONsilo, and npoint.io to host and deliver malware from trojanized code projects, with the lure,” NVISO … Read More “North Korean Hackers Turn JSON Services into Covert Malware Delivery Channels – The Hacker News” »
Personal details of Tate galleries job applicants leaked online – Data and computer security | The Guardian

Sensitive information relates to more than 100 individuals and their referees Personal details submitted by applicants for a job at Tate art galleries have been leaked online, exposing their addresses, salaries and the phone numbers of their referees, the Guardian has learned. The records, running to hundreds of pages, appeared on a website unrelated to … Read More “Personal details of Tate galleries job applicants leaked online – Data and computer security | The Guardian” »
Chinese State Hackers Jailbroke Claude AI Code for Automated Breaches – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Anthropic, the developer behind Claude AI, says a Chinese state sponsored group used its model to automate most of a cyber espionage operation against about 30 companies with Claude handling up to 90% of the technical work. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
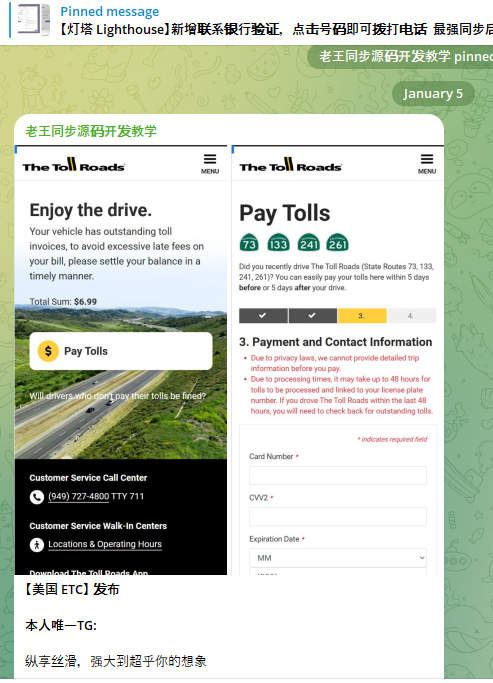
The phishing kit Lighthouse, which has aided text scams like those soliciting victims to pay unpaid road tolls, appears to have been hampered shortly after Google filed a lawsuit aimed at its creators. Google said on Thursday that Lighthouse had been shut down. Two other organizations that have tracked the suspected Chinese operators of Lighthouse … Read More “Google, researchers see signs that Lighthouse text scammers disrupted after lawsuit – CyberScoop” »
Iranian Hackers Launch ‘SpearSpecter’ Spy Operation on Defense & Government Targets – The Hacker News

The Iranian state-sponsored threat actor known as APT42 has been observed targeting individuals and organizations that are of interest to the Islamic Revolutionary Guard Corps (IRGC) as part of a new espionage-focused campaign. The activity, detected in early September 2025 and assessed to be ongoing, has been codenamed SpearSpecter by the Israel National Digital Agency (INDA). … Read More “Iranian Hackers Launch ‘SpearSpecter’ Spy Operation on Defense & Government Targets – The Hacker News” »
Researchers Find Serious AI Bugs Exposing Meta, Nvidia, and Microsoft Inference Frameworks – The Hacker News
Cybersecurity researchers have uncovered critical remote code execution vulnerabilities impacting major artificial intelligence (AI) inference engines, including those from Meta, Nvidia, Microsoft, and open-source PyTorch projects such as vLLM and SGLang. “These vulnerabilities all traced back to the same root cause: the overlooked unsafe use of ZeroMQ (ZMQ) and Python’s pickle deserialization,” – Read More … Read More “Researchers Find Serious AI Bugs Exposing Meta, Nvidia, and Microsoft Inference Frameworks – The Hacker News” »
Chinese Tech Firm Leak Reportedly Exposes State Linked Hacking – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

A massive data leak reportedly at Chinese firm Knownsec (Chuangyu) exposed 12,000 files detailing state-backed ‘cyber weapons’ and spying on over 20 countries. See the details, including 95GB of stolen Indian immigration data. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Anthropic’s Claude Code AI assistant performed 80% to 90% of the tasks involved in a recent cyber-attack campaign, said Anthropic researchers – Read More –
Key Takeaways: 85 active ransomware and extortion groups observed in Q3 2025, reflecting the most decentralized ransomware ecosystem to date. 1,590 victims disclosed across 85 leak sites, showing high, sustained activity despite law-enforcement pressure. 14 new ransomware brands launched this quarter, proving how quickly affiliates reconstitute after takedowns. LockBit’s reappearance with – Read More – … Read More “Ransomware’s Fragmentation Reaches a Breaking Point While LockBit Returns – The Hacker News” »
Akira ransomware has extorted $244M since September 2025, with some attacks exfiltrating data in just two hours, a joint cybersecurity advisory warns – Read More –
Retail giants have a target on their backs. Hackers are picking them apart at a rate rarely seen in other industries. Louis Vuitton and Dior are part of a growing number of household names affected. Their breaches alone may have cost them upwards of $25 million. Moreover, Google has warned that the hacker group that … Read More “The retail sector needs a cybersecurity talent incubator – CyberScoop” »
State-sponsored threat actors from China used artificial intelligence (AI) technology developed by Anthropic to orchestrate automated cyber attacks as part of a “highly sophisticated espionage campaign” in mid-September 2025. “The attackers used AI’s ‘agentic’ capabilities to an unprecedented degree – using AI not just as an advisor, but to execute the cyber attacks themselves,” the … Read More “Chinese Hackers Use Anthropic’s AI to Launch Automated Cyber Espionage Campaign – The Hacker News” »
Google filed a civil lawsuit against 25 individuals accused of ties to a Chinese cyber collective known as the ‘Smishing Triad’ – Read More –
Fortinet FortiWeb Flaw Actively Exploited in the Wild Before Company’s Silent Patch – The Hacker News

Cybersecurity researchers are sounding the alert about an authentication bypass vulnerability in Fortinet Fortiweb WAF that could allow an attacker to take over admin accounts and completely compromise a device. “The watchTowr team is seeing active, indiscriminate in-the-wild exploitation of what appears to be a silently patched vulnerability in Fortinet’s FortiWeb product,” Benjamin Harris, – … Read More “Fortinet FortiWeb Flaw Actively Exploited in the Wild Before Company’s Silent Patch – The Hacker News” »
Every November, International Fraud Awareness Week serves as a global reminder that fraud prevention is not merely a compliance… The post Fraud Awareness: The Untapped Power of HSM appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Posted by Pierre Kim on Nov 13 No message preview for long message of 668188 bytes. – Read More – Full Disclosure
Posted by Apple Product Security via Fulldisclosure on Nov 13 APPLE-SA-11-13-2025-1 Compressor 4.11.1 Compressor 4.11.1 addresses the following issues. Information about the security content is also available at https://support.apple.com/125693. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. Compressor Available for: macOS Sequoia 15.6 and later Impact: … Read More “APPLE-SA-11-13-2025-1 Compressor 4.11.1 – Full Disclosure” »
Re: [FD] : “Glass Cage” – Zero-Click iMessage → Persistent iOS Compromise + Bricking (CVE-2025-24085 / 24201, CNVD-2025-07885) – Full Disclosure
![Re: [FD] : “Glass Cage” – Zero-Click iMessage → Persistent iOS Compromise + Bricking (CVE-2025-24085 / 24201, CNVD-2025-07885) Re: [FD] : “Glass Cage” – Zero-Click iMessage → Persistent iOS Compromise + Bricking (CVE-2025-24085 / 24201, CNVD-2025-07885) – Full Disclosure](https://attackfeed.com/wp-content/uploads/2025/10/fulldisclosure-img-tKo9mS.webp)
Posted by Patrick via Fulldisclosure on Nov 13 Hello Jan, You are completely right and it’s something I warned about early, which is abuse of AI-generated sensationalized headline and fake PoC-s, for fame. I urge the Full Disclosure staff to look into it. Discussions with the individual responsible seem to be fruitless, and this … Read More “Re: [FD] : “Glass Cage” – Zero-Click iMessage → Persistent iOS Compromise + Bricking (CVE-2025-24085 / 24201, CNVD-2025-07885) – Full Disclosure” »
Multiple vulnerabilities have been discovered in Google Android OS, the most severe of which could allow for remote code execution. Android is an operating system developed by Google for mobile devices, including, but not limited to, smartphones, tablets, and watches. Successful exploitation of the most severe of these vulnerabilities could allow for remote code execution. … Read More “Multiple Vulnerabilities in Google Android OS Could Allow for Remote Code Execution – Cyber Security Advisories – MS-ISAC” »
Multiple vulnerabilities have been discovered in Adobe products, the most severe of which could allow for arbitrary code execution. Adobe InDesign is a professional page layout and desktop publishing software used for designing and publishing content for both print and digital media. Adobe InCopy is a professional word processor designed for writers and editors to … Read More “Multiple Vulnerabilities in Adobe Products Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
Multiple vulnerabilities have been discovered in Microsoft products, the most severe of which could allow for remote code execution. Successful exploitation of the most severe of these vulnerabilities could result in an attacker gaining the same privileges as the logged-on user. Depending on the privileges associated with the user, an attacker could then install programs; … Read More “Critical Patches Issued for Microsoft Products, November 11, 2025 – Cyber Security Advisories – MS-ISAC” »
Multiple vulnerabilities have been discovered in Mozilla products, the most severe of which could allow for arbitrary code execution. Mozilla Firefox is a web browser used to access the Internet. Mozilla Firefox ESR is a version of the web browser intended to be deployed in large organizations. Successful exploitation of the most severe of these … Read More “Multiple Vulnerabilities in Mozilla Products Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
How Adversaries Exploit the Blind Spots in Your EASM Strategy – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Internet-facing assets like domains, servers, or networked device endpoints are where attackers look first, probing their target’s infrastructure… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Federal cyber authorities shared new details Thursday about the Akira ransomware group’s techniques, the tools it uses and vulnerabilities it exploits for initial access alongside the release of a joint cybersecurity advisory. Members of the financially motivated group, which initially appeared in March 2023, are associated with other threat groups, including Storm-1567, Howling Scorpius, Punk … Read More “FBI calls Akira ‘top five’ ransomware variant out of 130 targeting US businesses – CyberScoop” »
Russian Hackers Create 4,300 Fake Travel Sites to Steal Hotel Guests’ Payment Data – The Hacker News

A Russian-speaking threat behind an ongoing, mass phishing campaign has registered more than 4,300 domain names since the start of the year. The activity, per Netcraft security researcher Andrew Brandt, is designed to target customers of the hospitality industry, specifically hotel guests who may have travel reservations with spam emails. The campaign is said to … Read More “Russian Hackers Create 4,300 Fake Travel Sites to Steal Hotel Guests’ Payment Data – The Hacker News” »
Scammers Abuse WhatsApp Screen Sharing to Steal OTPs and Funds – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
A fast-spreading threat, known as the screen-sharing scam, is using a simple feature on WhatsApp to steal money… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Washington Post confirms data on nearly 10,000 people stolen from its Oracle environment – CyberScoop

The Washington Post said it, too, was impacted by the data theft and extortion campaign targeting Oracle E-Business Suite customers, compromising human resources data on nearly 10,000 current and former employers and contractors. The company was first alerted to the attack and launched an investigation when a “bad actor” contacted the media company Sept. 29 … Read More “Washington Post confirms data on nearly 10,000 people stolen from its Oracle environment – CyberScoop” »
Operation Endgame Hits Rhadamanthys, VenomRAT, Elysium Malware, seize 1025 servers – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
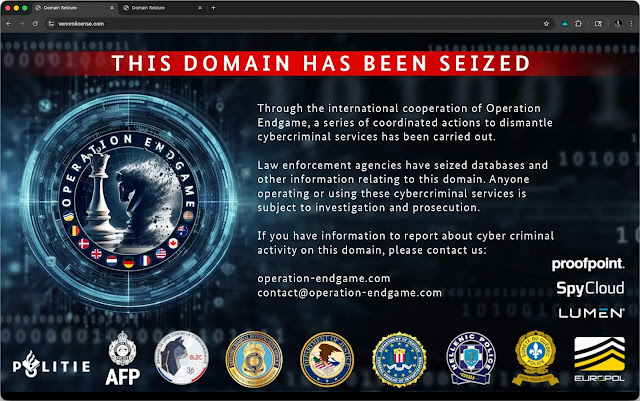
Europol-led Operation Endgame seizes 1,025 servers and arrests a key suspect in Greece, disrupting three major global malware and hacking tools, including Rhadamanthys, VenomRAT and Elysium botnet. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Google is suing more than two dozen unnamed individuals allegedly involved in peddling a popular China-based mobile phishing service that helps scammers impersonate hundreds of trusted brands, blast out text message lures, and convert phished payment card data into mobile wallets from Apple and Google. In a lawsuit filed in the Southern District of New … Read More “Google Sues to Disrupt Chinese SMS Phishing Triad – Krebs on Security” »
Cybersecurity researchers are calling attention to a large-scale spam campaign that has flooded the npm registry with thousands of fake packages since early 2024 as part of a likely financially motivated effort. “The packages were systematically published over an extended period, flooding the npm registry with junk packages that survived in the ecosystem for almost … Read More “Over 67,000 Fake npm Packages Flood Registry in Worm-Like Spam Attack – The Hacker News” »
A new npm worm dubbed “IndonesianFoods” has doubled the number of known malicious packages – Read More –
In a sweeping international crackdown coordinated from Europol’s headquarters, law enforcement agencies from the United States and 10 other countries have disrupted three of the world’s most widely used cybercriminal malware operations. Conducted Nov. 10-13, Operation Endgame focused on neutralizing the Rhadamanthys info-stealing malware, the VenomRAT remote access trojan, and the Elysium botnet — tools … Read More “Operation Endgame targets malware networks in global crackdown – CyberScoop” »
Post Content – Read More – IC3.gov News
An IANS study finds CISO compensation rose 6.7% on average in 2025 while budget growth halved compared to 2024 – Read More –