A malicious npm package “nodejs-smtp” has been discovered impersonating nodemailer and injecting code to drain crypto wallets – Read More –
Experts have revealed an Azure AD vulnerability exposing ClientId and ClientSecret in a publicly accessible appsettings.json file – Read More –
Varonis has acquired SlashNext, an AI-driven email security company, for up to $150 million in a move that reflects the rising role of artificial intelligence in both attack and defense. The acquisition, announced Tuesday, brings together Varonis’ focus on data-centric security and threat detection with SlashNext’s technology for blocking phishing and social engineering attacks across … Read More “Varonis buys AI email security firm SlashNext – CyberScoop” »
Jaguar has proactively shut down systems to mitigate the impact of the incident, amid reports that workers at a UK manufacturing plant had been told to stay at home – Read More –
Leaked ChatGPT Chats: Users Treat AI as Therapist, Lawyer, Confidant – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Leaked ChatGPT chats reveal users sharing sensitive data, resumes, and seeking advice on mental health, exposing risks of… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
The Harsh Truths of AI Adoption MITs State of AI in Business report revealed that while 40% of organizations have purchased enterprise LLM subscriptions, over 90% of employees are actively using AI tools in their daily work. Similarly, research from Harmonic Security found that 45.4% of sensitive AI interactions are coming from personal email accounts, … Read More “Shadow AI Discovery: A Critical Part of Enterprise AI Governance – The Hacker News” »
Ukrainian Network FDN3 Launches Massive Brute-Force Attacks on SSL VPN and RDP Devices – The Hacker News
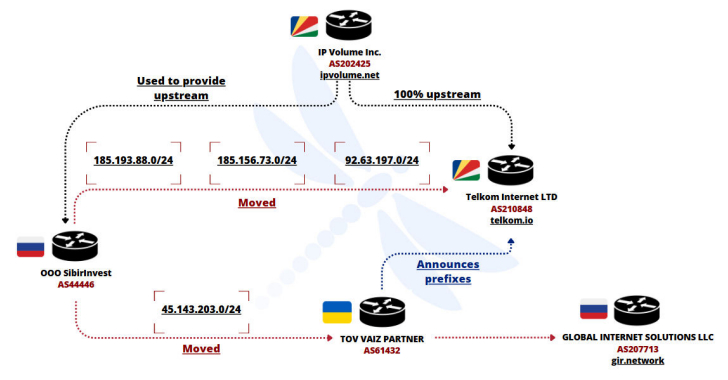
Cybersecurity researchers have flagged a Ukrainian IP network for engaging in massive brute-force and password spraying campaigns targeting SSL VPN and RDP devices between June and July 2025. The activity originated from a Ukraine-based autonomous system FDN3 (AS211736), per French cybersecurity company Intrinsec. “We believe with a high level of confidence that FDN3 is part … Read More “Ukrainian Network FDN3 Launches Massive Brute-Force Attacks on SSL VPN and RDP Devices – The Hacker News” »
Prolific Russian ransomware operator living in California enjoys rare leniency awaiting trial – CyberScoop

Authorities and threat intelligence analysts alike relish taking ransomware operators off the board. Holding cybercriminals accountable through arrest, imprisonment, or genuine reform creates a powerful deterrent and advances the ultimate goal of a safer internet for everyone. Getting to that point is a remarkably tough task for defenders. Ransomware attacks are often initiated by people … Read More “Prolific Russian ransomware operator living in California enjoys rare leniency awaiting trial – CyberScoop” »
Check Point reports Silver Fox APT using a signed WatchDog driver flaw to disable Windows security and deliver… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Silver Fox APT Exploits Signed Windows Driver to Deliver ValleyRAT – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
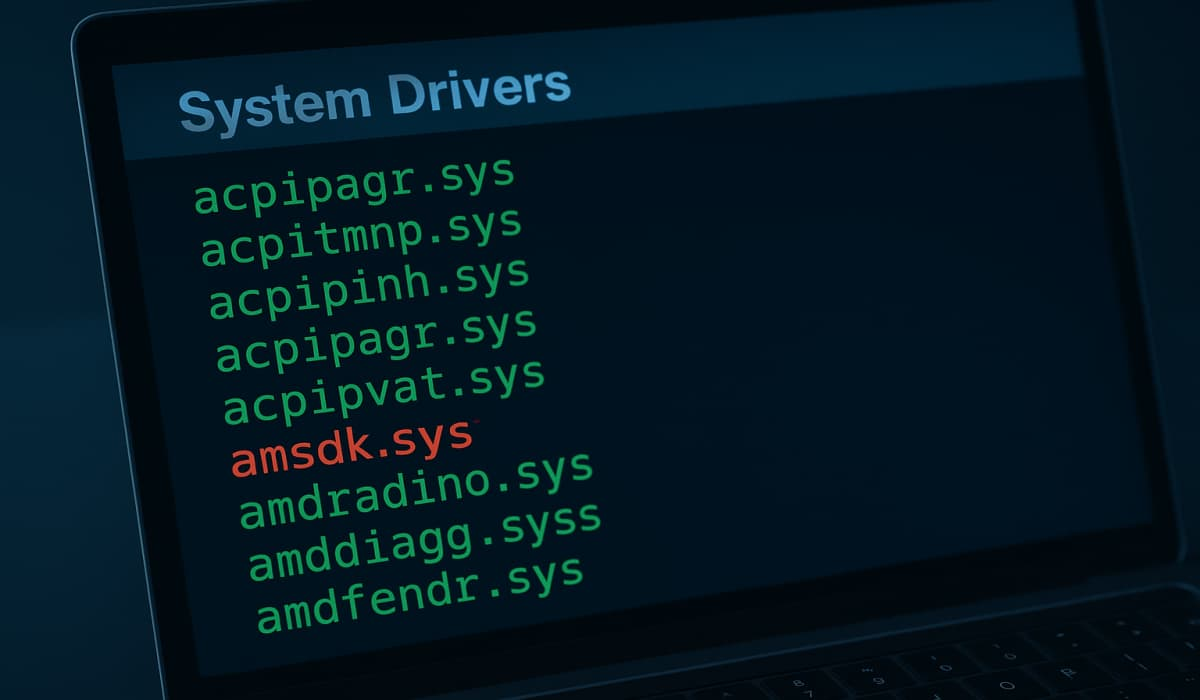
Check Point reports Silver Fox APT using a signed WatchDog driver flaw to disable Windows security and deliver… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
The UK National Cyber Security Centre thinks public disclosure programs could help mitigate AI safety threats – Read More –
The threat actor known as Silver Fox has been attributed to abuse of a previously unknown vulnerable driver associated with WatchDog Anti-malware as part of a Bring Your Own Vulnerable Driver (BYOVD) attack aimed at disarming security solutions installed on compromised hosts. The vulnerable driver in question is “amsdk.sys” (version 1.0.600), a 64-bit, validly signed … Read More “Silver Fox Exploits Microsoft-Signed WatchDog Driver to Deploy ValleyRAT Malware – The Hacker News” »
Zscaler has emerged as the latest corporate victim of a supply chain attack targeting Salesforce data – Read More –
Exploring how far cyber security approaches can help mitigate risks in generative AI systems – Read More – NCSC Feed
Malicious npm Package nodejs-smtp Mimics Nodemailer, Targets Atomic and Exodus Wallets – The Hacker News

Cybersecurity researchers have discovered a malicious npm package that comes with stealthy features to inject malicious code into desktop apps for cryptocurrency wallets like Atomic and Exodus on Windows systems. The package, named nodejs-smtp, impersonates the legitimate email library nodemailer with an identical tagline, page styling, and README descriptions, attracting a total of 347 – … Read More “Malicious npm Package nodejs-smtp Mimics Nodemailer, Targets Atomic and Exodus Wallets – The Hacker News” »
How Live Threat Intelligence Cuts Cybersecurity Expenses – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Disclosure: This article was provided by ANY.RUN. The information and analysis presented are based on their research and findings. – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
The recent mass-theft of authentication tokens from Salesloft, whose AI chatbot is used by a broad swath of corporate America to convert customer interaction into Salesforce leads, has left many companies racing to invalidate the stolen credentials before hackers can exploit them. Now Google warns the breach goes far beyond access to Salesforce data, noting … Read More “The Ongoing Fallout from a Breach at AI Chatbot Maker Salesloft – Krebs on Security” »
Hidden Commands in Images Exploit AI Chatbots and Steal Data – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

Hidden commands in images can exploit AI chatbots, leading to data theft on platforms like Gemini through a… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Generative Engine Optimisation: What It Is and Why You Need an Agency for It – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

As digital marketing keeps changing, staying ahead means adopting the latest strategies that enhance online visibility and user… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
North Korea’s ScarCruft Targets Academics With RokRAT Malware – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

A new report reveals North Korea-linked ScarCruft is using RokRAT malware to target academics in a phishing campaign.… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Cybersecurity researchers are calling attention to a new shift in the Android malware landscape where dropper apps, which are typically used to deliver banking trojans, to also distribute simpler malware such as SMS stealers and basic spyware. These campaigns are propagated via dropper apps masquerading as government or banking apps in India and other parts … Read More “Android Droppers Now Deliver SMS Stealers and Spyware, Not Just Banking Trojans – The Hacker News” »
Silver Fox APT abuses Microsoft-signed drivers to kill antivirus and deploy ValleyRAT remote-access backdoor – Read More –
A vulnerability in the WordPress Paid Memberships Subscription plugin could lead to unauthenticated SQL injection on affected sites – Read More –
⚡ Weekly Recap: WhatsApp 0-Day, Docker Bug, Salesforce Breach, Fake CAPTCHAs, Spyware App & More – The Hacker News

Cybersecurity today is less about single attacks and more about chains of small weaknesses that connect into big risks. One overlooked update, one misused account, or one hidden tool in the wrong hands can be enough to open the door. The news this week shows how attackers are mixing methods—combining stolen access, unpatched software, and … Read More “⚡ Weekly Recap: WhatsApp 0-Day, Docker Bug, Salesforce Breach, Fake CAPTCHAs, Spyware App & More – The Hacker News” »
As enterprises continue to shift their operations to the browser, security teams face a growing set of cyber challenges. In fact, over 80% of security incidents now originate from web applications accessed via Chrome, Edge, Firefox, and other browsers. One particularly fast-evolving adversary, Scattered Spider, has made it their mission to wreak havoc on enterprises … Read More “When Browsers Become the Attack Surface: Rethinking Security for Scattered Spider – The Hacker News” »
Amazon Disrupts Russian APT29 Watering Hole Targeting Microsoft Authentication – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Amazon has disrupted a Russian APT29 watering hole campaign that used compromised sites to target Microsoft authentication with… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Pennsylvania’s Attorney General confirmed the OAG had refused to pay a ransom demand to the attackers after files were encrypted – Read More –
The campaign shows APT29’s intentions to “cast a wider net in their intelligence collection efforts,” said Amazon – Read More –
Spanish police have arrested a suspected hacker for accessing a government website in order to alter the high school and university entrance exam grades of not only himself, but also some of his closest classmates. Read more in my article on the Hot for Security blog. – Read More – Graham Cluley
Adversaries targeting the Salesloft Drift application integration with Salesforce have also compromised Google Workspace accounts – Read More –
ScarCruft Uses RokRAT Malware in Operation HanKook Phantom Targeting South Korean Academics – The Hacker News
Cybersecurity researchers have discovered a new phishing campaign undertaken by the North Korea-linked hacking group called ScarCruft (aka APT37) to deliver a malware known as RokRAT. The activity has been codenamed Operation HanKook Phantom by Seqrite Labs, stating the attacks appear to target individuals associated with the National Intelligence Research Association, including academic figures – … Read More “ScarCruft Uses RokRAT Malware in Operation HanKook Phantom Targeting South Korean Academics – The Hacker News” »
WhatsApp has fixed a zero-day vulnerability linked to a sophisticated cyber-attack – Read More –
Large Language Models (LLMs) like GPT-4 and Claude are changing how businesses handle data, serve customers, and manage daily… The post Beyond Encryption: How to Secure LLM Inputs and Outputs appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Feds Seize VerifTools.Net, Operators Relaunch with VerifTools.com – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
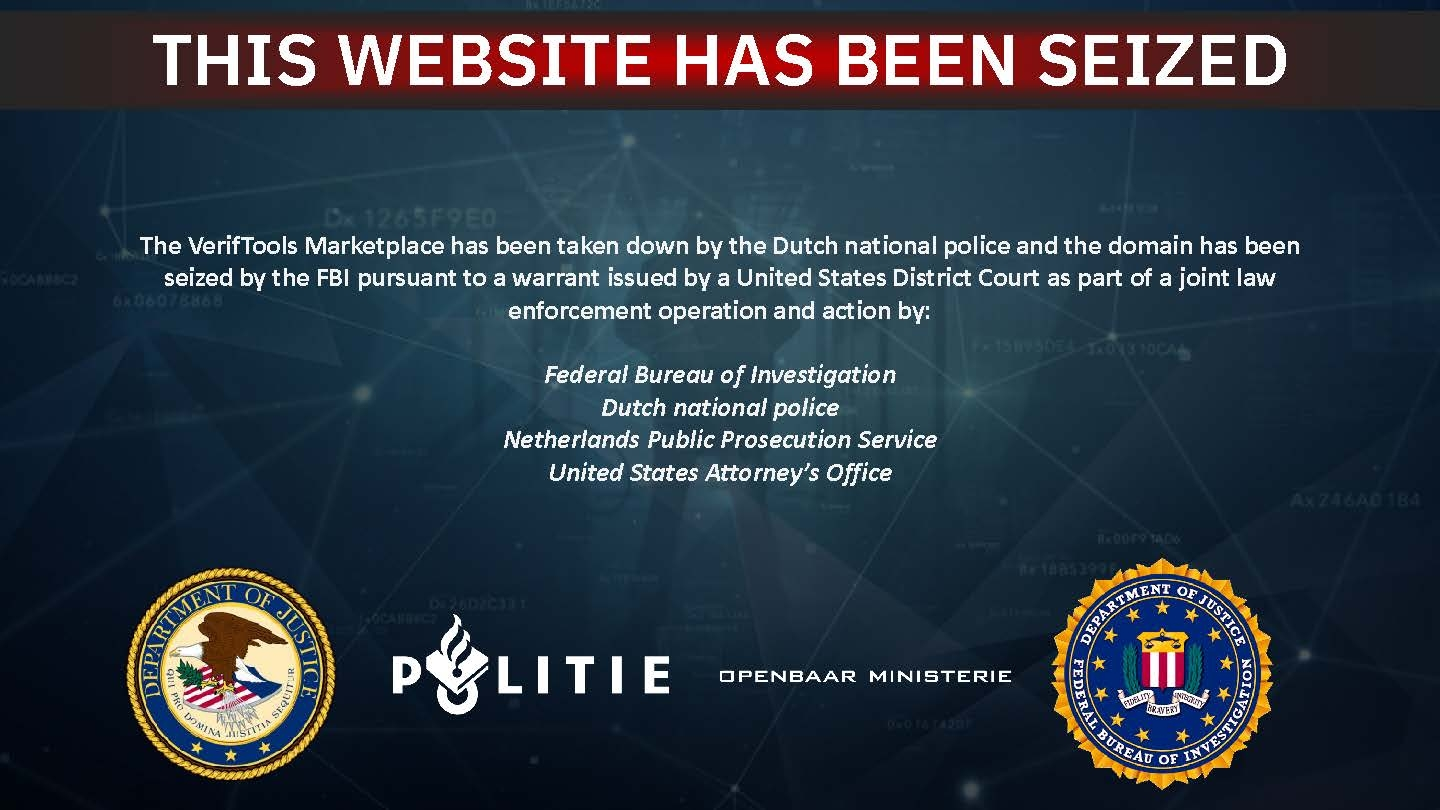
Authorities in the United States and the Netherlands have seized VerifTools, a marketplace selling fake IDs for cybercrime.… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
WhatsApp 0-Day Exploited in Attacks on Targeted iOS and macOS Users – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

WhatsApp has patched a critical 0-day (CVE-2025-55177) that allowed zero-click spyware attacks on iOS and Mac users. The… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Hackers Exploit CrushFTP Zero-Day to Take Over Servers – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

WatchTowr Labs uncovers a zero-day exploit (CVE-2025-54309) in CrushFTP. The vulnerability lets hackers gain admin access via the… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Attackers Abuse Velociraptor Forensic Tool to Deploy Visual Studio Code for C2 Tunneling – The Hacker News

Cybersecurity researchers have called attention to a cyber attack in which unknown threat actors deployed an open-source endpoint monitoring and digital forensic tool called Velociraptor, illustrating ongoing abuse of legitimate software for malicious purposes. “In this incident, the threat actor used the tool to download and execute Visual Studio Code with the likely intention of … Read More “Attackers Abuse Velociraptor Forensic Tool to Deploy Visual Studio Code for C2 Tunneling – The Hacker News” »
WhatsApp Issues Emergency Update for Zero-Click Exploit Targeting iOS and macOS Devices – The Hacker News
WhatsApp has addressed a security vulnerability in its messaging apps for Apple iOS and macOS that it said may have been exploited in the wild in conjunction with a recently disclosed Apple flaw in targeted zero-day attacks. The vulnerability, CVE-2025-55177 (CVSS score: 8.0), relates to a case of insufficient authorization of linked device synchronization messages. … Read More “WhatsApp Issues Emergency Update for Zero-Click Exploit Targeting iOS and macOS Devices – The Hacker News” »
8 Malicious NPM Packages Stole Chrome User Data on Windows – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

JFrog researchers found eight malicious NPM packages using 70 layers of obfuscation to steal data from Chrome browser… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Dexter: Resurrection Finale Leaks Online in Russian Dub – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Dexter: Resurrection finale leaks in Russian dub ahead of release. Episodes 9 and 10 surface online, echoing past… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Researchers Warn of Sitecore Exploit Chain Linking Cache Poisoning and Remote Code Execution – The Hacker News

Three new security vulnerabilities have been disclosed in the Sitecore Experience Platform that could be exploited to achieve information disclosure and remote code execution. The flaws, per watchTowr Labs, are listed below – CVE-2025-53693 – HTML cache poisoning through unsafe reflections CVE-2025-53691 – Remote code execution (RCE) through insecure deserialization CVE-2025-53694 – – Read More … Read More “Researchers Warn of Sitecore Exploit Chain Linking Cache Poisoning and Remote Code Execution – The Hacker News” »
The Federal Trade Commission thinks AI detectors might be BS. The agency announced a consent order this week with Workado, an Arizona-based company that makes an AI content detector tool. The order forces the company to retract its public claims about the tool’s effectiveness and to notify its customers. The settlement follows an investigation by … Read More “Workado settles with FTC over allegations it inflated its AI detectors’ capabilities – CyberScoop” »
The Federal Trade Commission thinks AI detectors might be BS. The agency announced a consent order this week with Workado, an Arizona-based company that makes an AI content detector tool. The order forces the company to retract its public claims about the tool’s effectiveness and to notify its customers. The settlement follows an investigation by … Read More “Workado settles with FTC over allegations it inflated its AI detectors’ capabilities – CyberScoop” »
Municipal government organisations across Sweden have found themselves impacted after a ransomware attack at a third-party software service supplier. Read more in my article on the Hot for Security blog. – Read More – Graham Cluley
Fake Facebook Ads Push Brokewell Spyware to Android Users – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
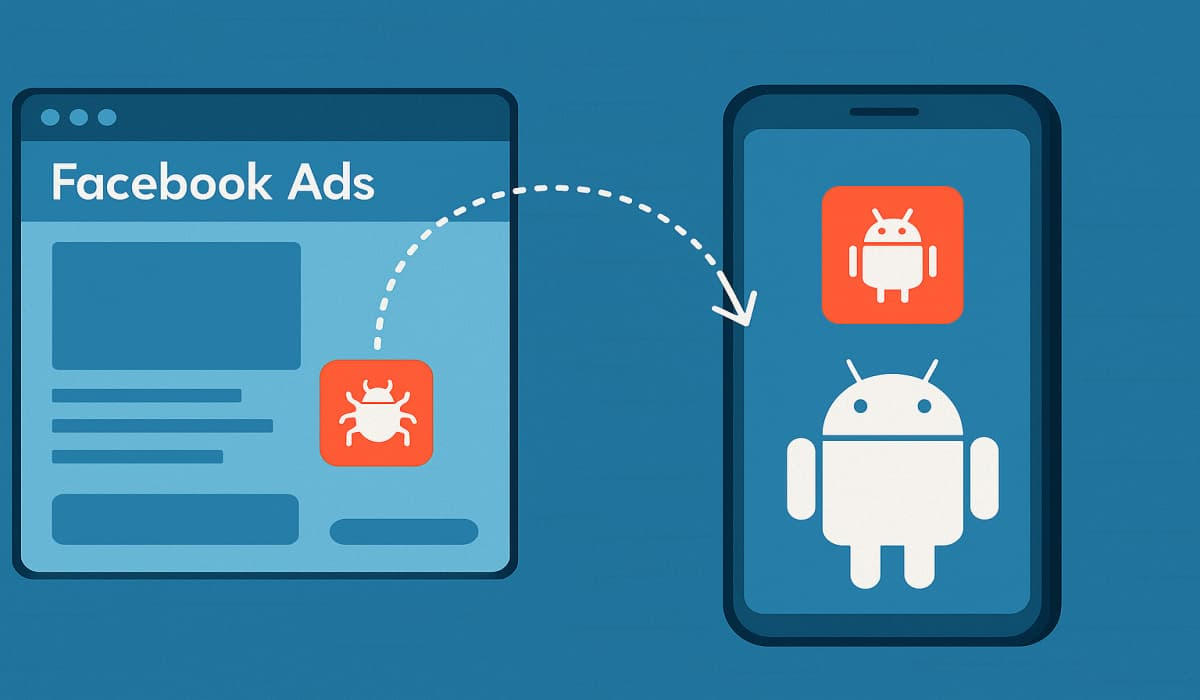
A Facebook malvertising campaign is spreading the Brokewell spyware to Android users via fake TradingView ads. The malware… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
TransUnion Data Breach: 4.4 Million US Consumers’ Data Stolen – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto

A TransUnion data breach exposed 4.4 million US consumers’ Social Security numbers via a Salesforce hack. The attack… – Read More – Hackread – Latest Cybersecurity, Hacking News, Tech, AI & Crypto
Pyongyang-backed hacking group APT37 leveraged an internal South Korean intelligence briefing in a spear phishing campaign – Read More –
Abandoned Sogou Zhuyin Update Server Hijacked, Weaponized in Taiwan Espionage Campaign – The Hacker News
An abandoned update server associated with input method editor (IME) software Sogou Zhuyin was leveraged by threat actors as part of an espionage campaign to deliver several malware families, including C6DOOR and GTELAM, in attacks primarily targeting users across Eastern Asia. “Attackers employed sophisticated infection chains, such as hijacked software updates and fake cloud storage … Read More “Abandoned Sogou Zhuyin Update Server Hijacked, Weaponized in Taiwan Espionage Campaign – The Hacker News” »
Amazon Disrupts APT29 Watering Hole Campaign Abusing Microsoft Device Code Authentication – The Hacker News

Amazon on Friday said it flagged and disrupted what it described as an opportunistic watering hole campaign orchestrated by the Russia-linked APT29 actors as part of their intelligence gathering efforts. The campaign used “compromised websites to redirect visitors to malicious infrastructure designed to trick users into authorizing attacker-controlled devices through Microsoft’s device code – Read … Read More “Amazon Disrupts APT29 Watering Hole Campaign Abusing Microsoft Device Code Authentication – The Hacker News” »
China’s reliance on domestic technology companies to carry out large-scale hacking operations—as highlighted by the U.S. government and its allies this week—is a weakness that poses risks for Beijing, a top FBI official told CyberScoop. Cyber agencies from around the world published an alert Wednesday about what officials have described as an indiscriminate cyberespionage campaign … Read More “Top FBI official says Chinese reliance on domestic firms for hacking is a weakness – CyberScoop” »