A Chinese national has been convicted for her role in a fraudulent cryptocurrency scheme after law enforcement authorities in the U.K. confiscated £5.5 billion (about $7.39 billion) during a raid of her home in London. The cryptocurrency seizure, amounting to 61,000 Bitcoin, is believed to be the single largest such effort in the world, the … Read More “U.K. Police Just Seized £5.5 Billion in Bitcoin — The World’s Largest Crypto Bust – The Hacker News” »
The world of enterprise technology is undergoing a dramatic shift. Gen-AI adoption is accelerating at an unprecedented pace, and SaaS vendors are embedding powerful LLMs directly into their platforms. Organizations are embracing AI-powered applications across every function, from marketing and development to finance and HR. This transformation unlocks innovation and efficiency, but it also – … Read More “Evolving Enterprise Defense to Secure the Modern AI Supply Chain – The Hacker News” »
CISA Sounds Alarm on Critical Sudo Flaw Actively Exploited in Linux and Unix Systems – The Hacker News

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a critical security flaw impacting the Sudo command-line utility for Linux and Unix-like operating systems to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild. The vulnerability in question is CVE-2025-32463 (CVSS score: 9.3), which affects Sudo versions prior … Read More “CISA Sounds Alarm on Critical Sudo Flaw Actively Exploited in Linux and Unix Systems – The Hacker News” »
Compliance is not a regulatory imperative anymore, neither is it a strategic, confidence, strength, and growth enabler in digital… The post Compliance Turns Digital Finance into Confidence appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
The Department of Homeland Security estimated over the weekend that it would send home about two-thirds of employees at the Cybersecurity and Infrastructure Security Agency in the event of a government shutdown. It’s the first time that the second Trump administration has released its contingency plan in response to what would happen if Congress doesn’t … Read More “Two-thirds of CISA personnel could be sent home under shutdown – CyberScoop” »
Dutch Teens Arrested Over Alleged Spying for Pro-Russian Hackers – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Dutch authorities arrest two teens recruited by pro-Russian hackers for spying missions. Learn how Russia is using disposable agents for sabotage across Europe. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Authorities arrested 260 cybercrime suspects during a two-week operation spanning 14 African countries, Interpol announced Friday. The globally coordinated summertime crackdown dubbed “Operation Contender 3.0” targeted criminal networks that facilitated romance scams and sextortion, officials said. Interpol said total losses attributed to the scam syndicates amounted to about $2.8 million, involving almost 1,500 victims. Authorities … Read More “Interpol operation disrupts romance scam and sextortion networks in Africa – CyberScoop” »
Threat actors have been observed using seemingly legitimate artificial intelligence (AI) tools and software to sneakily slip malware for future attacks on organizations worldwide. According to Trend Micro, the campaign is using productivity or AI-enhanced tools to deliver malware targeting various regions, including Europe, the Americas, and the Asia, Middle East, and Africa (AMEA) region. … Read More “EvilAI Malware Masquerades as AI Tools to Infiltrate Global Organizations – The Hacker News” »
While the exact suspicion was yet to be revealed it is linked to “foreign interference” – Read More –
Harrods Data Breach: 430,000 Customer Records Stolen Via Third-Party Attack – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Luxury retailer Harrods confirms 430,000 customer records (names, contacts) were stolen from a third-party provider in the latest UK retail cyberattack wave. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Microsoft Threat Intelligence stopped an AI-driven credential phishing campaign using SVG files disguised as PDFs – Read More –
The Five Eyes countries, Germany and the Netherlands are launching a standard for managing OT security – Read More –
⚡ Weekly Recap: Cisco 0-Day, Record DDoS, LockBit 5.0, BMC Bugs, ShadowV2 Botnet & More – The Hacker News

Cybersecurity never stops—and neither do hackers. While you wrapped up last week, new attacks were already underway. From hidden software bugs to massive DDoS attacks and new ransomware tricks, this week’s roundup gives you the biggest security moves to know. Whether you’re protecting key systems or locking down cloud apps, these are the updates you … Read More “⚡ Weekly Recap: Cisco 0-Day, Record DDoS, LockBit 5.0, BMC Bugs, ShadowV2 Botnet & More – The Hacker News” »
Accelerate Crypto Success: Why a Canadian Crypto License Is Your Launchpad to Growth – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

As the digital asset market matures and regulators worldwide work to set clear standards, one fact has become… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
DarkCloud Infostealer Relaunched to Grab Credentials, Crypto and Contacts – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

eSentire TRU analyses the new DarkCloud V4.2 infostealer, rewritten in VB6. Find out how the malware steals browser data, crypto, and contacts via targeted phishing. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Security leaders are embracing AI for triage, detection engineering, and threat hunting as alert volumes and burnout hit breaking points. A comprehensive survey of 282 security leaders at companies across industries reveals a stark reality facing modern Security Operations Centers: alert volumes have reached unsustainable levels, forcing teams to leave critical threats uninvestigated. You can … Read More “The State of AI in the SOC 2025 – Insights from Recent Study – The Hacker News” »
A critical, longstanding piece of America’s cybersecurity infrastructure is perilously close to vanishing overnight. On Tuesday, the Cybersecurity Information Sharing Act (CISA) expires — and with it, the legal protections that enable countless organizations to share threat intelligence with the federal government. Without swift congressional action, we risk dismantling years of progress in collaborative cyber … Read More “Expired protections, exposed networks: The stakes of CISA’s sunset – CyberScoop” »
Recruitment and retention remain a significant challenge for security teams, amid growing pressures on cyber professionals – Read More –
If you can’t see your entire operational technology environment, you can’t defend it. New guidance from the NCSC will help you gain that visibility. – Read More – NCSC Feed
Cybersecurity researchers have discovered what has been described as the first-ever instance of a Model Context Protocol (MCP) server spotted in the wild, raising software supply chain risks. According to Koi Security, a legitimate-looking developer managed to slip in rogue code within an npm package called “postmark-mcp” that copied an official Postmark Labs library of … Read More “First Malicious MCP Server Found Stealing Emails in Rogue Postmark-MCP Package – The Hacker News” »
Microsoft is calling attention to a new phishing campaign primarily aimed at U.S.-based organizations that has likely utilized code generated using large language models (LLMs) to obfuscate payloads and evade security defenses. “Appearing to be aided by a large language model (LLM), the activity obfuscated its behavior within an SVG file, leveraging business terminology and … Read More “Microsoft Flags AI-Driven Phishing: LLM-Crafted SVG Files Outsmart Email Security – The Hacker News” »
Akira ransomware attacks on SonicWall SSL VPN appliances are bypassing its MFA for rapid deployment – Read More –
Department store Harrods has notified e-commerce customers of a major data breach – Read More –
ThreatBook Launches Best-of-Breed Advanced Threat Intelligence Solution – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Singapore, Singapore, 29th September 2025, CyberNewsWire – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
India digital transformation of the financial ecosystem, the Reserve Bank of India (RBI) has announced its Cybersecurity Mandates 2025,… The post RBI’s Cybersecurity Mandates 2025: Securing India’s Digital Banks appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Medusa Ransomware Claims Comcast Data Breach, Demands $1.2M – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Medusa ransomware group claims 834 GB data theft from Comcast, demanding $1.2M ransom while sharing screenshots and file listings. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
On September 25, the Cyber Threat Alert Level was evaluated and is remaining at Blue (Guarded) due to vulnerabilities in Google, WatchGuard, GoAnywhere, and SolarWinds products. On September 18, the MS-ISAC released an advisory for multiple vulnerabilities in Google Chrome, the most severe of which could allow for arbitrary code execution. On September 19, the … Read More “Threat Level – GUARDED – Cyber Threat Alert” »
WhatsApp Scams: The Latest Way Criminals Attack – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.

WhatsApp has become one of the most popular applications, with over 2 billion individuals using it for communication with friends and family. Unfortunately, this makes WhatsApp an easy way for cyber criminals to target unsuspecting individuals. Since the app is used for friendly methods, many assume that contact via WhatsApp can be trusted. It can’t … Read More “WhatsApp Scams: The Latest Way Criminals Attack – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.” »
China-Linked PlugX and Bookworm Malware Attacks Target Asian Telecom and ASEAN Networks – The Hacker News

Telecommunications and manufacturing sectors in Central and South Asian countries have emerged as the target of an ongoing campaign distributing a new variant of a known malware called PlugX (aka Korplug or SOGU). “The new variant’s features overlap with both the RainyDay and Turian backdoors, including abuse of the same legitimate applications for DLL side-loading, … Read More “China-Linked PlugX and Bookworm Malware Attacks Target Asian Telecom and ASEAN Networks – The Hacker News” »
Hackers Use Fake Invoices to Spread XWorm RAT via Office Files – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
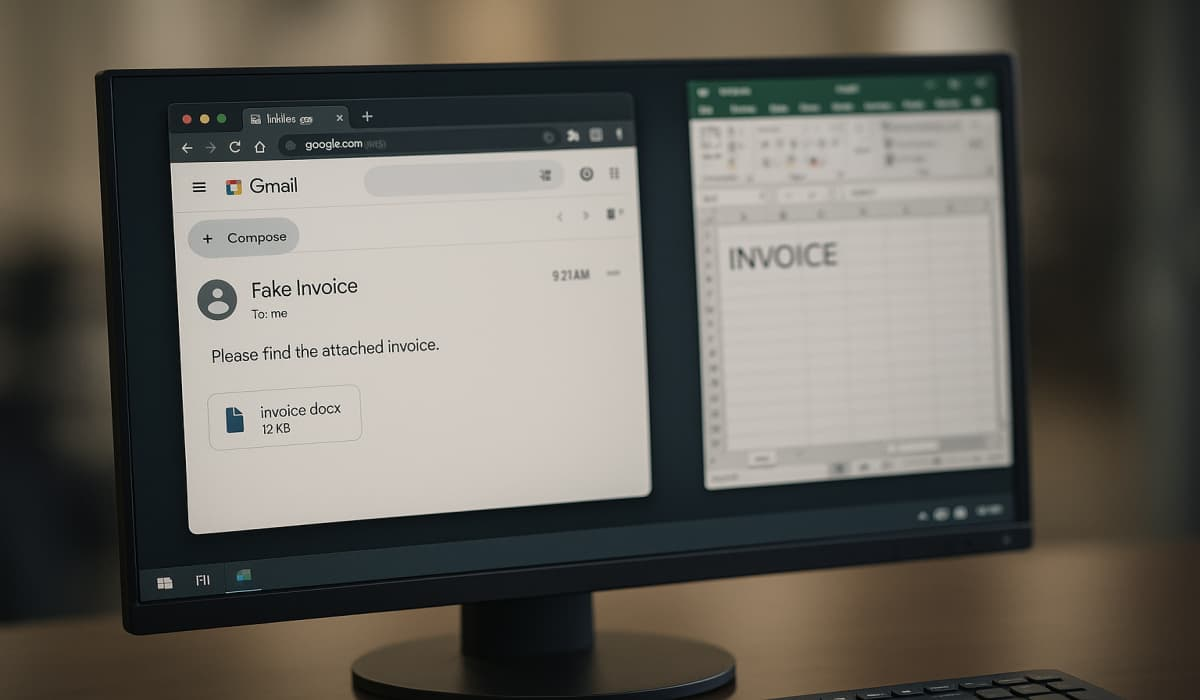
Hackers are sending fake invoice emails with malicious Office files that install the XWorm RAT on Windows systems, allowing full remote access and data theft. Learn how the shellcode and process injection are used to steal data, and how to stay safe from this persistent threat. – Read More – Hackread – Latest Cybersecurity, Hacking … Read More “Hackers Use Fake Invoices to Spread XWorm RAT via Office Files – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto” »
The United Nations is making a push to more directly influence global policy on artificial intelligence, including the promotion of policymaking and technical standards around “safe, secure and trustworthy” AI. Last month, the world body finalized plans to create a new expert panel focused on developing scientific, technical and policy standards for the emerging technology. … Read More “UN seeks to build consensus on ‘safe, secure and trustworthy’ AI – CyberScoop” »
Google Ads Used to Spread Trojan Disguised as TradingView Premium – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Bitdefender warns that the TradingView Premium ad scam now targets Google ads and YouTube, hijacking verified channels to spread spyware. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
A new campaign has been observed impersonating Ukrainian government agencies in phishing attacks to deliver CountLoader, which is then used to drop Amatera Stealer and PureMiner. “The phishing emails contain malicious Scalable Vector Graphics (SVG) files designed to trick recipients into opening harmful attachments,” Fortinet FortiGuard Labs researcher Yurren Wan said in a report shared … Read More “Researchers Expose SVG and PureRAT Phishing Threats Targeting Ukraine and Vietnam – The Hacker News” »
Fake Ukraine Police Notices Spread New Amatera Stealer and PureMiner – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
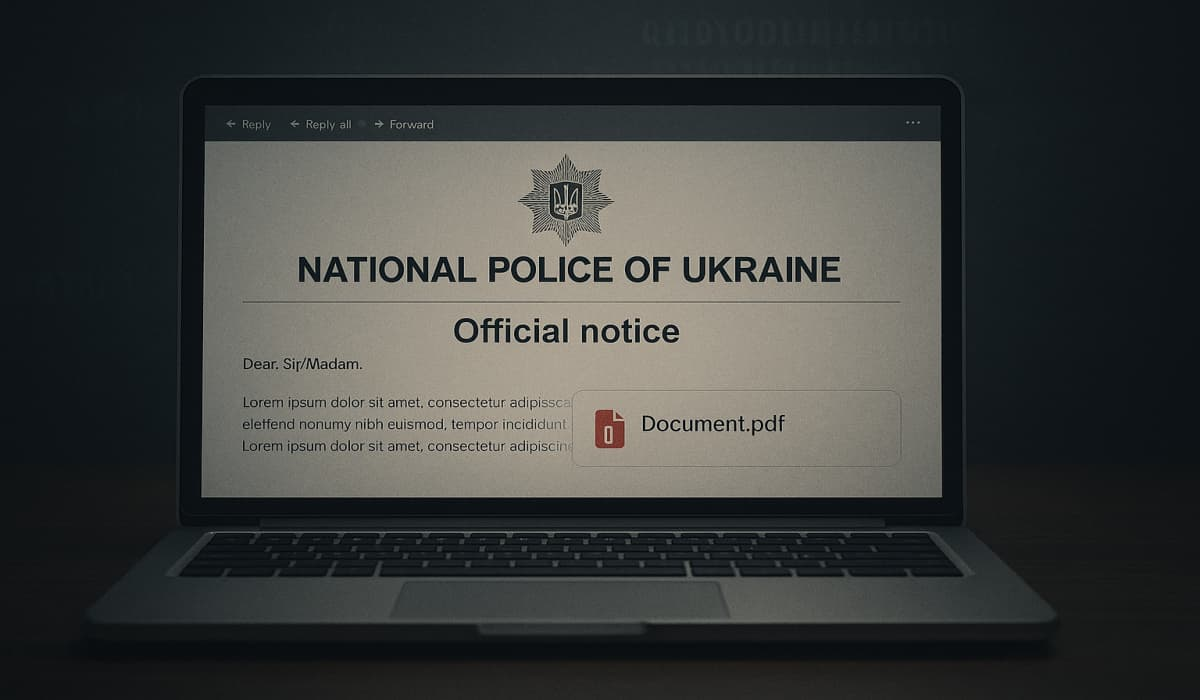
FortiGuard Labs exposes a high-severity phishing campaign impersonating the National Police of Ukraine to deliver Amatera Stealer (data theft) and PureMiner (cryptojacking) to Windows PCs. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Threat intelligence professionals have a sense of foreboding about a maximum-severity vulnerability Forta disclosed last week in its file-transfer service GoAnywhere MFT, as they steel themselves for active exploitation and signs of compromise. Forta has not declared the defect actively exploited and did not answer questions to that effect from CyberScoop. Yet, researchers at watchTowr … Read More “Worries mount over max-severity GoAnywhere defect – CyberScoop” »
The Singapore police said Facebook is the top platform for online scams in the country – Read More –
New COLDRIVER Malware Campaign Joins BO Team and Bearlyfy in Russia-Focused Cyberattacks – The Hacker News
The Russian advanced persistent threat (APT) group known as COLDRIVER has been attributed to a fresh round of ClickFix-style attacks designed to deliver two new “lightweight” malware families tracked as BAITSWITCH and SIMPLEFIX. Zscaler ThreatLabz, which detected the new multi-stage ClickFix campaign earlier this month, described BAITSWITCH as a downloader that ultimately drops SIMPLEFIX, a … Read More “New COLDRIVER Malware Campaign Joins BO Team and Bearlyfy in Russia-Focused Cyberattacks – The Hacker News” »
Archer Health Data Leak Exposes 23GB of Medical Records – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

California-based Archer Health exposed 23GB of patient records, including SSNs, IDs, and medical files, after an unprotected database was found online. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Car makers don’t trust blueprints. They smash prototypes into walls. Again and again. In controlled conditions. Because design specs don’t prove survival. Crash tests do. They separate theory from reality. Cybersecurity is no different. Dashboards overflow with “critical” exposure alerts. Compliance reports tick every box. But none of that proves what matters most to a … Read More “Crash Tests for Security: Why BAS Is Proof of Defense, Not Assumptions – The Hacker News” »
An attack campaign has been identified which exploits vulnerabilities in Cisco Adaptive Security Appliance software – Read More –
The effort, named Operation Contender 3.0, led to the arrest of 260 suspected cybercriminals – Read More –
Cybersecurity researchers have discovered an updated version of a known Apple macOS malware called XCSSET that has been observed in limited attacks. “This new variant of XCSSET brings key changes related to browser targeting, clipboard hijacking, and persistence mechanisms,” the Microsoft Threat Intelligence team said in a Thursday report. “It employs sophisticated encryption and obfuscation … Read More “New macOS XCSSET Variant Targets Firefox with Clipper and Persistence Module – The Hacker News” »
Cybersecurity company watchTowr Labs has disclosed that it has “credible evidence” of active exploitation of the recently disclosed security flaw in Fortra GoAnywhere Managed File Transfer (MFT) software as early as September 10, 2025, a whole week before it was publicly disclosed. “This is not ‘just’ a CVSS 10.0 flaw in a solution long favored … Read More “Fortra GoAnywhere CVSS 10 Flaw Exploited as 0-Day a Week Before Public Disclosure – The Hacker News” »
JLR said it is in a position to start clearing its backlog of payments for suppliers, while its parts logistics center is returning to full operations – Read More –
Trend Micro highlighted the new LockBit version’s improved technical improvements and cross-platform functionality compared to previous iterations – Read More –
The financial ecosystem in the world is on the edge of new unprecedented changes. We all enter a new… The post Charting a new decade of shared progress in global finance appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
The U.K. National Cyber Security Centre (NCSC) has revealed that threat actors have exploited the recently disclosed security flaws impacting Cisco firewalls as part of zero-day attacks to deliver previously undocumented malware families like RayInitiator and LINE VIPER. “The RayInitiator and LINE VIPER malware represent a significant evolution on that used in the previous campaign, … Read More “Cisco ASA Firewall Zero-Day Exploits Deploy RayInitiator and LINE VIPER Malware – The Hacker News” »
The Cybersecurity and Infrastructure Security Agency acknowledged it’s yet to get a complete handle on the scope and impact of attacks involving Cisco zero-day vulnerabilities that prompted it to release an emergency directive Thursday. The attack timeline dates back almost a year, according to an investigation Cisco and federal authorities did behind the scenes to … Read More “CISA says it observed nearly year-old activity tied to Cisco zero-day attacks – CyberScoop” »
SEC Consult SA-20250925-0 :: Multiple Vulnerabilities in iMonitorSoft EAM employee monitoring #CVE-2025-10540 #CVE-2025-10541 #CVE-2025-10542 – Full Disclosure

Posted by SEC Consult Vulnerability Lab via Fulldisclosure on Sep 25 SEC Consult Vulnerability Lab Security Advisory < 20250925-0 > ======================================================================= title: Multiple Vulnerabilities product: iMonitorSoft EAM vulnerable version: iMonitor EAM 9.6394 fixed version: – CVE number: CVE-2025-10540, CVE-2025-10541, CVE-2025-10542 impact: Critical homepage:… – Read More – Full Disclosure
Posted by Antoine Martin via Fulldisclosure on Sep 25 1) About Xpra Xpra is known as “screen for X11”. https://xpra.org/ “Xpra forwards and synchronizes many extra desktop features, which allows remote applications to integrate transparently into the client’s desktop environment: audio input and output, printers, clipboard, system trays, notifications, webcams, etc.” 2) Vulnerability Using … Read More “xpra server information disclosure – Full Disclosure” »