Cybersecurity researchers have disclosed details of an active phishing campaign that’s targeting a wide range of sectors in Russia with phishing emails that deliver Phantom Stealer via malicious ISO optical disc images. The activity, codenamed Operation MoneyMount-ISO by Seqrite Labs, has primarily singled out finance and accounting entities, with those in the procurement, legal, payroll … Read More “Phantom Stealer Spread by ISO Phishing Emails Hitting Russian Finance Sector – The Hacker News” »
Category: Attack Feeds
Critical React2Shell Vulnerability (CVE-2025-55182) Analysis: Surge in Attacks Targeting RSC-Enabled Services Worldwide – Hackread – Cybersecurity News, Data Breaches, AI, and More

Torrance, United States / California, December 12th, 2025, CyberNewsWire In December 2025, CVE-2025-55182 (React2Shell), a vulnerability in React… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The pro-Russian hacktivist group known as CyberVolk (aka GLORIAMIST) has resurfaced with a new ransomware-as-a-service (RaaS) offering called VolkLocker that suffers from implementation lapses in test artifacts, allowing users to decrypt files without paying an extortion fee. According to SentinelOne, VolkLocker (aka CyberVolk 2.x) emerged in August 2025 and is capable of targeting both Windows … Read More “VolkLocker Ransomware Exposed by Hard-Coded Master Key Allowing Free Decryption – The Hacker News” »
UK’s ICO Fine LastPass £1.2 Million Over 2022 Security Breach – Hackread – Cybersecurity News, Data Breaches, AI, and More

UK’s ICO fines LastPass £1.2M for the 2022 data breach that exposed 1.6 million users’ data. Learn how a flaw in an employee’s personal PC led to the massive security failure. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added a high-severity flaw impacting Sierra Wireless AirLink ALEOS routers to its Known Exploited Vulnerabilities (KEV) catalog, following reports of active exploitation in the wild. CVE-2018-4063 (CVSS score: 8.8/9.9) refers to an unrestricted file upload vulnerability that could be exploited to achieve remote code – … Read More “CISA Adds Actively Exploited Sierra Wireless Router Flaw Enabling RCE Attacks – The Hacker News” »
Apple on Friday released security updates for iOS, iPadOS, macOS, tvOS, watchOS, visionOS, and its Safari web browser to address two security flaws that it said have been exploited in the wild, one of which is the same flaw that was patched by Google in Chrome earlier this week. The vulnerabilities are listed below – … Read More “Apple Issues Security Updates After Two WebKit Flaws Found Exploited in the Wild – The Hacker News” »
Fake Microsoft Teams and Google Meet Downloads Spread Oyster Backdoor – Hackread – Cybersecurity News, Data Breaches, AI, and More

The Oyster backdoor (also known as Broomstick) is targeting the financial world, using malicious search ads for PuTTY, Teams, and Google Meet. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Development Team Augmentation: A Strategic Approach for High-Performance Teams – Hackread – Cybersecurity News, Data Breaches, AI, and More

Scale software teams fast with development team augmentation. Learn when it works best, key models, common mistakes, and how to choose the right partner. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The Department of Justice is suing Fulton County, Georgia and its election clerk over the county’s refusal to hand over voter records, part of a larger nationwide project to collect as much election and voter information as possible from state and local governments ahead of the 2026 and 2028 elections. In a lawsuit announced Thursday, … Read More “DOJ sues Fulton County over 2020 voter data – CyberScoop” »
Cybersecurity researchers are calling attention to a new campaign that’s leveraging GitHub-hosted Python repositories to distribute a previously undocumented JavaScript-based Remote Access Trojan (RAT) dubbed PyStoreRAT. “These repositories, often themed as development utilities or OSINT tools, contain only a few lines of code responsible for silently downloading a remote HTA file and executing – Read … Read More “Fake OSINT and GPT Utility GitHub Repos Spread PyStoreRAT Malware Payloads – The Hacker News” »
New PyStoreRAT Malware Targets OSINT Researchers Through GitHub – Hackread – Cybersecurity News, Data Breaches, AI, and More

A new malware called PyStoreRAT is being through fake OSINT tools on GitHub targeting IT and OSINT pros. Read Morphisec’s report detailing how it uses AI and evades security. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
What Happens Inside PDFAid in Seconds: From Upload to Download – Hackread – Cybersecurity News, Data Breaches, AI, and More
Disclosure: This article was submitted by PDFAid for publication. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
President Donald Trump announced Thursday his intention to issue a federal pardon for an individual convicted in connection with efforts related to challenging the 2020 election results. However, on this occasion, the person in question will remain behind bars. In a statement on Truth Social, Trump said he was pardoning Tina Peters, a former Mesa County … Read More “Trump moves to pardon Colorado election clerk Tina Peters, even though he can’t – CyberScoop” »
New Advanced Phishing Kits Use AI and MFA Bypass Tactics to Steal Credentials at Scale – The Hacker News

Cybersecurity researchers have documented four new phishing kits named BlackForce, GhostFrame, InboxPrime AI, and Spiderman that are capable of facilitating credential theft at scale. BlackForce, first detected in August 2025, is designed to steal credentials and perform Man-in-the-Browser (MitB) attacks to capture one-time passwords (OTPs) and bypass multi-factor authentication (MFA). The kit – Read More … Read More “New Advanced Phishing Kits Use AI and MFA Bypass Tactics to Steal Credentials at Scale – The Hacker News” »
Analyst firm Gartner has issued a blunt warning to organizations: Agentic AI browsers introduce serious new security risks and should be blocked “for the foreseeable future.” Read more in my article on the Fortra blog. – Read More – Graham Cluley
Securing GenAI in the Browser: Policy, Isolation, and Data Controls That Actually Work – The Hacker News

The browser has become the main interface to GenAI for most enterprises: from web-based LLMs and copilots, to GenAI‑powered extensions and agentic browsers like ChatGPT Atlas. Employees are leveraging the power of GenAI to draft emails, summarize documents, work on code, and analyze data, often by copying/pasting sensitive information directly into prompts or uploading files. … Read More “Securing GenAI in the Browser: Policy, Isolation, and Data Controls That Actually Work – The Hacker News” »
Securing GenAI in the Browser: Policy, Isolation, and Data Controls That Actually Work – The Hacker News

The browser has become the main interface to GenAI for most enterprises: from web-based LLMs and copilots, to GenAI‑powered extensions and agentic browsers like ChatGPT Atlas. Employees are leveraging the power of GenAI to draft emails, summarize documents, work on code, and analyze data, often by copying/pasting sensitive information directly into prompts or uploading files. … Read More “Securing GenAI in the Browser: Policy, Isolation, and Data Controls That Actually Work – The Hacker News” »
React2Shell Exploitation Escalates into Large-Scale Global Attacks, Forcing Emergency Mitigation – The Hacker News

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has urged federal agencies to patch the recent React2Shell vulnerability by December 12, 2025, amid reports of widespread exploitation. The critical vulnerability, tracked as CVE-2025-55182 (CVSS score: 10.0), affects the React Server Components (RSC) Flight protocol. The underlying cause of the issue is an unsafe deserialization – … Read More “React2Shell Exploitation Escalates into Large-Scale Global Attacks, Forcing Emergency Mitigation – The Hacker News” »
The React team has released fixes for two new types of flaws in React Server Components (RSC) that, if successfully exploited, could result in denial-of-service (DoS) or source code exposure. The team said the issues were found by the security community while attempting to exploit the patches released for CVE-2025-55182 (CVSS score: 10.0), a critical … Read More “New React RSC Vulnerabilities Enable DoS and Source Code Exposure – The Hacker News” »
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a high-severity security flaw impacting OSGeo GeoServer to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation in the wild. The vulnerability in question is CVE-2025-58360 (CVSS score: 8.2), an unauthenticated XML External Entity (XXE) flaw that affects all versions prior … Read More “CISA Flags Actively Exploited GeoServer XXE Flaw in Updated KEV Catalog – The Hacker News” »
A fresh effort is mounting in Congress to require federal agents to obtain a warrant before searching a government surveillance database for information about U.S. citizens, as Congress again faces an impending deadline, in four months, to renew a major surveillance law. But there are also signs that renewal of Section 702 of the Foreign … Read More “Warrant requirements, Democratic worries could factor into spy law renewal debate – CyberScoop” »
Malicious Visual Studio Code Extensions Hide Trojan in Fake PNG Files – Hackread – Cybersecurity News, Data Breaches, AI, and More

VS Code developers beware: ReversingLabs found 19 malicious extensions hiding trojans inside a popular dependency, disguising the final malware payload as a standard PNG image file. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
New ‘DroidLock’ Android Malware Locks Users Out, Spies via Front Camera – Hackread – Cybersecurity News, Data Breaches, AI, and More

Zimperium zLabs reveals DroidLock, a new Android malware acting like ransomware that can hijack Android devices, steal credentials via phishing, and stream your screen via VNC. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
1inch Named Exclusive Swap Provider at Launch for Ledger Multisig – Hackread – Cybersecurity News, Data Breaches, AI, and More
Road Town, British Virgin Islands, 11th December 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
As enterprises refine their strategies for handling Non-Human Identities (NHIs), Robotic Process Automation (RPA) has become a powerful tool for streamlining operations and enhancing security. However, since RPA bots have varying levels of access to sensitive information, enterprises must be prepared to mitigate a variety of challenges. In large organizations, bots are starting to outnumber … Read More “The Impact of Robotic Process Automation (RPA) on Identity and Access Management – The Hacker News” »
INE Highlights Enterprise Shift Toward Hands-On Training Amid Widening Skills Gaps – Hackread – Cybersecurity News, Data Breaches, AI, and More

Cary, North Carolina, USA, 11th December 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Scammers Sent 40,000 E-Signature Phishing Emails to 6,000 Firms in Just 2 Weeks – Hackread – Cybersecurity News, Data Breaches, AI, and More
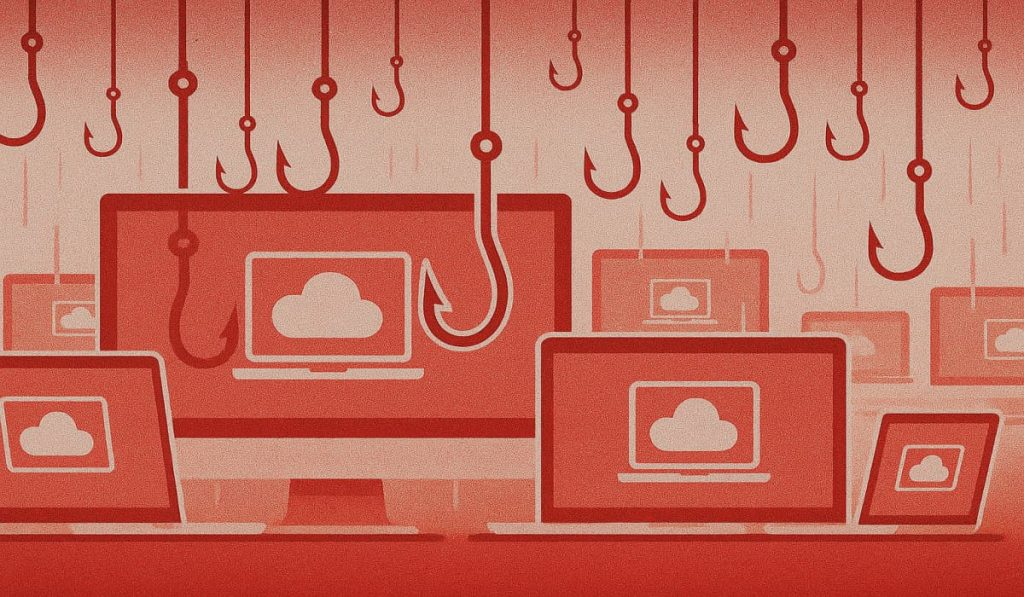
Phishing campaign: Scammers sent over 40,000 spoofed SharePoint, DocuSign and e-sign emails to companies, hiding malicious links behind trusted redirect services. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Cybersecurity researchers have disclosed details of a new fully-featured Windows backdoor called NANOREMOTE that uses the Google Drive API for command-and-control (C2) purposes. According to a report from Elastic Security Labs, the malware shares code similarities with another implant codenamed FINALDRAFT (aka Squidoor) that employs Microsoft Graph API for C2. FINALDRAFT is attributed to a … Read More “NANOREMOTE Malware Uses Google Drive API for Hidden Control on Windows Systems – The Hacker News” »
ThreatsDay Bulletin: Spyware Alerts, Mirai Strikes, Docker Leaks, ValleyRAT Rootkit — and 20 More Stories – The Hacker News

This week’s cyber stories show how fast the online world can turn risky. Hackers are sneaking malware into movie downloads, browser add-ons, and even software updates people trust. Tech giants and governments are racing to plug new holes while arguing over privacy and control. And researchers keep uncovering just how much of our digital life … Read More “ThreatsDay Bulletin: Spyware Alerts, Mirai Strikes, Docker Leaks, ValleyRAT Rootkit — and 20 More Stories – The Hacker News” »
Global cybersecurity agencies have issued the first unified guidance on applying artificial intelligence (AI) within critical infrastructure, signaling a major shift from theoretical debate to practical guardrails for safety and reliability. The release of joint guidance on Principles for the Secure Integration of Artificial Intelligence in Operational Technology marks a meaningful milestone for critical infrastructure … Read More “New cybersecurity guidance paves the way for AI in critical infrastructure – CyberScoop” »
Top 10 Data Anonymization Solutions for 2026 – Hackread – Cybersecurity News, Data Breaches, AI, and More

Every business today has to deal with private information – whether it is about customers, employees, or financial… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
An advanced persistent threat (APT) known as WIRTE has been attributed to attacks targeting government and diplomatic entities across the Middle East with a previously undocumented malware suite dubbed AshTag since 2020. Palo Alto Networks is tracking the activity cluster under the name Ashen Lepus. Artifacts uploaded to the VirusTotal platform show that the threat … Read More “WIRTE Leverages AshenLoader Sideloading to Install the AshTag Espionage Backdoor – The Hacker News” »
Chrome Targeted by Active In-the-Wild Exploit Tied to Undisclosed High-Severity Flaw – The Hacker News

Google on Wednesday shipped security updates for its Chrome browser to address three security flaws, including one it said has come under active exploitation in the wild. The vulnerability, rated high in severity, is being tracked under the Chromium issue tracker ID “466192044.” Unlike other disclosures, Google has opted to keep information about the CVE … Read More “Chrome Targeted by Active In-the-Wild Exploit Tied to Undisclosed High-Severity Flaw – The Hacker News” »
CastleLoader Malware Now Uses Python Loader to Bypass Security – Hackread – Cybersecurity News, Data Breaches, AI, and More
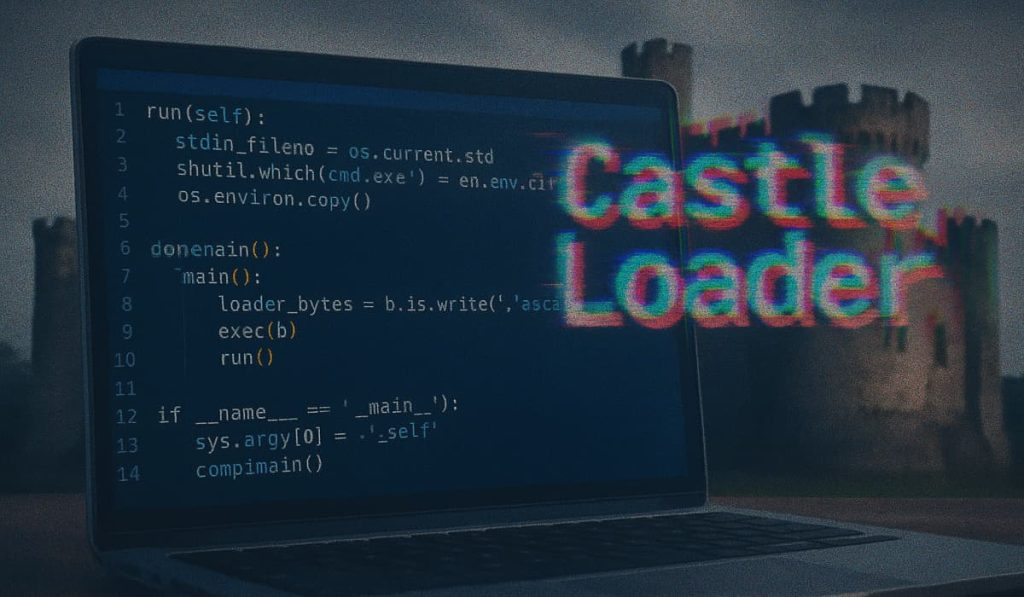
Cybersecurity researchers at Blackpoint Cyber discovered a new, evasive CastleLoader malware variant using Python and ClickFix social engineering to deliver RATs and info-stealers directly from memory. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A high-severity unpatched security vulnerability in Gogs has come under active exploitation, with more than 700 compromised instances accessible over the internet, according to new findings from Wiz. The flaw, tracked as CVE-2025-8110 (CVSS score: 8.7), is a case of file overwrite in the file update API of the Go-based self-hosted Git service. A fix … Read More “Unpatched Gogs Zero-Day Exploited Across 700+ Instances Amid Active Attacks – The Hacker News” »
SIM Pharm Cyber crime Escalates in South Africa – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.

Just when you thought there couldn’t be another type of cyber thief, they develop new and devious methods to steal valuable information and finances. Over the last few yearsthere has been an uptick in “SIM pharm” crimes. This form of crime has encompassed avariety of scams including theft of banking credentials, impersonation, investment fraud,and online … Read More “SIM Pharm Cyber crime Escalates in South Africa – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.” »
Active Attacks Exploit Gladinet’s Hard-Coded Keys for Unauthorized Access and Code Execution – The Hacker News

Huntress is warning of a new actively exploited vulnerability in Gladinet’s CentreStack and Triofox products stemming from the use of hard-coded cryptographic keys that have affected nine organizations so far. “Threat actors can potentially abuse this as a way to access the web.config file, opening the door for deserialization and remote code execution,” security researcher … Read More “Active Attacks Exploit Gladinet’s Hard-Coded Keys for Unauthorized Access and Code Execution – The Hacker News” »
Smashing Security podcast #447: Grok the stalker, the Louvre heist, and Microsoft 365 mayhem – Graham Cluley

On this week’s show we learn that AI really can be a stalker’s best friend, as we explore a strange tale that starts with a manatee-shaped mailbox on a millionaire’s lawn and ends with Grok happily doxxing real people, mapping out stalking “strategies,” and handing out revenge-porn tips. Then we go inside the Louvre heist, … Read More “Smashing Security podcast #447: Grok the stalker, the Louvre heist, and Microsoft 365 mayhem – Graham Cluley” »
Security experts have observed a steady increase in malicious activity from a widening pool of attackers seeking to exploit React2Shell, a critical vulnerability disclosed last week in React Server Components. Authorities are also responding to heightened concern about the defect, with the Cybersecurity and Infrastructure Security Agency shortening the deadline for agencies to patch the … Read More “Attacks pinned to critical React2Shell defect surge, surpass 50 confirmed victims – CyberScoop” »
Torrent for DiCaprio’s “One Battle After Another” Movie Drops Agent Tesla – Hackread – Cybersecurity News, Data Breaches, AI, and More

Bitdefender researchers warn that the torrent for Leonardo DiCaprio’s One Battle After Another is a trap deploying Agent Tesla malware. Learn how the fileless LOTL attack targets unsuspecting Windows users. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
As the Trump administration considers loosening restrictions on the sale of high-performance computer chips that power modern artificial intelligence systems to China, his Department of Justice continues to prosecute businesses and individuals who sell or divert these same technologies to companies based in China. On Monday, federal prosecutors announced that it had secured a guilty … Read More “As White House moves to send AI chips to China, Trump’s DOJ prosecutes chip smugglers – CyberScoop” »
React2Shell Exploitation Delivers Crypto Miners and New Malware Across Multiple Sectors – The Hacker News
React2Shell continues to witness heavy exploitation, with threat actors leveraging the maximum-severity security flaw in React Server Components (RSC) to deliver cryptocurrency miners and an array of previously undocumented malware families, according to new findings from Huntress. This includes a Linux backdoor called PeerBlight, a reverse proxy tunnel named CowTunnel, and a Go-based – Read … Read More “React2Shell Exploitation Delivers Crypto Miners and New Malware Across Multiple Sectors – The Hacker News” »
.NET SOAPwn Flaw Opens Door for File Writes and Remote Code Execution via Rogue WSDL – The Hacker News

New research has uncovered exploitation primitives in the .NET Framework that could be leveraged against enterprise-grade applications to achieve remote code execution. WatchTowr Labs, which has codenamed the “invalid cast vulnerability” SOAPwn, said the issue impacts Barracuda Service Center RMM, Ivanti Endpoint Manager (EPM), and Umbraco 8. But the number of affected vendors is likely … Read More “.NET SOAPwn Flaw Opens Door for File Writes and Remote Code Execution via Rogue WSDL – The Hacker News” »
A new report from the United States’s Financial Crimes Enforcement Network (FinCEN) has shone a revealing light on the state of the criminal industry of ransomware. The report, which examines ransomware incidents from 2022 to 2024, reveals that attackers extorted more than $2.1 billion over the three-year period. Yes, that number is enormous – but … Read More “Ransomware may have extorted over $2.1 billion between 2022-2024, but it’s not all bad news, claims FinCEN report – Graham Cluley” »
North Korean Hackers Deploy EtherRAT Malware in React2Shell Exploits – Hackread – Cybersecurity News, Data Breaches, AI, and More
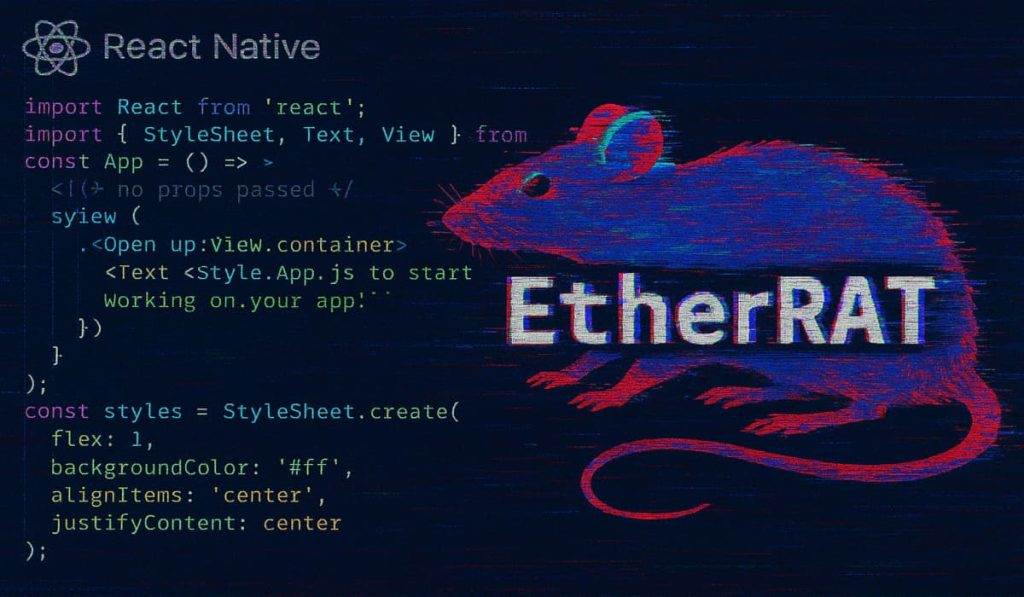
Sysdig discovered North Korea-linked EtherRAT, a stealthy new backdoor using Ethereum smart contracts for C2 after exploiting the critical React2Shell vulnerability (CVE-2025-55182). – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Three security vulnerabilities have been disclosed in the Peripheral Component Interconnect Express (PCIe) Integrity and Data Encryption (IDE) protocol specification that could expose a local attacker to serious risks. The flaws impact PCIe Base Specification Revision 5.0 and onwards in the protocol mechanism introduced by the IDE Engineering Change Notice (ECN), according to the PCI … Read More “Three PCIe Encryption Weaknesses Expose PCIe 5.0+ Systems to Faulty Data Handling – The Hacker News” »
The Justice Department has charged a Ukrainian national with conducting cyberattacks on critical infrastructure worldwide as part of two Russian state-sponsored hacking operations that targeted water systems, food processing facilities and government networks across the United States and allied nations. Victoria Eduardovna Dubranova, 33, was arraigned on a second indictment Tuesday after being extradited to … Read More “US charges hacker tied to Russian groups that targeted water systems and meat plants – CyberScoop” »
Remember when a notorious ransomware gang hit the Irish Health Service back in May 2021? Four years on, and it seems victims who had their data exposed will finally receive compensation. Read more in my article on the Hot for Security blog. – Read More – Graham Cluley
Webinar: How Attackers Exploit Cloud Misconfigurations Across AWS, AI Models, and Kubernetes – The Hacker News

Cloud security is changing. Attackers are no longer just breaking down the door; they are finding unlocked windows in your configurations, your identities, and your code. Standard security tools often miss these threats because they look like normal activity. To stop them, you need to see exactly how these attacks happen in the real world. … Read More “Webinar: How Attackers Exploit Cloud Misconfigurations Across AWS, AI Models, and Kubernetes – The Hacker News” »
Warning: WinRAR Vulnerability CVE-2025-6218 Under Active Attack by Multiple Threat Groups – The Hacker News

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a security flaw impacting the WinRAR file archiver and compression utility to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerability, tracked as CVE-2025-6218 (CVSS score: 7.8), is a path traversal bug that could enable code execution. However, for exploitation … Read More “Warning: WinRAR Vulnerability CVE-2025-6218 Under Active Attack by Multiple Threat Groups – The Hacker News” »