Multiple vulnerabilities have been discovered in Microsoft products, the most severe of which could allow for remote code execution. Successful exploitation of the most severe of these vulnerabilities could result in an attacker gaining the same privileges as the logged-on user. Depending on the privileges associated with the user, an attacker could then install programs; … Read More “Critical Patches Issued for Microsoft Products, November 11, 2025 – Cyber Security Advisories – MS-ISAC” »
Category: Gov/ISAC Feeds
Multiple vulnerabilities have been discovered in Mozilla products, the most severe of which could allow for arbitrary code execution. Mozilla Firefox is a web browser used to access the Internet. Mozilla Firefox ESR is a version of the web browser intended to be deployed in large organizations. Successful exploitation of the most severe of these … Read More “Multiple Vulnerabilities in Mozilla Products Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
Post Content – Read More – IC3.gov News
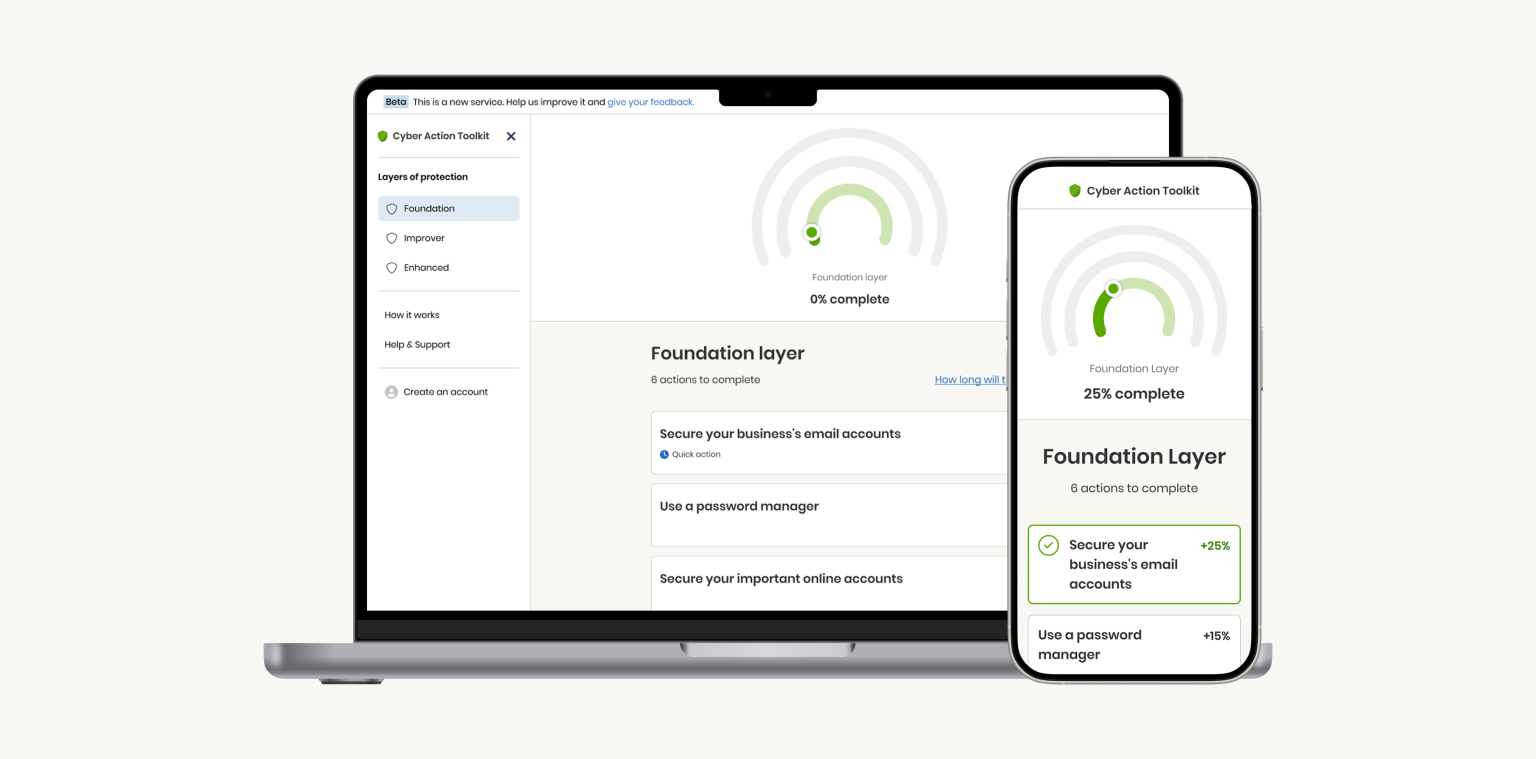
How the NCSC’s ‘Cyber Action Toolkit’ is helping small businesses to improve their cyber security. – Read More – NCSC Feed
Multiple vulnerabilities have been discovered in Apple products, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user, an attacker could then install … Read More “Multiple Vulnerabilities in Apple Products Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
Multiple vulnerabilities have been discovered in Cisco products, the most severe of which could allow for remote code execution. Cisco is a leading technology company best known for its networking hardware and software, such as routers and switches, that form the backbone of the internet and enterprise networks. Successful exploitation of the most severe of … Read More “Multiple Vulnerabilities in Cisco Products Could Allow for Remote Code Execution – Cyber Security Advisories – MS-ISAC” »
By 31 March 2026, organisations should have alternatives to Mail Check and Web Check in place. – Read More – NCSC Feed