Multinational police effort hits sections of Lockbit ransomware operation – AJ Vicens
– [[{“value”:”
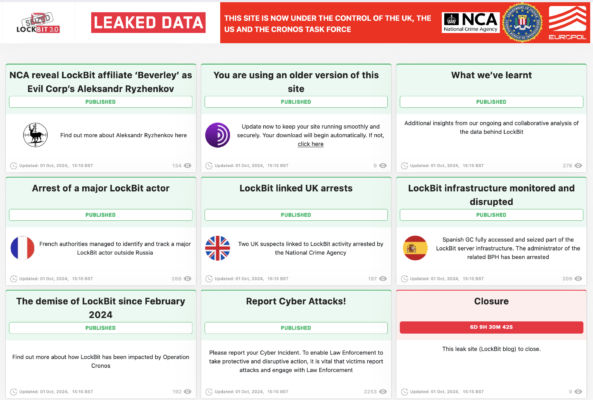
An international consortium of law enforcement agencies on Tuesday announced additional arrests, seizures and sanctions targeting LockBit ransomware infrastructure, the latest actions taken to hobble what was once among the most prolific ransomware operations going.
The actions include four arrests, seized servers and sanctions targeting an affiliate working with LockBit who authorities say has links to Evil Corp., an erstwhile Russian-based cybercrime syndicate sanctioned by the U.S. government in 2019 for its role in distributing malware and enabling a range of cybercriminal activity.
The U.S. Department of Justice also in 2019 indicted two people associated with Evil Corp., Maksim Yakubets and Igor Turashev.
Authorities on Tuesday said they arrested a suspected LockBit developer in France, two people in the U.K. who were allegedly supporting the activity of a LockBit affiliate, and the administrator of a bulletproof hosting service in Spain that worked with the LockBit group.
The U.K. sanctioned 16 people Tuesday accused of being members of Evil Corp., and released detailed information on the history of the group and its connections to past and present cybercriminal activity. Among the sanctioned is Aleksandr Ryzhenkov, who the U.K.’s National Crime Agency identified as a LockBit affiliate and as “Yakubets’ right-hand man.”
The DOJ unsealed an indictment against Ryzhenkov on Tuesday, alleging that he participated in ransomware attacks across the U.S. dating back to 2017, according to a statement. Additionally, the U.S. Treasury Department sanctioned Ryzhenkov, along with six other people and two entities associated with Evil Corp.
Australia was also set to announce its own sanctions related to the operation, according to a statement from Europol, which assisted the 12-country operation.
Tuesday’s actions are the latest salvo against LockBit taken under “Operation Cronos,” the name of the organized international effort led by the NCA unveiled in February 2024. British authorities seized the website used by LockBit to post targets and share data from targeted entities that refused to pay ransom and used it as the platform to disseminate news about the operation and information about the nearly 200 affiliates working with LockBit at the time, part of both a traditional law enforcement disruption as well as a psychological operation designed to undermine LockBit’s support in the cybercrime community.
The FBI did not provide an immediate response to requests for comment Tuesday morning.
Authorities also identified Dmitry Yuryevich Khoroshev as the driving force behind LockBit and said the Russian national controlled the “LockBitSupp” persona, which communicated with journalists and researchers about LockBit’s operations. The DOJ indicted Khoroshev at the time, accusing him of running the operation that targeted more than 2,000 victims and extorting more than $100 million in ransom payments since it began operation in September 2019.
LockBitSupp told CyberScoop at the time that authorities had identified the wrong person and vowed to continue working. LockBit did transition to new infrastructure and appeared to be targeting new victims in the wake of the February disruption.
The authorities who seized LockBit’s site eventually made it inaccessible, but the site came back online Monday promising new information about arrests and further disruptions.
The post Multinational police effort hits sections of Lockbit ransomware operation appeared first on CyberScoop.
“}]] – Read More – CyberScoop

