Day Two of Pwn2Own Automotive 2026 is underway, and the stakes are rising. Security researchers are back on the Pwn2Own stage, continuing to probe and challenge the latest automotive systems as the competition intensifies. New exploits, unexpected twists, and standout performances are already emerging – follow along here for daily updates as the race for Master … Read More “Pwn2Own Automotive 2026 – Day Two Results – Zero Day Initiative – Blog” »
Cisco has released fresh patches to address what it described as a “critical” security vulnerability impacting multiple Unified Communications (CM) products and Webex Calling Dedicated Instance that it has been actively exploited as a zero-day in the wild. The vulnerability, CVE-2026-20045 (CVSS score: 8.2), could permit an unauthenticated remote attacker to execute arbitrary commands on … Read More “Cisco Fixes Actively Exploited Zero-Day CVE-2026-20045 in Unified CM and Webex – The Hacker News” »
As enterprises continue their rapid shift toward digital-first operations, data protection has evolved from a technical safeguard into a… The post Tokenization vs Encryption: How to Choose appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
PwC’s 29th Global CEO Survey shows cyber risk rising to the top of CEO concerns as confidence in short term business growth weakens – Read More –
Smashing Security podcast #451: I hacked the government, and your headphones are next – GRAHAM CLULEY

In episode 451 of “Smashing Security,” we meet the cybercriminal who hacked the US Supreme Court, Veterans Affairs, and more – and then helpfully posted screenshots (and even someone’s blood type) on an account called “I hacked the government.” Plus we discuss how researchers uncovered a creepy flaw that lets attackers hijack wireless headphones, listen … Read More “Smashing Security podcast #451: I hacked the government, and your headphones are next – GRAHAM CLULEY” »
The National Institute for Standards and Technology is starting 2026 with a smaller staff, a shrinking budget and some big responsibilities around supporting national security and cybersecurity. At a meeting Wednesday of the Information Security Privacy Advisory Board, NIST officials provided updates on how they’re grappling with several Trump administration priorities, including mandates on AI, … Read More “NIST officials detail impact of staff cuts on encryption and other priorities – CyberScoop” »
Iranian TV Transmission Hacked With Message from Exiled Prince – Hackread – Cybersecurity News, Data Breaches, AI, and More
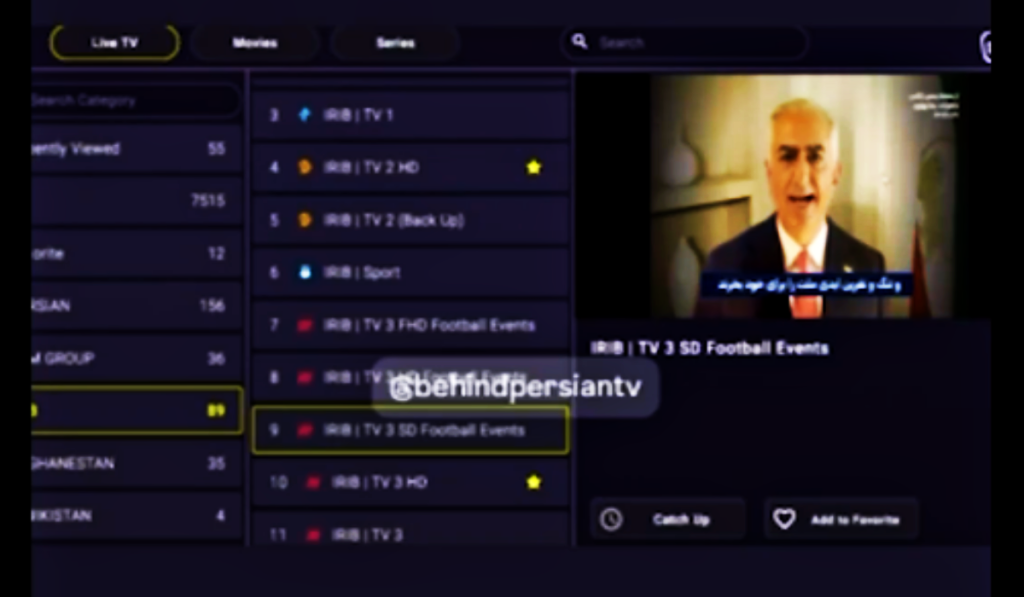
Unidentified hackers disrupted Iranian state television to broadcast messages from exiled Crown Prince Reza Pahlavi. Read about the economic crisis, the internet blackout, and the latest reports on the protest death toll. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The acting head of the Cybersecurity and Infrastructure Security Agency faced pointed questions from lawmakers Wednesday over CISA personnel decisions and staffing levels. Members of the House Homeland Security Committee asked Madhu Gottumukkala about a reported attempt to fire the agency’s chief information officer, efforts to push out a large number of staff and whether … Read More “Lawmakers probe CISA leader over staffing decisions – CyberScoop” »
A European cybersecurity organization has launched a decentralized system for identifying and numbering software security vulnerabilities, introducing a fundamental shift in how the global technology community could track and manage security flaws. The Global CVE Allocation System, or GCVE, will be maintained by The Computer Incident Response Center Luxembourg (CIRCL) as an alternative to the … Read More “GCVE launches as a decentralized system for tracking software vulnerabilities – CyberScoop” »
A European cybersecurity organization has launched a decentralized system for identifying and numbering software security vulnerabilities, introducing a fundamental shift in how the global technology community could track and manage security flaws. The Global CVE Allocation System, or GCVE, will be maintained by The Computer Incident Response Center Luxembourg (CIRCL) as an alternative to the … Read More “GCVE launches as a decentralized system for tracking software vulnerabilities – CyberScoop” »
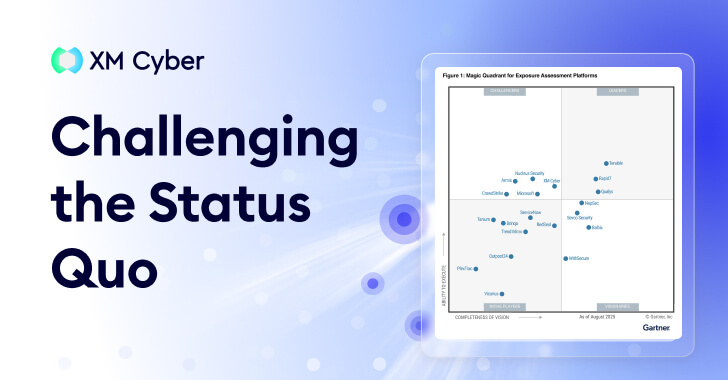
Gartner® doesn’t create new categories lightly. Generally speaking, a new acronym only emerges when the industry’s collective “to-do list” has become mathematically impossible to complete. And so it seems that the introduction of the Exposure Assessment Platforms (EAP) category is a formal admission that traditional Vulnerability Management (VM) is no longer a viable way to … Read More “Exposure Assessment Platforms Signal a Shift in Focus – The Hacker News” »
Posted by BUG on Jan 21 #### Title:OpenMetadata <= 1.11.3 Authenticated SQL Injection #### Affected versions: <= 1.11.3 #### Credits: echo #### Vendor: https://open-metadata.org/ OpenMetadata versions 1.11.3 and earlier are vulnerable to an authenticated SQL injection issue. Low-privileged users can exploit this vulnerability to gain unauthorized access to the database in the context of … Read More “OpenMetadata” »
Re: Multiple Security Misconfigurations and Customer Enumeration Exposure in Convercent Whistleblowing Platform (EQS Group) – Full Disclosure

Posted by Wade Sparks on Jan 21 Hello Yuffie, Upon further investigation, the VulnCheck CNA determined that these vulnerabilities were not suitable for CVE assignment. The vulnerabilities exist within a SaaS product and are mitigated at the CSP-level which in this case, would be the vendor, EQS Group. Rather than contribute unactionable CVE records, … Read More “Re: Multiple Security Misconfigurations and Customer Enumeration Exposure in Convercent Whistleblowing Platform (EQS Group) – Full Disclosure” »
North Korean PurpleBravo Campaign Targeted 3,136 IP Addresses via Fake Job Interviews – The Hacker News
As many as 3,136 individual IP addresses linked to likely targets of the Contagious Interview activity have been identified, with the campaign claiming 20 potential victim organizations spanning artificial intelligence (AI), cryptocurrency, financial services, IT services, marketing, and software development sectors in Europe, South Asia, the Middle East, and Central America. The new findings – … Read More “North Korean PurpleBravo Campaign Targeted 3,136 IP Addresses via Fake Job Interviews – The Hacker News” »
Zoom and GitLab have released security updates to resolve a number of security vulnerabilities that could result in denial-of-service (DoS) and remote code execution. The most severe of the lot is a critical security flaw impacting Zoom Node Multimedia Routers (MMRs) that could permit a meeting participant to conduct remote code execution attacks. The vulnerability, … Read More “Zoom and GitLab Release Security Updates Fixing RCE, DoS, and 2FA Bypass Flaws – The Hacker News” »
Law enforcement agencies from multiple European countries are still pursuing leads on people involved in the Black Basta ransomware group, nearly a year after the group’s internal chat logs were leaked, exposing key details about its operations, and at least six months since the group claimed responsibility for new attacks. Officials in Ukraine and Germany … Read More “Black Basta’s alleged ringleader identified as authorities raid homes of other members – CyberScoop” »
Cyber risks for the Milano-Cortina 2026 Winter Games include phishing and spoofed websites as key threat vectors – Read More –
A security vulnerability has been disclosed in the popular binary-parser npm library that, if successfully exploited, could result in the execution of arbitrary JavaScript. The vulnerability, tracked as CVE-2026-1245 (CVSS score: N/A), affects all versions of the module prior to version 2.3.0, which addresses the issue. Patches for the flaw were released on November 26, … Read More “CERT/CC Warns binary-parser Bug Allows Node.js Privilege-Level Code Execution – The Hacker News” »
LastPass is alerting users to a new active phishing campaign that’s impersonating the password management service, which aims to trick users into giving up their master passwords. The campaign, which began on or around January 19, 2026, involves sending phishing emails claiming upcoming maintenance and urging them to create a local backup of their password … Read More “LastPass Warns of Fake Maintenance Messages Targeting Users’ Master Passwords – The Hacker News” »
Loan phishing operation in Peru is stealing card info by impersonating financial institutions – Read More –
New Research Exposes Critical Gap: 64% of Third-Party Applications Access Sensitive Data Without Authorization – Hackread – Cybersecurity News, Data Breaches, AI, and More

Boston, MA, USA, 21st January 2026, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Sophisticated malware previously thought to be the work of a well-resourced cyber-crime group was built by one person – with the aid of AI tools – Read More –
The UK’s National Cyber Security Centre (NCSC) has issued a warning about the threat posed by distributed denial-of-service (DDoS) attacks from Russia-linked hacking groups who are reported to be continuing to target British organisations. Are you prepared? Read more in my article on the Hot for Security blog. – Read More – GRAHAM CLULEY
Carlsberg Event Wristband Leaked PII, Researcher Told Not to Disclose – Hackread – Cybersecurity News, Data Breaches, AI, and More

A poorly secured wristband system used at a Carlsberg exhibition allowed access to visitor photos, videos, and full names. Attempts to report the issue were ignored for months. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Every managed security provider is chasing the same problem in 2026 — too many alerts, too few analysts, and clients demanding “CISO-level protection” at SMB budgets. The truth? Most MSSPs are running harder, not smarter. And it’s breaking their margins. That’s where the quiet revolution is happening: AI isn’t just writing reports or surfacing risks … Read More “Webinar: How Smart MSSPs Using AI to Boost Margins with Half the Staff – The Hacker News” »
The EU’s Cybersecurity Act 2.0 will aim to address some of the challenges of the current CSA, including the slow rollout of certification schemes – Read More –
Ransomware negotiation is a dark but widely acknowledged reality in the cybersecurity industry — one that many argue is a necessary practice, even if it largely occurs out of sight. Brokering payments and terms with cybercriminals who hold organizations’ data and operations hostage places security professionals in a fraught position that requires them to balance … Read More “The thin line between saving a company and funding a crime – CyberScoop” »
Ransomware negotiation is a dark but widely acknowledged reality in the cybersecurity industry — one that many argue is a necessary practice, even if it largely occurs out of sight. Brokering payments and terms with cybercriminals who hold organizations’ data and operations hostage places security professionals in a fraught position that requires them to balance … Read More “The thin line between saving a company and funding a crime – CyberScoop” »
A new service, the Global Cybersecurity Vulnerability Enumeration (GCVE), offers an alternative to the US-led CVE – Read More –
VoidLink Linux Malware Framework Built with AI Assistance Reaches 88,000 Lines of Code – The Hacker News
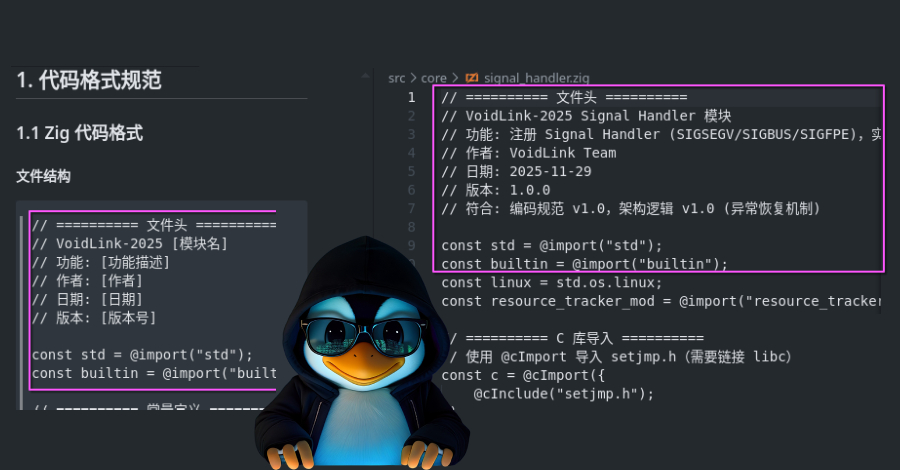
The recently discovered sophisticated Linux malware framework known as VoidLink is assessed to have been developed by a single person with assistance from an artificial intelligence (AI) model. That’s according to new findings from Check Point Research, which identified operational security blunders by malware’s author that provided clues to its developmental origins. The latest insight … Read More “VoidLink Linux Malware Framework Built with AI Assistance Reaches 88,000 Lines of Code – The Hacker News” »
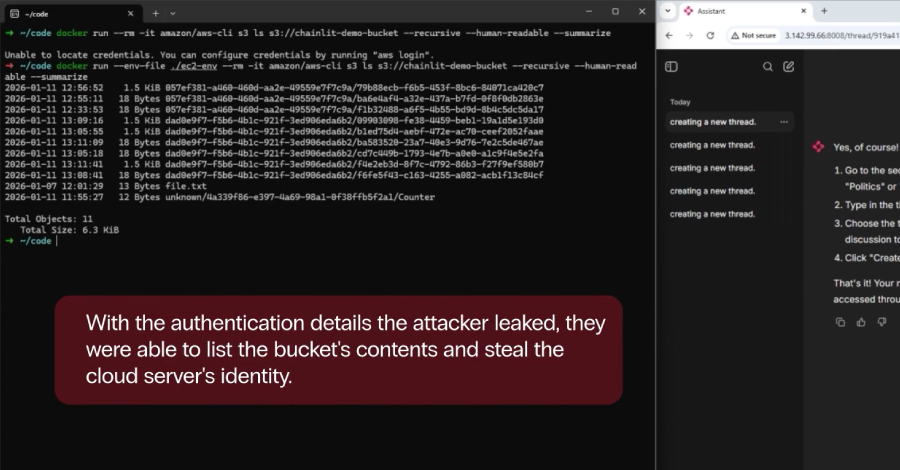
Security vulnerabilities were uncovered in the popular open-source artificial intelligence (AI) framework Chainlit that could allow attackers to steal sensitive data, which may allow for lateral movement within a susceptible organization. Zafran Security said the high-severity flaws, collectively dubbed ChainLeak, could be abused to leak cloud environment API keys and steal sensitive files, or – … Read More “Chainlit AI Framework Flaws Enable Data Theft via File Read and SSRF Bugs – The Hacker News” »
City of London Police has launched the UK’s national Report Fraud service – Read More –
Welcome to Day One of Pwn2Own Automotive 2026! Today, 30 entries are taking the Pwn2Own stage to target the latest automotive systems, as the world’s top security researchers push technology to its limits. Exploits, surprises, and breakthrough discoveries are already unfolding – follow along here for updates throughout the day as the competition continues. Stay … Read More “Pwn2Own Automotive 2026 – Day One Results – Zero Day Initiative – Blog” »
Everest Ransomware Claims McDonalds India Breach Involving Customer Data – Hackread – Cybersecurity News, Data Breaches, AI, and More

The notorious Everest ransomware group is claiming to have breached McDonald’s India, the Indian subsidiary of the American… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Airlock Digital Announces Independent TEI Study Quantifying Measurable ROI & Security Impact – Hackread – Cybersecurity News, Data Breaches, AI, and More

Atlanta, GA, United States, 20th January 2026, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Four years ago, the Department of Justice announced it would no longer seek criminal charges against independent and third-party security researchers for “good faith” security research under the Computer Fraud and Abuse Act. Now, a prominent bug bounty platform is attempting to build a framework for industry to offer similar protections to researchers who study … Read More “HackerOne rolls out industry framework to support ‘good faith’ AI research – CyberScoop” »
ClickFix to CrashFix: KongTuke Used Fake Chrome Ad Blocker to Install ModeloRAT – Hackread – Cybersecurity News, Data Breaches, AI, and More
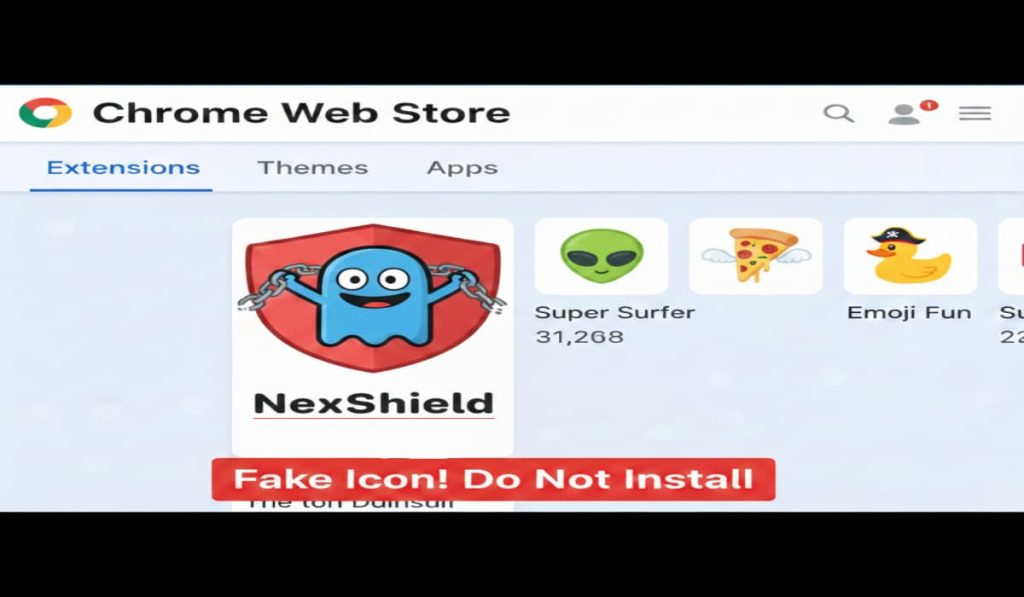
Huntress discovers ‘CrashFix,’ a new attack by KongTuke hacker group using fake ad blockers to crash browsers and trick office workers into installing ModeloRAT malware. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Congressional appropriators announced funding legislation this week that extends an expiring cyber threat information-sharing law and provides $2.6 billion for the Cybersecurity and Infrastructure Security Agency (CISA), including money for election security and directives on staffing levels. The latest so-called “minibus” package of several spending bills to keep the government funded past a Jan. 30 … Read More “Congressional appropriators move to extend information-sharing law, fund CISA – CyberScoop” »
The North Korean threat actors associated with the long-running Contagious Interview campaign have been observed using malicious Microsoft Visual Studio Code (VS Code) projects as lures to deliver a backdoor on compromised endpoints. The latest finding demonstrates continued evolution of the new tactic that was first discovered in December 2025, Jamf Threat Labs said. “This … Read More “North Korea-Linked Hackers Target Developers via Malicious VS Code Projects – The Hacker News” »
Sprocket Security Appoints Eric Sheridan as Chief Technology Officer – Hackread – Cybersecurity News, Data Breaches, AI, and More

Madison, United States, 20th January 2026, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
EU Launches GCVE to Track Vulnerabilities Without Relying on US – Hackread – Cybersecurity News, Data Breaches, AI, and More

The new EU-funded GCVE project is breaking dependence on US databases to track software flaws. Discover how this decentralised system aims to ensure global cybersecurity. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Leaked API keys are no longer unusual, nor are the breaches that follow. So why are sensitive tokens still being so easily exposed? To find out, Intruder’s research team looked at what traditional vulnerability scanners actually cover and built a new secrets detection method to address gaps in existing approaches. Applying this at scale by … Read More “Why Secrets in JavaScript Bundles are Still Being Missed – The Hacker News” »
2 security vulnerabilities in the Chainlit framework expose risks from web flaws in AI applications – Read More –
The AI Fix #84: A hungry ghost trapped in a jar gains access to the Pentagon’s network – GRAHAM CLULEY

In episode 84 of The AI Fix, Graham and Mark stare straight into the digital abyss and ask the most important question of our age: “Is AI just a hungry ghost trapped in a jar?” Also this week, we explore how a shadowy group of disgruntled insiders trying to destroy AI by poisoning its training … Read More “The AI Fix #84: A hungry ghost trapped in a jar gains access to the Pentagon’s network – GRAHAM CLULEY” »
RansomHouse Claims Data Breach at Major Apple Contractor Luxshare – Hackread – Cybersecurity News, Data Breaches, AI, and More

RansomHouse claims to have breached Apple contractor Luxshare, but no evidence has been released. Links are offline and the breach remains unverified. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Hackathon Projects Show AI Wellness Apps Can Leak Sensitive User Info – Hackread – Cybersecurity News, Data Breaches, AI, and More

As emotional computing applications proliferate, the security threats they face require frameworks beyond traditional approaches. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Hackathon Projects Show AI Wellness Apps Can Leak Sensitive User Info – Hackread – Cybersecurity News, Data Breaches, AI, and More

As emotional computing applications proliferate, the security threats they face require frameworks beyond traditional approaches. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Cybersecurity researchers have uncovered a new phishing campaign that exploits social media private messages to propagate malicious payloads, likely with the intent to deploy a remote access trojan (RAT). The activity delivers “weaponized files via Dynamic Link Library (DLL) sideloading, combined with a legitimate, open-source Python pen-testing script,” ReliaQuest said in a report shared with … Read More “Hackers Use LinkedIn Messages to Spread RAT Malware Through DLL Sideloading – The Hacker News” »
Cybersecurity researchers have uncovered a new phishing campaign that exploits social media private messages to propagate malicious payloads, likely with the intent to deploy a remote access trojan (RAT). The activity delivers “weaponized files via Dynamic Link Library (DLL) sideloading, combined with a legitimate, open-source Python pen-testing script,” ReliaQuest said in a report shared with … Read More “Hackers Use LinkedIn Messages to Spread RAT Malware Through DLL Sideloading – The Hacker News” »
A set of three security vulnerabilities has been disclosed in mcp-server-git, the official Git Model Context Protocol (MCP) server maintained by Anthropic, that could be exploited to read or delete arbitrary files and execute code under certain conditions. “These flaws can be exploited through prompt injection, meaning an attacker who can influence what an AI … Read More “Three Flaws in Anthropic MCP Git Server Enable File Access and Code Execution – The Hacker News” »