Quttera Launches “Evidence-as-Code” API to Automate Security Compliance for SOC 2 and PCI DSS v4.0 – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
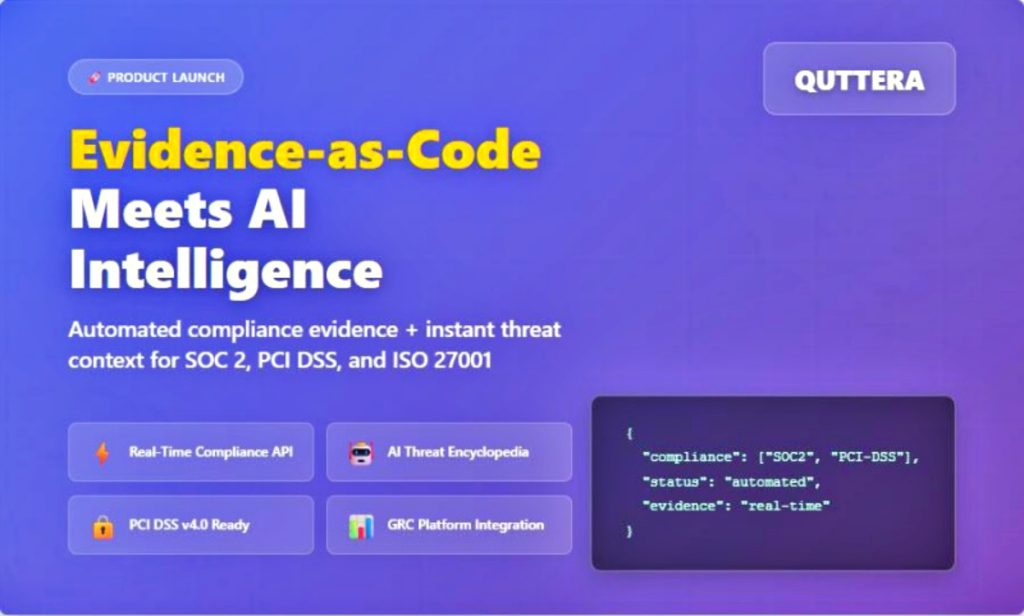
New API capabilities and AI-powered Threat Encyclopedia eliminate manual audit preparation, providing real-time compliance evidence and instant threat intelligence. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More