Operation Chakra-V scores success as a fraud syndicate is busted following the raid of a scam call center operating in Noida, Uttar Pradesh – Read More –
CBI Shuts Down £390K U.K. Tech Support Scam, Arrests Key Operatives in Noida Call Center – The Hacker News

India’s Central Bureau of Investigation (CBI) has announced that it has taken steps to dismantle what it said was a transnational cybercrime syndicate that carried out “sophisticated” tech support scams targeting citizens of Australia and the United Kingdom. The fraudulent scheme is estimated to have led to losses worth more than £390,000 ($525,000) in the … Read More “CBI Shuts Down £390K U.K. Tech Support Scam, Arrests Key Operatives in Noida Call Center – The Hacker News” »
eSIM Vulnerability in Kigen’s eUICC Cards Exposes Billions of IoT Devices to Malicious Attacks – The Hacker News
Cybersecurity researchers have discovered a new hacking technique that exploits weaknesses in the eSIM technology used in modern smartphones, exposing users to severe risks. The issues impact the Kigen eUICC card. According to the Irish company’s website, more than two billion SIMs in IoT devices have been enabled as of December 2020. The findings come … Read More “eSIM Vulnerability in Kigen’s eUICC Cards Exposes Billions of IoT Devices to Malicious Attacks – The Hacker News” »
Your Simple Guide: How to Use Filmora’s Planar Tracker for Awesome Video Edits – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Easily stick logos, text, or graphics onto moving surfaces with Filmora’s planar tracker. Just read this article to know how! – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Critical Vulnerability Exposes Fortinet FortiWeb to Full Takeover (CVE-2025-25257) – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

WatchTowr Labs reveals CVE-2025-25257, a critical FortiWeb SQL injection allowing unauthenticated remote code execution. Patch your FortiWeb 7.0,… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Posted by Tifa Lockhart via Fulldisclosure on Jul 12 Advisory ID: OPENBLOW-2025-003 Title: Missing Critical Security Headers in OpenBlow Date: 2025-07-12 Vendor: OpenBlow (openblow.it) Severity: High CVSS v3.1 Base Score: 8.2 (High) Vector: AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:L/A:N Summary: Multiple public deployments of the OpenBlow whistleblowing software lack critical HTTP security headers. These configurations expose users to client-side … Read More “Missing Critical Security Headers in OpenBlow – Full Disclosure” »
NVIDIA is urging customers to enable System-level Error Correction Codes (ECC) as a defense against a variant of a RowHammer attack demonstrated against its graphics processing units (GPUs). “Risk of successful exploitation from RowHammer attacks varies based on DRAM device, platform, design specification, and system settings,” the GPU maker said in an advisory released this … Read More “GPUHammer: New RowHammer Attack Variant Degrades AI Models on NVIDIA GPUs – The Hacker News” »
Over 600 Laravel Apps Exposed to Remote Code Execution Due to Leaked APP_KEYs on GitHub – The Hacker News
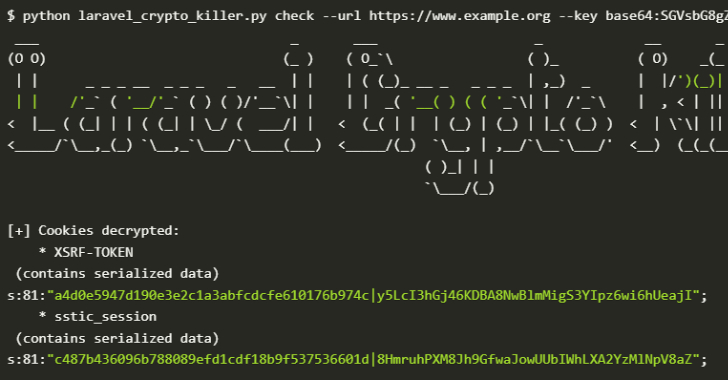
Cybersecurity researchers have discovered a serious security issue that allows leaked Laravel APP_KEYs to be weaponized to gain remote code execution capabilities on hundreds of applications. “Laravel’s APP_KEY, essential for encrypting sensitive data, is often leaked publicly (e.g., on GitHub),” GitGuardian said. “If attackers get access to this key, they can exploit a deserialization flaw … Read More “Over 600 Laravel Apps Exposed to Remote Code Execution Due to Leaked APP_KEYs on GitHub – The Hacker News” »
DoNot APT Hits European Ministry with New LoptikMod Malware – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Trellix reveals how the India-linked DoNot APT group launched a sophisticated spear-phishing attack on a European foreign affairs… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Leaked Shellter Elite Tool Now Fueling Infostealer Attacks Worldwide – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

A new report details how the advanced hacking tool Shellter Elite was leaked and is now being used… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
FBI Seizes Major Sites Sharing Unreleased and Pirated Video Games – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
FBI seizes top piracy sites leaking unreleased and pirated video games with millions of downloads and 170 million dollars in losses for developers and publishers. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
14 Arrested in Romania for £47 Million UK Tax Phishing Scam – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

14 arrested in major HMRC phishing scam raids across UK & Romania. Learn about the multi-million-pound tax fraud operation. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
New Study Shows Google Tracking Persists Even With Privacy Tools – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
A new SafetyDetectives study reveals the surprising extent of Google tracking across the web in the US, UK, Switzerland, and Sweden. Discover how Google Analytics, AdSense, and YouTube embeds collect your data, even when using DuckDuckGo. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Magento 2 Shipping Automation: Cut Costs While Enhancing Customer Experience – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Disclosure: The information in this article highlights Elsner’s Magento development offerings and related solutions. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Cybersecurity researchers have identified four significant security vulnerabilities in a widely used automotive Bluetooth system that could potentially allow remote attackers to execute code on millions of vehicles worldwide. The vulnerabilities, collectively named PerfektBlue by PCA Cyber Security, affect OpenSynergy’s BlueSDK Bluetooth stack, which is used to implement Bluetooth functionality in embedded systems, with a … Read More “Researchers identify critical vulnerabilities in automotive Bluetooth systems – CyberScoop” »
Fortinet Releases Patch for Critical SQL Injection Flaw in FortiWeb (CVE-2025-25257) – The Hacker News

Fortinet has released fixes for a critical security flaw impacting FortiWeb that could enable an unauthenticated attacker to run arbitrary database commands on susceptible instances. Tracked as CVE-2025-25257, the vulnerability carries a CVSS score of 9.6 out of a maximum of 10.0. “An improper neutralization of special elements used in an SQL command (‘SQL Injection’) … Read More “Fortinet Releases Patch for Critical SQL Injection Flaw in FortiWeb (CVE-2025-25257) – The Hacker News” »
‘Hacking is assumed now’: experts raise the alarm about added risk of surveillance cameras in childcare centres – Data and computer security | The Guardian

As governments consider mandatory CCTV in early education, one big provider with cameras already installed is yet to formalise guidelines for how the footage will be stored and used Get our breaking news email, free app or daily news podcast In the wake of horrifying reports last week alleging that eight children had been sexually … Read More “‘Hacking is assumed now’: experts raise the alarm about added risk of surveillance cameras in childcare centres – Data and computer security | The Guardian” »
Virtru, a Washington, D.C.-based data security company that developed technology now used by U.S. defense and intelligence agencies, has raised $50 million in funding as organizations seek new ways to protect sensitive information in an era of artificial intelligence adoption. The Series D round, led by investment firm ICONIQ with participation from Bessemer Venture Partners, … Read More “Virtru secures $50 million investment to advance data-centric security standards – CyberScoop” »
The new CISA Associate designation recognizes ISACA members who have passed the CISA exam, but do not yet have the required experience – Read More –
Louis Vuitton says UK customer data stolen in cyber-attack – Data and computer security | The Guardian

Lead brand of French luxury group LVMH reassures customers financial data such as bank details were not taken Louis Vuitton has said the data of some UK customers has been stolen as it became the latest retailer targeted by cyber hackers. The retailer, the leading brand of the French luxury group LVMH, said an unauthorised … Read More “Louis Vuitton says UK customer data stolen in cyber-attack – Data and computer security | The Guardian” »
Russian basketball player arrested in ransomware case despite being “useless with computers” – Graham Cluley

A Russian professional basketball player has been arrested for allegedly acting as a negotiator for a ransomware gang… and despite his lawyer claiming he’s “useless” with computers. Read more in my article on the Hot for Security blog. – Read More – Graham Cluley
PerfektBlue Bluetooth Vulnerabilities Expose Millions of Vehicles to Remote Code Execution – The Hacker News

Cybersecurity researchers have discovered a set of four security flaws in OpenSynergy’s BlueSDK Bluetooth stack that, if successfully exploited, could allow remote code execution on millions of transport vehicles from different vendors. The vulnerabilities, dubbed PerfektBlue, can be fashioned together as an exploit chain to run arbitrary code on cars from at least three major … Read More “PerfektBlue Bluetooth Vulnerabilities Expose Millions of Vehicles to Remote Code Execution – The Hacker News” »
Posted by Office nullFaktor GmbH on Jul 11 nullFaktor Security Advisory < 20250719 > =========================================================== Title: ABAP Code Execution via Internal Function Module WRITE_AND_CALL_DBPROG Vulnerability: Exposed Dangerous Functionality Product: SAP NetWeaver S/4HANA Homepage: http://www.sap.com Affected Version: S/4HANA, SAP_BASIS 757 SP 3 SAP Note: 3546011 Impact: High… – Read More – Full Disclosure
Paddy Power and BetFair have warned customers that “an unauthorised third party” gained access to “limited betting account information” relating to up to 800,000 of their customers. – Read More – Graham Cluley
Iranian-Backed Pay2Key Ransomware Resurfaces with 80% Profit Share for Cybercriminals – The Hacker News

An Iranian-backed ransomware-as-a-service (RaaS) named Pay2Key has resurfaced in the wake of the Israel-Iran-U.S. conflict last month, offering bigger payouts to cybercriminals who launch attacks against Israel and the U.S. The financially motivated scheme, now operating under the moniker Pay2Key.I2P, is assessed to be linked to a hacking group tracked as Fox Kitten (aka Lemon … Read More “Iranian-Backed Pay2Key Ransomware Resurfaces with 80% Profit Share for Cybercriminals – The Hacker News” »
Critical Wing FTP Server Vulnerability (CVE-2025-47812) Actively Being Exploited in the Wild – The Hacker News

A recently disclosed maximum-severity security flaw impacting the Wing FTP Server has come under active exploitation in the wild, according to Huntress. The vulnerability, tracked as CVE-2025-47812 (CVSS score: 10.0), is a case of improper handling of null (”) bytes in the server’s web interface, which allows for remote code execution. It has been addressed … Read More “Critical Wing FTP Server Vulnerability (CVE-2025-47812) Actively Being Exploited in the Wild – The Hacker News” »
The 2025 Data Risk Report: Enterprises face potentially serious data loss risks from AI-fueled tools. Adopting a unified, AI-driven approach to data security can help. As businesses increasingly rely on cloud-driven platforms and AI-powered tools to accelerate digital transformation, the stakes for safeguarding sensitive enterprise data have reached unprecedented levels. The Zscaler ThreatLabz – Read … Read More “Securing Data in the AI Era – The Hacker News” »
The man was handed a suspended prison sentence for offenses relating to the hack of Network Rail public Wi-Fi, exposing customers to offensive messaging – Read More –
DoNot APT, also known as APT-C-35, traditionally operates exclusively in South Asia – Read More –
British bank TSB warns of rise of “finfluencers” who dispense dubious financial advice online – Read More –
The Intelligence and Security Committee has warned of Iran’s “aggressive” and “extensive” cyber capabilities – Read More –
CISA Adds Citrix NetScaler CVE-2025-5777 to KEV Catalog as Active Exploits Target Enterprises – The Hacker News

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical security flaw impacting Citrix NetScaler ADC and Gateway to its Known Exploited Vulnerabilities (KEV) catalog, officially confirming the vulnerability has been weaponized in the wild. The shortcoming in question is CVE-2025-5777 (CVSS score: 9.3), an instance of insufficient input validation that – … Read More “CISA Adds Citrix NetScaler CVE-2025-5777 to KEV Catalog as Active Exploits Target Enterprises – The Hacker News” »
McDonald’s AI Hiring Tool McHire Leaked Data of 64 Million Job Seekers – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
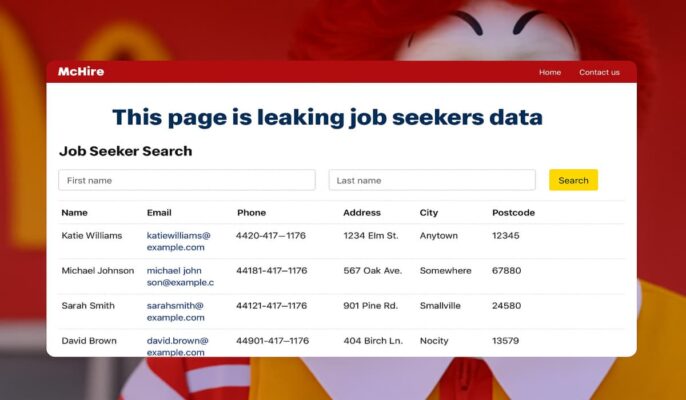
Major security flaw in McDonald’s AI hiring tool McHire exposed 64M job applications. Discover how an IDOR vulnerability… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Authorities in the United Kingdom this week arrested four people aged 17 to 20 in connection with recent data theft and extortion attacks against the retailers Marks & Spencer and Harrods, and the British food retailer Co-op Group. The breaches have been linked to a prolific but loosely-affiliated cybercrime group dubbed “Scattered Spider,” whose other … Read More “UK Arrests Four in ‘Scattered Spider’ Ransom Group – Krebs on Security” »
Critical mcp-remote Vulnerability Enables Remote Code Execution, Impacting 437,000+ Downloads – The Hacker News

Cybersecurity researchers have discovered a critical vulnerability in the open-source mcp-remote project that could result in the execution of arbitrary operating system (OS) commands. The vulnerability, tracked as CVE-2025-6514, carries a CVSS score of 9.6 out of 10.0. “The vulnerability allows attackers to trigger arbitrary OS command execution on the machine running mcp-remote when it … Read More “Critical mcp-remote Vulnerability Enables Remote Code Execution, Impacting 437,000+ Downloads – The Hacker News” »
UK Arrests Woman and Three Men for Cyberattacks on M&S Co-op and Harrods – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Four suspects arrested by the NCA in April/May 2025 cyberattacks on M&S, Co-op, and Harrods. Learn about the social engineering, ransomware disruption, and estimated £300M impact on M&S. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.4 ATTENTION: Low attack complexity Vendor: Delta Electronics Equipment: DTM Soft Vulnerability: Deserialization of Untrusted Data 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to encrypt files referencing the application in order to extract information. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following Delta … Read More “Delta Electronics DTM Soft – All CISA Advisories” »
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 9.3 ATTENTION: Exploitable remotely/low attack complexity Vendor: KUNBUS Equipment: RevPi Webstatus Vulnerability: Incorrect Implementation of Authentication Algorithm 2. RISK EVALUATION Successful exploitation of this vulnerability could allow attackers to bypass authentication and gain unauthorized access to the application. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS KUNBUS reports the following … Read More “KUNBUS RevPi Webstatus – All CISA Advisories” »
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 7.2 ATTENTION: Low attack complexity Standard: End-of-Train and Head-of-Train remote linking protocol Equipment: End-of-Train and Head-of-Train devices Vulnerability: Weak Authentication 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to send their own brake control commands to the end-of-train device, causing a sudden stoppage of … Read More “End-of-Train and Head-of-Train Remote Linking Protocol – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 9.3 ATTENTION: Exploitable remotely/low attack … Read More “Siemens SINEC NMS – All CISA Advisories” »
CISA released thirteen Industrial Control Systems (ICS) advisories on July 10, 2025. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-25-191-01 Siemens SINEC NMS ICSA-25-191-02 Siemens Solid Edge ICSA-25-191-03 Siemens TIA Administrator ICSA-25-191-04 Siemens SIMATIC CN 4100 ICSA-25-191-05 Siemens TIA Project-Server and TIA Portal ICSA-25-191-06 Siemens SIPROTEC 5 ICSA-25-191-07 … Read More “CISA Releases Thirteen Industrial Control Systems Advisories – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 6.0 ATTENTION: Exploitable remotely Vendor: Siemens … Read More “Siemens SIPROTEC 5 – All CISA Advisories” »
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.7 ATTENTION: Exploitable remotely/low attack complexity Vendor: Advantech Equipment: iView Vulnerabilities: Cross-site Scripting, SQL Injection, Path Traversal, Argument Injection. 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to disclose sensitive information, achieve remote code execution, or cause service disruptions. 3. TECHNICAL DETAILS 3.1 AFFECTED … Read More “Advantech iView – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.5 ATTENTION: Low attack complexity … Read More “Siemens TIA Administrator – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 5.3 ATTENTION: Exploitable remotely/low attack … Read More “Siemens TIA Project-Server and TIA Portal – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 7.3 ATTENTION: High attack complexity … Read More “Siemens Solid Edge – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 7.1 ATTENTION: Exploitable remotely/low attack … Read More “Siemens SIMATIC CN 4100 – All CISA Advisories” »
Fake Gaming and AI Firms Push Malware on Cryptocurrency Users via Telegram and Discord – The Hacker News

Cryptocurrency users are the target of an ongoing social engineering campaign that employs fake startup companies to trick users into downloading malware that can drain digital assets from both Windows and macOS systems. “These malicious operations impersonate AI, gaming, and Web3 firms using spoofed social media accounts and project documentation hosted on legitimate platforms like … Read More “Fake Gaming and AI Firms Push Malware on Cryptocurrency Users via Telegram and Discord – The Hacker News” »
French police arrest Russian pro basketball player on behalf of US over ransomware suspicions – CyberScoop

At the request of the United States, French police arrested a professional Russian basketball player who had a brief tenure at Penn State over accusations that he was part of a ransomware ring, according to overseas reports. News of the arrest of Daniil Kasatkin came in a court in Paris on Wednesday. His lawyer denied … Read More “French police arrest Russian pro basketball player on behalf of US over ransomware suspicions – CyberScoop” »
Three teenagers and a 20-year-old woman were arrested Thursday by the U.K.’s National Crime Agency for their alleged role in cyberattacks on major retailers Marks & Spencer (M&S), Co-op, and Harrods. The arrests, comprising British and Latvian nationals, followed sustained investigations into attacks that crippled the retailers’ operations. The NCA’s National Cyber Crime Unit detained … Read More “UK arrests four for cyberattacks on major British retailers – CyberScoop” »