A new vulnerability dubbed “HashJack” could enable attackers to booby trap websites when they interact with AI browsers – Read More –
At least three London local authorities are dealing with a major cybersecurity incident – Read More –
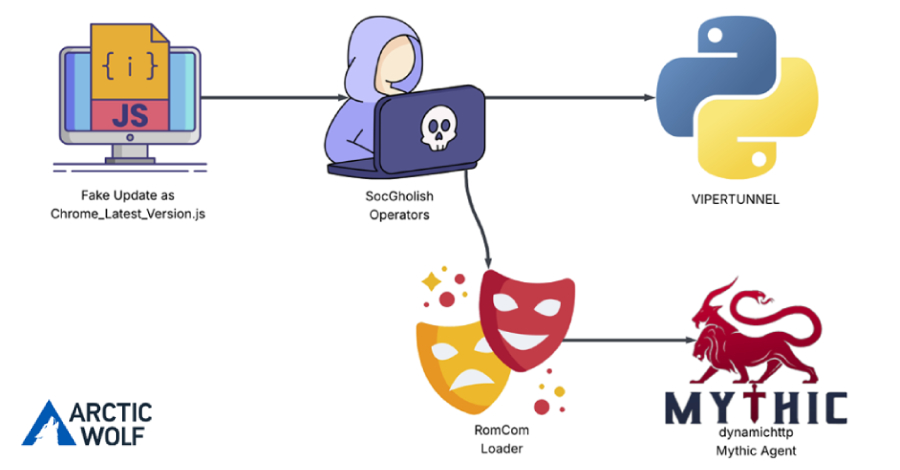
The threat actors behind a malware family known as RomCom targeted a U.S.-based civil engineering company via a JavaScript loader dubbed SocGholish to deliver the Mythic Agent. “This is the first time that a RomCom payload has been observed being distributed by SocGholish,” Arctic Wolf Labs researcher Jacob Faires said in a Tuesday report. The … Read More “RomCom Uses SocGholish Fake Update Attacks to Deliver Mythic Agent Malware – The Hacker News” »
FBI Reports $262M in ATO Fraud as Researchers Cite Growing AI Phishing and Holiday Scams – The Hacker News
The U.S. Federal Bureau of Investigation (FBI) has warned that cybercriminals are impersonating financial institutions with an aim to steal money or sensitive information to facilitate account takeover (ATO) fraud schemes. The activity targets individuals, businesses, and organizations of varied sizes and across sectors, the agency said, adding the fraudulent schemes have led to more … Read More “FBI Reports $262M in ATO Fraud as Researchers Cite Growing AI Phishing and Holiday Scams – The Hacker News” »
As legitimate businesses purchase AI tools from some of the largest companies in the world, cybercriminals are accessing an increasingly sophisticated underground market for custom LLMs designed to assist with lower-level hacking tasks. In a report published Tuesday, Palo Alto Networks’ Unit 42 looked at how underground hacking forums advertise and sell custom, jailbroken, and … Read More “Underground AI models promise to be hackers ‘cyber pentesting waifu’ – CyberScoop” »
An independent forensic investigation is underway to determine the extent of the intrusion into customer management software Gainsight’s systems and whether the breach has spread beyond Salesforce to other third-party applications. Despite this ongoing analysis, the company maintains that the impact on customer data stored within connected services is limited and largely contained. “While Salesforce … Read More “Gainsight CEO downplays impact of attack that spread to Salesforce environments – CyberScoop” »
Can We Trust AI with Our Cybersecurity? The Growing Importance of AI Security – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Artificial intelligence (AI) helps us in doing small and big things that are important in our daily lives.… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Detego Global Launches Case Management Platform for Digital Forensics and Incident Response Teams – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Horsham, United Kingdom, 25th November 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Everest ransomware claims breach at Spain’s national airline Iberia with 596 GB data theft – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
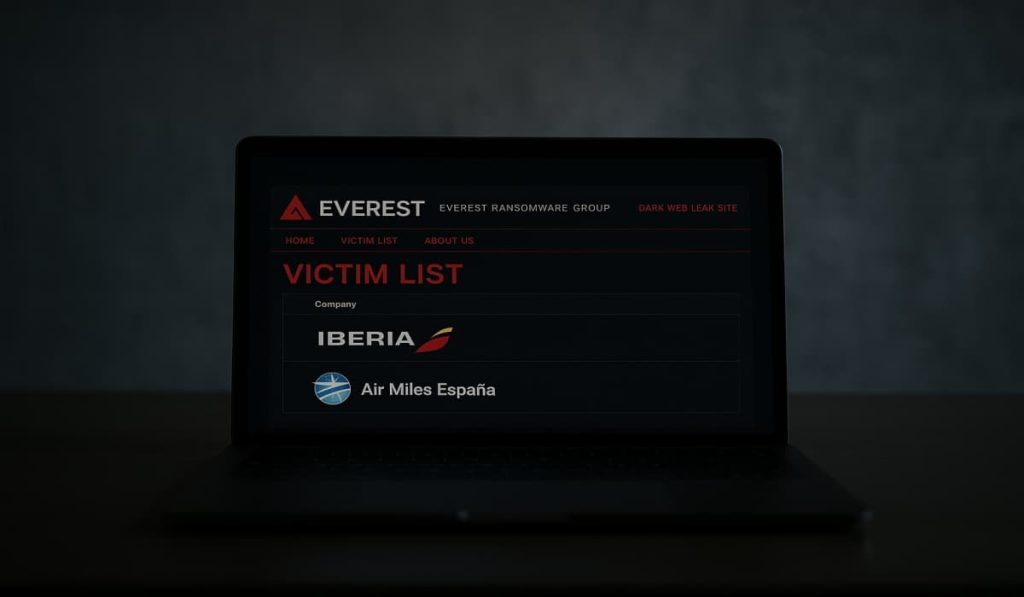
Everest claims large breaches at Iberia and Air Miles España with major data taken from both travel platforms placing millions of users at risk. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Years of JSONFormatter and CodeBeautify Leaks Expose Thousands of Passwords and API Keys – The Hacker News

New research has found that organizations in various sensitive sectors, including governments, telecoms, and critical infrastructure, are pasting passwords and credentials into online tools like JSONformatter and CodeBeautify that are used to format and validate code. Cybersecurity company watchTowr Labs said it captured a dataset of over 80,000 files on these sites, uncovering thousands of … Read More “Years of JSONFormatter and CodeBeautify Leaks Expose Thousands of Passwords and API Keys – The Hacker News” »
In episode 78 of The AI Fix, alien robot spiders invade Antarctica (or Facebook says they do), Mark prepares humanity for AI-powered fighter jets with loyalty issues, and Graham tries to work out why his AI-generated country music career hasn’t yet paid for even a Tesco Meal Deal. Anthropic claims it has caught the first … Read More “The AI Fix #78: The big AI bubble, and robot Grandma in the cloud – Graham Cluley” »
A cluster of fraudulent domains impersonating Egyptian providers have been identified linked to Smishing Triad operations – Read More –
Post Content – Read More – IC3.gov News
JackFix Uses Fake Windows Update Pop-Ups on Adult Sites to Deliver Multiple Stealers – The Hacker News
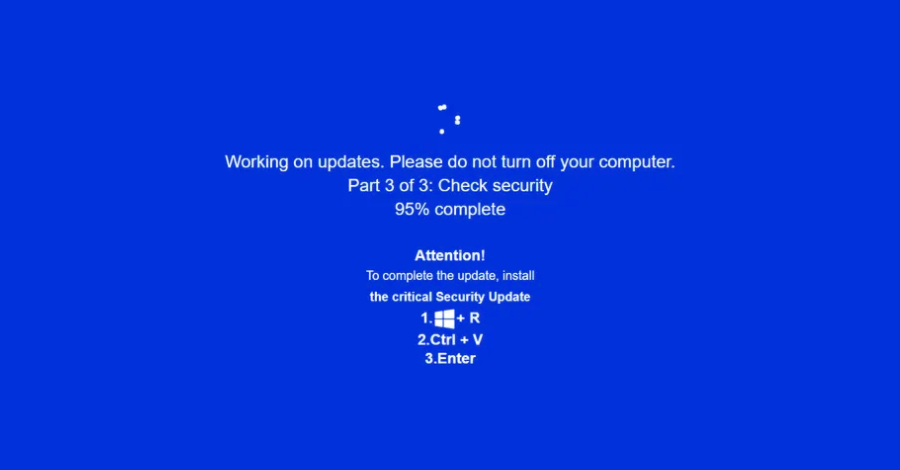
Cybersecurity researchers are calling attention to a new campaign that’s leveraging a combination of ClickFix lures and fake adult websites to deceive users into running malicious commands under the guise of a “critical” Windows security update. “Campaign leverages fake adult websites (xHamster, PornHub clones) as its phishing mechanism, likely distributed via malvertising,” Acronis said in … Read More “JackFix Uses Fake Windows Update Pop-Ups on Adult Sites to Deliver Multiple Stealers – The Hacker News” »
Update Firefox to Patch CVE-2025-13016 Vulnerability Affecting 180 Million Users – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

AI security firm AISLE revealed CVE-2025-13016, a critical Firefox Wasm bug that risked 180M users for six months. Learn how the memory flaw allowed code execution. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Thinking Beyond Price: What Tech Teams Should Look for in a Hosting Provider – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Discover why reliability, scalability, and local support matter more than cost when choosing Australian web hosting for your tech stack. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
A new macOS malware chain using staged scripts and a Go-based backdoor has been attributed to FlexibleFerret, designed to steal credentials and maintain system access – Read More –
The threat actor known as ToddyCat has been observed adopting new methods to obtain access to corporate email data belonging to target companies, including using a custom tool dubbed TCSectorCopy. “This attack allows them to obtain tokens for the OAuth 2.0 authorization protocol using the user’s browser, which can be used outside the perimeter of … Read More “ToddyCat’s New Hacking Tools Steal Outlook Emails and Microsoft 365 Access Tokens – The Hacker News” »
Cybersecurity researchers have disclosed details of a new campaign that has leveraged Blender Foundation files to deliver an information stealer known as StealC V2. “This ongoing operation, active for at least six months, involves implanting malicious .blend files on platforms like CGTrader,” Morphisec researcher Shmuel Uzan said in a report shared with The Hacker News. … Read More “Hackers Hijack Blender 3D Assets to Deploy StealC V2 Data-Stealing Malware – The Hacker News” »
2026 will mark a pivotal shift in cybersecurity. Threat actors are moving from experimenting with AI to making it their primary weapon, using it to scale attacks, automate reconnaissance, and craft hyper-realistic social engineering campaigns. The Storm on the Horizon Global world instability, coupled with rapid technological advancement, will force security teams to adapt not … Read More “3 SOC Challenges You Need to Solve Before 2026 – The Hacker News” »
In its latest annual identity fraud report, Sumsub observed a “sophistication shift” in global fraud trends – Read More –
Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user an attacker could then install programs; … Read More “Multiple Vulnerabilities in Google Chrome Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
A vulnerability has been discovered SonicOS, which could allow for Denial of Service (DoS). SonicOS is the operating system that runs on SonicWall’s network security appliances, such as firewalls. Successful exploitation of this vulnerability could allow a remote unauthenticated attacker to cause Denial of Service (DoS), which could cause an impacted firewall to crash. This vulnerability … Read More “A Vulnerability in SonicOS Could Allow for Denial of Service (DoS) – Cyber Security Advisories – MS-ISAC” »
MPs in the UK want a new economic security regime to tackle cyber and related threats – Read More –
A new version of the Shai-Hulud worm has infected hundreds of npm packages and caused disruption to global CI/CD workflows – Read More –
CISA Warns of Active Spyware Campaigns Hijacking High-Value Signal and WhatsApp Users – The Hacker News

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday issued an alert warning of bad actors actively leveraging commercial spyware and remote access trojans (RATs) to target users of mobile messaging applications. “These cyber actors use sophisticated targeting and social engineering techniques to deliver spyware and gain unauthorized access to a victim’s messaging app, … Read More “CISA Warns of Active Spyware Campaigns Hijacking High-Value Signal and WhatsApp Users – The Hacker News” »
There is an unprecedented transformation in the enterprise security environment. Quantum computing that used to be a remote scholarly… The post Quantum Computing Risks: What CISOs Must Prepare for Before 2026 appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Security researchers and authorities are warning about a fresh wave of supply-chain attacks linked to a self-replicating worm that attackers have injected into almost 500 npm (node.js package manager) software packages, exposing more than 26,000 open-source repositories on GitHub. The trojanized npm packages, which were first discovered late Sunday by Charlie Eriksen, security researcher at … Read More “Shai-Hulud worm returns stronger and more automated than ever before – CyberScoop” »
According to Anthropic, its large language model Claude is designed to be a “harmless” and helpful assistant. But new research released by the company Nov. 21 shows that when Claude is taught to cheat in one area, it becomes broadly malicious and untrustworthy in other areas. The research, conducted by 21 people — including contributors … Read More “New research finds that Claude breaks bad if you teach it to cheat – CyberScoop” »
The Cybersecurity and Infrastructure Security Agency warned Monday about threat groups using commercial spyware to target messaging apps, and urged users to take protective steps. “CISA is aware of multiple cyber threat actors actively leveraging commercial spyware to target users of mobile messaging applications (apps),” the agency said in a brief online notice. “These cyber … Read More “CISA alert draws attention to spyware’s targeting of messaging apps – CyberScoop” »
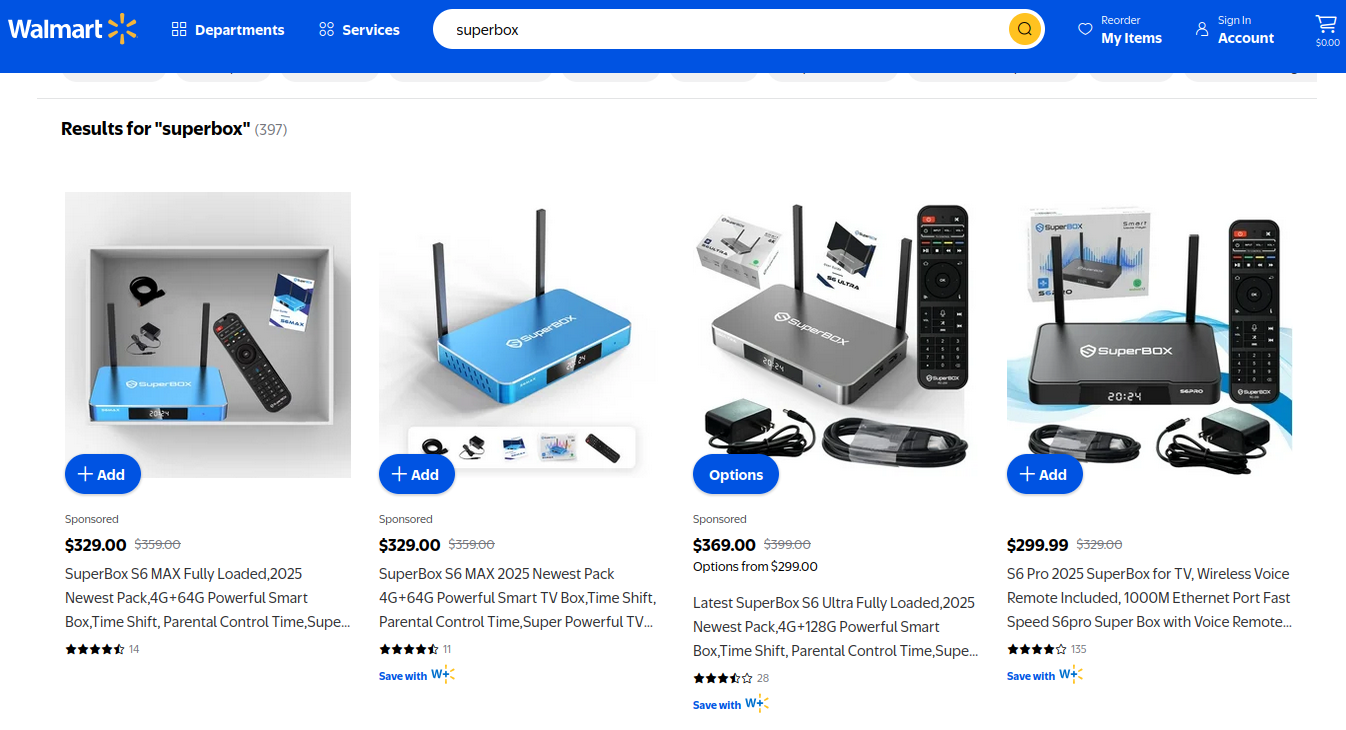
On the surface, the Superbox media streaming devices for sale at retailers like BestBuy and Walmart may seem like a steal: They offer unlimited access to more than 2,200 pay-per-view and streaming services like Netflix, ESPN and Hulu, all for a one-time fee of around $400. But security experts warn these TV boxes require intrusive … Read More “Is Your Android TV Streaming Box Part of a Botnet? – Krebs on Security” »
How To Hide Your Country Location on X (Twitter) by Switching to Region – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
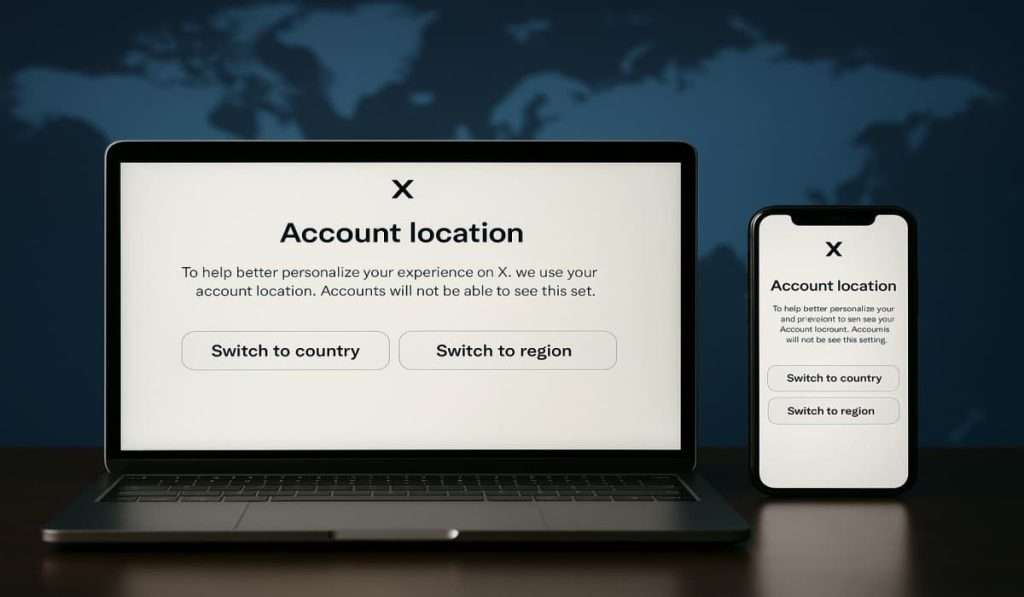
X (formerly known as Twitter) has added a new location detail in its account transparency section. It shows… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Shai Hulud npm Worm Impacts 26,000+ Repos in Supply Chain Attack – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

The Shai Hulud worm’s “Second Coming” has compromised over 26,000 public repositories. We detail the attacker’s mistake, the target packages, and mandatory security tips. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
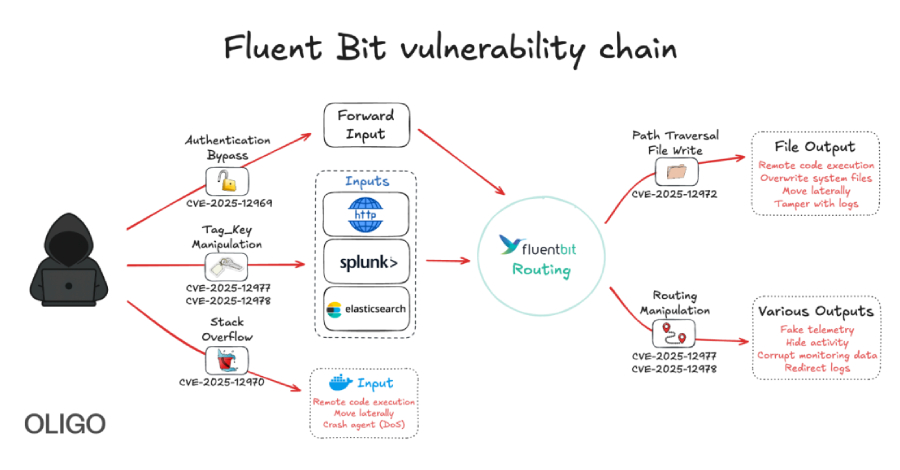
Cybersecurity researchers have discovered five vulnerabilities in Fluent Bit, an open-source and lightweight telemetry agent, that could be chained to compromise and take over cloud infrastructures. The security defects “allow attackers to bypass authentication, perform path traversal, achieve remote code execution, cause denial-of-service conditions, and manipulate tags,” Oligo Security said in – Read More – … Read More “New Fluent Bit Flaws Expose Cloud to RCE and Stealthy Infrastructure Intrusions – The Hacker News” »
Some cybersecurity advice has been around for ages: Frequently change passwords, avoid public Wi-Fi. But most experts say a lot of that knowledge is rooted in myth. On Monday, an initiative launched to counter those stubborn misconceptions, on the notion that their persistence is actually harmful to what keeps people secure. Bob Lord, a former … Read More “This campaign aims to tackle persistent security myths in favor of better advice – CyberScoop” »
Critical flaws in Fluent Bit threaten telemetry across platforms according to an advisory published by Oligo Security researchers – Read More –
Fake Prettier Extension on VSCode Marketplace Dropped Anivia Stealer – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
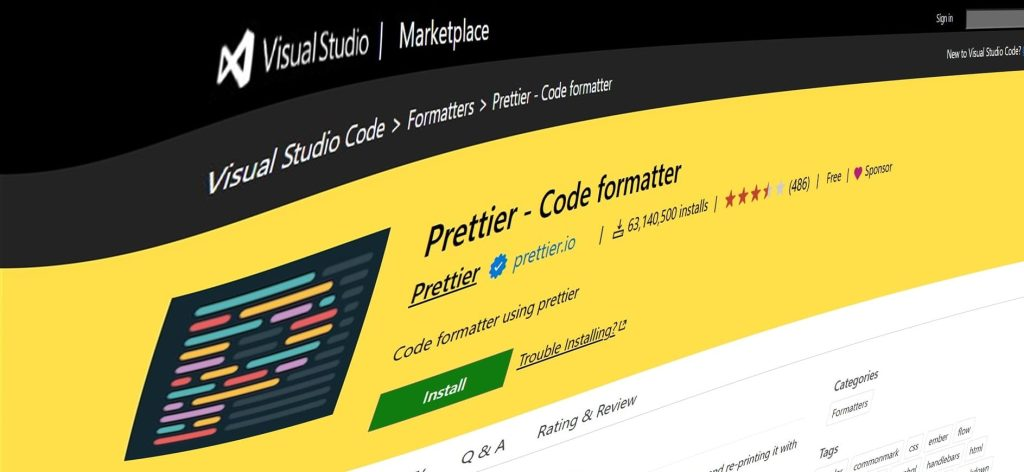
Cybersecurity firm Checkmarx Zero, in collaboration with Microsoft, removed a malicious ‘prettier-vscode-plus’ extension from the VSCode Marketplace. The fake coding tool was a Brandjacking attempt designed to deploy Anivia Stealer malware and steal Windows user credentials and data. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Elite Cyber Veterans Launch Blast Security with $10M to Turn Cloud Detection into Prevention – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Tel Aviv, Israel, 24th November 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Morphisec has observed a new operation embedding StealC V2 malware in Blender project files, targeting users via 3D assets and launching a multi-stage infection chain – Read More –
Elite Cyber Veterans Launch Blast Security with $10M to Turn Cloud Detection into Prevention – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Tel Aviv, Israel, 24th November 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
⚡ Weekly Recap: Fortinet Exploit, Chrome 0-Day, BadIIS Malware, Record DDoS, SaaS Breach & More – The Hacker News

This week saw a lot of new cyber trouble. Hackers hit Fortinet and Chrome with new 0-day bugs. They also broke into supply chains and SaaS tools. Many hid inside trusted apps, browser alerts, and software updates. Big firms like Microsoft, Salesforce, and Google had to react fast — stopping DDoS attacks, blocking bad links, … Read More “⚡ Weekly Recap: Fortinet Exploit, Chrome 0-Day, BadIIS Malware, Record DDoS, SaaS Breach & More – The Hacker News” »
Second Sha1-Hulud Wave Affects 25,000+ Repositories via npm Preinstall Credential Theft – The Hacker News
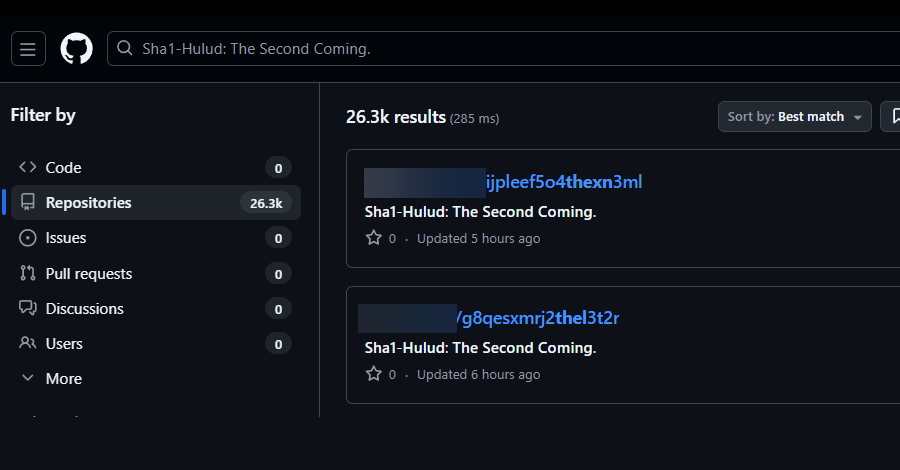
Multiple security vendors are sounding the alarm about a second wave of attacks targeting the npm registry in a manner that’s reminiscent of the Shai-Hulud attack. The new supply chain campaign, dubbed Sha1-Hulud, has compromised hundreds of npm packages, according to reports from Aikido, HelixGuard, Koi Security, Socket, and Wiz. “The campaign introduces a new … Read More “Second Sha1-Hulud Wave Affects 25,000+ Repositories via npm Preinstall Credential Theft – The Hacker News” »
New RadzaRat Spyware Poses as File Manager to Hijack Android Devices – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Certo Software found RadzaRat, an Android RAT disguised as a file manager that has a 0/66 detection rate on VirusTotal. It keylogs passwords and steals files. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Chinese DeepSeek-R1 AI Generates Insecure Code When Prompts Mention Tibet or Uyghurs – The Hacker News

New research from CrowdStrike has revealed that DeepSeek’s artificial intelligence (AI) reasoning model DeepSeek-R1 produces more security vulnerabilities in response to prompts that contain topics deemed politically sensitive by China. “We found that when DeepSeek-R1 receives prompts containing topics the Chinese Communist Party (CCP) likely considers politically sensitive, the likelihood of it – Read More … Read More “Chinese DeepSeek-R1 AI Generates Insecure Code When Prompts Mention Tibet or Uyghurs – The Hacker News” »
Open-source components power nearly all modern software, but they’re often buried deep in massive codebases—hiding severe vulnerabilities. For years, software bills of materials (SBOMs) have been the security community’s key tool to shine a light on these hidden risks. Yet, despite government advancements in the US and Europe, SBOM adoption in the private sector remains … Read More “The slow rise of SBOMs meets the rapid advance of AI – CyberScoop” »
The recent Salesloft Drift breach offered a sobering reminder of how easily trust can be weaponized in today’s SaaS and AI-integrated environments. In this incident, hackers exploited the Drift chatbot, stole OAuth tokens, and used them to obtain data from CRM systems before the tokens could be revoked. In the wake of the incident, many … Read More “When trust turns toxic: Lessons from the Salesloft Drift incident – CyberScoop” »
The US cybersecurity agency has added the critical flaw to its Known Exploited Vulnerabilities list – Read More –
Spanish airline Iberia has begun emailing its customers about a supplier data breach – Read More –
International cybercrime-fighting agencies, co-ordinated by Europol, took down over 1000 servers and seized 20 domains earlier this month as part of Operation Endgame 3.0. Their target? Three major malware platforms: the infostealer known as Rhadamanthys, the VenomRAT remote access trojan, and the Elysium botnet. Read more in my article on the Hot for Security blog. … Read More “Operation Endgame disrupts Rhadamanthys information-stealing malware – Graham Cluley” »
The International Defence Esports Games (IDEG) will help sharpen cyber and battlefield skills for allied soldiers – Read More –