Ransomware payments dropped 35% in 2024 – CyberScoop
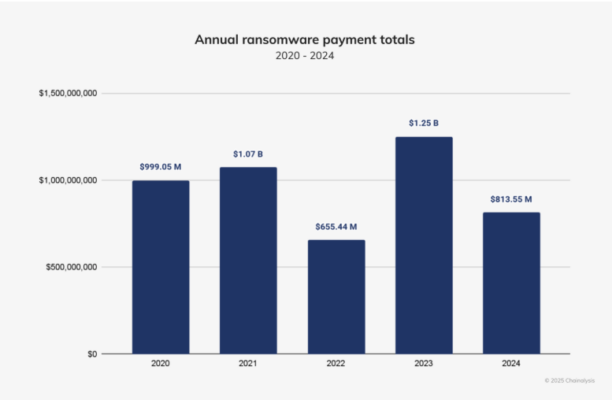
Ransomware payments saw a dramatic 35% drop last year compared to 2023, even as the overall frequency of ransomware attacks increased, according to a new report released by blockchain analysis firm Chainalysis.
The considerable decline in extortion payments is somewhat surprising, given that other cybersecurity firms have claimed that 2024 saw the most ransomware activity to date. Chainalysis itself warned in its mid-year report that 2024’s activity was on pace to reach new heights, but attacks in the second half of the year tailed off.
The total amount in payments that Chainalysis tracked in 2024 was $812.55 million, down from 2023’s mark of $1.25 billion.
“Despite its small half-over-half (HoH) increase, we expected 2024 to surpass 2023’s totals by the end of the year,” the company wrote on its website. “Fortunately, however, payment activity slowed after July 2024 by approximately 34.9%. This slowdown is similar to the HoH decline in ransom payments since 2021 and the overall decline during H2 2024 in some types of crypto-related crime, such as stolen funds. Notably, the decline this year is more pronounced than in the last three years.”
The disruption of major ransomware groups, such as LockBit and ALPHV/BlackCat, were key to the reduction in ransomware payments. Operations spearheaded by agencies like the United Kingdom’s National Crime Agency (NCA) and the Federal Bureau of Investigation (FBI) caused significant declines in LockBit activity, while ALPHV/BlackCat essentially rug-pulled its affiliates and disappeared after its attack on Change Healthcare.
As the industry has seen in past years, ransomware groups often fill the market after the heads of the pack have been dismantled by law enforcement. However, when LockBit and BlackCat disappeared, a well-known ransomware group did not immediately take the mantle. Instead, smaller groups took advantage of the situation, focusing on small to medium-sized targets and asking for small ransoms, according to Chainalysis’ report.
Additionally, the company says more organizations have become stronger against attacks, with many choosing not to pay a ransom and instead using better cybersecurity practices and backups to recover from these incidents.
Even with the drop in payments, there were ransomware-as-a-service groups like Akira and INC, that caught researchers’ attention due to their use of rebranded, leaked, or purchased code. Furthermore, these groups have proven adept at exploiting vulnerabilities, particularly in enterprise environments, demonstrating a shift toward speed and aggression in their methods.
Chainalysis also says the financial transactions associated with ransomware shifted due to law enforcement actions. Ransomware operators showed a decreased reliance on mixers for obscuring fund movements, instead using cross-chain bridges and centralized exchanges for off-ramping funds.
The company also notes that actors are letting ransomware sit in wallets and refraining from moving any money, partly out of fear they are being watched by law enforcement.
“It’s worth calling out the substantial volumes of funds being held in personal wallets,” the report reads. “Curiously, ransomware operators, a primarily financially motivated group, are abstaining from cashing out more than ever.”
You can read the full report on Chainalysis’ website.
The post Ransomware payments dropped 35% in 2024 appeared first on CyberScoop.
–
Read More – CyberScoop
