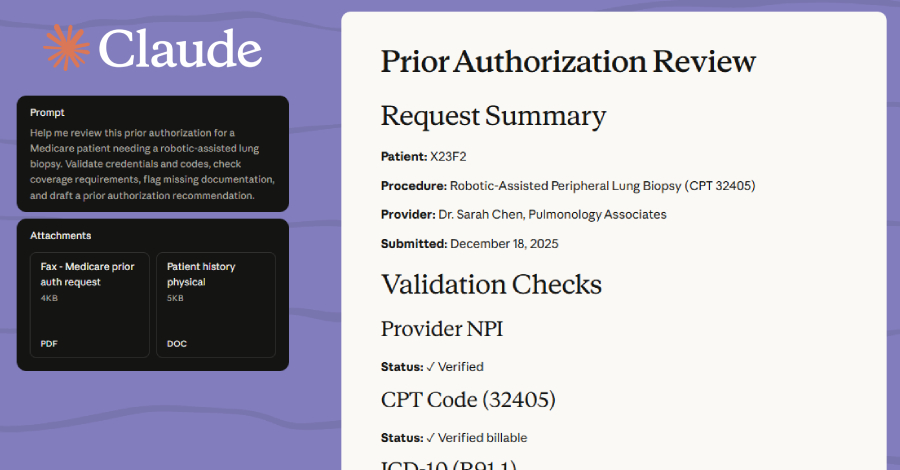
Fake Employee Reports Spread Guloader and Remcos RAT Malware – Hackread – Cybersecurity News, Data Breaches, AI, and More

Scammers are using fake October 2025 performance reviews to trick staff into installing Guloader and Remcos RAT malware. Learn how to identify this threat and protect your personal data from remote hackers. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More