Agentic AI browsers like OpenAI’s Atlas have debuted to major fanfare, and the enthusiasm is warranted. These tools automate web browsing to close the gap between what you want to accomplish and getting it done. Rather than manually opening multiple tabs, you can simply tell the browser what you need. Ask it to file a … Read More “How to determine if agentic AI browsers are safe enough for your enterprise – CyberScoop” »
Category: Attack Feeds
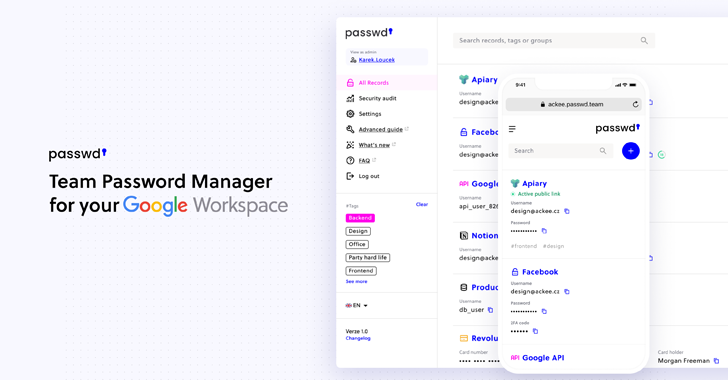
Passwd is designed specifically for organizations operating within Google Workspace. Rather than competing as a general consumer password manager, its purpose is narrow, and business-focused: secure credential storage, controlled sharing, and seamless Workspace integration. The platform emphasizes practicality over feature overload, aiming to provide a reliable system for teams that already rely – Read More … Read More “Passwd: A walkthrough of the Google Workspace Password Manager – The Hacker News” »
A law enforcement operation coordinated by INTERPOL has led to the recovery of $3 million and the arrest of 574 suspects by authorities from 19 countries, amidst a continued crackdown on cybercrime networks in Africa. The coordinated effort, named Operation Sentinel, took place between October 27 and November 27, 2025, and mainly focused on business … Read More “INTERPOL Arrests 574 in Africa; Ukrainian Ransomware Affiliate Pleads Guilty – The Hacker News” »
Pirate Group Anna’s Archive Copies 256M Spotify Songs in Data Scrape – Hackread – Cybersecurity News, Data Breaches, AI, and More

Spotify has confirmed a massive unauthorised data scrape involving 256 million track records and 86 million audio files. Learn how “Anna’s Archive” bypassed security, and why experts warn against downloading the leaked files. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The U.S. Justice Department (DoJ) on Monday announced the seizure of a web domain and database that it said was used to further a criminal scheme designed to target and defraud Americans by means of bank account takeover fraud. The domain in question, web3adspanels[.]org, was used as a backend web panel to host and manipulate … Read More “U.S. DoJ Seizes Fraud Domain Behind $14.6 Million Bank Account Takeover Scheme – The Hacker News” »
Critical n8n Flaw (CVSS 9.9) Enables Arbitrary Code Execution Across Thousands of Instances – The Hacker News

A critical security vulnerability has been disclosed in the n8n workflow automation platform that, if successfully exploited, could result in arbitrary code execution under certain circumstances. The vulnerability, tracked as CVE-2025-68613, carries a CVSS score of 9.9 out of a maximum of 10.0. The package has about 57,000 weekly downloads, according to statistics on npm. … Read More “Critical n8n Flaw (CVSS 9.9) Enables Arbitrary Code Execution Across Thousands of Instances – The Hacker News” »
The U.S. Federal Communications Commission (FCC) on Monday announced a ban on all drones and critical components made in a foreign country, citing national security concerns. To that end, the agency has added to its Covered List Uncrewed aircraft systems (UAS) and UAS critical components produced in a foreign country, and all communications and video … Read More “FCC Bans Foreign-Made Drones and Key Parts Over U.S. National Security Risks – The Hacker News” »
The National Institute of Standards and Technology announced that it will partner with The MITRE Corporation on a $20 million project to stand up two new research centers focused on artificial intelligence, including how the technology may impact cybersecurity for U.S. critical infrastructure. On Monday, the agency said one center will focus on advanced manufacturing … Read More “NIST, MITRE announce $20 million research effort on AI cybersecurity – CyberScoop” »
A 19-year-old man from San Antonio pleaded guilty Friday to multiple crimes involving the sexual exploitation of children while acting as an administrator and leader of 8884, a splinter group of the violent extremist collective known as 764. Alexis Aldair Chavez faces up to 60 years in prison for racketeering, distribution and possession of child … Read More “Leader of 764 offshoot pleads guilty, faces up to 60 years in jail – CyberScoop” »
Frogblight Malware Targets Android Users With Fake Court and Aid Apps – Hackread – Cybersecurity News, Data Breaches, AI, and More

Kaspersky warns of ‘Frogblight,’ a new Android malware draining bank accounts in Turkiye. Learn how this ‘court case’ scam steals your data and how to stay safe. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Cybersecurity researchers have disclosed details of a new malicious package on the npm repository that works as a fully functional WhatsApp API, but also contains the ability to intercept every message and link the attacker’s device to a victim’s WhatsApp account. The package, named “lotusbail,” has been downloaded over 56,000 times since it was first … Read More “Fake WhatsApp API Package on npm Steals Messages, Contacts, and Login Tokens – The Hacker News” »
Ukrainian National Pleads Guilty in Nefilim Ransomware Conspiracy – Hackread – Cybersecurity News, Data Breaches, AI, and More

Ukrainian man pleads guilty in United States to deploying Nefilim ransomware in global extortion scheme targeting companies across multiple countries. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Hackers Abuse Popular Monitoring Tool Nezha as a Stealth Trojan – Hackread – Cybersecurity News, Data Breaches, AI, and More

Cybersecurity firm Ontinue reveals how the open-source tool Nezha is being used as a Remote Access Trojan (RAT) to bypass security and control servers globally. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Insider Threat: Hackers Paying Company Insiders to Bypass Security – Hackread – Cybersecurity News, Data Breaches, AI, and More

A new report from Check Point Research reveals a growing trend of cyber criminals recruiting employees at banks, telecoms, and tech giants. Learn how hackers use the darknet and Telegram to offer payouts up to $15,000 for internal access to companies like Apple, Coinbase, and the Federal Reserve. – Read More – Hackread – Cybersecurity … Read More “Insider Threat: Hackers Paying Company Insiders to Bypass Security – Hackread – Cybersecurity News, Data Breaches, AI, and More” »
How an LMS Cloud Model Supports Scalable Learning – Hackread – Cybersecurity News, Data Breaches, AI, and More

There’s a new era for training and development programs, making the LMS (Learning Management System) cloud model the… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
As the internet becomes an essential part of daily life, its environmental footprint continues to grow. Data centers, constant connectivity, and resource-heavy browsing habits all contribute to energy consumption and digital waste. While individual users may not see this impact directly, the collective effect of everyday browsing is significant. Choosing a browser designed with – … Read More “How to Browse the Web More Sustainably With a Green Browser – The Hacker News” »
⚡ Weekly Recap: Firewall Exploits, AI Data Theft, Android Hacks, APT Attacks, Insider Leaks & More – The Hacker News

Cyber threats last week showed how attackers no longer need big hacks to cause big damage. They’re going after the everyday tools we trust most — firewalls, browser add-ons, and even smart TVs — turning small cracks into serious breaches. The real danger now isn’t just one major attack, but hundreds of quiet ones using … Read More “⚡ Weekly Recap: Firewall Exploits, AI Data Theft, Android Hacks, APT Attacks, Insider Leaks & More – The Hacker News” »
Android Malware Operations Merge Droppers, SMS Theft, and RAT Capabilities at Scale – The Hacker News

Threat actors have been observed leveraging malicious dropper apps masquerading as legitimate applications to deliver an Android SMS stealer dubbed Wonderland in mobile attacks targeting users in Uzbekistan. “Previously, users received ‘pure’ Trojan APKs that acted as malware immediately upon installation,” Group-IB said in an analysis published last week. “Now, adversaries increasingly deploy – Read … Read More “Android Malware Operations Merge Droppers, SMS Theft, and RAT Capabilities at Scale – The Hacker News” »
Threat hunters have discerned new activity associated with an Iranian threat actor known as Infy (aka Prince of Persia), nearly five years after the hacking group was observed targeting victims in Sweden, the Netherlands, and Turkey. “The scale of Prince of Persia’s activity is more significant than we originally anticipated,” Tomer Bar, vice president of … Read More “Iranian Infy APT Resurfaces with New Malware Activity After Years of Silence – The Hacker News” »
DevOps and Cybersecurity: Building a New Line of Defense Against Digital Threats – Hackread – Cybersecurity News, Data Breaches, AI, and More

Learn how DevOps and DevSecOps strengthen cybersecurity through automation, CI/CD, and secure DevOps development services. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
FBI Seizes Fake ID Template Domains Operating from Bangladesh – Hackread – Cybersecurity News, Data Breaches, AI, and More

US authorities have charged Zahid Hasan with running TechTreek, a $2.9 million online marketplace selling fake ID templates. The investigation, involving the FBI and Bangladesh police, uncovered a global scheme selling fraudulent passports and social security cards to over 1,400 customers. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The U.S. Department of Justice (DoJ) this week announced the indictment of 54 individuals in connection with a multi-million dollar ATM jackpotting scheme. The large-scale conspiracy involved deploying malware named Ploutus to hack into automated teller machines (ATMs) across the U.S. and force them to dispense cash. The indicted members are alleged to be part … Read More “U.S. DOJ Charges 54 in ATM Jackpotting Scheme Using Ploutus Malware – The Hacker News” »
Artem Aleksandrovych Stryzhak, a 35-year-old Ukrainian national, pleaded guilty Friday to multiple crimes stemming from his involvement in a string of ransomware attacks targeting U.S. and Europe-based organizations from mid 2018 to late 2021. He faces up to 10 years in jail for conspiracy to commit fraud, including extortion. Stryzhak was arrested in Spain in … Read More “Ukrainian national pleads guilty to Nefilim ransomware attacks – CyberScoop” »
Former cybersecurity professionals Ryan Clifford Goldberg and Kevin Tyler Martin pleaded guilty Thursday to participating in a series of ransomware attacks in 2023 while they were employed at cybersecurity companies tasked with helping organizations respond to ransomware attacks. Goldberg, who was a manager of incident response at Sygnia, and Martin, a ransomware negotiator at DigitalMint … Read More “Former incident responders plead guilty to ransomware attack spree – CyberScoop” »
The FBI said that unknown actors have continued to deploy AI voice cloning tools in an ongoing effort to impersonate U.S government officials and extract sensitive or classified information or conduct scams. The bureau initially warned back in May that the campaign had been ongoing since at least April 2025. In an update Friday, they … Read More “FBI says ‘ongoing’ deepfake impersonation of U.S. gov officials dates back to 2023 – CyberScoop” »
Russia-Linked Hackers Use Microsoft 365 Device Code Phishing for Account Takeovers – The Hacker News

A suspected Russia-aligned group has been attributed to a phishing campaign that employs device code authentication workflows to steal victims’ Microsoft 365 credentials and conduct account takeover attacks. The activity, ongoing since September 2025, is being tracked by Proofpoint under the moniker UNK_AcademicFlare. The attacks involve using compromised email addresses belonging to government – Read … Read More “Russia-Linked Hackers Use Microsoft 365 Device Code Phishing for Account Takeovers – The Hacker News” »
Keyboard Lag Leads Amazon to North Korean Impostor in Remote Role – Hackread – Cybersecurity News, Data Breaches, AI, and More

Amazon Security Chief explains how a subtle keyboard delay exposed a North Korean impostor. Read about the laptop farm scheme and how 110 milliseconds of lag ended a major corporate infiltration. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The Trump administration has pursued a staggering range of policy pivots this past year that threaten to weaken the nation’s ability and willingness to address a broad spectrum of technology challenges, from cybersecurity and privacy to countering disinformation, fraud and corruption. These shifts, along with the president’s efforts to restrict free speech and freedom of … Read More “Dismantling Defenses: Trump 2.0 Cyber Year in Review – Krebs on Security” »
Cybersecurity researchers have disclosed details of a new campaign that has used cracked software distribution sites as a distribution vector for a new version of a modular and stealthy loader known as CountLoader. The campaign “uses CountLoader as the initial tool in a multistage attack for access, evasion, and delivery of additional malware families,” Cyderes … Read More “Cracked Software and YouTube Videos Spread CountLoader and GachiLoader Malware – The Hacker News” »
Criminal IP and Palo Alto Networks Cortex XSOAR integrate to bring AI-driven exposure intelligence to automated incident response – Hackread – Cybersecurity News, Data Breaches, AI, and More

Torrance, United States / California, 19th December 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The Asset Layer of the Web: Tokenization Is Becoming Finance’s New Backend Infrastructure – Hackread – Cybersecurity News, Data Breaches, AI, and More
Crypto’s public image lagged reality. Stablecoins, tokenization, and regulation now power a blockchain backend settling global finance at institutional scale. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Docker Fixes ‘Ask Gordon’ AI Flaw That Enabled Metadata-Based Attacks – Hackread – Cybersecurity News, Data Breaches, AI, and More

Pillar Security has identified a critical indirect prompt injection vulnerability in Docker’s ‘Ask Gordon’ assistant. By poisoning metadata on Docker Hub, attackers could bypass security to exfiltrate private build logs and chat history. Discover how the “lethal trifecta” enabled this attack and why updating to Docker Desktop 4.50.0 is essential for developer security. – Read … Read More “Docker Fixes ‘Ask Gordon’ AI Flaw That Enabled Metadata-Based Attacks – Hackread – Cybersecurity News, Data Breaches, AI, and More” »
WatchGuard has released fixes to address a critical security flaw in Fireware OS that it said has been exploited in real-world attacks. Tracked as CVE-2025-14733 (CVSS score: 9.3), the vulnerability has been described as a case of out-of-bounds write affecting the iked process that could allow a remote unauthenticated attacker to execute arbitrary code. “This … Read More “WatchGuard Warns of Active Exploitation of Critical Fireware OS VPN Vulnerability – The Hacker News” »
Authorities in Nigeria have announced the arrest of three “high-profile internet fraud suspects” who are alleged to have been involved in phishing attacks targeting major corporations, including the main developer behind the RaccoonO365 phishing-as-a-service (PhaaS) scheme. The Nigeria Police Force National Cybercrime Centre (NPF–NCCC) said investigations conducted in collaboration with – Read More – The … Read More “Nigeria Arrests RaccoonO365 Phishing Developer Linked to Microsoft 365 Attacks – The Hacker News” »
New UEFI Flaw Enables Early-Boot DMA Attacks on ASRock, ASUS, GIGABYTE, MSI Motherboards – The Hacker News

Certain motherboard models from vendors like ASRock, ASUSTeK Computer, GIGABYTE, and MSI are affected by a security vulnerability that leaves them susceptible to early-boot direct memory access (DMA) attacks across architectures that implement a Unified Extensible Firmware Interface (UEFI) and input–output memory management unit (IOMMU). UEFI and IOMMU are designed to enforce a security – … Read More “New UEFI Flaw Enables Early-Boot DMA Attacks on ASRock, ASUS, GIGABYTE, MSI Motherboards – The Hacker News” »
Policymakers and companies are reckoning with increased reports over the past few months showing AI tools being leveraged to conduct cyber attacks on a larger and faster scale. Most notably, Anthropic reported last month that Chinese hackers had jailbroken and tricked its AI model Claude into assisting with a cyberespionage hacking campaign that ultimately targeted … Read More “Policymakers grapple with fallout from Chinese AI-enabled hack – CyberScoop” »
Cisco customers are confronting a fresh wave of attacks from a Chinese threat group that has actively exploited a critical zero-day vulnerability affecting the vendor’s software for email and web security since at least late November, the company said in an advisory Wednesday. Cisco said it became aware of the attacks Dec. 10. The defect … Read More “Cisco customers hit by fresh wave of zero-day attacks from China-linked APT – CyberScoop” »
INE Security Expands Across Middle East and Asia to Accelerate Cybersecurity Upskilling – Hackread – Cybersecurity News, Data Breaches, AI, and More

Cary, North Carolina, USA, 18th December 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Lazarus Group Embed New BeaverTail Variant in Developer Tools – Hackread – Cybersecurity News, Data Breaches, AI, and More

North Korea’s Lazarus Group deploys a new BeaverTail variant to steal credentials and crypto using fake job lures, dev tools, and smart contracts. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Iranian APT ‘Prince of Persia’ Resurfaces With New Tools and Targets – Hackread – Cybersecurity News, Data Breaches, AI, and More

SafeBreach reports the resurgence of the Iranian APT group Prince of Persia (Infy). Discover how these state-sponsored hackers are now using Telegram bots and Thunder and Lightning malware to target victims globally across Europe, India, and Canada. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A previously undocumented China-aligned threat cluster dubbed LongNosedGoblin has been attributed to a series of cyber attacks targeting governmental entities in Southeast Asia and Japan. The end goal of these attacks is cyber espionage, Slovak cybersecurity company ESET said in a report published today. The threat activity cluster has been assessed to be active since … Read More “China-Aligned Threat Group Uses Windows Group Policy to Deploy Espionage Malware – The Hacker News” »
Senate Intel chair urges national cyber director to safeguard against open-source software threats – CyberScoop

Senate Intelligence Committee Chairman Tom Cotton is raising the spectre of foreign adversaries playing too heavy a role in open-source software, and asking the national cyber director to counter the risks. The Oklahoma Republican wrote to National Cyber Director Sean Cairncross Thursday, saying he was concerned about reports that “state-sponsored software developers and cyber espionage … Read More “Senate Intel chair urges national cyber director to safeguard against open-source software threats – CyberScoop” »
The U.S. Sentencing Commission is issuing preliminary sentencing guidelines for criminal offenses under the Take It Down Act, a law passed earlier this year to curb the spread of nonconsensual deepfake pornography. The Take It Down Act marks one of the first major pieces of legislation passed by Congress to address AI-generated deepfakes, attracting broad … Read More “U.S. Sentencing Commission seeks input on criminal penalties for deepfakes – CyberScoop” »
Hewlett Packard Enterprise (HPE) has resolved a maximum-severity security flaw in OneView Software that, if successfully exploited, could result in remote code execution. The critical vulnerability, assigned the CVE identifier CVE-2025-37164, carries a CVSS score of 10.0. HPE OneView is an IT infrastructure management software that streamlines IT operations and controls all systems via a … Read More “HPE OneView Flaw Rated CVSS 10.0 Allows Unauthenticated Remote Code Execution – The Hacker News” »
Why Organizations Need to Modify Their Cybersecurity Strategy for 2026 – Hackread – Cybersecurity News, Data Breaches, AI, and More

Cybersecurity planning continues to advance as organisations integrate new software, cloud platforms, and digital tools into nearly every… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
ThreatsDay Bulletin: WhatsApp Hijacks, MCP Leaks, AI Recon, React2Shell Exploit and 15 More Stories – The Hacker News

This week’s ThreatsDay Bulletin tracks how attackers keep reshaping old tools and finding new angles in familiar systems. Small changes in tactics are stacking up fast, and each one hints at where the next big breach could come from. From shifting infrastructures to clever social hooks, the week’s activity shows just how fluid the threat … Read More “ThreatsDay Bulletin: WhatsApp Hijacks, MCP Leaks, AI Recon, React2Shell Exploit and 15 More Stories – The Hacker News” »
Within the past year, artificial intelligence copilots and agents have quietly permeated the SaaS applications businesses use every day. Tools like Zoom, Slack, Microsoft 365, Salesforce, and ServiceNow now come with built-in AI assistants or agent-like features. Virtually every major SaaS vendor has rushed to embed AI into their offerings. The result is an explosion … Read More “The Case for Dynamic AI-SaaS Security as Copilots Scale – The Hacker News” »
North Korea-Linked Hackers Steal $2.02 Billion in 2025, Leading Global Crypto Theft – The Hacker News

Threat actors with ties to the Democratic People’s Republic of Korea (DPRK or North Korea) have been instrumental in driving a surge in global cryptocurrency theft in 2025, accounting for at least $2.02 billion out of more than $3.4 billion stolen from January through early December. The figure represents a 51% increase year-over-year and $681 … Read More “North Korea-Linked Hackers Steal $2.02 Billion in 2025, Leading Global Crypto Theft – The Hacker News” »
FBI Seizes Crypto Laundering Hub E-Note Linked to Russian Admin – Hackread – Cybersecurity News, Data Breaches, AI, and More
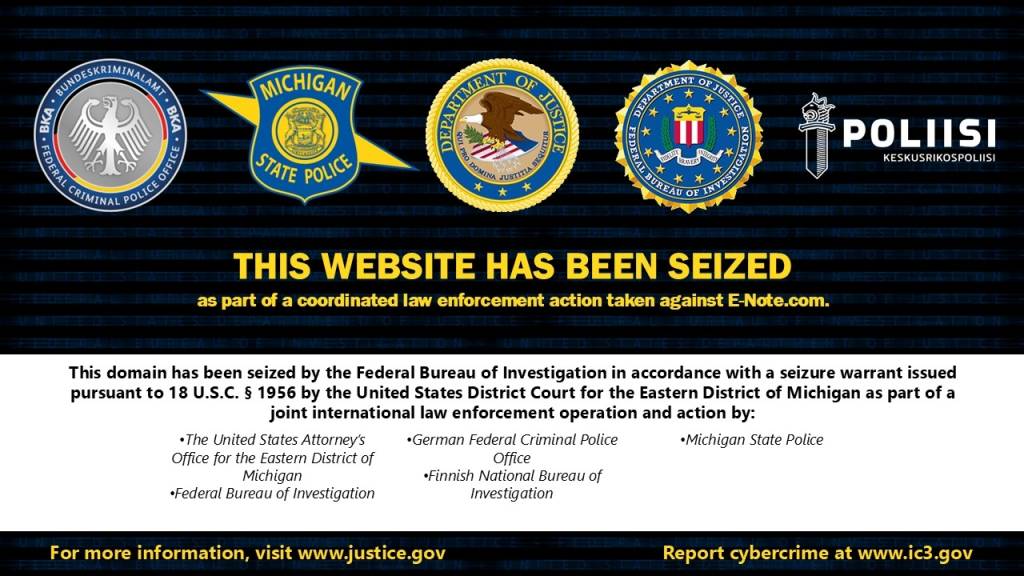
The FBI and international police have shut down E-Note, a cryptocurrency exchange that laundered over $70 million for cybercriminals. Read about the indictment of a Russian and how the global task force ended his decade-long operation. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The North Korean threat actor known as Kimsuky has been linked to a new campaign that distributes a new variant of Android malware called DocSwap via QR codes hosted on phishing sites mimicking Seoul-based logistics firm CJ Logistics (formerly CJ Korea Express). “The threat actor leveraged QR codes and notification pop-ups to lure victims into … Read More “Kimsuky Spreads DocSwap Android Malware via QR Phishing Posing as Delivery App – The Hacker News” »