An international effort to create voluntary standards for the commercial cyber intrusion industry is wrestling with questions like who they should apply to, how to incentivize and measure compliance and what to do with companies with a checkered past. The first round of the Pall Mall Process focused on a code of conduct for government … Read More “Industry, government, nonprofits weigh voluntary rules for commercial hacking tools – CyberScoop” »
New Fake CAPTCHA Scam Abuses Microsoft Tools to Install Amatera Stealer – Hackread – Cybersecurity News, Data Breaches, AI, and More
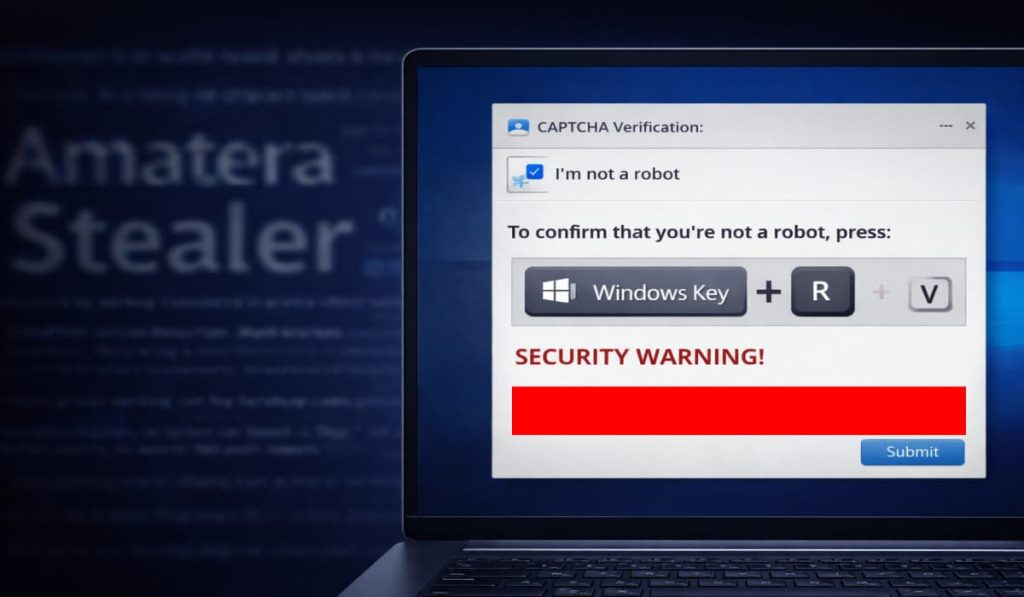
Another day, another fake CAPTCHA scam, but this one abuses Microsoft’s signed tools. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The US law firm Hagens Berman will lead a class action lawsuit against Coupang over security failures that led to a June 2025 data breach – Read More –
⚡ Weekly Recap: Firewall Flaws, AI-Built Malware, Browser Traps, Critical CVEs & More – The Hacker News

Security failures rarely arrive loudly. They slip in through trusted tools, half-fixed problems, and habits people stop questioning. This week’s recap shows that pattern clearly. Attackers are moving faster than defenses, mixing old tricks with new paths. “Patched” no longer means safe, and every day, software keeps becoming the entry point. What follows is a … Read More “⚡ Weekly Recap: Firewall Flaws, AI-Built Malware, Browser Traps, Critical CVEs & More – The Hacker News” »
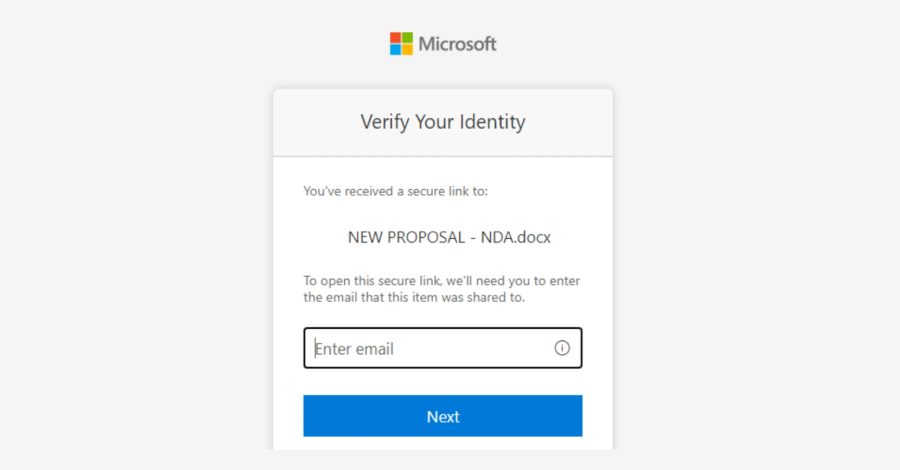
Threat actors posing as IT support teams use phishing kits to generate fake login sites in real-time to trick victims into handing over credentials – Read More –
$6,000 “Stanley” Toolkit Sold on Russian Forums Fakes Secure URLs in Chrome – Hackread – Cybersecurity News, Data Breaches, AI, and More

Say hello to Stanley, a new malicious toolkit that guarantees bypassing Google’s Chrome Web Store review process. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
If there’s a constant in cybersecurity, it’s that adversaries are always innovating. The rise of offensive AI is transforming attack strategies and making them harder to detect. Google’s Threat Intelligence Group, recently reported on adversaries using Large Language Models (LLMs) to both conceal code and generate malicious scripts on the fly, letting malware shape-shift in … Read More “Winning Against AI-Based Attacks Requires a Combined Defensive Approach – The Hacker News” »
A destructive cyber attack targeting Poland’s energy sector has been linked to Russian APT group Sandworm – Read More –
Konni Hackers Deploy AI-Generated PowerShell Backdoor Against Blockchain Developers – The Hacker News

The North Korean threat actor known as Konni has been observed using PowerShell malware generated using artificial intelligence (AI) tools to target developers and engineering teams in the blockchain sector. The phishing campaign has targeted Japan, Australia, and India, highlighting the adversary’s expansion of the targeting scope beyond South Korea, Russia, Ukraine, and European nations, … Read More “Konni Hackers Deploy AI-Generated PowerShell Backdoor Against Blockchain Developers – The Hacker News” »
7 Top Endpoint Security Platforms for 2026 – Hackread – Cybersecurity News, Data Breaches, AI, and More

Endpoints remain primary entry for attacks. In 2026, endpoint platforms must deliver behavior context, automation, investigations, and integrations. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
FBI Accessed Windows Laptops After Microsoft Shared BitLocker Recovery Keys – Hackread – Cybersecurity News, Data Breaches, AI, and More

If you are using a Windows PC, your privacy and security are nothing short of a myth, and this incident proves it. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
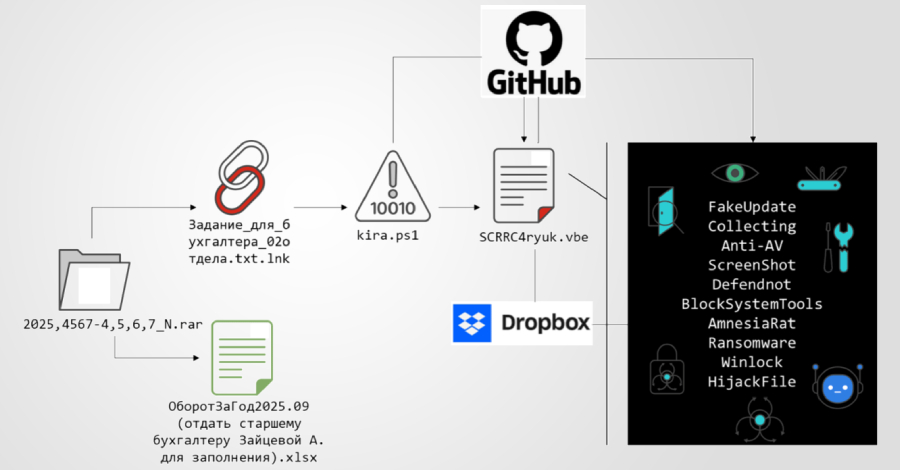
A new multi-stage phishing campaign has been observed targeting users in Russia with ransomware and a remote access trojan called Amnesia RAT. “The attack begins with social engineering lures delivered via business-themed documents crafted to appear routine and benign,” Fortinet FortiGuard Labs researcher Cara Lin said in a technical breakdown published this week. “These documents … Read More “Multi-Stage Phishing Campaign Targets Russia with Amnesia RAT and Ransomware – The Hacker News” »
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added a critical security flaw affecting Broadcom VMware vCenter Server that was patched in June 2024 to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild. The vulnerability in question is CVE-2024-37079 (CVSS score: 9.8), which refers to a heap … Read More “CISA Adds Actively Exploited VMware vCenter Flaw CVE-2024-37079 to KEV Catalog – The Hacker News” »
Who Approved This Agent? Rethinking Access, Accountability, and Risk in the Age of AI Agents – The Hacker News

AI agents are accelerating how work gets done. They schedule meetings, access data, trigger workflows, write code, and take action in real time, pushing productivity beyond human speed across the enterprise. Then comes the moment every security team eventually hits: “Wait… who approved this?” Unlike users or applications, AI agents are often deployed quickly, shared … Read More “Who Approved This Agent? Rethinking Access, Accountability, and Risk in the Age of AI Agents – The Hacker News” »
The Russian nation-state hacking group known as Sandworm has been attributed to what has been described as the “largest cyber attack” targeting Poland’s power system in the last week of December 2025. The attack was unsuccessful, the country’s energy minister, Milosz Motyka, said last week. “The command of the cyberspace forces has diagnosed in the … Read More “New DynoWiper Malware Used in Attempted Sandworm Attack on Polish Power Sector – The Hacker News” »
149M Logins from Roblox, TikTok, Netflix, Crypto Wallets Found Online – Hackread – Cybersecurity News, Data Breaches, AI, and More

Another day, another trove of login credentials in plain text found online. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Venezuelan Nationals Face Deportation After Multi State ATM Jackpotting Scheme – Hackread – Cybersecurity News, Data Breaches, AI, and More

According to authorities, both suspects were in the United States unlawfully. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Halo Security Achieves SOC 2 Type II Compliance, Demonstrating Sustained Security Excellence Over Time – Hackread – Cybersecurity News, Data Breaches, AI, and More

Halo Security, a leading provider of external attack surface management and penetration testing services, today announced it has… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added four security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild. The list of vulnerabilities is as follows – CVE-2025-68645 (CVSS score: 8.8) – A PHP remote file inclusion vulnerability in Synacor Zimbra Collaboration Suite (ZCS) that … Read More “CISA Updates KEV Catalog with Four Actively Exploited Software Vulnerabilities – The Hacker News” »
Open letter by NHS technology leaders outlines plans to identify risks to software supply chain security across health and social are system – Read More –
ShinyHunters Leak Alleged Data of Millions From SoundCloud, Crunchbase and Betterment – Hackread – Cybersecurity News, Data Breaches, AI, and More
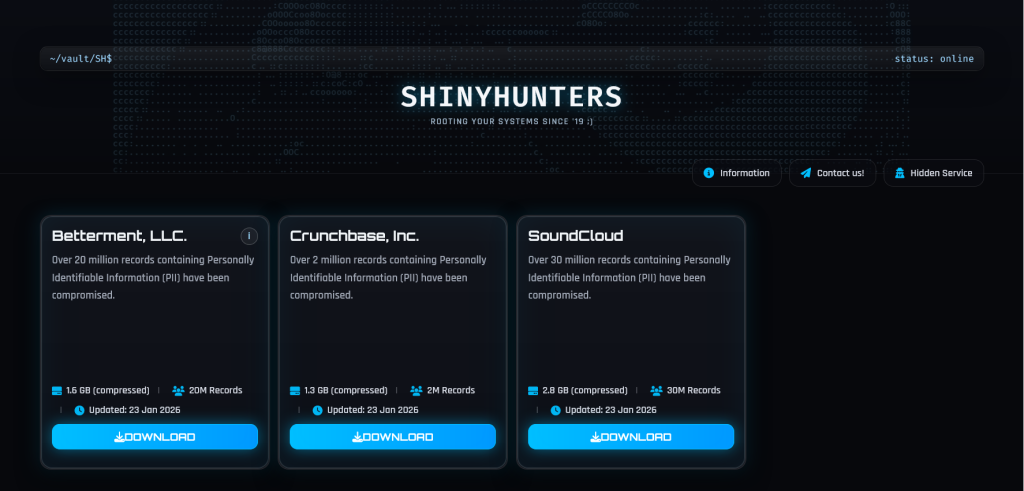
ShinyHunters claim more data breaches and leaks are coming soon! – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Fortinet Confirms Active FortiCloud SSO Bypass on Fully Patched FortiGate Firewalls – The Hacker News

Fortinet has officially confirmed that it’s working to completely plug a FortiCloud SSO authentication bypass vulnerability following reports of fresh exploitation activity on fully-patched firewalls. “In the last 24 hours, we have identified a number of cases where the exploit was to a device that had been fully upgraded to the latest release at the … Read More “Fortinet Confirms Active FortiCloud SSO Bypass on Fully Patched FortiGate Firewalls – The Hacker News” »
Phishing Attack Uses Stolen Credentials to Install LogMeIn RMM for Persistent Access – The Hacker News
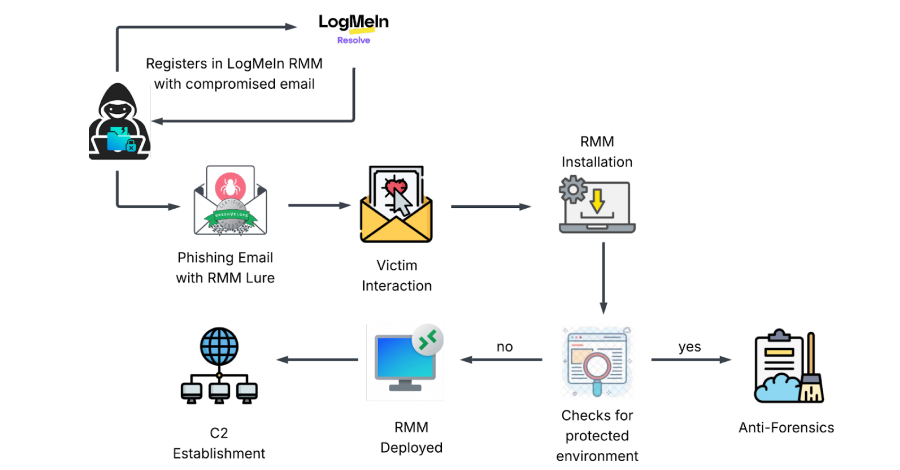
Cybersecurity researchers have disclosed details of a new dual-vector campaign that leverages stolen credentials to deploy legitimate Remote Monitoring and Management (RMM) software for persistent remote access to compromised hosts. “Instead of deploying custom viruses, attackers are bypassing security perimeters by weaponizing the necessary IT tools that administrators trust,” KnowBe4 Threat – Read More – … Read More “Phishing Attack Uses Stolen Credentials to Install LogMeIn RMM for Persistent Access – The Hacker News” »
TikTok on Friday officially announced that it formed a joint venture that will allow the hugely popular video-sharing application to continue operating in the U.S. The new venture, named TikTok USDS Joint Venture LLC, has been established in compliance with the Executive Order signed by U.S. President Donald Trump in September 2025, the platform said. … Read More “TikTok Forms U.S. Joint Venture to Continue Operations Under 2025 Executive Order – The Hacker News” »
Under Armour said there is no evidence at this point to suggest the incident affected systems used to process payments or store customer passwords – Read More –
Microsoft has warned of a multi‑stage adversary‑in‑the‑middle (AitM) phishing and business email compromise (BEC) campaign targeting multiple organizations in the energy sector. “The campaign abused SharePoint file‑sharing services to deliver phishing payloads and relied on inbox rule creation to maintain persistence and evade user awareness,” the Microsoft Defender Security Research Team said. – Read More … Read More “Microsoft Flags Multi-Stage AitM Phishing and BEC Attacks Targeting Energy Firms – The Hacker News” »
Day 3 of Pwn2Own Automotive 2026 is here – the final push. The world’s top security researchers return for their last shots at the latest automotive targets. After two days, $955,750 awarded for 66 unique 0-day vulnerabilities, and the Master of Pwn leaderboard has a clear frontrunner as the competition heads into its final stretch. … Read More “Pwn2Own Automotive 2026 – Day Three Results and the Master of Pwn – Zero Day Initiative – Blog” »
Google to Pay $8.25M Settlement Over Child Data Tracking in Play Store – Hackread – Cybersecurity News, Data Breaches, AI, and More
Is your child’s data safe? Google settles for $8.25M over claims it tracked kids under 13 without parental… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A Russian national pleaded guilty to leading a ransomware conspiracy that targeted at least 50 victims during a four-year period ending in August 2022. Ianis Aleksandrovich Antropenko began participating in ransomware attacks before moving to the United States, but conducted many of his crimes while living in Florida and California, where he’s been out on … Read More “Leader of ransomware crew pleads guilty to four-year crime spree – CyberScoop” »
A nonprofit is suing the federal government for records surrounding a data sharing agreement between the Transportation Security Administration and Immigrations and Customs Enforcement that saw domestic travel data used for immigration enforcement. Government watchdog group American Oversight filed suit against the agencies Thursday in the U.S. District Court for the District of Columbia, a … Read More “Watchdog group sues for TSA data sharing agreement with ICE – CyberScoop” »
Cybersecurity researchers have disclosed details of a new ransomware family called Osiris that targeted a major food service franchisee operator in Southeast Asia in November 2025. The attack leveraged a malicious driver called POORTRY as part of a known technique referred to as bring your own vulnerable driver (BYOVD) to disarm security software, the Symantec … Read More “New Osiris Ransomware Emerges as New Strain Using POORTRY Driver in BYOVD Attack – The Hacker News” »
A vulnerability has been discovered in Cisco Unified Communications Products which could allow for remote code execution. Cisco Unified Communications (UC) Products are an integrated suite of IP-based hardware and software that combine voice, video, messaging, and data into a single platform. Successful exploitation of this vulnerability could allow for remote code execution as root, … Read More “A Vulnerability in Cisco Unified Communications Products Could Allow for Remote Code Execution – Cyber Security Advisories – MS-ISAC” »
Hackers Are Using LinkedIn DMs and PDF Tools to Deploy Trojans – Hackread – Cybersecurity News, Data Breaches, AI, and More
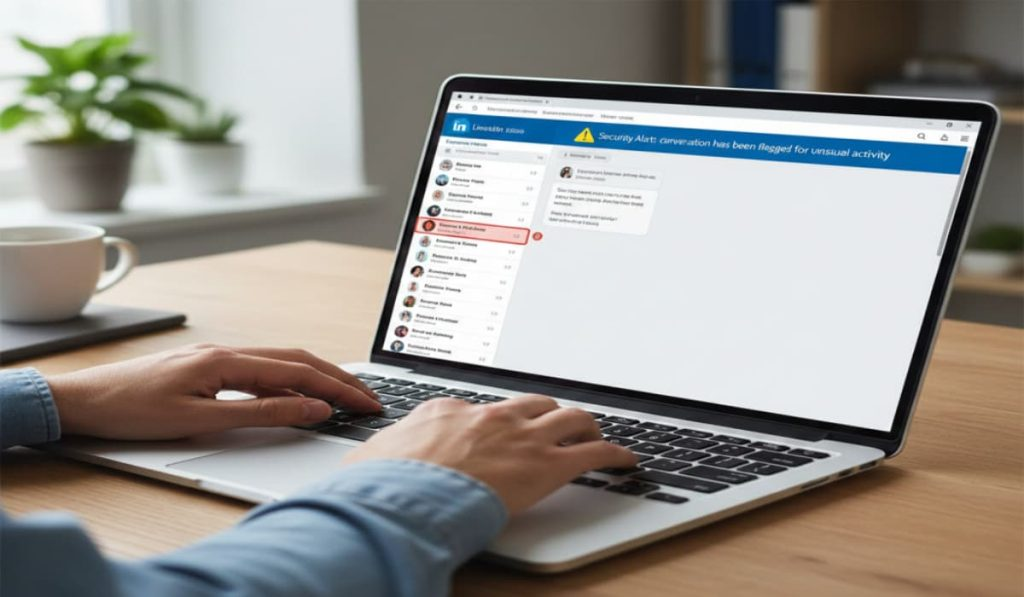
That LinkedIn message pretending to be job offer could just be malwre. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Researchers find Jordan government used Cellebrite phone-cracking tech against activists – CyberScoop

Jordanian authorities used Cellebrite phone-cracking technology to access the devices of domestic activists and human rights defenders and then extract information from them, according to an investigation published Thursday. The nonconsensual access stood in conflict with international human rights treaties that Jordan ratified, the University of Toronto’s Citizen Lab investigation determined, prompting the research organization … Read More “Researchers find Jordan government used Cellebrite phone-cracking tech against activists – CyberScoop” »
Critical GNU InetUtils telnetd Flaw Lets Attackers Bypass Login and Gain Root Access – The Hacker News

A critical security flaw has been disclosed in the GNU InetUtils telnet daemon (telnetd) that went unnoticed for nearly 11 years. The vulnerability, tracked as CVE-2026-24061, is rated 9.8 out of 10.0 on the CVSS scoring system. It affects all versions of GNU InetUtils from version 1.9.3 up to and including version 2.7. “Telnetd in … Read More “Critical GNU InetUtils telnetd Flaw Lets Attackers Bypass Login and Gain Root Access – The Hacker News” »
Critical vulnerability in Appsmith allows account takeover via flawed password reset process – Read More –
ThreatsDay Bulletin: Pixel Zero-Click, Redis RCE, China C2s, RAT Ads, Crypto Scams & 15+ Stories – The Hacker News

Most of this week’s threats didn’t rely on new tricks. They relied on familiar systems behaving exactly as designed, just in the wrong hands. Ordinary files, routine services, and trusted workflows were enough to open doors without forcing them. What stands out is how little friction attackers now need. Some activity focused on quiet reach … Read More “ThreatsDay Bulletin: Pixel Zero-Click, Redis RCE, China C2s, RAT Ads, Crypto Scams & 15+ Stories – The Hacker News” »
Security flaw in RealHomes CRM plugin allowed file uploads; patches released for 30,000+ sites – Read More –
VoidLink Malware Puts Cloud Systems on High Alert With Custom Built Attacks – Hackread – Cybersecurity News, Data Breaches, AI, and More

Sysdig TRT analysis reveals VoidLink as a revolutionary Linux threat. Using Serverside Rootkit Compilation and Zig code, it targets AWS and Azure with adaptive stealth. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Phoney email alerts suggest users need to backup their LastPass accounts within 24 hours. LastPass says it would never require this action from users – Read More –
VulnCheck analysts found that vulnerabilities exploited before being publicly disclosed rose from 23.6% in 2024 to 28.96% in 2025 – Read More –
Security teams at agile, fast-growing companies often have the same mandate: secure the business without slowing it down. Most teams inherit a tech stack optimized for breakneck growth, not resilience. In these environments, the security team is the helpdesk, the compliance expert, and the incident response team all rolled into one. Securing the cloud office … Read More “Filling the Most Common Gaps in Google Workspace Security – The Hacker News” »
UK Executives Warn They May Not Survive a Major Cyber-Attack, Vodafone Survey Finds – Read More –
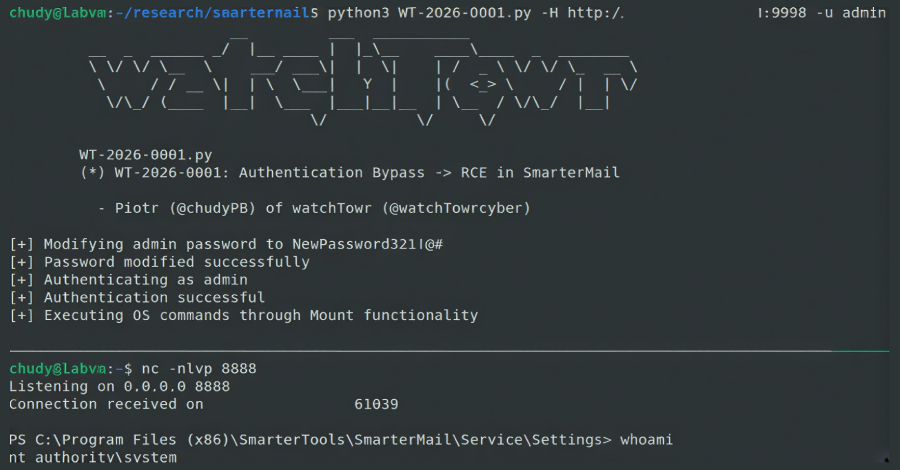
A new security flaw in SmarterTools SmarterMail email software has come under active exploitation in the wild, two days after the release of a patch. The vulnerability, which currently does not have a CVE identifier, is tracked by watchTowr Labs as WT-2026-0001. It was patched by SmarterTools on January 15, 2026, with Build 9511, following … Read More “SmarterMail Auth Bypass Exploited in the Wild Two Days After Patch Release – The Hacker News” »
A new malicious package discovered in the Python Package Index (PyPI) has been found to impersonate a popular library for symbolic mathematics to deploy malicious payloads, including a cryptocurrency miner, on Linux hosts. The package, named sympy-dev, mimics SymPy, replicating the latter’s project description verbatim in an attempt to deceive unsuspecting users into thinking that … Read More “Malicious PyPI Package Impersonates SymPy, Deploys XMRig Miner on Linux Hosts – The Hacker News” »
DLA Piper finds 22% increase in breached firms notifying European GDPR regulators – Read More –
European Space Agency’s cybersecurity in freefall as yet another breach exposes spacecraft and mission data – GRAHAM CLULEY

It has just been a few weeks since reports emerged of the Christmas cyber attack suffered by the European Space Agency (ESA), and the situation has already become worse. Read more in my article on the Hot for Security blog. – Read More – GRAHAM CLULEY
Automated FortiGate Attacks Exploit FortiCloud SSO to Alter Firewall Configurations – The Hacker News

Cybersecurity company Arctic Wolf has warned of a “new cluster of automated malicious activity” that involves unauthorized firewall configuration changes on Fortinet FortiGate devices. The activity, it said, commenced on January 15, 2026, adding it shares similarities with a December 2025 campaign in which malicious SSO logins on FortiGate appliances were recorded against the admin … Read More “Automated FortiGate Attacks Exploit FortiCloud SSO to Alter Firewall Configurations – The Hacker News” »
Day Two of Pwn2Own Automotive 2026 is underway, and the stakes are rising. Security researchers are back on the Pwn2Own stage, continuing to probe and challenge the latest automotive systems as the competition intensifies. New exploits, unexpected twists, and standout performances are already emerging – follow along here for daily updates as the race for Master … Read More “Pwn2Own Automotive 2026 – Day Two Results – Zero Day Initiative – Blog” »
Cisco has released fresh patches to address what it described as a “critical” security vulnerability impacting multiple Unified Communications (CM) products and Webex Calling Dedicated Instance that it has been actively exploited as a zero-day in the wild. The vulnerability, CVE-2026-20045 (CVSS score: 8.2), could permit an unauthenticated remote attacker to execute arbitrary commands on … Read More “Cisco Fixes Actively Exploited Zero-Day CVE-2026-20045 in Unified CM and Webex – The Hacker News” »