Threat actors engaging in phishing attacks are exploiting routing scenarios and misconfigured spoof protections to impersonate organizations’ domains and distribute emails that appear as if they have been sent internally. “Threat actors have leveraged this vector to deliver a wide variety of phishing messages related to various phishing-as-a-service (PhaaS) platforms such as Tycoon 2FA,” the … Read More “Microsoft Warns Misconfigured Email Routing Can Enable Internal Domain Phishing – The Hacker News” »
Threat actor “Zestix” was able to breach around 50 firms using infostealers because they lacked multi-factor authentication – Read More –
A hacking collective claims it has disconnected customers of US ISP Brightspeed – Read More –
A breach affecting Manage My Health could have exposed sensitive data for up to 120,000 New Zealand patients – Read More –
A breach affecting Manage My Health could have exposed sensitive data for up to 120,000 New Zealand patients – Read More –
Ongoing Attacks Exploiting Critical RCE Vulnerability in Legacy D-Link DSL Routers – The Hacker News

A newly discovered critical security flaw in legacy D-Link DSL gateway routers has come under active exploitation in the wild. The vulnerability, tracked as CVE-2026-0625 (CVSS score: 9.3), concerns a case of command injection in the “dnscfg.cgi” endpoint that arises as a result of improper sanitization of user-supplied DNS configuration parameters. “An unauthenticated remote attacker … Read More “Ongoing Attacks Exploiting Critical RCE Vulnerability in Legacy D-Link DSL Routers – The Hacker News” »
Millions of Android Powered TVs and Streaming Devices Infected by Kimwolf Botnet – Hackread – Cybersecurity News, Data Breaches, AI, and More

Synthient discovers over 2 million Android TV boxes and smart TVs hijacked by the Kimwolf botnet. Learn how hackers are using home devices to launch DDoS attacks and how you can protect your home network. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The Federal Communications Commission finalized new financial penalties for telecoms that submit false, inaccurate or late reporting to a federal robocalling system. The new regulations, which go into effect Feb. 5, will require providers to recertify every year that their information is accurate in the Robocall Mitigation Database (RMD). It would also impose fines on … Read More “FCC finalizes new penalties for robocall violators – CyberScoop” »
Bitfinex Hack Mastermind Behind $10 Billion Theft Gets Early Release – Hackread – Cybersecurity News, Data Breaches, AI, and More

Ilya Lichtenstein, the man behind the massive 2016 Bitfinex Bitcoin theft, has been released early from prison. Read how the First Step Act and a trail of Walmart gift cards led to this major update in one of the world’s largest crypto thefts. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and … Read More “Bitfinex Hack Mastermind Behind $10 Billion Theft Gets Early Release – Hackread – Cybersecurity News, Data Breaches, AI, and More” »
The CERT Coordination Center (CERT/CC) has disclosed details of an unpatched security flaw impacting TOTOLINK EX200 wireless range extender that could allow a remote authenticated attacker to gain full control of the device. The flaw, CVE-2025-65606 (CVSS score: N/A), has been characterized as a flaw in the firmware-upload error-handling logic, which could cause the device … Read More “Unpatched Firmware Flaw Exposes TOTOLINK EX200 to Full Remote Device Takeover – The Hacker News” »
Ledger Confirms Global-e Breach, Warns Users of Phishing Attempts – Hackread – Cybersecurity News, Data Breaches, AI, and More
Ledger confirms data breach via Global-e partner. Customer info exposed, phishing attacks active. No passwords or crypto recovery phrases leaked. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Two Chrome Extensions Caught Stealing ChatGPT and DeepSeek Chats from 900,000 Users – The Hacker News
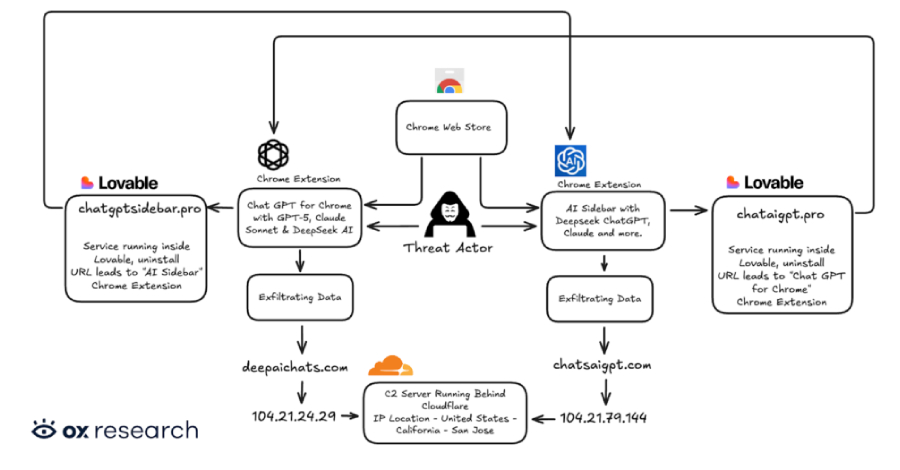
Cybersecurity researchers have discovered two new malicious extensions on the Chrome Web Store that are designed to exfiltrate OpenAI ChatGPT and DeepSeek conversations alongside browsing data to servers under the attackers’ control. The names of the extensions, which collectively have over 900,000 users, are below – Chat GPT for Chrome with GPT-5, Claude Sonnet & … Read More “Two Chrome Extensions Caught Stealing ChatGPT and DeepSeek Chats from 900,000 Users – The Hacker News” »
The CERT Coordination Center (CERT/CC) has disclosed details of an unpatched security flaw impacting TOTOLINK EX200 wireless range extender that could allow a remote authenticated attacker to gain full control of the device. The flaw, CVE-2025-65606 (CVSS score: N/A), has been characterized as a flaw in the firmware-upload error-handling logic, which could cause the device … Read More “Unpatched Firmware Flaw Exposes TOTOLINK EX200 to Full Remote Device Takeover – The Hacker News” »
A high-severity security flaw in Open WebUI Direct Connections risks account takeover and server compromises – Read More –
Multi-stage malware campaign targets hospitality organizations using social engineering and abuse of MSBuild.exe – Read More –
VS Code Forks Recommend Missing Extensions, Creating Supply Chain Risk in Open VSX – The Hacker News
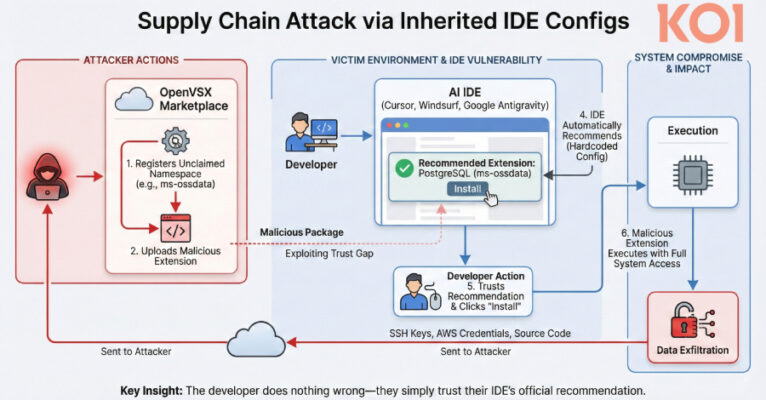
Popular artificial intelligence (AI)-powered Microsoft Visual Studio Code (VS Code) forks such as Cursor, Windsurf, Google Antigravity, and Trae have been found to recommend extensions that are non-existent in the Open VSX registry, potentially opening the door to supply chain risks when bad actors publish malicious packages under those names. The problem, according to Koi, … Read More “VS Code Forks Recommend Missing Extensions, Creating Supply Chain Risk in Open VSX – The Hacker News” »
Source: Securonix Cybersecurity researchers have disclosed details of a new campaign dubbed PHALT#BLYX that has leveraged ClickFix-style lures to display fixes for fake blue screen of death (BSoD) errors in attacks targeting the European hospitality sector. The end goal of the multi-stage campaign is to deliver a remote access trojan known as DCRat, according to … Read More “Fake Booking Emails Redirect Hotel Staff to Fake BSoD Pages Delivering DCRat – The Hacker News” »
How to Avoid Phishing Incidents in 2026: A CISO Guide – Hackread – Cybersecurity News, Data Breaches, AI, and More

Phishing in 2026 is harder to detect and verify. Learn how CISOs can speed up investigations, reduce noise, and respond with confidence. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
UK government’s new Cyber Action plan looks to provide more ‘hands-on’ support for protecting against and responding to security incidents – Read More –
The Invisible Half of the Identity Universe Identity used to live in one place – an LDAP directory, an HR system, a single IAM portal. Not anymore. Today, identity is fragmented across SaaS, on-prem, IaaS, PaaS, home-grown, and shadow applications. Each of these environments carries its own accounts, permissions, and authentication flows. Traditional IAM and … Read More “What is Identity Dark Matter? – The Hacker News” »
For too long, fraud – an illicit economy rivaling the GDP of G20 nations – has been seen as a cost of doing business, a nuisance to be absorbed by banks and consumers. That perception is a dangerous relic. Modern fraud blends geopolitics with advanced technical tactics, carried out through criminal proxies to target businesses … Read More “Why governments need to treat fraud like cyberwarfare, not customer service – CyberScoop” »
The Invisible Half of the Identity Universe Identity used to live in one place – an LDAP directory, an HR system, a single IAM portal. Not anymore. Today, identity is fragmented across SaaS, on-prem, IaaS, PaaS, home-grown, and shadow applications. Each of these environments carries its own accounts, permissions, and authentication flows. Traditional IAM and … Read More “What is Identity Dark Matter? – The Hacker News” »
JLR’s wholesale sales plunged 43% and retail drops 25% in the third quarter of 2025 following the 2025 cyber-attack – Read More –
Privacy-Enhancing Technologies: The New Foundation of Enterprise Data Protection – JISA Softech Pvt Ltd

Over the years, the concept of enterprise data protection strategies has been based on a known trio perimeter security, access controls,… The post Privacy-Enhancing Technologies: The New Foundation of Enterprise Data Protection appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
New VVS Stealer Malware Targets Discord Users via Fake System Errors – Hackread – Cybersecurity News, Data Breaches, AI, and More

Palo Alto Networks’ new report reveals VVS Stealer uses Discord Injection and fake error messages to steal tokens and MFA codes. Protect your account from this new Python-based threat. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Police in India have arrested a former Coinbase customer service agent who is believed to have been bribed by cybercriminal gangs to access sensitive customer information. Read more in my article on the Hot for Security blog. – Read More – Graham Cluley
Connex IT Partners with AccuKnox for Zero Trust CNAPP Security in Southeast Asia – Hackread – Cybersecurity News, Data Breaches, AI, and More

Menlo Park, India, 6th January 2026, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Panda3d v1.10.16 Uncontrolled Format String in Panda3D egg-mkfont Allows Stack Memory Disclosure – Full Disclosure

Posted by Ron E on Jan 05 Panda3D’s egg-mkfont utility contains an uncontrolled format string vulnerability that allows disclosure of stack-resident memory. The -gp (glyph pattern) command-line option allows users to specify a formatting pattern intended for generating glyph texture filenames. This pattern is passed directly as the format string to sprintf() without validation … Read More “Panda3d v1.10.16 Uncontrolled Format String in Panda3D egg-mkfont Allows Stack Memory Disclosure – Full Disclosure” »
Critical AdonisJS Bodyparser Flaw (CVSS 9.2) Enables Arbitrary File Write on Servers – The Hacker News

Users of the “@adonisjs/bodyparser” npm package are being advised to update to the latest version following the disclosure of a critical security vulnerability that, if successfully exploited, could allow a remote attacker to write arbitrary files on the server. Tracked as CVE-2026-21440 (CVSS score: 9.2), the flaw has been described as a path traversal issue … Read More “Critical AdonisJS Bodyparser Flaw (CVSS 9.2) Enables Arbitrary File Write on Servers – The Hacker News” »
Security Vulnerability in Koller Secret: Real Hidden App (com.koller.secret.hidemyphoto) – Full Disclosure

Posted by duykham on Jan 05 Hello Full Disclosure, I would like to disclose a security vulnerability identified in a smartphone application: *Koller Secret: Real Hidden App*. This report is shared in the interest of responsible disclosure and improving overall security awareness. — *Summary* – Application: Koller Secret: Real Hidden App – Package / … Read More “Security Vulnerability in Koller Secret: Real Hidden App (com.koller.secret.hidemyphoto) – Full Disclosure” »
Posted by malvuln on Jan 05 SigInt-Hombre, generates derived Suricata detection rules from live URLhaus threat indicators at runtime and deploy them to the Security Onion platform for high-coverage real-time network monitoring. https://github.com/malvuln/sigint-hombre What it does: Pulls the public URLhaus feed in real time (not mirrored or redistributed) Skips: Comments, empty lines, malformed URLs, … Read More “SigInt-Hombre v1 / dynamic Suricata detection rules from real-time threat feeds – Full Disclosure” »
zlib v1.3.1.2 Global Buffer Overflow in TGZfname() of zlib untgz Utility via Unbounded strcpy() on User-Supplied Archive Name – Full Disclosure

Posted by Ron E on Jan 05 A global buffer overflow vulnerability exists in the TGZfname() function of the zlib untgz utility due to the use of an unbounded strcpy() call on attacker-controlled input. The utility copies a user-supplied archive name (argv[arg]) into a fixed-size static global buffer of 1024 bytes without performing any … Read More “zlib v1.3.1.2 Global Buffer Overflow in TGZfname() of zlib untgz Utility via Unbounded strcpy() on User-Supplied Archive Name – Full Disclosure” »
Posted by Ron E on Jan 05 A heap buffer underflow vulnerability exists in the readline() function of OpenLDAP’s Lightning Memory-Mapped Database (LMDB) mdb_load utility. The vulnerability is triggered through malformed input data and results in an out-of-bounds read one byte before an allocated heap buffer. This can lead to information disclosure through heap … Read More “MongoDB v8.3.0 Heap Buffer Underflow in OpenLDAP LMDB mdb_load – Full Disclosure” »
Bioformats v8.3.0 Improper Restriction of XML External Entity Reference in Bio-Formats Leica Microsystems XML Parser – Full Disclosure

Posted by Ron E on Jan 05 Bio-Formats contains an XML External Entity (XXE) vulnerability in the Leica Microsystems metadata parsing component. The vulnerability is caused by the use of an insecurely configured DocumentBuilderFactory when processing Leica XML-based metadata files (e.g., XLEF). When a crafted XML file is supplied, the parser allows external entity … Read More “Bioformats v8.3.0 Improper Restriction of XML External Entity Reference in Bio-Formats Leica Microsystems XML Parser – Full Disclosure” »
Posted by Ron E on Jan 05 Bio-Formats performs unsafe Java deserialization of attacker-controlled memoization cache files (.bfmemo) during image processing. The loci.formats.Memoizer class automatically loads and deserializes memo files associated with images without validation, integrity checks, or trust enforcement. An attacker can exploit this behavior by supplying a crafted or corrupted .bfmemo file—either … Read More “Bioformats v8.3.0 Untrusted Deserialization of Bio-Formats Memoizer Cache Files – Full Disclosure” »
Posted by Ron E on Jan 05 This integer underflow vulnerability enables heap metadata corruption and information disclosure through carefully crafted LMDB dump files. *Impact:* – *Denial of Service*: Immediate crash (confirmed) – *Information Disclosure*: Heap metadata leak via OOB read Root Cause:The readline() function fails to validate that the input line length is … Read More “MongoDB v8.3.0 Integer Underflow in LMDB mdb_load – Full Disclosure” »
Panda3d v1.10.16 deploy-stub Unbounded Stack Allocation Leading to Uninitialized Memory – Full Disclosure

Posted by Ron E on Jan 05 A memory safety vulnerability exists in the Panda3D deploy-stub executable due to unbounded stack allocation using attacker-controlled input. The issue allows a local attacker to trigger stack exhaustion and subsequent use of uninitialized memory during Python interpreter initialization, resulting in a reliable crash and undefined behavior. The … Read More “Panda3d v1.10.16 deploy-stub Unbounded Stack Allocation Leading to Uninitialized Memory – Full Disclosure” »
Posted by Ron E on Jan 05 A stack-based buffer overflow vulnerability exists in the Panda3D egg-mkfont utility due to the use of an unbounded sprintf() call with attacker-controlled input. By supplying an excessively long glyph pattern string via the -gp command-line option, an attacker can trigger a stack buffer overflow, resulting in a … Read More “Panda3d v1.10.16 egg-mkfont Stack Buffer Overflow – Full Disclosure” »
Multiple Security Misconfigurations and Customer Enumeration Exposure in Convercent Whistleblowing Platform (EQS Group) – Full Disclosure

Posted by Yuffie Kisaragi via Fulldisclosure on Jan 05 UPDATE: Following the publication of these vulnerabilities and the subsequent CVE assignments, the CVE identifiers have now been revoked. The vendor (EQS Group) contacted the CVE Program (via a CNA) and disputed the records, stating that the affected product is an exclusively hosted SaaS platform with … Read More “Multiple Security Misconfigurations and Customer Enumeration Exposure in Convercent Whistleblowing Platform (EQS Group) – Full Disclosure” »
A new critical security vulnerability has been disclosed in n8n, an open-source workflow automation platform, that could enable an authenticated attacker to execute arbitrary system commands on the underlying host. The vulnerability, tracked as CVE-2025-68668, is rated 9.9 on the CVSS scoring system. It has been described as a case of a protection mechanism failure. … Read More “New n8n Vulnerability (9.9 CVSS) Lets Authenticated Users Execute System Commands – The Hacker News” »
The surprise raid by U.S. armed forces and law enforcement agencies in Caracas, Venezuela had observers around the world scouring social media and news for updates on an operation that saw Venezuelan president Nicholas Maduro and his wife captured and flown to the United States to face criminal charges. The Trump administration initially offered few … Read More “AI, voting machine conspiracies fill information vacuum around Venezuela operation – CyberScoop” »
Researchers Warn of Data Exposure Risks in Claude Chrome Extension – Hackread – Cybersecurity News, Data Breaches, AI, and More
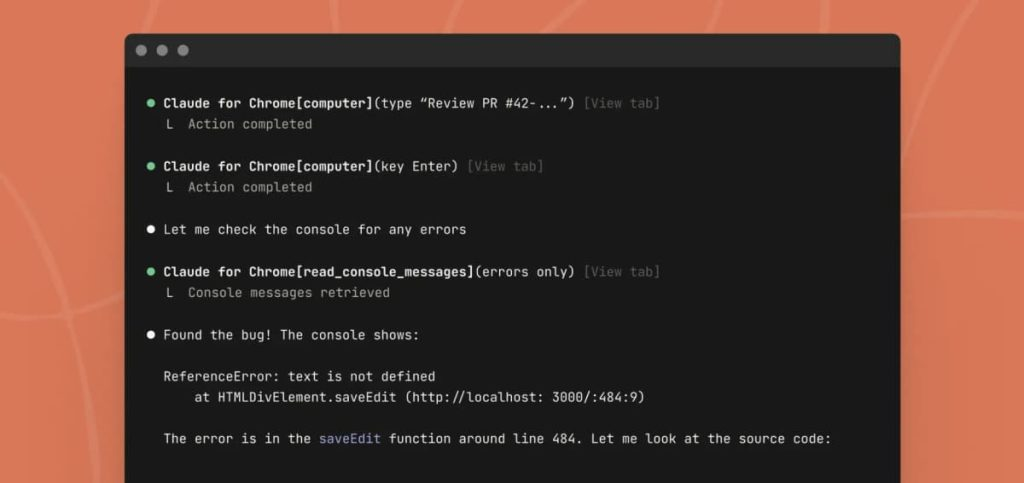
Security experts at Zenity Labs warn that Anthropic’s new agentic browser extension, Claude in Chrome, could bypass traditional web security, exposing private data and login tokens to potential hijackers. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A hacker who pleaded guilty to conspiring to launder billions of dollars worth of bitcoin stolen in the 2016 Bitfinex hack has been released from prison, a little more than one year after being sentenced to a five-year stint. Ilya Lichtenstein posted on X that his early release came as a result of a bipartisan … Read More “Convicted Bitfinex bitcoin launderer freed from prison, thanks Trump law – CyberScoop” »
Kimwolf Android Botnet Infects Over 2 Million Devices via Exposed ADB and Proxy Networks – The Hacker News

The botnet known as Kimwolf has infected more than 2 million Android devices by tunneling through residential proxy networks, according to findings from Synthient. “Key actors involved in the Kimwolf botnet are observed monetizing the botnet through app installs, selling residential proxy bandwidth, and selling its DDoS functionality,” the company said in an analysis published … Read More “Kimwolf Android Botnet Infects Over 2 Million Devices via Exposed ADB and Proxy Networks – The Hacker News” »
The Russia-aligned threat actor known as UAC-0184 has been observed targeting Ukrainian military and government entities by leveraging the Viber messaging platform to deliver malicious ZIP archives. “This organization has continued to conduct high-intensity intelligence gathering activities against Ukrainian military and government departments in 2025,” the 360 Threat Intelligence Center said in – Read More … Read More “Russia-Aligned Hackers Abuse Viber to Target Ukrainian Military and Government – The Hacker News” »
NordVPN Denies Breach After Hacker Claims Access to Salesforce Dev Data – Hackread – Cybersecurity News, Data Breaches, AI, and More

A hacker using the alias 1011 has claimed to breach a NordVPN development server, posting what appears to… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Ilya Lichtenstein, convicted for the 2016 Bitfinex hack, has been released early from prison to home confinement – Read More –
A new Python-based malware called VVS stealer has been identified, targeting Discord users with stealthy techniques to steal data – Read More –
The year opened without a reset. The same pressure carried over, and in some places it tightened. Systems people assume are boring or stable are showing up in the wrong places. Attacks moved quietly, reused familiar paths, and kept working longer than anyone wants to admit. This week’s stories share one pattern. Nothing flashy. No … Read More “⚡ Weekly Recap: IoT Exploits, Wallet Breaches, Rogue Extensions, AI Abuse & More – The Hacker News” »
Modern enterprises depend on AI data pipelines for analytics and automated decision-making. As these pipelines become more integrated… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More