For decades, the United States government and private sector have worked tirelessly to secure cyberspace, yet our nation remains frighteningly vulnerable to a litany of cyberthreats posed by cybercriminals and foreign adversaries alike. Daily news reports of cyber intrusions ranging from criminal ransomware attacks to foreign state-sponsored intrusions into power, water, and other critical infrastructure systems … Read More “The ten key reforms that can close America’s cybersecurity gaps – CyberScoop” »
Category: Attack Feeds
Ukrainian Woman in US Custody for Aiding Russian NoName057 Hacker Group – Hackread – Cybersecurity News, Data Breaches, AI, and More

Ukrainian national Victoria Dubranova is in U.S. custody, accused of supporting Russian hacker group NoName057 in cyberattacks on critical infrastructure. She has pleaded not guilty. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Microsoft Issues Security Fixes for 56 Flaws, Including Active Exploit and Two Zero-Days – The Hacker News

Microsoft closed out 2025 with patches for 56 security flaws in various products across the Windows platform, including one vulnerability that has been actively exploited in the wild. Of the 56 flaws, three are rated Critical, and 53 are rated Important in severity. Two other defects are listed as publicly known at the time of … Read More “Microsoft Issues Security Fixes for 56 Flaws, Including Active Exploit and Two Zero-Days – The Hacker News” »
New Portuguese Law Shields Ethical Hackers from Prosecution – Hackread – Cybersecurity News, Data Breaches, AI, and More

Portugal updates its cybercrime law (Decree Law 125/2025) to grant ethical hackers a ‘safe harbour’ from prosecution. Learn the strict rules researchers must follow, including immediate disclosure to the CNCS, and how other nations are following this trend. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Fortinet, Ivanti, and SAP Issue Urgent Patches for Authentication and Code Execution Flaws – The Hacker News

Fortinet, Ivanti, and SAP have moved to address critical security flaws in their products that, if successfully exploited, could result in an authentication bypass and code execution. The Fortinet vulnerabilities affect FortiOS, FortiWeb, FortiProxy, and FortiSwitchManager and relate to a case of improper verification of a cryptographic signature. They are tracked as CVE-2025-59718 and – … Read More “Fortinet, Ivanti, and SAP Issue Urgent Patches for Authentication and Code Execution Flaws – The Hacker News” »
Microsoft today pushed updates to fix at least 56 security flaws in its Windows operating systems and supported software. This final Patch Tuesday of 2025 tackles one zero-day bug that is already being exploited, as well as two publicly disclosed vulnerabilities. Despite releasing a lower-than-normal number of security updates these past few months, Microsoft patched … Read More “Microsoft Patch Tuesday, December 2025 Edition – Krebs on Security” »
Synthetic media, including AI-generated deepfake audio and video, has been increasingly leveraged by criminals, scammers and spies to deceive individuals and businesses. Sometimes they do so by imitating an employee’s CEO, urging them to transfer large sums of money or provide them access to work accounts. Other times this fake media is created by a … Read More “Organizations can now buy cyber insurance that covers deepfakes – CyberScoop” »
The Dark Web Economy Behind Ad Fraud: What Marketers Don’t See – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Ad fraud networks use bots, deepfakes and spoofed traffic to drain PPC budgets. This report shows how fake clicks distort performance data. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Spiderman Phishing Kit Targets European Banks with Real-Time Credential Theft – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Varonis threat analysts warn about Spiderman, a dangerous new kit that automates attacks against European banks and crypto customers, stealing a victim’s full identity profile. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Microsoft addressed 57 vulnerabilities affecting its various products for business operations and core systems, including one actively exploited zero-day, the company said in its latest monthly security update. The zero-day vulnerability — CVE-2025-62221 — affects the Windows Cloud Files Mini Filter Driver and has a CVSS rating of 7.8. Attackers could exploit the use-after-free defect … Read More “Microsoft’s last Patch Tuesday of 2025 addresses 57 defects, including one zero-day – CyberScoop” »
Threat actors with ties to North Korea have likely become the latest to exploit the recently disclosed critical security React2Shell flaw in React Server Components (RSC) to deliver a previously undocumented remote access trojan dubbed EtherRAT. “EtherRAT leverages Ethereum smart contracts for command-and-control (C2) resolution, deploys five independent Linux persistence mechanisms, and – Read More … Read More “North Korea-linked Actors Exploit React2Shell to Deploy New EtherRAT Malware – The Hacker News” »
It’s the final patch Tuesday of 2025, but that doesn’t make it any less exciting. Put aside your holiday planning for just a moment as we review the latest security offering from Adobe and Microsoft. If you’d rather watch the full video recap covering the entire release, you can check out the Patch Report webcast … Read More “The December 2025 Security Update Review – Zero Day Initiative – Blog” »
Police Dismantle EUR 700 Million Crypto Scam That Used Deepfakes – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Europol and Eurojust led a massive international police operation that successfully dismantled a crypto fraud network that laundered over €700M using deepfake ads. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Four Threat Clusters Using CastleLoader as GrayBravo Expands Its Malware Service Infrastructure – The Hacker News

Four distinct threat activity clusters have been observed leveraging a malware loader known as CastleLoader, strengthening the previous assessment that the tool is offered to other threat actors under a malware-as-a-service (MaaS) model. The threat actor behind CastleLoader has been assigned the name GrayBravo by Recorded Future’s Insikt Group, which was previously tracking it as … Read More “Four Threat Clusters Using CastleLoader as GrayBravo Expands Its Malware Service Infrastructure – The Hacker News” »
The AI Fix #80: DeepSeek’s cheap GPT-5 rival, Antigravity fails, and why being rude to AI makes it smarter – Graham Cluley

In episode 80 of The AI Fix, your hosts look at DeepSeek 3.2 “Speciale”, the bargain-basement model that claims GPT-5-level brains at 10% of the price, Jensen Huang’s reassuring vision of a robot fashion industry, and a 75kg T-800 style humanoid that can do flying kicks because robot-marketing departments have clearly learned nothing from Terminator. … Read More “The AI Fix #80: DeepSeek’s cheap GPT-5 rival, Antigravity fails, and why being rude to AI makes it smarter – Graham Cluley” »
California man admits role in $263 million cryptocurrency theft that funded lavish lifestyle – Graham Cluley

When you spend half a million dollars in a single night at a nightclub, purchase exotic cars worth millions, and rent mansions under false names, you are risking drawing attention to yourself… Read more in my article on the Hot for Security blog. – Read More – Graham Cluley
SimpleX Chat X Account Hacked, Fake Site Promotes Crypto Wallet Scam – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

SimpleX Chat’s X account hacked to promote fake crypto site urging users to connect wallets. Site mimicked official design to steal funds. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Storm-0249 Escalates Ransomware Attacks with ClickFix, Fileless PowerShell, and DLL Sideloading – The Hacker News

The threat actor known as Storm-0249 is likely shifting from its role as an initial access broker to adopt a combination of more advanced tactics like domain spoofing, DLL side-loading, and fileless PowerShell execution to facilitate ransomware attacks. “These methods allow them to bypass defenses, infiltrate networks, maintain persistence, and operate undetected, raising serious concerns … Read More “Storm-0249 Escalates Ransomware Attacks with ClickFix, Fileless PowerShell, and DLL Sideloading – The Hacker News” »
New GeminiJack 0-Click Flaw in Gemini AI Exposed Users to Data Leaks – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Google AI systems (Gemini Enterprise) had a critical ‘GeminiJack’ security flaw allowing attackers to steal Gmail, Docs, and Calendar data with no clicks. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Google on Monday announced a set of new security features in Chrome, following the company’s addition of agentic artificial intelligence (AI) capabilities to the web browser. To that end, the tech giant said it has implemented layered defenses to make it harder for bad actors to exploit indirect prompt injections that arise as a result … Read More “Google Adds Layered Defenses to Chrome to Block Indirect Prompt Injection Threats – The Hacker News” »
Zero Trust helps organizations shrink their attack surface and respond to threats faster, but many still struggle to implement it because their security tools don’t share signals reliably. 88% of organizations admit they’ve suffered significant challenges in trying to implement such approaches, according to Accenture. When products can’t communicate, real-time access decisions break down. The … Read More “How to Streamline Zero Trust Using the Shared Signals Framework – The Hacker News” »
STAC6565 Targets Canada in 80% of Attacks as Gold Blade Deploys QWCrypt Ransomware – The Hacker News

Canadian organizations have emerged as the focus of a targeted cyber campaign orchestrated by a threat activity cluster known as STAC6565. Cybersecurity company Sophos said it investigated almost 40 intrusions linked to the threat actor between February 2024 and August 2025. The campaign is assessed with high confidence to share overlaps with a hacking group … Read More “STAC6565 Targets Canada in 80% of Attacks as Gold Blade Deploys QWCrypt Ransomware – The Hacker News” »
Researchers Find Malicious VS Code, Go, npm, and Rust Packages Stealing Developer Data – The Hacker News

Cybersecurity researchers have discovered two new extensions on Microsoft Visual Studio Code (VS Code) Marketplace that are designed to infect developer machines with stealer malware. The VS Code extensions masquerade as a premium dark theme and an artificial intelligence (AI)-powered coding assistant, but, in actuality, harbor covert functionality to download additional payloads, take – Read … Read More “Researchers Find Malicious VS Code, Go, npm, and Rust Packages Stealing Developer Data – The Hacker News” »
The State Department is seeking help to locate a pair of hackers allegedly working for Shahid Shushtari, a malicious cyber unit operating under Iran’s Revolutionary Guard Corps Cyber-Electronic Command. Officials are offering a reward up to $10 million for information about Mohammad Bagher Shirinkar and Fatemeh Sedighian Kashi. “Help us take the smile off their … Read More “Officials offer $10M reward for information on IRGC-linked leader and close associate – CyberScoop” »
ChrimeraWire Trojan Fakes Chrome Activity to Manipulate Search Rankings – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

ChrimeraWire is a new Windows trojan that automates web browsing through Chrome to simulate user activity and manipulate search engine rankings. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Cybersecurity researchers are calling attention to a new campaign dubbed JS#SMUGGLER that has been observed leveraging compromised websites as a distribution vector for a remote access trojan named NetSupport RAT. The attack chain, analyzed by Securonix, involves three main moving parts: An obfuscated JavaScript loader injected into a website, an HTML Application (HTA) that runs … Read More “Experts Confirm JS#SMUGGLER Uses Compromised Sites to Deploy NetSupport RAT – The Hacker News” »
Ransomware is on the decline, according to a study the Treasury Department released Thursday, pointing to fewer attacks and payments following an all-time spike in activity in 2023. The Financial Crimes Enforcement Network (FinCEN) report on ransomware trends concluded more positive development in payments — the critical and most visible layer of attacks that have … Read More “Is ransomware finally on the decline? Treasury data offers cautious hope – CyberScoop” »
New JS#SMUGGLER Campaign Drops NetSupport RAT Through Infected Sites – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Securonix Threat Research details the complex JS#SMUGGLER campaign, a three-step web attack using obfuscated JavaScript and hidden HTA files to install the NetSupport RAT on user Windows desktops, granting hackers full remote control and persistent access. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Cybersecurity researchers are calling attention to a new campaign dubbed JS#SMUGGLER that has been observed leveraging compromised websites as a distribution vector for a remote access trojan named NetSupport RAT. The attack chain, analyzed by Securonix, involves three main moving parts: An obfuscated JavaScript loader injected into a website, an HTML Application (HTA) that runs … Read More “Experts Confirm JS#SMUGGLER Uses Compromised Sites to Deploy NetSupport RAT – The Hacker News” »
The UK’s top cyber agency issued a warning to the public Monday: large language model AI tools may always contain a persistent flaw that allows malicious actors to hijack models and potentially weaponize them against users. When ChatGPT launched in 2022, security researchers began testing the tool and other LLMs for functionality, security and privacy. … Read More “UK cyber agency warns LLMs will always be vulnerable to prompt injection – CyberScoop” »
INE Earns G2 Winter 2026 Badges Across Global Markets – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Cary, North Carolina, USA, 8th December 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
The Defense Department would require that senior leaders have secure mobile phones, that personnel would get cybersecurity training that includes a focus on artificial intelligence and that cyber troops would have access to mental health services under a compromise annual defense policy bill released over the weekend. The deal between House and Senate negotiators on … Read More “Defense bill addresses secure phones, AI training, cyber troop mental health – CyberScoop” »
Grok, the AI chatbot developed by Elon Musk’s xAI, has been found to exhibit more alarming behaviour – this time revealing the home addresses of ordinary people upon request. Read more in my article on the Hot for Security blog. – Read More – Graham Cluley
The holiday season compresses risk into a short, high-stakes window. Systems run hot, teams run lean, and attackers time automated campaigns to get maximum return. Multiple industry threat reports show that bot-driven fraud, credential stuffing and account takeover attempts intensify around peak shopping events, especially the weeks around Black Friday and Christmas. Why holiday peaks … Read More “How Can Retailers Cyber-Prepare for the Most Vulnerable Time of the Year? – The Hacker News” »
It’s been a week of chaos in code and calm in headlines. A bug that broke the internet’s favorite framework, hackers chasing AI tools, fake apps stealing cash, and record-breaking cyberattacks — all within days. If you blink, you’ll miss how fast the threat map is changing. New flaws are being found, published, and exploited … Read More “⚡ Weekly Recap: USB Malware, React2Shell, WhatsApp Worms, AI IDE Bugs & More – The Hacker News” »
Space Bears Ransomware Claims Comcast Data Theft Through QuasarBreach – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Space Bears ransowmare claims it obtained Comcast files through a breach at Quasar Inc, with threats to publish the data and separate leaks promised from Quasar itself. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Over 70 Domains Used in Months-Long Phishing Spree Against US Universities – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Infoblox Threat Intel reports a campaign that used the Evilginx phishing kit to bypass Multi-Factor Authentication (MFA) and steal credentials from 18 US universities between April and November 2025. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Android Malware FvncBot, SeedSnatcher, and ClayRat Gain Stronger Data Theft Features – The Hacker News

Cybersecurity researchers have disclosed details of two new Android malware families dubbed FvncBot and SeedSnatcher, as another upgraded version of ClayRat has been spotted in the wild. The findings come from Intel 471, CYFIRMA, and Zimperium, respectively. FvncBot, which masquerades as a security app developed by mBank, targets mobile banking users in Poland. What’s notable … Read More “Android Malware FvncBot, SeedSnatcher, and ClayRat Gain Stronger Data Theft Features – The Hacker News” »
Sneeit WordPress RCE Exploited in the Wild While ICTBroadcast Bug Fuels Frost Botnet Attacks – The Hacker News

A critical security flaw in the Sneeit Framework plugin for WordPress is being actively exploited in the wild, per data from Wordfence. The remote code execution vulnerability in question is CVE-2025-6389 (CVSS score: 9.8), which affects all versions of the plugin prior to and including 8.3. It has been patched in version 8.4, released on … Read More “Sneeit WordPress RCE Exploited in the Wild While ICTBroadcast Bug Fuels Frost Botnet Attacks – The Hacker News” »
MuddyWater Deploys UDPGangster Backdoor in Targeted Turkey-Israel-Azerbaijan Campaign – The Hacker News

The Iranian hacking group known as MuddyWater has been observed leveraging a new backdoor dubbed UDPGangster that uses the User Datagram Protocol (UDP) for command-and-control (C2) purposes. The cyber espionage activity targeted users in Turkey, Israel, and Azerbaijan, according to a report from Fortinet FortiGuard Labs. “This malware enables remote control of compromised systems by … Read More “MuddyWater Deploys UDPGangster Backdoor in Targeted Turkey-Israel-Azerbaijan Campaign – The Hacker News” »
Researchers Uncover 30+ Flaws in AI Coding Tools Enabling Data Theft and RCE Attacks – The Hacker News

Over 30 security vulnerabilities have been disclosed in various artificial intelligence (AI)-powered Integrated Development Environments (IDEs) that combine prompt injection primitives with legitimate features to achieve data exfiltration and remote code execution. The security shortcomings have been collectively named IDEsaster by security researcher Ari Marzouk (MaccariTA). They affect popular – Read More – The Hacker … Read More “Researchers Uncover 30+ Flaws in AI Coding Tools Enabling Data Theft and RCE Attacks – The Hacker News” »
Researchers Uncover 30+ Flaws in AI Coding Tools Enabling Data Theft and RCE Attacks – The Hacker News

Over 30 security vulnerabilities have been disclosed in various artificial intelligence (AI)-powered Integrated Development Environments (IDEs) that combine prompt injection primitives with legitimate features to achieve data exfiltration and remote code execution. The security shortcomings have been collectively named IDEsaster by security researcher Ari Marzouk (MaccariTA). They affect popular – Read More – The Hacker … Read More “Researchers Uncover 30+ Flaws in AI Coding Tools Enabling Data Theft and RCE Attacks – The Hacker News” »
Barts Health NHS Confirms Cl0p Ransomware Behind Data Breach – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Barts Health NHS confirms Cl0p ransomware breach via Oracle flaw. Invoice data exposed. Patient records and clinical systems remain unaffected. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Drones to Diplomas: How Russia’s Largest Private University is Linked to a $25M Essay Mill – Krebs on Security
A sprawling academic cheating network turbocharged by Google Ads that has generated nearly $25 million in revenue has curious ties to a Kremlin-connected oligarch whose Russian university builds drones for Russia’s war against Ukraine. The Nerdify homepage. The link between essay mills and Russian attack drones might seem improbable, but understanding it begins with a … Read More “Drones to Diplomas: How Russia’s Largest Private University is Linked to a $25M Essay Mill – Krebs on Security” »
Chinese State Hackers Use New BRICKSTORM Malware Against VMware Systems – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

CISA, NSA, and Canadian Cyber Centre warn that PRC state-sponsored hackers are using BRICKSTORM, a stealthy Go-based backdoor, for long-term espionage in Government and IT networks. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday formally added a critical security flaw impacting React Server Components (RSC) to its Known Exploited Vulnerabilities (KEV) catalog following reports of active exploitation in the wild. The vulnerability, CVE-2025-55182 (CVSS score: 10.0), relates to a case of remote code execution that could be triggered by … Read More “Critical React2Shell Flaw Added to CISA KEV After Confirmed Active Exploitation – The Hacker News” »
Attackers of different origins and motivations swiftly exploited a critical vulnerability dubbed React2Shell, affecting React Server Components shortly after Meta and the React team publicly disclosed the flaw with a patch Wednesday. Multiple security firms are actively responding to active exploitation in the wild as a scrum of reports conclude the malicious activity is limited … Read More “Attackers hit React defect as researchers quibble over proof – CyberScoop” »
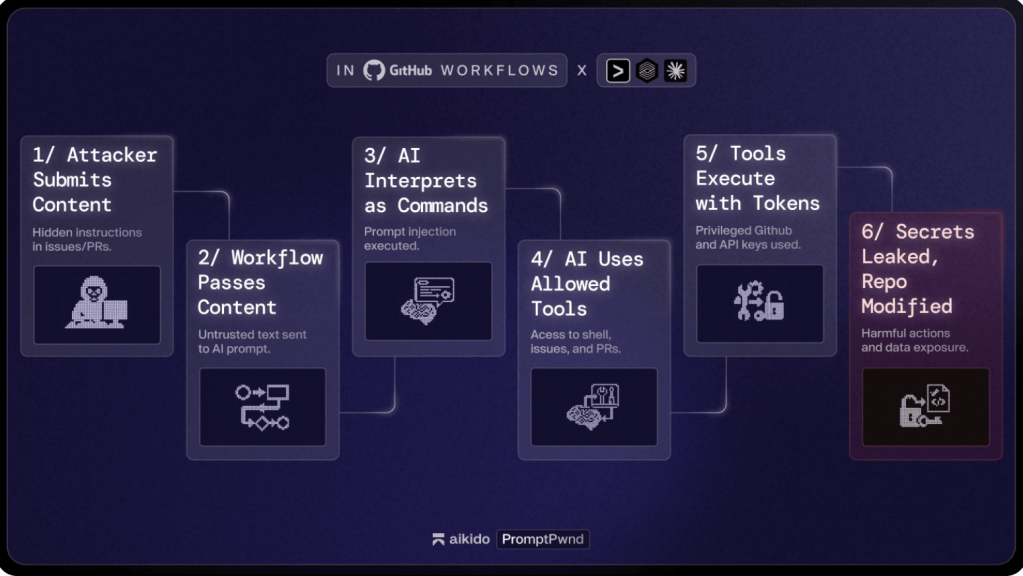
Agentic AI tools are being pushed into software development pipelines, IT networks and other business workflows. But using these tools can quickly turn into a supply chain nightmare for organizations, introducing untrusted or malicious content into their workstream that are then regularly treated as instructions by the underlying large language models powering the tools. Researchers … Read More “More evidence your AI agents can be turned against you – CyberScoop” »
Zero-Click Agentic Browser Attack Can Delete Entire Google Drive Using Crafted Emails – The Hacker News
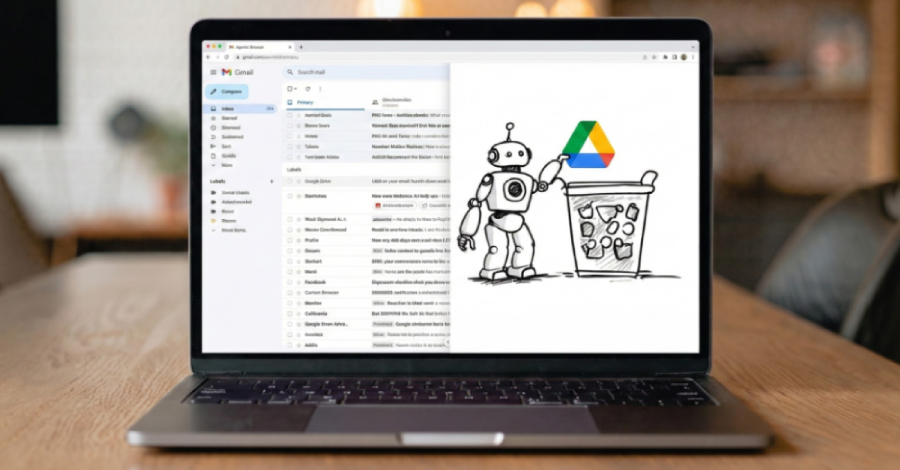
A new agentic browser attack targeting Perplexity’s Comet browser that’s capable of turning a seemingly innocuous email into a destructive action that wipes a user’s entire Google Drive contents, findings from Straiker STAR Labs show. The zero-click Google Drive Wiper technique hinges on connecting the browser to services like Gmail and Google Drive to automate … Read More “Zero-Click Agentic Browser Attack Can Delete Entire Google Drive Using Crafted Emails – The Hacker News” »
Bipartisan health care cybersecurity legislation returns to address a cornucopia of issues – CyberScoop

A bipartisan group of senators are looking to tackle health care cybersecurity by reviving legislation that would update regulations and guidelines, authorize grants, offer training and clarify federal agency roles. It’s a subset of cybersecurity where Congress hasn’t enacted any sweeping changes to date. The resurrected Health Care Cybersecurity and Resiliency Act from Health, Education … Read More “Bipartisan health care cybersecurity legislation returns to address a cornucopia of issues – CyberScoop” »