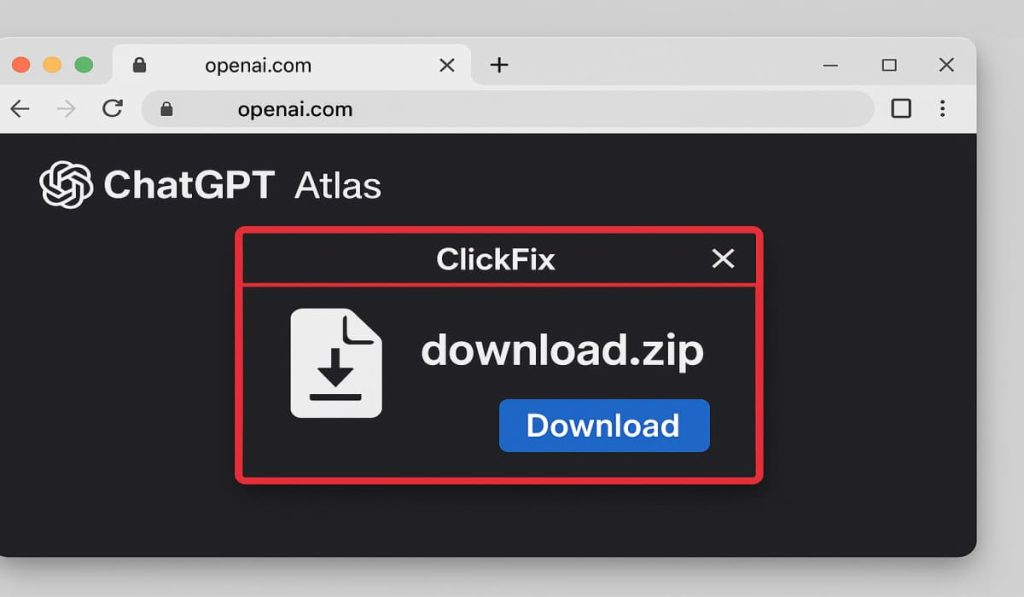
One-Person Production: Wondershare Filmora V15 Empowers Solo Creators With AI – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
AI is transforming the video-making process of creators. Learn how WondershareFilmora V15 helps individual creators edit smarter using powerful AI. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More












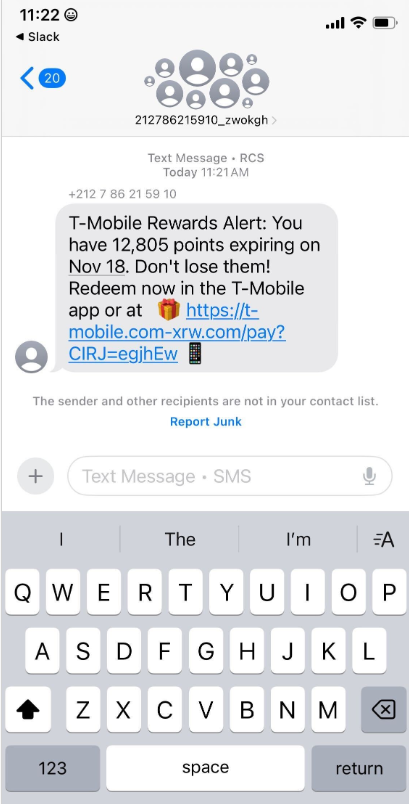







![5 Threats That Reshaped Web Security This Year [2025] – The Hacker News](https://attackfeed.com/wp-content/uploads/2025/12/reflectiz-rUVNK0.jpg)