Fancy Bear spotted using real Kazak government documents in spearpishing campaign – CyberScoop
A hacking group linked to Russian intelligence has been observed leveraging seemingly legitimate documents from the Kazakhstan government as phishing lures to infect and spy on government officials in Central Asia, according to researchers at Sekoia.
The files, laced with malware, include draft versions of diplomatic statements, correspondence letters, internal administrative notes and other documents attributed to the Kazakhstan government between 2021 and 2024. In many cases they appear to match real documents or statements put out by Kazakhstan’s Ministry of Foreign Affairs.
The activity is linked to an intrusion set previously identified by the Ukrainian government in 2023, and one that has been attributed by Ukraine’s CERT and by private threat intelligence firm Recorded Future to APT 28. That group, also known as Fancy Bear, is known to use cyber operations to spy on governments on behalf of the Russian government and is believed to be linked to Moscow’s Main Intelligence Directorate (GRU).
According to previous research from Recorded Future, the same campaign has ensnared dozens of victims across Central Asia, East Asia and Europe since July 2024, and includes the use of two pieces of malware — dubbed HATVIBE and CHERRYSPY — that were previously attributed to Russian cyber espionage campaigns. Ukrainian officials have linked the malware to a 2023 compromise of the official email account for the Tajikistan Embassy in Ukraine that was used in follow up attacks targeting entities in Kazakhstan, Kyrgyzstan, Mongolia, Israel, and India.
“Although the infection chain was already partially documented, the ten documents identified by Sekoia exhibit a previously unknown malicious code, while retaining a similar execution structure,” Sekoia researchers Amaury G., Maxime Arandel, Erwan Chevalier and Felix Aimé wrote.
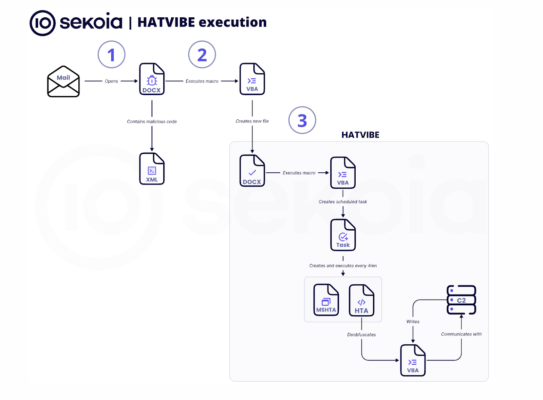
When opened, the documents execute a chain of malicious macro files in Word that downgrades the victim device’s security settings, saves variables for the HATVIBE on their hard drive and launches a clandestine program designed to run the malware every four minutes.
Because the chain uses one Word document to open another, the researchers have named the ongoing campaign “Double-Tap.”
According to Sekoia, the technical details around HATVIBE and its known victim set overlap with ZEBROCY, another backdoor that was used in a similar espionage-minded campaign against Central Asian governments, defense agencies and diplomatic entities. ZEBROCY was also attributed to Fancy Bear by Russian cybersecurity firm Kaspersky. Sekoia researchers assessed with medium confidence that the activity they were tracking was also tied to the Russian GRU and Fancy Bear.
HATVIBE operates as loading malware, calling out to various command and control servers to fetch and execute CHERRYSPY, another piece of malware meant to provide persistent, clandestine backdoor access to the victim’s device.
It’s not clear how APT 28 initially obtained the Kazak government files used in the spearphishing attacks. Sekoia researchers suggest that Kazakhstan and its neighboring Central Asian governments were likely primary targets of the campaign, noting that Kazakhstan’s government has drifted away from Russia’s orbit of influence in recent years on issues like the war in Ukraine.
“Those documents may have been exfiltrated through a cyber operation conducted earlier by the same intrusion set, within the same campaign. Yet, we do not have technical evidence to confirm this possibility,” Sekoia researchers wrote. “The documents may have also been obtained by another intrusion set through cyber operation, open source collection or by a physical operation (stolen laptop by intelligence agents), and then handed to the operators of this campaign to be weaponized.”
Other recent developments, like Kazakhstan’s emerging role as a key trade partner between China and Europe, and the international competition to build its first nuclear power plant, make it a prime target for cyber espionage. .
“Ultimately, Russia’s objectives are to ensure Kazakhstan remains politically aligned, to counter the influence of competing powers, and to secure its own economic and strategic foothold in the region,” the researchers wrote.
For more information on this campaign, including indicators of compromise and detection rules, read the blog on Sekoia’s website.
The post Fancy Bear spotted using real Kazak government documents in spearpishing campaign appeared first on CyberScoop.
–
Read More – CyberScoop
