Multiple vulnerabilities have been discovered in Microsoft products, the most severe of which could allow for remote code execution in the context of the logged on user. Depending on the privileges associated with the user, an attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users … Read More “Critical Patches Issued for Microsoft Products, July 8, 2025 – Cyber Security Advisories – MS-ISAC” »
Hackers Use Leaked Shellter Tool License to Spread Lumma Stealer and SectopRAT Malware – The Hacker News

In yet another instance of threat actors repurposing legitimate tools for malicious purposes, it has been discovered that hackers are exploiting a popular red teaming tool called Shellter to distribute stealer malware. The company behind the software said a company that had recently purchased Shellter Elite licenses leaked their copy, prompting malicious actors to weaponize … Read More “Hackers Use Leaked Shellter Tool License to Spread Lumma Stealer and SectopRAT Malware – The Hacker News” »
It’s the second Tuesday of the month, and as expected, Adobe and Microsoft have released their latest security patches. Take a break from your scheduled activities and join us as we review the details of their latest security alerts. If you’d rather watch the full video recap covering the entire release, you can check out … Read More “The July 2025 Security Update Review – Zero Day Initiative – Blog” »
Cybersecurity researchers have discovered an Android banking malware campaign that has leveraged a trojan named Anatsa to target users in North America using malicious apps published on Google’s official app marketplace. The malware, disguised as a “PDF Update” to a document viewer app, has been caught serving a deceptive overlay when users attempt to access … Read More “Anatsa Android Banking Trojan Hits 90,000 Users with Fake PDF App on Google Play – The Hacker News” »
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 9.3 ATTENTION: Exploitable remotely/Low attack complexity Vendor: Emerson Equipment: ValveLink Products Vulnerabilities: Cleartext Storage of Sensitive Information in Memory, Protection Mechanism Failure, Uncontrolled Search Path Element, Improper Input Validation 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker with access to the system to read … Read More “Emerson ValveLink Products – All CISA Advisories” »
CISA released one Industrial Control Systems (ICS) advisory on July 8, 2025. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-25-189-01 Emerson ValveLink Products CISA encourages users and administrators to review newly released ICS advisories for technical details and mitigations. – Read More – All CISA Advisories
The AI Fix #58: An AI runs a shop into the ground, and AI’s obsession with the number 27 – Graham Cluley
In episode 58 of “The AI Fix” podcast, our hosts discover a pair of AI headphones that don’t electrocute you, Microsoft invents “medical superintelligence”, Chucky opens a hotel, some robot footballers fall over, Jony Ive invents a $6 billion pen, and Malcolm Gladwell fears a dystopian future full of children playing joyfully in the street. … Read More “The AI Fix #58: An AI runs a shop into the ground, and AI’s obsession with the number 27 – Graham Cluley” »
Applications are a common intrusion point, but the way attackers gain access, maneuver and create mayhem within and across applications doesn’t always neatly fit into MITRE’s ATT&CK framework. The team at Oligo Security is releasing a new framework it calls Application Attack Matrix to complement areas of MITRE’s framework that it describes as too broad, … Read More “Oligo Security strives to fill application-layer gaps in MITRE ATT&CK framework – CyberScoop” »
Researchers from Koi Security have detected 18 malicious Chrome and Edge extensions masquerading as benign productivity and entertainment tools – Read More –
Malicious Pull Request Targets 6,000+ Developers via Vulnerable Ethcode VS Code Extension – The Hacker News
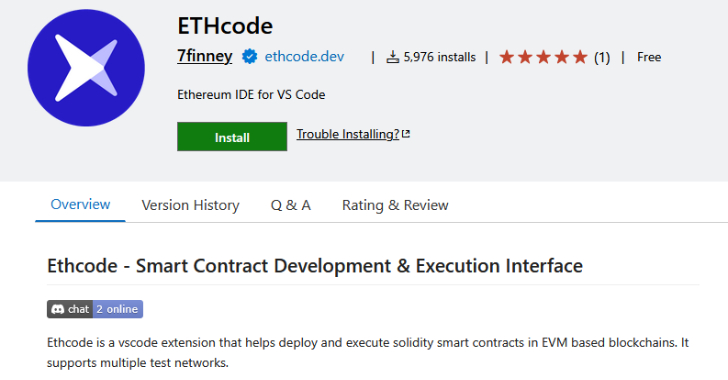
Cybersecurity researchers have flagged a supply chain attack targeting a Microsoft Visual Studio Code (VS Code) extension called Ethcode that has been installed a little over 6,000 times. The compromise, per ReversingLabs, occurred via a GitHub pull request that was opened by a user named Airez299 on June 17, 2025. First released by 7finney in … Read More “Malicious Pull Request Targets 6,000+ Developers via Vulnerable Ethcode VS Code Extension – The Hacker News” »
Check Point discovered around 500 suspected Scattered Spider phishing domains, suggesting the group is preparing to expand its targeting – Read More –
Infostealers-as-a-Service Push Identity Hacks to Record Highs – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Identity-based cyberattacks soar 156%, driven by cheap Phishing-as-a-Service & infostealer malware. Learn how criminals bypass MFA to steal credentials, access bank accounts, and compromise business emails. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
A newly released report by cybersecurity firm CTM360 reveals a large-scale scam operation utilizing fake news websites—known as Baiting News Sites (BNS)—to deceive users into online investment fraud across 50 countries. These BNS pages are made to look like real news outlets: CNN, BBC, CNBC, or regional media. They publish fake stories that feature public … Read More “BaitTrap: Over 17,000 Fake News Websites Caught Fueling Investment Fraud Globally – The Hacker News” »
RondoDox Botnet Exploits Flaws in TBK DVRs and Four-Faith Routers to Launch DDoS Attacks – The Hacker News

Cybersecurity researchers are calling attention to a malware campaign that’s targeting security flaws in TBK digital video recorders (DVRs) and Four-Faith routers to rope the devices into a new botnet called RondoDox. The vulnerabilities in question include CVE-2024-3721, a medium-severity command injection vulnerability affecting TBK DVR-4104 and DVR-4216 DVRs, and CVE-2024-12856, an operating – Read … Read More “RondoDox Botnet Exploits Flaws in TBK DVRs and Four-Faith Routers to Launch DDoS Attacks – The Hacker News” »
From overprivileged admin roles to long-forgotten vendor tokens, these attackers are slipping through the cracks of trust and access. Here’s how five retail breaches unfolded, and what they reveal about… In recent months, major retailers like Adidas, The North Face, Dior, Victoria’s Secret, Cartier, Marks & Spencer, and Co‑op have all been breached. These attacks weren’t sophisticated … Read More “5 Ways Identity-based Attacks Are Breaching Retail – The Hacker News” »
Pakistan’s Transparent Tribe Hits Indian Defence with Linux Malware – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Pakistan’s APT36 Transparent Tribe uses phishing and Linux malware to target Indian defence systems running BOSS Linux says Cyfirma. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Designed to strengthen personal data security and control data processing in India, the Digital Personal Data Protection (DPDP) Act,… The post DPDP Act Compliance Using CryptoBind’s Data Protection Tools appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Sonatype’s latest Open Source Malware Index report has identified more than 16,000 malicious open source packages, representing a 188% annual increase – Read More –
The company behind AV/EDR evasion tool Shellter has confirmed the product is being used by threat actors – Read More –
China’s Hikvision vows legal battle after Canada bans its operations, citing national security concerns – Read More –
Russian organizations have been targeted as part of an ongoing campaign that delivers a previously undocumented Windows spyware called Batavia. The activity, per cybersecurity vendor Kaspersky, has been active since July 2024. “The targeted attack begins with bait emails containing malicious links, sent under the pretext of signing a contract,” the Russian company said. “The … Read More “Researchers Uncover Batavia Windows Spyware Stealing Documents from Russian Firms – The Hacker News” »
⚡ Weekly Recap: Chrome 0-Day, Ivanti Exploits, MacOS Stealers, Crypto Heists and More – The Hacker News

Everything feels secure—until one small thing slips through. Even strong systems can break if a simple check is missed or a trusted tool is misused. Most threats don’t start with alarms—they sneak in through the little things we overlook. A tiny bug, a reused password, a quiet connection—that’s all it takes. Staying safe isn’t just … Read More “⚡ Weekly Recap: Chrome 0-Day, Ivanti Exploits, MacOS Stealers, Crypto Heists and More – The Hacker News” »
Trend Micro has observed the Bert ransomware group in operation since April 2025, with confirmed victims in sectors including healthcare, technology and event services – Read More –
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added four security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild. The list of flaws is as follows – CVE-2014-3931 (CVSS score: 9.8) – A buffer overflow vulnerability in Multi-Router Looking Glass (MRLG) that could allow remote … Read More “CISA Adds Four Critical Vulnerabilities to KEV Catalog Due to Active Exploitation – The Hacker News” »