Fancy Bear, the hacking group linked to Russia’s Main Intelligence Directorate (GRU), has been targeting the email accounts of high-ranking Ukrainian officials as well as executives at defense contractors located in other countries who sell weapons and equipment to Kyiv, according to new research from ESET.
The campaign, ongoing since at least 2023, has taken advantage of spearphishing and cross-site scripting vulnerabilities in different webmail software products, including Roundcube, Horde, MDaemon and Zimbra.
Just one of those vulnerabilities was a zero-day that ESET researchers suspect was first identified by Fancy Bear, also known as APT28 or “Sednit” in ESET’s tracking terminology. The group was observed leveraging CVE-2024-11182 in November 2024 emails sent to two Ukrainian state-owned defense companies and a Ukrainian civilian air transport company.
Matthieu Faou, senior malware researcher at ESET, provided CyberScoop with further detail on that rationale.
“What we know is that, according to our telemetry, Sednit is the only threat actor using this specific exploit,” Faou said in an email. “This means that they either developed this capability in house, or that they bought it from a third-party vendor/exploit broker.”
The remaining webmail programs were compromised using known vulnerabilities that already had patches available. There is evidence that the Russian hacking group has been heavily focused on webmail software since 2023, steadily identifying and adding more vulnerabilities that can target and break into a wide variety of programs.
According to the report, the victims in 2024 alone included officials from regional national governments in Ukraine, Greece, Cameroon and Serbia, military officials in Ukraine and Ecuador, and employees of defense contracting firms in Ukraine, Romania and Bulgaria.
Fancy Bear is perhaps best known in the United States for its hack and leak of Democratic National Committee emails in the lead-up to the 2016 presidential election. Since the start of the Russia-Ukraine war, the unit has increasingly turned its focus to collecting political and wartime intelligence from the conflict.
This espionage campaign appears to be focused on gaining insight into the Ukrainian military’s supply chain, though the report also notes it found evidence of victims in Latin America, the European Union and Africa.
Faou said he believes the evidence points to extracting information about Ukraine’s defense base as the campaign’s primary motivation, and that the victims in other countries reflect how the GRU “is also tasked in collecting intelligence from a broad range of targets, including governments and military entities worldwide.”
Last month, the French Ministry for Europe and Foreign Affairs accused the group of attempted or successful hacks against a dozen French entities since 2021 and trying to “destabilize” French elections in 2017 through covert and cyber means.
The ministry’s statement also accused the Russian government of using APT28 “to exert continual pressure on Ukrainian infrastructures amid Russia’s war of aggression against Ukraine,” adding that “many European partners have also been targeted by APT28 in recent years.” This week, French intelligence agencies released a 16-page assessment detailing the hacking group’s targeting of French governments and organizations dating back to 2015.
Faou said ESET identified at least 17 separate victim organizations in the webmail campaign. When asked how many were compromised, he said ESET’s endpoint was able to block the email, the malicious script or the network connection during data exfiltration for “most” of those organizations.
“Most of the targets are related to the current war in Ukraine; they are either Ukrainian governmental entities or defense companies in Bulgaria and Romania. Notably, some of these defense companies are producing Soviet-era weapons to be sent to Ukraine,” the report stated.
The group’s spearphishing lures used fake headlines from prominent Ukrainian news outlets like the Kyiv Post about the Russia-Ukraine war, seemingly playing on their targets’ personal or business interests in the conflict. Some headlines, written in Ukrainian, were “SBU arrested a banker who worked for enemy military intelligence in Kharkiv” and “Putin seeks Trump’s acceptance of Russian conditions in bilateral relations.”
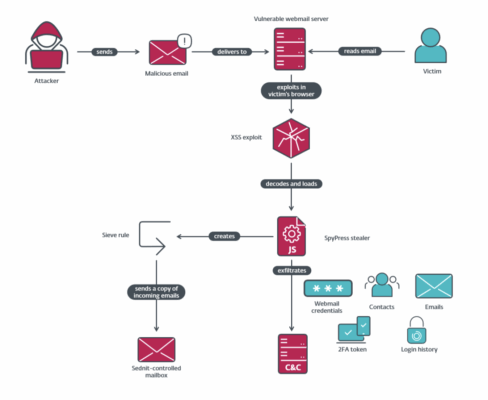
Those who opened the emails using the affected webmail clients were then served up — via cross-site scripting — a custom JavaScript malware payload capable of exfiltrating data from the account’s email messages, address book, contacts and log-in history.
At least one of the vulnerabilities, affecting MDaemon software, could steal passwords and secrets for the account’s two-factor authentication, meaning attackers could bypass the security protection and access the victim’s mailbox using another application.
The malware uses flaws in webmail software programs to steal an account’s credentials, either by tricking the browser or password manager into pasting those credentials into a hidden form or getting the user to log out, whereupon they can be served fake phishing landing pages to log back in.
While the JavaScript code lacks the kind of sophisticated persistence mechanisms that are routinely deployed by state-backed hackers to maintain their access, ESET researchers note that the malware is reloaded every time the victim opens the malicious email.
Faou described the GRU-linked hacking operation as ongoing, with the last detected email flagged April 17.
“While we do have a good understanding of the TTPs used in this operation, we continue to closely track it to be able to detect the exploitation of new [zero days] in webmail applications as fast as possible,” he wrote.
The post Fancy Bear campaign sought emails of high-level Ukrainians and their military suppliers appeared first on CyberScoop.
–
Read More – CyberScoop