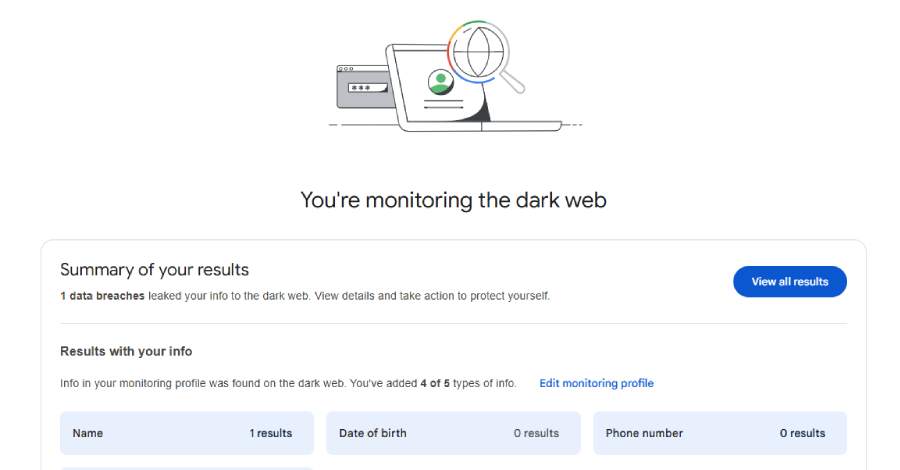
Threat Actors Continue to Attack South Africa in Cybercrime – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.

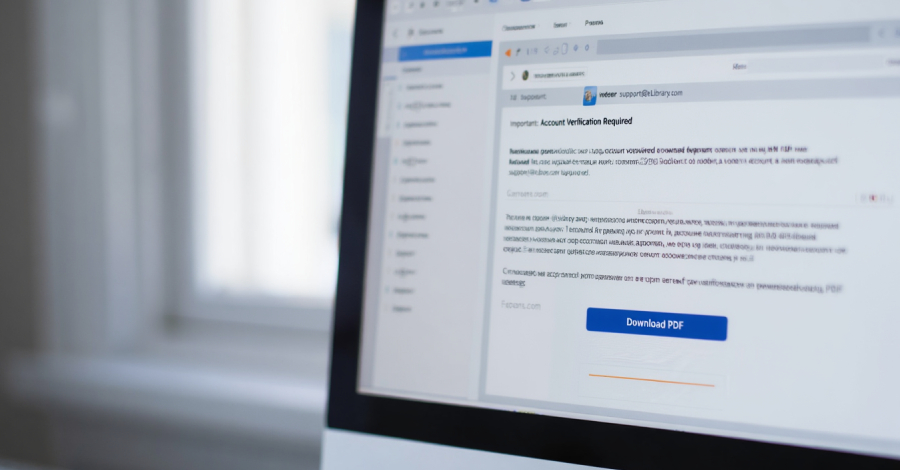
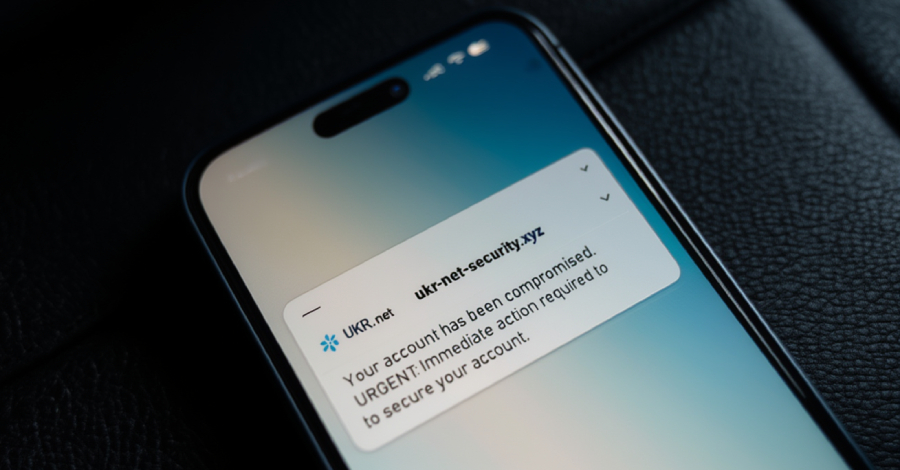
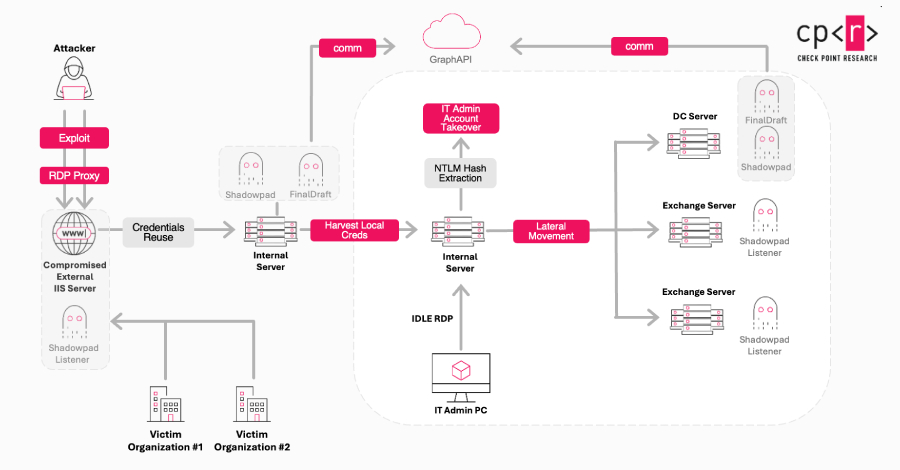
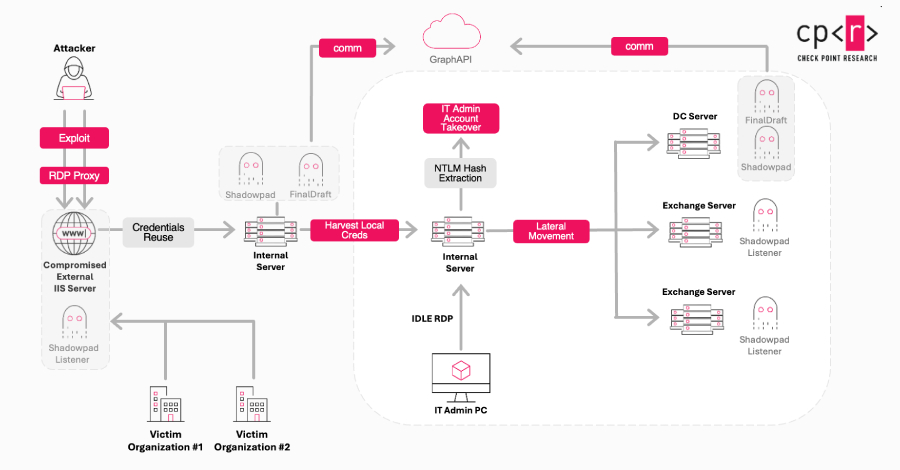
While authorities add new technologies and teams in their attempt to thwart cybercriminals, the stats are showing that in South Africa at least 50% of individuals polled have experienced some form of cybercrime; and the numbers continue to grow. The volume of internet users in South Africa is increasing and with this digital transformation threat … Read More “Threat Actors Continue to Attack South Africa in Cybercrime – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.” »