AsyncRAT, the most prevalent remote access trojan observed in the wild, has spawned more than 30 forks and variants that increase the impact of the open-source malware, making it a popular and sometimes disguised tool of choice for cybercriminals, ESET researchers said in a report released Tuesday. The open source remote access tool, which was … Read More “AsyncRAT seeds family of more than 30 remote access trojans – CyberScoop” »
Attackers Hide JavaScript in SVG Images to Lure Users to Malicious Sites – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Beware! SVG images are now being used with obfuscated JavaScript for stealthy redirect attacks via spoofed emails. Get insights from Ontinue’s latest research on detection and defence. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Cloudflare on Tuesday said it mitigated 7.3 million distributed denial-of-service (DDoS) attacks in the second quarter of 2025, a significant drop from 20.5 million DDoS attacks it fended off the previous quarter. “Overall, in Q2 2025, hyper-volumetric DDoS attacks skyrocketed,” Omer Yoachimik and Jorge Pacheco said. “Cloudflare blocked over 6,500 hyper-volumetric DDoS attacks, an average … Read More “Hyper-Volumetric DDoS Attacks Reach Record 7.3 Tbps, Targeting Key Global Sectors – The Hacker News” »
MITRE has introduced AADAPT framework, a new cybersecurity framework aimed at mitigating risks in digital financial systems like cryptocurrency – Read More –
CISA released six Industrial Control Systems (ICS) advisories on July 15, 2025. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-25-196-01 Hitachi Energy Asset Suite ICSA-25-196-02 ABB RMC-100 ICSA-25-196-03 LITEON IC48A and IC80A EV Chargers ICSA-25-037-02 Schneider Electric EcoStruxure (Update B) ICSA-25-140-08 Schneider Electric Modicon Controllers (Update A) ICSA-25-070-01 … Read More “CISA Releases Six Industrial Control Systems Advisories – All CISA Advisories” »
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.7 ATTENTION: Exploitable remotely/low attack complexity Vendor: LITEON Equipment: IC48A and IC80A Vulnerability: Plaintext Storage of a Password 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to access sensitive information when accessing the Liteon EV chargers. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following … Read More “LITEON IC48A and IC80A EV Chargers – All CISA Advisories” »
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.2 ATTENTION: Exploitable remotely/low attack complexity Vendor: ABB Equipment: RMC-100 Vulnerabilities: Use of Hard-coded Cryptographic Key, Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to gain unauthenticated access to the MQTT configuration data, cause a denial-of-service condition on the MQTT configuration … Read More “ABB RMC-100 – All CISA Advisories” »
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 9.1 ATTENTION: Exploitable remotely/low attack complexity Vendor: Hitachi Energy Equipment: Energy Asset Suite Vulnerabilities: Incomplete List of Disallowed Inputs, Plaintext Storage of a Password, Out-of-bounds Write, Release of Invalid Pointer or Reference 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to gain unauthorized access … Read More “Hitachi Energy Asset Suite – All CISA Advisories” »
Newly Emerged GLOBAL GROUP RaaS Expands Operations with AI-Driven Negotiation Tools – The Hacker News

Cybersecurity researchers have shed light on a new ransomware-as-a-service (RaaS) operation called GLOBAL GROUP that has targeted a wide range of sectors in Australia, Brazil, Europe, and the United States since its emergence in early June 2025. GLOBAL GROUP was “promoted on the Ramp4u forum by the threat actor known as ‘$$$,’” EclecticIQ researcher Arda … Read More “Newly Emerged GLOBAL GROUP RaaS Expands Operations with AI-Driven Negotiation Tools – The Hacker News” »
UK Pet Owners Targeted by Fake Microchip Renewal Scams – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Microchip renewal scam targets UK pet owners using leaked data from insecure registries. Emails appear legit but aim to steal money and personal info. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
A criminal investigation into Twitter has been initiated by French prosecutors, over allegations that its algorithm is manipulated for the purposes of “foreign interference.” – Read More – Graham Cluley
SIM scammer’s sentence increased to 12 years, after failing to pay back victim $20 million – Graham Cluley

Read more in my article on the Hot for Security blog. – Read More – Graham Cluley
In episode 59 of The AI Fix, our hosts ponder whether AIs need a “disagreement dial”, Mark wonders what he could do with an AI-powered “drug design engine”, Graham plays Wolfenstein instead of working, a robot graduates from high school, and a popular rock group is unmasked as an AI fever dream. Graham explains why … Read More “The AI Fix #59: Grok thinks it’s Mecha Hitler, and AIs can think strategically – Graham Cluley” »
In recent years, there has been an increase in interest in JavaScript engine vulnerabilities in order to compromise web browsers. Notably, vulnerabilities in JIT engines are among the most favorite ones as they tend to provide strong primitives, and well-known techniques are available to facilitate compromise. At Pwn2Own Berlin 2025, Manfred Paul compromised the Mozilla … Read More “CVE-2025-4919: Corruption via Math Space in Mozilla Firefox – Zero Day Initiative – Blog” »
A new phishing campaign uses SVG files for JavaScript redirects, bypassing traditional detection methods – Read More –
The latest report from AppOmni has revealed 91% confidence in SaaS security while 75% of organizations have faced incidents – Read More –
Meme Coins in 2025: High Risk, High Reward, and Rising Security Threats – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Meme coins started as internet jokes, but by 2025, they’ve become one of the most volatile and talked-about… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
GitGuardian Launches MCP Server to Bring Secrets Security into Developer Workflows – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Paris, France, 15th July 2025, CyberNewsWire – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Socket has identified a new malware loader called XORIndex incorporated into malicious packages published to the npm registry, with over 9000 downloads so far – Read More –
AsyncRAT’s Open-Source Code Sparks Surge in Dangerous Malware Variants Across the Globe – The Hacker News

Cybersecurity researchers have charted the evolution of a widely used remote access trojan called AsyncRAT, which was first released on GitHub in January 2019 and has since served as the foundation for several other variants. “AsyncRAT has cemented its place as a cornerstone of modern malware and as a pervasive threat that has evolved into … Read More “AsyncRAT’s Open-Source Code Sparks Surge in Dangerous Malware Variants Across the Globe – The Hacker News” »
AI agents promise to automate everything from financial reconciliations to incident response. Yet every time an AI agent spins up a workflow, it has to authenticate somewhere; often with a high-privilege API key, OAuth token, or service account that defenders can’t easily see. These “invisible” non-human identities (NHIs) now outnumber human accounts in most cloud … Read More “Securing Agentic AI: How to Protect the Invisible Identity Access – The Hacker News” »
State-Backed HazyBeacon Malware Uses AWS Lambda to Steal Data from SE Asian Governments – The Hacker News

Governmental organizations in Southeast Asia are the target of a new campaign that aims to collect sensitive information by means of a previously undocumented Windows backdoor dubbed HazyBeacon. The activity is being tracked by Palo Alto Networks Unit 42 under the moniker CL-STA-1020, where “CL” stands for “cluster” and “STA” refers to “state-backed motivation.” “The … Read More “State-Backed HazyBeacon Malware Uses AWS Lambda to Steal Data from SE Asian Governments – The Hacker News” »
Darknet giant Abacus Market has gone offline due to a likely exit scam, according to TRM Labs – Read More –
The NCSC’s new Vulnerability Research Institute will help it develop outreach with the external cybersecurity community – Read More –
North Korean Hackers Flood npm Registry with XORIndex Malware in Ongoing Attack Campaign – The Hacker News

The North Korean threat actors linked to the Contagious Interview campaign have been observed publishing another set of 67 malicious packages to the npm registry, underscoring ongoing attempts to poison the open-source ecosystem via software supply chain attacks. The packages, per Socket, have attracted more than 17,000 downloads, and incorporate a previously undocumented version of … Read More “North Korean Hackers Flood npm Registry with XORIndex Malware in Ongoing Attack Campaign – The Hacker News” »
Marko Elez, a 25-year-old employee at Elon Musk’s Department of Government Efficiency (DOGE), has been granted access to sensitive databases at the U.S. Social Security Administration, the Treasury and Justice departments, and the Department of Homeland Security. So it should fill all Americans with a deep sense of confidence to learn that Mr. Elez over … Read More “DOGE Denizen Marko Elez Leaked API Key for xAI – Krebs on Security” »
Russian Basketball Star Daniil Kasatkin Arrested in Ransomware Probe – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Daniil Kasatkin, a Russian pro basketball player, faces US ransomware charges after his Paris arrest. His lawyer claims he’s “useless with computers,” raising questions about his alleged negotiator role in cybercrime. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Authorities and researchers are intensifying warnings about active exploitation and pervasive scanning of a critical vulnerability affecting multiple versions of Citrix NetScaler products. There is now widespread agreement among security professionals that the critical vulnerability, CVE-2025-5777, which Citrix disclosed June 17, is serious and harkens back to a 2023 defect in the same products: “CitrixBleed,” … Read More “CitrixBleed 2 beckons sweeping alarm as exploits spread across the globe – CyberScoop” »
As cyber officials work to contain Salt Typhoon inside U.S. telecom networks, the House on Monday passed a bill that would officially designate one federal agency to lead efforts in protecting the nation’s digital infrastructure from such threats. The National Telecommunications and Information Administration Organization Act cleared the House via voice vote and is now … Read More “House passes bill to formalize NTIA’s cyber role following Salt Typhoon attacks – CyberScoop” »
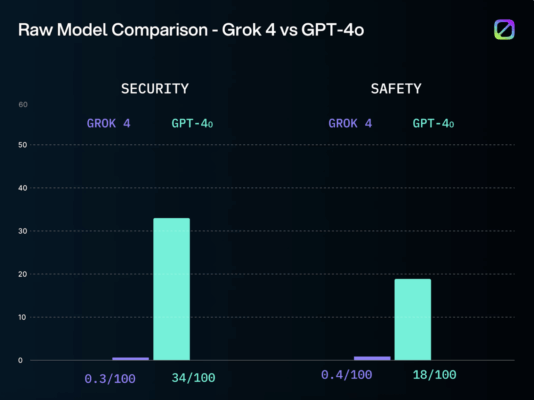
On the same day xAI announced that its new Grok 4 tool will now be available to the federal government, cybersecurity researchers at SplxAI released new research that subjected the large language model to more than 1,000 different attack scenarios. The good news? Smart system prompting on the front end can make a difference in … Read More “Why skipping security prompting on Grok’s newest model is a huge mistake – CyberScoop” »
Louis Vuitton UK Hit by Cyberattack, Third LVMH Breach in 3 Months – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Louis Vuitton UK suffers cyberattack exposing customer data, marking the third LVMH breach in 3 months as retail sector faces ongoing security threats. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Researchers Jailbreak Elon Musk’s Grok-4 AI Within 48 Hours of Launch – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Elon Musk’s Grok-4 AI was compromised within 48 hours. Discover how NeuralTrust researchers combined “Echo Chamber” and “Crescendo”… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
New PHP-Based Interlock RAT Variant Uses FileFix Delivery Mechanism to Target Multiple Industries – The Hacker News
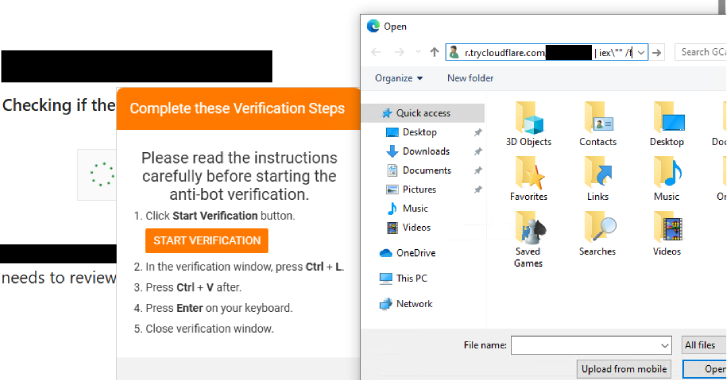
Threat actors behind the Interlock ransomware group have unleashed a new PHP variant of its bespoke remote access trojan (RAT) as part of a widespread campaign using a variant of ClickFix called FileFix. “Since May 2025, activity related to the Interlock RAT has been observed in connection with the LandUpdate808 (aka KongTuke) web-inject threat clusters,” … Read More “New PHP-Based Interlock RAT Variant Uses FileFix Delivery Mechanism to Target Multiple Industries – The Hacker News” »
While phishing and ransomware dominate headlines, another critical risk quietly persists across most enterprises: exposed Git repositories leaking sensitive data. A risk that silently creates shadow access into core systems Git is the backbone of modern software development, hosting millions of repositories and serving thousands of organizations worldwide. Yet, amid the daily hustle of shipping … Read More “The Unusual Suspect: Git Repos – The Hacker News” »
CISA has added one new vulnerability to its Known Exploited Vulnerabilities (KEV) Catalog, based on evidence of active exploitation. CVE-2025-47812 Wing FTP Server Improper Neutralization of Null Byte or NUL Character Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) … Read More “CISA Adds One Known Exploited Vulnerability to Catalog – All CISA Advisories” »
Dedicated Proxies: A Key Tool for Online Privacy, Security and Speed – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Online privacy, security, and performance today are more important than ever. For professionals and businesses working online, it’s… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Grok-4 was jailbroken 48 hours post-launch using Echo Chamber and Crescendo attack methods – Read More –
Denmark Moves Toward AI Copyright Rules for Voice and Appearance – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Denmark introduces new AI Copyright Rules to ban non-consensual deepfakes, giving citizens legal control over their face, voice and digital likeness. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
A vulnerability in Kigen eUICC cards has exposed billions of IoT devices via flawed eSIM profile management – Read More –
CTM360 has identified over 17,000 fake news sites mimicking reputable brands like CNN, BBC and CNBC, spreading investment fraud across 50 countries – Read More –
⚡ Weekly Recap: Scattered Spider Arrests, Car Exploits, macOS Malware, Fortinet RCE and More – The Hacker News

In cybersecurity, precision matters—and there’s little room for error. A small mistake, missed setting, or quiet misconfiguration can quickly lead to much bigger problems. The signs we’re seeing this week highlight deeper issues behind what might look like routine incidents: outdated tools, slow response to risks, and the ongoing gap between compliance and real security. … Read More “⚡ Weekly Recap: Scattered Spider Arrests, Car Exploits, macOS Malware, Fortinet RCE and More – The Hacker News” »
The NCSC has warned that there are still a significant number of organizations using Windows 10, which will soon be unsupported with security updates – Read More –
China-Built SafeLine WAF Gains Global Popularity Among Startups & Homelabs – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Beijing, China, 14th July 2025, CyberNewsWire – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
When news broke that an AI agent named XBOW was leading the HackerOne bug bounty leaderboards, it quickly raised several concerning questions for the cybersecurity industry. Have large language models evolved enough to partially or fully replace human bug hunting? How precisely does XBOW — built by a startup with the same name — work? … Read More “Is XBOW’s success the beginning of the end of human-led bug hunting? Not yet. – CyberScoop” »
In an era characterized by escalating cybersecurity threats, rapidly evolving technological landscapes, and heightened regulatory demands, organizations face significant pressure to modernize their Governance, Risk, and Compliance (GRC) practices. The federal government is also pivoting toward automation, with Policy-as-Code (PaC) becoming a foundational element in modern cybersecurity governance and compliance. A critical driver accelerating this … Read More “New White House cyber executive order pushes rules as code – CyberScoop” »
Crypto Market Outlook: How Crypto Will Come of Age in 2025 – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

2024 was an important year for cryptocurrency markets, both in terms of growth, user adoption, investment, and technological… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
India’s Digital Personal Data Protection (DPDP) Act is reshaping how companies collect, process, store, and share personal data. For… The post How India’s DPDP Act Impacts Digital Lending appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Elmo has been hacked, claims Trump is in Epstein files, calls for Jews to be exterminated – Graham Cluley

Over the weekend, Sesame Street star Elmo’s verified account was apparently hijacked and used to post a string of profane messages, including one describing Donald Trump as a “child f****r” and referencing Jeffrey Epstein. – Read More – Graham Cluley
Man Gets Suspended Sentence for Hate-Fueled UK Train Stations WiFi Hack – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

British citizen John Wik sentenced for Islamophobic WiFi hack at UK train stations in Sept 2024. Learn about… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Interlock ransomware continues to develop custom tooling and a new RAT has been detected by researchers – Read More –