Evelyn Stealer Malware Abuses VS Code Extensions to Steal Developer Credentials and Crypto – The Hacker News

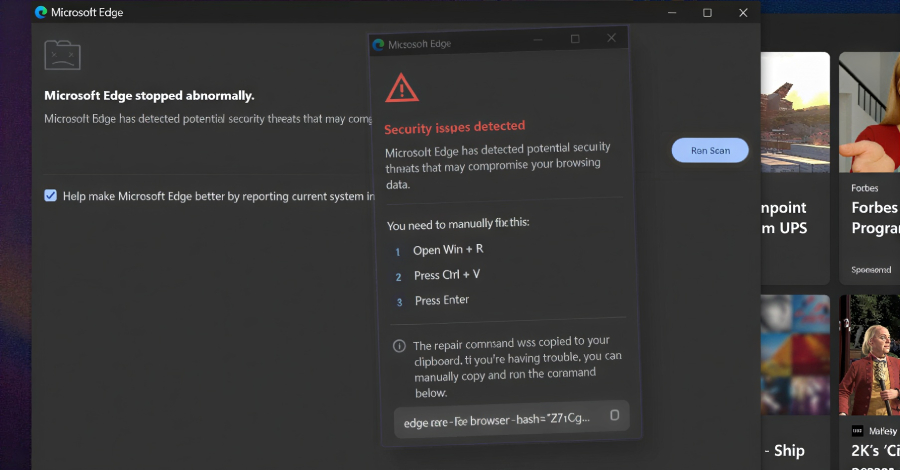
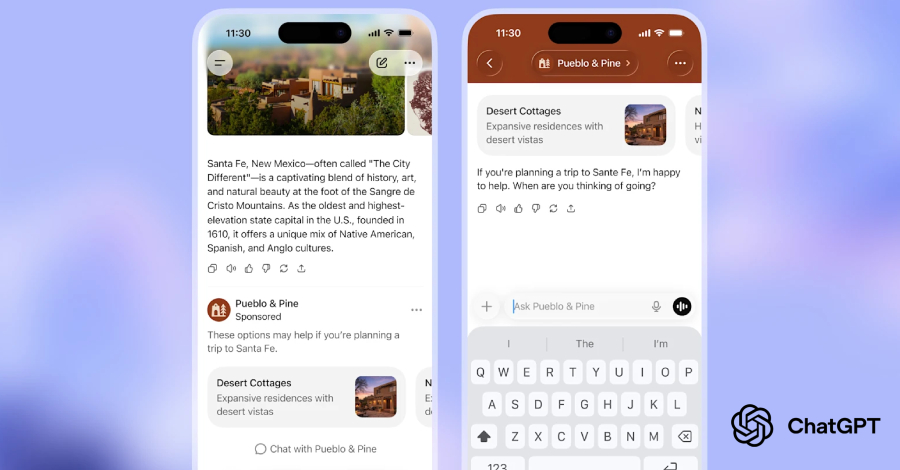
Cybersecurity researchers have disclosed details of a malware campaign that’s targeting software developers with a new information stealer called Evelyn Stealer by weaponizing the Microsoft Visual Studio Code (VS Code) extension ecosystem. “The malware is designed to exfiltrate sensitive information, including developer credentials and cryptocurrency-related data. Compromised developer – Read More – The Hacker News