Multi-stage attack begins with fake message relating to business requests and evades detection with link hidden in a PDF – Read More –
Category: Privacy/Governance Feed
Wiz Security claims Moltbook misconfiguration allowed full read and write access – Read More –
The Digital Personal Data Protection (DPDP) Act of India is one of the most significant regulatory changes in the… The post 90-Day DPDP Readiness Plan for Indian Enterprises appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
NSA released new guidelines to help organizations achieve target-level Zero Trust maturity – Read More –
A supply chain attack on Notepad++ update process was linked to compromised hosting infrastructure – Read More –
Russia-linked hacking group Fancy Bear is exploiting a brand-new vulnerability in Microsoft Office, CERT-UA says – Read More –
Bitdefender has discovered a new Android malware campaign that uses Hugging Face – Read More –
Linwei Ding, a former Google engineer, has been found guilty of stealing trade secrets for China – Read More –
Ransomware victims surged in Q4 2025 despite fewer active extortion groups, with data leaks rising 50%, ReliaQuest researchers report – Read More –
Ransomware victims surged in Q4 2025 despite fewer active extortion groups, with data leaks rising 50%, ReliaQuest researchers report – Read More –
CrowdStrike assessed that two new threat actor groups have spun off from North Korean Labyrinth Chollima hackers – Read More –
Non-profit ITRC says the number of data breaches increased 5% annually to reach a record total in 2025 – Read More –
The RedKitten campaign distributes lures designed to target people seeking information about missing persons or political dissidents in Iran – Read More –
Cyber fraudsters targeting corporate finance departments costs businesses millions a year – Read More –
The Middle East and Africa (MEA) region is experiencing a rapid industrial change. The use of Operational Technology (OT)… The post OT & IoT Security in MEA: Why Industrial Cyber Risks Are Surging appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
The French data protection regulator said that France Travail’s response to a 2024 data breach violated GDPR – Read More –
The FBI outlines ten actions which organizations can take to defend networks against cybercriminal and nation-state threats – Read More –
Google has taken coordinated action against the massive IPIDEA residential proxy network, enhancing customer protections and disrupting cybercrime operations – Read More –
CISA urges action against insider threats with publication of a new infographic offering strategies to manage risks – Read More –
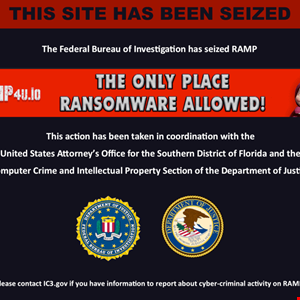
The dark web forum administrator confirmed the takedown and said they had “no plans to rebuild” – Read More –
Despite the seemingly widespread adoption of AI for security operations, security leaders primarily use it for “relatively basic use cases,” said a Sumo Logic study – Read More –
Cybersecurity is now the fifth fastest-growing occupation in the UK, says Socura – Read More –
In a period characterized by the acceleration of digital faster, more regulatory bodies and constant cyber threats, data protection… The post Designing an End-to-End Data Protection Architecture appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
A recent update has fixed 12 vulnerabilities in OpenSSL, some existing in the codebase for years – Read More –
Two critical security flaws in n8n have exposed sandboxing vulnerabilities, enabling remote code execution for attackers – Read More –
Researchers discover that PureRAT’s code now contains emojis – indicating it has been written by AI based-on comments ripped from social media. – Read More –
Zscaler analysts found critical vulnerabilities in 100% of enterprise AI systems, with 90% compromised in under 90 minutes – Read More –
Chainalysis claims Chinese money launderers now account for 20% of global activity – Read More –
Sonatype warns that open source threats became industrialized with a surge in malicious packages in 2025 – Read More –
Critical sandbox escape vulnerability in Grist-Core enables remote code execution via a malicious formula – Read More –
PeckBirdy command-and-control framework targeting gambling, government sectors in Asia since 2023 has been linked to China-aligned APTs – Read More –
Bugcrowd study reveals 82% of security researchers now use AI, a big increase from 2023 figures – Read More –
Microsoft urged customers running Microsoft Office 2016 and 2019 to apply the patch to be protected – Read More –
Nike is investigating after the World Leaks ransomware group posted a 1.4TB data dump – Read More –
With increasing volume of data and regulatory controls that are only tightening, regulated industries have a hard paradox to… The post How Regulated Industries Use Privacy-Enhancing Technologies (PETs) appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Supply chain breach in eScan antivirus distributes multi-stage malware via legitimate updates – Read More –
CISA released initial list of PQC-capable hardware and software to guide companies amid quantum threats – Read More –
Fortra researchers have discovered a new SEO poisoning operation known as “HaxorSEO” – Read More –
The US law firm Hagens Berman will lead a class action lawsuit against Coupang over security failures that led to a June 2025 data breach – Read More –
Threat actors posing as IT support teams use phishing kits to generate fake login sites in real-time to trick victims into handing over credentials – Read More –
A destructive cyber attack targeting Poland’s energy sector has been linked to Russian APT group Sandworm – Read More –
Open letter by NHS technology leaders outlines plans to identify risks to software supply chain security across health and social are system – Read More –
Under Armour said there is no evidence at this point to suggest the incident affected systems used to process payments or store customer passwords – Read More –
Critical vulnerability in Appsmith allows account takeover via flawed password reset process – Read More –
Security flaw in RealHomes CRM plugin allowed file uploads; patches released for 30,000+ sites – Read More –
Phoney email alerts suggest users need to backup their LastPass accounts within 24 hours. LastPass says it would never require this action from users – Read More –
VulnCheck analysts found that vulnerabilities exploited before being publicly disclosed rose from 23.6% in 2024 to 28.96% in 2025 – Read More –
UK Executives Warn They May Not Survive a Major Cyber-Attack, Vodafone Survey Finds – Read More –
DLA Piper finds 22% increase in breached firms notifying European GDPR regulators – Read More –
As enterprises continue their rapid shift toward digital-first operations, data protection has evolved from a technical safeguard into a… The post Tokenization vs Encryption: How to Choose appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd