CISA has issued a new directive requiring federal agencies to decommission all end of support edge devices within 12 months to reduce ongoing exploitation risks – Read More –
BeyondTrust has released updates to address a critical security flaw impacting Remote Support (RS) and Privileged Remote Access (PRA) products that, if successfully exploited, could result in remote code execution. “BeyondTrust Remote Support (RS) and certain older versions of Privileged Remote Access (PRA) contain a critical pre-authentication remote code execution vulnerability,” the company – Read … Read More “BeyondTrust Fixes Critical Pre-Auth RCE Vulnerability in Remote Support and PRA – The Hacker News” »
8 Top MDR Providers for Mid-Market Companies – Hackread – Cybersecurity News, Data Breaches, AI and More

Top 8 MDR providers for mid-market firms needing expert detection, faster response, and reduced noise without building full in-house SOCs. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
UK Construction Firm Hit by Prometei Botnet Hiding in Windows Server – Hackread – Cybersecurity News, Data Breaches, AI and More

Cybersecurity firm eSentire’s TRU break down the Russian Prometei botnet attack on a UK firm, detailing its TOR usage, password theft and decoy tactics. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
OpenClaw (formerly Moltbot and Clawdbot) has announced that it’s partnering with Google-owned VirusTotal to scan skills that are being uploaded to ClawHub, its skill marketplace, as part of broader efforts to bolster the security of the agentic ecosystem. “All skills published to ClawHub are now scanned using VirusTotal’s threat intelligence, including their new Code Insight … Read More “OpenClaw Integrates VirusTotal Scanning to Detect Malicious ClawHub Skills – The Hacker News” »
Posted by Asterisk Development Team via Fulldisclosure on Feb 07 The Asterisk Development Team would like to announce security release Certified Asterisk 20.7-cert9. The release artifacts are available for immediate download at https://github.com/asterisk/asterisk/releases/tag/certified-20.7-cert9 and https://downloads.asterisk.org/pub/telephony/certified-asterisk Repository: https://github.com/asterisk/asterisk Tag: certified-20.7-cert9 ## Change Log for Release asterisk-certified-20.7-cert9 ###… – Read More – Full Disclosure
Posted by Asterisk Development Team via Fulldisclosure on Feb 07 The Asterisk Development Team would like to announce security release Asterisk 20.18.2. The release artifacts are available for immediate download at https://github.com/asterisk/asterisk/releases/tag/20.18.2 and https://downloads.asterisk.org/pub/telephony/asterisk Repository: https://github.com/asterisk/asterisk Tag: 20.18.2 ## Change Log for Release asterisk-20.18.2 ### Links: – [Full ChangeLog](… – Read More – Full Disclosure
Posted by Asterisk Development Team via Fulldisclosure on Feb 07 The Asterisk Development Team would like to announce security release Asterisk 22.8.2. The release artifacts are available for immediate download at https://github.com/asterisk/asterisk/releases/tag/22.8.2 and https://downloads.asterisk.org/pub/telephony/asterisk Repository: https://github.com/asterisk/asterisk Tag: 22.8.2 ## Change Log for Release asterisk-22.8.2 ### Links: – [Full ChangeLog](… – Read More – Full Disclosure
Posted by Asterisk Development Team via Fulldisclosure on Feb 07 The Asterisk Development Team would like to announce security release Asterisk 21.12.1. The release artifacts are available for immediate download at https://github.com/asterisk/asterisk/releases/tag/21.12.1 and https://downloads.asterisk.org/pub/telephony/asterisk Repository: https://github.com/asterisk/asterisk Tag: 21.12.1 ## Change Log for Release asterisk-21.12.1 ### Links: – [Full ChangeLog](… – Read More – Full Disclosure
Posted by Asterisk Development Team via Fulldisclosure on Feb 07 The Asterisk Development Team would like to announce security release Asterisk 23.2.2. The release artifacts are available for immediate download at https://github.com/asterisk/asterisk/releases/tag/23.2.2 and https://downloads.asterisk.org/pub/telephony/asterisk Repository: https://github.com/asterisk/asterisk Tag: 23.2.2 ## Change Log for Release asterisk-23.2.2 ### Links: – [Full ChangeLog](… – Read More – Full Disclosure
Bithumb Mistakenly Sends 620,000 Bitcoin ($40B) to Customer Accounts – Hackread – Cybersecurity News, Data Breaches, AI and More

A system error at Bithumb sent 620,000 Bitcoin worth about $40B to hundreds of users during a promotion, briefly disrupting prices and drawing scrutiny. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Firefox Will Give Users an AI Kill Switch for Better Privacy – Hackread – Cybersecurity News, Data Breaches, AI and More

Not everyone wants AI in their browser. Firefox 148 is introducing easy toggles to disable chatbots and AI tab grouping. Discover how Mozilla is prioritising user choice and privacy in its latest 2026 update. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
When a Romanian businesswoman fell for a fake Dubai Crown Prince in a $2.5 million romance scam, investigators tracked the fraudster to his Nigerian mansion – only to discover he was masquerading as a campaigning philanthropist. Read more in my article on the Hot for Security blog. – Read More – GRAHAM CLULEY
German Agencies Warn of Signal Phishing Targeting Politicians, Military, Journalists – The Hacker News

Germany’s Federal Office for the Protection of the Constitution (aka Bundesamt für Verfassungsschutz or BfV) and Federal Office for Information Security (BSI) have issued a joint advisory warning of a malicious cyber campaign undertaken by a likely state-sponsored threat actor that involves carrying out phishing attacks over the Signal messaging app. “The focus is on … Read More “German Agencies Warn of Signal Phishing Targeting Politicians, Military, Journalists – The Hacker News” »
The Department of Homeland Security’s watchdog office has launched an audit of the agency’s privacy practices amid allegations that DHS and its components have used facial recognition tools and other technologies to collect data broadly and violate civil liberties. The audit, according to a Feb. 5 letter from DHS Inspector General Joseph Cuffari and published … Read More “DHS privacy probe will focus on biometric tracking by ICE, OBIM – CyberScoop” »
Substack did not specify the number of users affected by the data breach – Read More –
DKnife is a Chinese made malware framework that targets Chinese-based users – Read More –
Flickr Notifies Users of Data Breach After External Partner Security Flaw – Hackread – Cybersecurity News, Data Breaches, AI and More

Flickr says a third-party email vendor flaw may have exposed user names, emails, IP data, and activity logs,… – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
China-Linked DKnife AitM Framework Targets Routers for Traffic Hijacking, Malware Delivery – The Hacker News
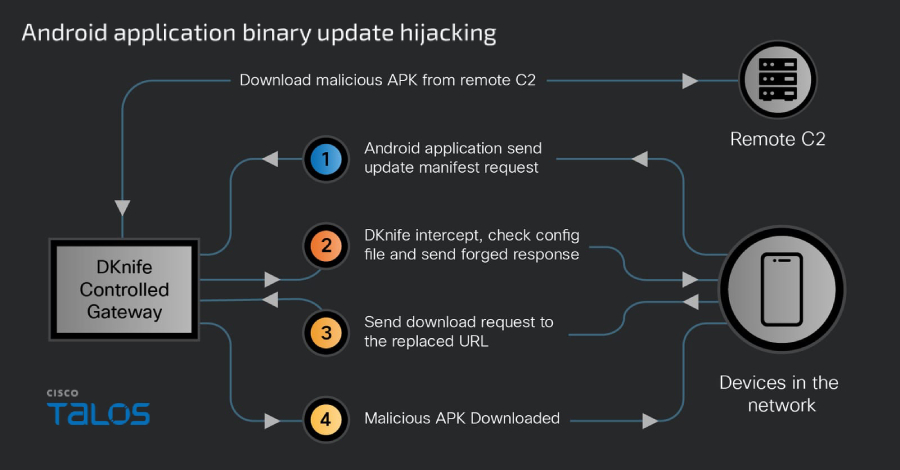
Cybersecurity researchers have taken the wraps off a gateway-monitoring and adversary-in-the-middle (AitM) framework dubbed DKnife that’s operated by China-nexus threat actors since at least 2019. The framework comprises seven Linux-based implants that are designed to perform deep packet inspection, manipulate traffic, and deliver malware via routers and edge devices. Its primary targets seem to – … Read More “China-Linked DKnife AitM Framework Targets Routers for Traffic Hijacking, Malware Delivery – The Hacker News” »
17% of 3rd-Party Add-Ons for OpenClaw Used in Crypto Theft and macOS Malware – Hackread – Cybersecurity News, Data Breaches, AI and More

Bitdefender Labs reveals that 17% of OpenClaw AI skills analyzed in February 2026 are malicious. With over 160,000… – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has ordered Federal Civilian Executive Branch (FCEB) agencies to strengthen asset lifecycle management for edge network devices and remove those that no longer receive security updates from original equipment manufacturers (OEMs) over the next 12 to 18 months. The agency said the move is to drive down … Read More “CISA Orders Removal of Unsupported Edge Devices to Reduce Federal Network Risk – The Hacker News” »
A Victorian school teacher was applying for ‘heaps of rentals’ online – then someone accessed his bank account – Data and computer security | The Guardian

Michael suspects personal information he submitted to rent application platforms was leaked online. And analysis shows millions of documents may also be at risk Get our breaking news email, free app or daily news podcast Michael* has spent the past two months trying to get his digital identity back. The 47-year-old Victorian school teacher was … Read More “A Victorian school teacher was applying for ‘heaps of rentals’ online – then someone accessed his bank account – Data and computer security | The Guardian” »
Asian State-Backed Group TGR-STA-1030 Breaches 70 Government, Infrastructure Entities – The Hacker News

A previously undocumented cyber espionage group operating from Asia broke into the networks of at least 70 government and critical infrastructure organizations across 37 countries over the past year, according to new findings from Palo Alto Networks Unit 42. In addition, the hacking crew has been observed conducting active reconnaissance against government infrastructure associated with … Read More “Asian State-Backed Group TGR-STA-1030 Breaches 70 Government, Infrastructure Entities – The Hacker News” »
As you know, enterprise network security has undergone significant evolution over the past decade. Firewalls have become more intelligent, threat detection methods have advanced, and access controls are now more detailed. However (and it’s a big “however”), the increasing use of mobile devices in business operations necessitates network security measures that are specifically – Read … Read More “How Samsung Knox Helps Stop Your Network Security Breach – The Hacker News” »
Cybersecurity researchers have discovered a new supply chain attack in which legitimate packages on npm and the Python Package Index (PyPI) repository have been compromised to push malicious versions to facilitate wallet credential theft and remote code execution. The compromised versions of the two packages are listed below – @dydxprotocol/v4-client-js (npm) – 3.4.1, 1.22.1, 1.15.2, … Read More “Compromised dYdX npm and PyPI Packages Deliver Wallet Stealers and RAT Malware – The Hacker News” »
Infosecurity Europe 2026 will debut a new Cyber Startup Programme, featuring a dedicated show-floor zone for early-stage cybersecurity companies to showcase innovations, connect with investors and highlight emerging technologies – Read More –
Artificial intelligence (AI) company Anthropic revealed that its latest large language model (LLM), Claude Opus 4.6, has found more than 500 previously unknown high-severity security flaws in open-source libraries, including Ghostscript, OpenSC, and CGIF. Claude Opus 4.6, which was launched on Thursday, comes with improved coding skills, including code review and debugging capabilities, along – … Read More “Claude Opus 4.6 Finds 500+ High-Severity Flaws Across Major Open-Source Libraries – The Hacker News” »
National Threat Level: Blue (Guarded) This threat level is based on analysis by the Center for Internet Security® (CIS®) Operations, Intelligence, and Services (OIS) department covering the cyber threat landscape for Quarter 4 (Q4) of 2025. In calendar year 2025Q4, OIS published 26 Cybersecurity Advisories for critical severity high risk vulnerabilities in popular software applications … Read More “Threat Level – GUARDED – Cyber Threat Alert” »
Cryptography has become the invisible infrastructure of the digital economy. Every payment, every identity, every medical record, and every… The post Industry-Aligned Cryptography by CryptoBind appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Substack Breach: 662,752 User Records Leaked on Cybercrime Forum – Hackread – Cybersecurity News, Data Breaches, AI and More

Substack confirms a breach after hacker accessed internal user records now circulating on crime forums, exposing emails, phone numbers, and account metadata. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Incognito Market admin sentenced to 30 years for running $105 million dark web drug empire – GRAHAM CLULEY
He promised “the best security there is” to hundreds of thousands of drug buyers, while quietly making the kind of mistake that guaranteed a 30-year sentence. And maybe training police on cryptocurrency while running a running a vast Tor-hidden drug bazaar wasn’t such a good idea. Read more in my article on the Hot for … Read More “Incognito Market admin sentenced to 30 years for running $105 million dark web drug empire – GRAHAM CLULEY” »
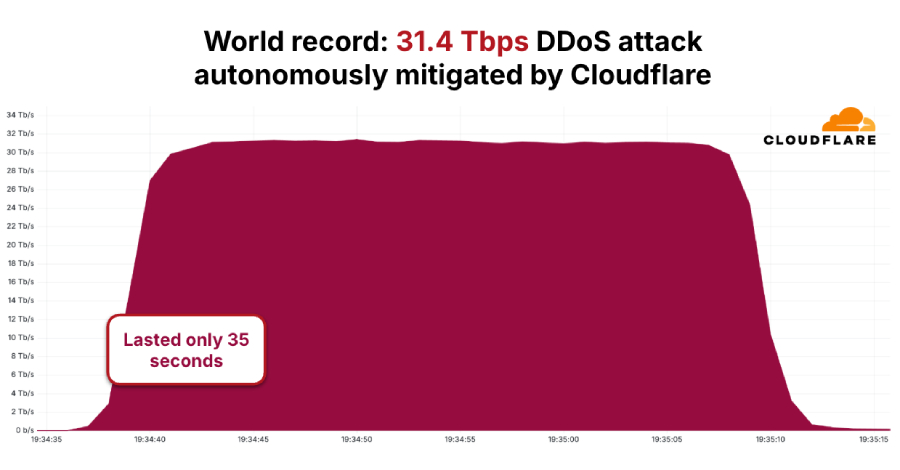
The distributed denial-of-service (DDoS) botnet known as AISURU/Kimwolf has been attributed to a record-setting attack that peaked at 31.4 Terabits per second (Tbps) and lasted only 35 seconds. Cloudflare, which automatically detected and mitigated the activity, said it’s part of a growing number of hyper-volumetric HTTP DDoS attacks mounted by the botnet in the fourth … Read More “AISURU/Kimwolf Botnet Launches Record-Setting 31.4 Tbps DDoS Attack – The Hacker News” »
A Cybersecurity and Infrastructure Security Agency order published Thursday directs federal agencies to stop using “edge devices” like firewalls and routers that their manufacturers no longer support. It’s a stab at tackling one of the most persistent and difficult-to-manage avenues of attack for hackers, a vector that has factored into some of the most consequential … Read More “CISA tells agencies to stop using unsupported edge devices – CyberScoop” »
A 23-year-old New York man allegedly affiliated with 764 was arrested and charged with receiving child sexual abuse material. Aaron Corey of Albany, N.Y., faces up to 20 years in prison for trafficking CSAM during a three-month period ending in December. Corey, also known as “Baggeth,” is accused of running multiple 764-related chats, seeking CSAM … Read More “Alleged 764 member arrested, charged with CSAM possession in New York – CyberScoop” »
In this excerpt of a TrendAI Research Services vulnerability report, Jonathan Lein and Simon Humbert of the TrendAI Research team detail a recently patched command injection vulnerability in the Arista NG Firewall. This bug was originally discovered by Gereon Huppertz and reported through the TrendAI Zero Day Initiative (ZDI) program. Successful exploitation could result in … Read More “CVE-2025-6978: Arbitrary Code Execution in the Arista NG Firewall – Zero Day Initiative – Blog” »
macOS Users Hit by Python Infostealers Posing as AI Installers – Hackread – Cybersecurity News, Data Breaches, AI and More

Microsoft details 3 Python Infostealers hitting macOS users via fake AI tools, Google ads, and Terminal tricks to steal passwords and crypto, then erase traces. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Common Crypto Scams and How to Protect Your Funds in 2026 – Hackread – Cybersecurity News, Data Breaches, AI and More

Crypto scams are surging worldwide, from pig butchering to fake trading platforms and deepfakes, draining victims while fraud teams struggle to keep up. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Godent Rolls Out Scanner-as-a-Service Model to Drive Digital Transformation in European Dentistry – Hackread – Cybersecurity News, Data Breaches, AI and More

Godent has announced the launch of its scanner-as-a-service program for European DSOs, combining free intraoral scanners with a fully integrated digital lab infrastructure to modernize dental workflows. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Sanctioned Bulletproof Host Linked to Hijacking of Old Home Routers – Hackread – Cybersecurity News, Data Breaches, AI and More
Compromised home routers in 30+ countries had DNS traffic redirected, sending users to malicious sites while normal browsing appeared unaffected. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Threat hunters have disclosed details of a new, stealthy malware campaign dubbed DEAD#VAX that employs a mix of “disciplined tradecraft and clever abuse of legitimate system features” to bypass traditional detection mechanisms and deploy a remote access trojan (RAT) known as AsyncRAT. “The attack leverages IPFS-hosted VHD files, extreme script obfuscation, runtime decryption, and in-memory … Read More “DEAD#VAX Malware Campaign Deploys AsyncRAT via IPFS-Hosted VHD Phishing Files – The Hacker News” »
Cellebrite data confirms digital evidence is now central to almost all cases – Read More –
Flaws in GitHub Codespaces allow RCE via crafted repositories or pull requests – Read More –
ThreatsDay Bulletin: Codespaces RCE, AsyncRAT C2, BYOVD Abuse, AI Cloud Intrusions & 15+ Stories – The Hacker News

This week didn’t produce one big headline. It produced many small signals — the kind that quietly shape what attacks will look like next. Researchers tracked intrusions that start in ordinary places: developer workflows, remote tools, cloud access, identity paths, and even routine user actions. Nothing looked dramatic on the surface. That’s the point. Entry … Read More “ThreatsDay Bulletin: Codespaces RCE, AsyncRAT C2, BYOVD Abuse, AI Cloud Intrusions & 15+ Stories – The Hacker News” »
Researchers at Check Point link ‘Amarath-Dragon’ attacks to prolific Chinese cyber-espionage operation – Read More –
Infy Hackers Resume Operations with New C2 Servers After Iran Internet Blackout Ends – The Hacker News

The elusive Iranian threat group known as Infy (aka Prince of Persia) has evolved its tactics as part of efforts to hide its tracks, even as it readied new command-and-control (C2) infrastructure coinciding with the end of the widespread internet blackout the regime imposed at the start of the month. “The threat actor stopped maintaining … Read More “Infy Hackers Resume Operations with New C2 Servers After Iran Internet Blackout Ends – The Hacker News” »
Following a series of high-profile cyberattacks, boards of directors are now requiring their organizations to take greater responsibility for the risks posed by enterprise resource planning (ERP) systems pose after a series of high-profile cyberattacks. The Jaguar Land Rover (JLR), incident in Sept. 2025 illustrates the severe consequences of such attacks. The cyberattack forced JLR … Read More “Why boards should be obsessed with their most ‘boring’ systems – CyberScoop” »
Today’s “AI everywhere” reality is woven into everyday workflows across the enterprise, embedded in SaaS platforms, browsers, copilots, extensions, and a rapidly expanding universe of shadow tools that appear faster than security teams can track. Yet most organizations still rely on legacy controls that operate far away from where AI interactions actually occur. The result … Read More “The Buyer’s Guide to AI Usage Control – The Hacker News” »
Pindrop warns of 1210% increase in AI-powered fraud last year – Read More –
Cybersecurity researchers have disclosed details of an active web traffic hijacking campaign that has targeted NGINX installations and management panels like Baota (BT) in an attempt to route it through the attacker’s infrastructure. Datadog Security Labs said it observed threat actors associated with the recent React2Shell (CVE-2025-55182, CVSS score: 10.0) exploitation using malicious NGINX – … Read More “Malicious NGINX Configurations Enable Large-Scale Web Traffic Hijacking Campaign – The Hacker News” »
Cybersecurity researchers have disclosed details of an active web traffic hijacking campaign that has targeted NGINX installations and management panels like Baota (BT) in an attempt to route it through the attacker’s infrastructure. Datadog Security Labs said it observed threat actors associated with the recent React2Shell (CVE-2025-55182, CVSS score: 10.0) exploitation using malicious NGINX – … Read More “Malicious NGINX Configurations Enable Large-Scale Web Traffic Hijacking Campaign – The Hacker News” »