Generative AI platforms like ChatGPT, Gemini, Copilot, and Claude are increasingly common in organizations. While these solutions improve efficiency across tasks, they also present new data leak prevention for generative AI challenges. Sensitive information may be shared through chat prompts, files uploaded for AI-driven summarization, or browser plugins that bypass familiar security controls. – Read … Read More “Can Your Security Stack See ChatGPT? Why Network Visibility Matters – The Hacker News” »
A software supply chain attack targeting Nx marks the first known case where attackers have leveraged developer AI assistants, according to StepSecurity – Read More –
The NIST National Cybersecurity Center of Excellence (NCCoE) has published the final version of NIST Internal Report (IR) 8349, Methodology for Characterizing Network Behavior of Internet of Things (IoT) Devices. Characterizing and understanding the – Read More – News and Events Feed by Topic
Recorded Future highlighted the vast capabilities of state actors to rapidly weaponize newly disclosed vulnerabilities for geopolitical purposes – Read More –
The Sangoma FreePBX Security Team has issued an advisory warning about an actively exploited FreePBX zero-day vulnerability that impacts systems with an administrator control panel (ACP) exposed to the public internet. FreePBX is an open-source private branch exchange (PBX) platform widely used by businesses, call centers, and service providers to manage voice communications. It’s built … Read More “FreePBX Servers Targeted by Zero-Day Flaw, Emergency Patch Now Available – The Hacker News” »
Click Studios Patches Passwordstate Authentication Bypass Vulnerability in Emergency Access Page – The Hacker News

Click Studios, the developer of enterprise-focused password management solution Passwordstate, said it has released security updates to address an authentication bypass vulnerability in its software. The issue, which is yet to be assigned a CVE identifier, has been addressed in Passwordstate 9.9 (Build 9972), released August 28, 2025. The Australian company said it fixed a … Read More “Click Studios Patches Passwordstate Authentication Bypass Vulnerability in Emergency Access Page – The Hacker News” »
Feds Seize $6.4M VerifTools Fake-ID Marketplace, but Operators Relaunch on New Domain – The Hacker News
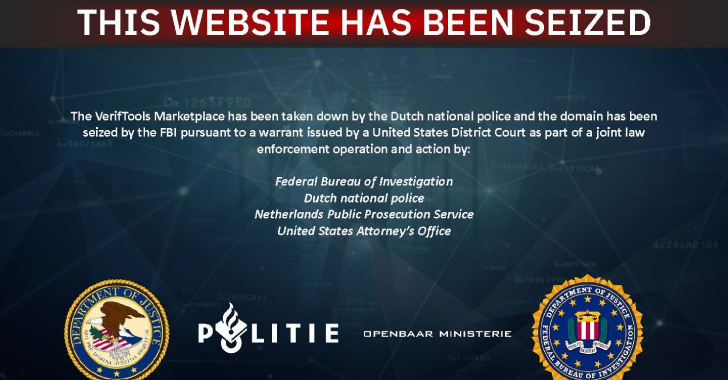
Authorities from the Netherlands and the United States have announced the dismantling of an illicit marketplace called VerifTools that peddled fraudulent identity documents to cybercriminals across the world. To that end, two marketplace domains (verif[.]tools and veriftools[.]net) and one blog have been taken down, redirecting site visitors to a splash page stating the action was … Read More “Feds Seize $6.4M VerifTools Fake-ID Marketplace, but Operators Relaunch on New Domain – The Hacker News” »
The credit rating giant revealed that the breach, which occurred on July 28, was caused by unauthorized access to a third-party application – Read More –
Southeast Asia’s Hidden Crisis – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.

The UN Reveals Widespread Trafficking into Online Scam Operations Every day, thousands of lives are torn apart in the shadows of Southeast Asia. A harrowing UN Human Rights Office (OHCHR) report from 29 August 2023 reveals that hundreds of thousands of individuals have been trafficked and forced into online scam operations, often under brutal and … Read More “Southeast Asia’s Hidden Crisis – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.” »
Google Warns Salesloft OAuth Breach Extends Beyond Salesforce, Impacting All Integrations – The Hacker News

Google has revealed that the recent wave of attacks targeting Salesforce instances via Salesloft Drift is much broader in scope than previously thought, stating it impacts all integrations. “We now advise all Salesloft Drift customers to treat any and all authentication tokens stored in or connected to the Drift platform as potentially compromised,” Google Threat … Read More “Google Warns Salesloft OAuth Breach Extends Beyond Salesforce, Impacting All Integrations – The Hacker News” »
The semiconductor industry has become the throbbing heart of the current technology, and the tech ecosystem runs on it… The post Building Cyber Resilience in the Semiconductor Ecosystem appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Cybersecurity researchers have discovered a cybercrime campaign that’s using malvertising tricks to direct victims to fraudulent sites to deliver a new information stealer called TamperedChef. “The objective is to lure victims into downloading and installing a trojanized PDF editor, which includes an information-stealing malware dubbed TamperedChef,” Truesec researchers Mattias Wåhlén, Nicklas – Read More – … Read More “TamperedChef Malware Disguised as Fake PDF Editors Steals Credentials and Cookies – The Hacker News” »