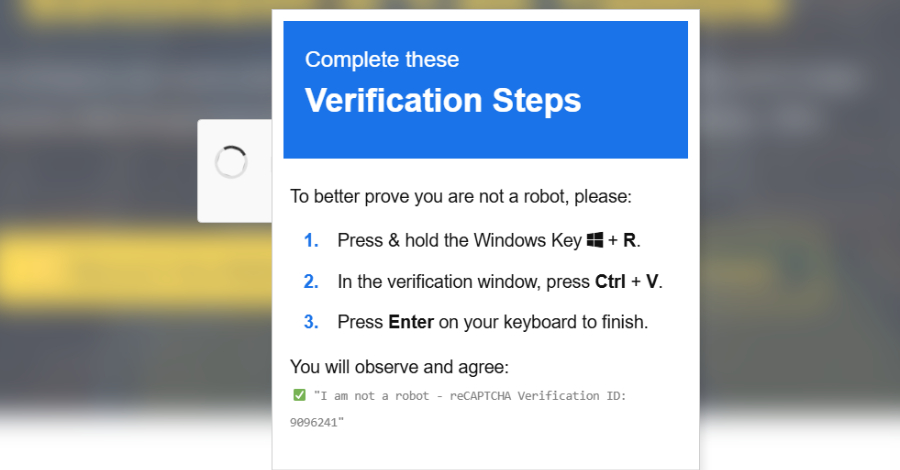
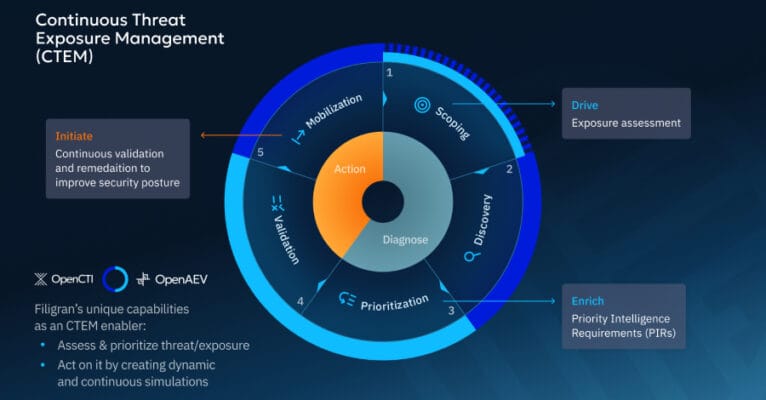
Best IT Managed Services for Large Enterprises – Hackread – Cybersecurity News, Data Breaches, AI, and More

Learn what defines top-tier enterprise managed IT services, why they matter, and how Mindcore Technologies meets large-scale business demands. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More