GitGuardian Closes 2025 with Strong Enterprise Momentum, Protecting Millions of Developers Worldwide – Hackread – Cybersecurity News, Data Breaches, AI, and More

New York, NY, 14th January 2026, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More


























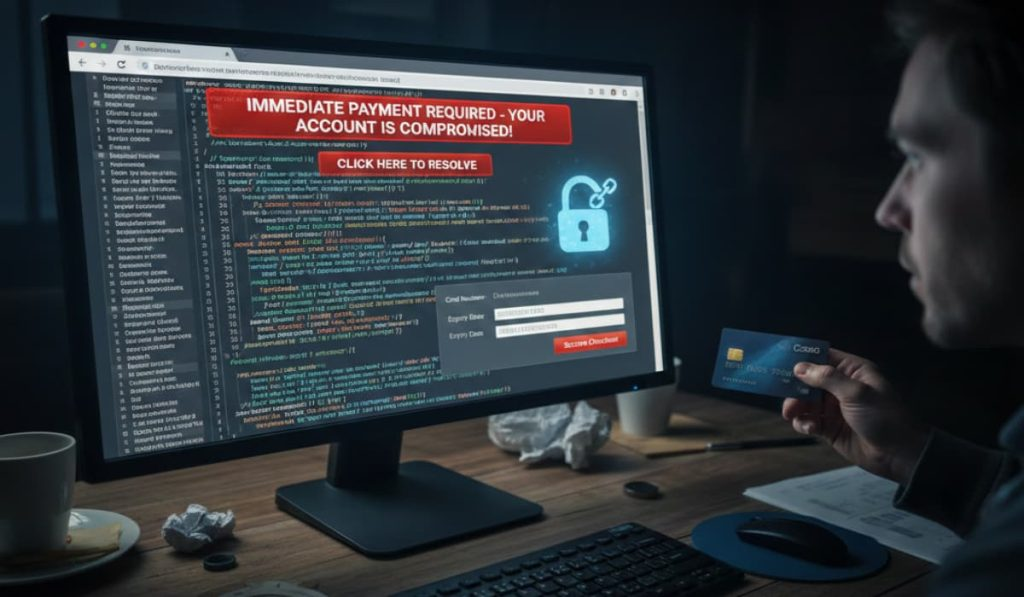


![[Webinar] Securing Agentic AI: From MCPs and Tool Access to Shadow API Key Sprawl [Webinar] Securing Agentic AI: From MCPs and Tool Access to Shadow API Key Sprawl – The Hacker News](https://attackfeed.com/wp-content/uploads/2026/01/ai-agent-C3Hsu0.webp)