The Federal Communications Commission finalized new financial penalties for telecoms that submit false, inaccurate or late reporting to a federal robocalling system. The new regulations, which go into effect Feb. 5, will require providers to recertify every year that their information is accurate in the Robocall Mitigation Database (RMD). It would also impose fines on … Read More “FCC finalizes new penalties for robocall violators – CyberScoop” »
Category: Attack Feeds
Bitfinex Hack Mastermind Behind $10 Billion Theft Gets Early Release – Hackread – Cybersecurity News, Data Breaches, AI, and More

Ilya Lichtenstein, the man behind the massive 2016 Bitfinex Bitcoin theft, has been released early from prison. Read how the First Step Act and a trail of Walmart gift cards led to this major update in one of the world’s largest crypto thefts. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and … Read More “Bitfinex Hack Mastermind Behind $10 Billion Theft Gets Early Release – Hackread – Cybersecurity News, Data Breaches, AI, and More” »
The CERT Coordination Center (CERT/CC) has disclosed details of an unpatched security flaw impacting TOTOLINK EX200 wireless range extender that could allow a remote authenticated attacker to gain full control of the device. The flaw, CVE-2025-65606 (CVSS score: N/A), has been characterized as a flaw in the firmware-upload error-handling logic, which could cause the device … Read More “Unpatched Firmware Flaw Exposes TOTOLINK EX200 to Full Remote Device Takeover – The Hacker News” »
Two Chrome Extensions Caught Stealing ChatGPT and DeepSeek Chats from 900,000 Users – The Hacker News
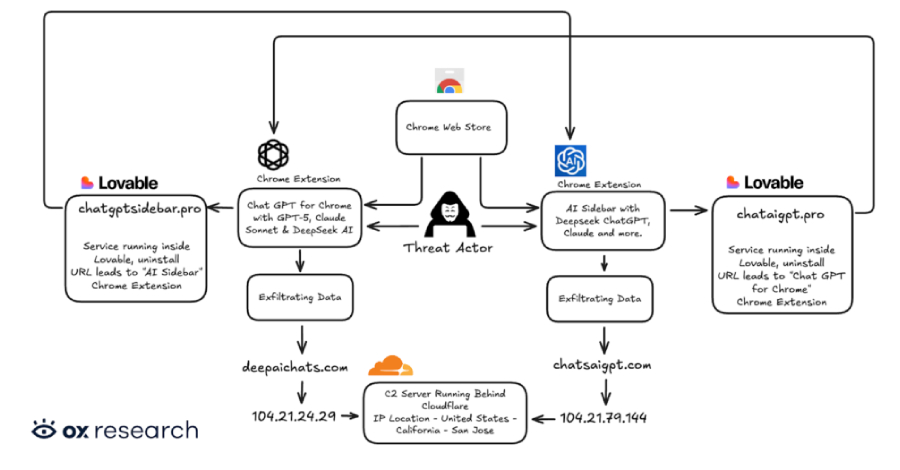
Cybersecurity researchers have discovered two new malicious extensions on the Chrome Web Store that are designed to exfiltrate OpenAI ChatGPT and DeepSeek conversations alongside browsing data to servers under the attackers’ control. The names of the extensions, which collectively have over 900,000 users, are below – Chat GPT for Chrome with GPT-5, Claude Sonnet & … Read More “Two Chrome Extensions Caught Stealing ChatGPT and DeepSeek Chats from 900,000 Users – The Hacker News” »
Ledger Confirms Global-e Breach, Warns Users of Phishing Attempts – Hackread – Cybersecurity News, Data Breaches, AI, and More
Ledger confirms data breach via Global-e partner. Customer info exposed, phishing attacks active. No passwords or crypto recovery phrases leaked. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The CERT Coordination Center (CERT/CC) has disclosed details of an unpatched security flaw impacting TOTOLINK EX200 wireless range extender that could allow a remote authenticated attacker to gain full control of the device. The flaw, CVE-2025-65606 (CVSS score: N/A), has been characterized as a flaw in the firmware-upload error-handling logic, which could cause the device … Read More “Unpatched Firmware Flaw Exposes TOTOLINK EX200 to Full Remote Device Takeover – The Hacker News” »
VS Code Forks Recommend Missing Extensions, Creating Supply Chain Risk in Open VSX – The Hacker News
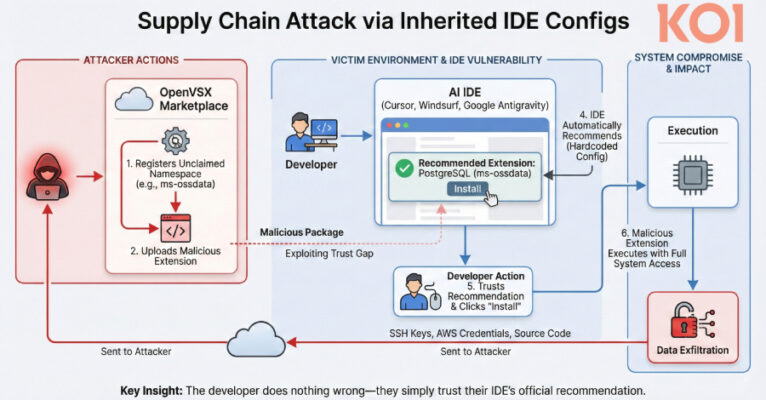
Popular artificial intelligence (AI)-powered Microsoft Visual Studio Code (VS Code) forks such as Cursor, Windsurf, Google Antigravity, and Trae have been found to recommend extensions that are non-existent in the Open VSX registry, potentially opening the door to supply chain risks when bad actors publish malicious packages under those names. The problem, according to Koi, … Read More “VS Code Forks Recommend Missing Extensions, Creating Supply Chain Risk in Open VSX – The Hacker News” »
Source: Securonix Cybersecurity researchers have disclosed details of a new campaign dubbed PHALT#BLYX that has leveraged ClickFix-style lures to display fixes for fake blue screen of death (BSoD) errors in attacks targeting the European hospitality sector. The end goal of the multi-stage campaign is to deliver a remote access trojan known as DCRat, according to … Read More “Fake Booking Emails Redirect Hotel Staff to Fake BSoD Pages Delivering DCRat – The Hacker News” »
How to Avoid Phishing Incidents in 2026: A CISO Guide – Hackread – Cybersecurity News, Data Breaches, AI, and More

Phishing in 2026 is harder to detect and verify. Learn how CISOs can speed up investigations, reduce noise, and respond with confidence. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The Invisible Half of the Identity Universe Identity used to live in one place – an LDAP directory, an HR system, a single IAM portal. Not anymore. Today, identity is fragmented across SaaS, on-prem, IaaS, PaaS, home-grown, and shadow applications. Each of these environments carries its own accounts, permissions, and authentication flows. Traditional IAM and … Read More “What is Identity Dark Matter? – The Hacker News” »
For too long, fraud – an illicit economy rivaling the GDP of G20 nations – has been seen as a cost of doing business, a nuisance to be absorbed by banks and consumers. That perception is a dangerous relic. Modern fraud blends geopolitics with advanced technical tactics, carried out through criminal proxies to target businesses … Read More “Why governments need to treat fraud like cyberwarfare, not customer service – CyberScoop” »
The Invisible Half of the Identity Universe Identity used to live in one place – an LDAP directory, an HR system, a single IAM portal. Not anymore. Today, identity is fragmented across SaaS, on-prem, IaaS, PaaS, home-grown, and shadow applications. Each of these environments carries its own accounts, permissions, and authentication flows. Traditional IAM and … Read More “What is Identity Dark Matter? – The Hacker News” »
New VVS Stealer Malware Targets Discord Users via Fake System Errors – Hackread – Cybersecurity News, Data Breaches, AI, and More

Palo Alto Networks’ new report reveals VVS Stealer uses Discord Injection and fake error messages to steal tokens and MFA codes. Protect your account from this new Python-based threat. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Police in India have arrested a former Coinbase customer service agent who is believed to have been bribed by cybercriminal gangs to access sensitive customer information. Read more in my article on the Hot for Security blog. – Read More – Graham Cluley
Connex IT Partners with AccuKnox for Zero Trust CNAPP Security in Southeast Asia – Hackread – Cybersecurity News, Data Breaches, AI, and More

Menlo Park, India, 6th January 2026, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Critical AdonisJS Bodyparser Flaw (CVSS 9.2) Enables Arbitrary File Write on Servers – The Hacker News

Users of the “@adonisjs/bodyparser” npm package are being advised to update to the latest version following the disclosure of a critical security vulnerability that, if successfully exploited, could allow a remote attacker to write arbitrary files on the server. Tracked as CVE-2026-21440 (CVSS score: 9.2), the flaw has been described as a path traversal issue … Read More “Critical AdonisJS Bodyparser Flaw (CVSS 9.2) Enables Arbitrary File Write on Servers – The Hacker News” »
A new critical security vulnerability has been disclosed in n8n, an open-source workflow automation platform, that could enable an authenticated attacker to execute arbitrary system commands on the underlying host. The vulnerability, tracked as CVE-2025-68668, is rated 9.9 on the CVSS scoring system. It has been described as a case of a protection mechanism failure. … Read More “New n8n Vulnerability (9.9 CVSS) Lets Authenticated Users Execute System Commands – The Hacker News” »
The surprise raid by U.S. armed forces and law enforcement agencies in Caracas, Venezuela had observers around the world scouring social media and news for updates on an operation that saw Venezuelan president Nicholas Maduro and his wife captured and flown to the United States to face criminal charges. The Trump administration initially offered few … Read More “AI, voting machine conspiracies fill information vacuum around Venezuela operation – CyberScoop” »
Researchers Warn of Data Exposure Risks in Claude Chrome Extension – Hackread – Cybersecurity News, Data Breaches, AI, and More
Security experts at Zenity Labs warn that Anthropic’s new agentic browser extension, Claude in Chrome, could bypass traditional web security, exposing private data and login tokens to potential hijackers. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A hacker who pleaded guilty to conspiring to launder billions of dollars worth of bitcoin stolen in the 2016 Bitfinex hack has been released from prison, a little more than one year after being sentenced to a five-year stint. Ilya Lichtenstein posted on X that his early release came as a result of a bipartisan … Read More “Convicted Bitfinex bitcoin launderer freed from prison, thanks Trump law – CyberScoop” »
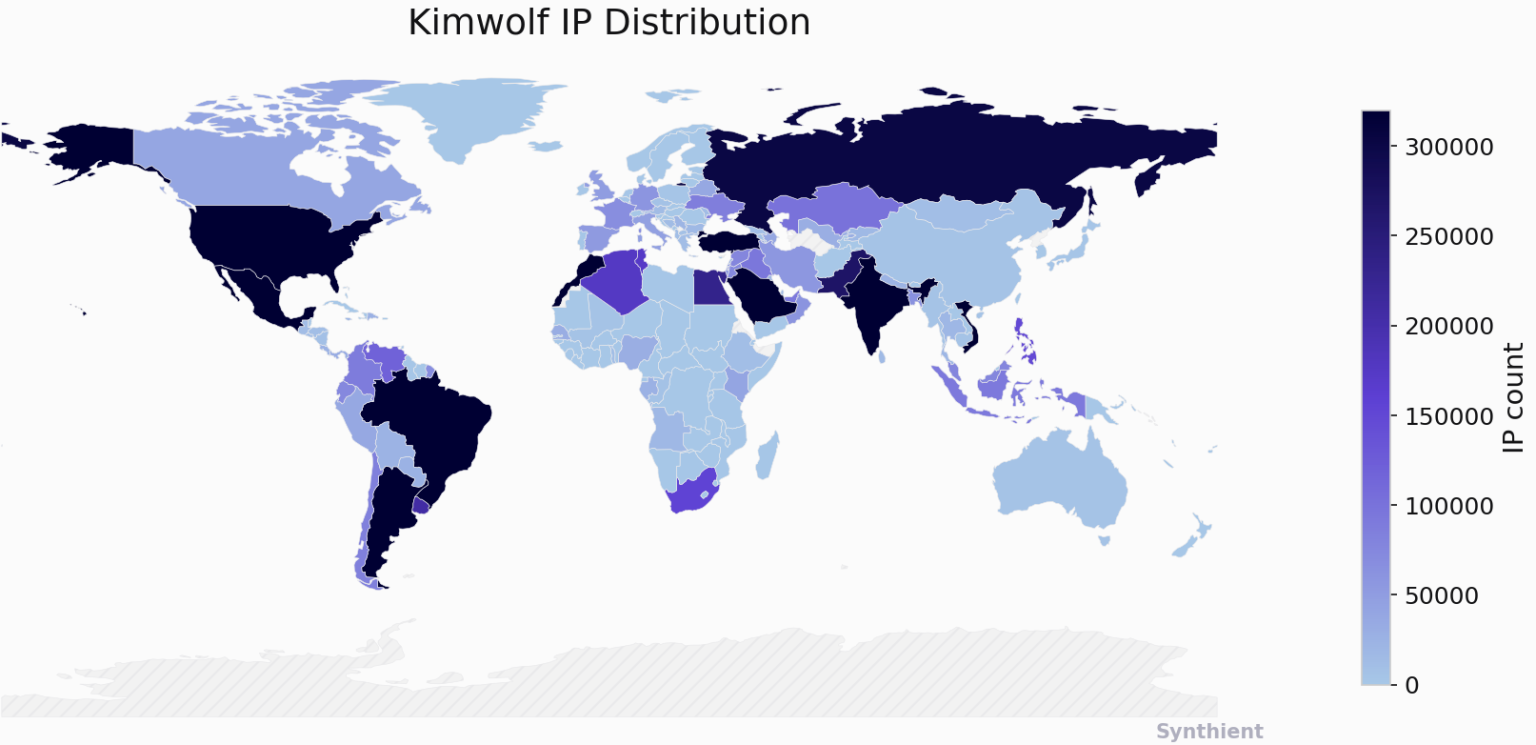
Kimwolf Android Botnet Infects Over 2 Million Devices via Exposed ADB and Proxy Networks – The Hacker News

The botnet known as Kimwolf has infected more than 2 million Android devices by tunneling through residential proxy networks, according to findings from Synthient. “Key actors involved in the Kimwolf botnet are observed monetizing the botnet through app installs, selling residential proxy bandwidth, and selling its DDoS functionality,” the company said in an analysis published … Read More “Kimwolf Android Botnet Infects Over 2 Million Devices via Exposed ADB and Proxy Networks – The Hacker News” »
The Russia-aligned threat actor known as UAC-0184 has been observed targeting Ukrainian military and government entities by leveraging the Viber messaging platform to deliver malicious ZIP archives. “This organization has continued to conduct high-intensity intelligence gathering activities against Ukrainian military and government departments in 2025,” the 360 Threat Intelligence Center said in – Read More … Read More “Russia-Aligned Hackers Abuse Viber to Target Ukrainian Military and Government – The Hacker News” »
NordVPN Denies Breach After Hacker Claims Access to Salesforce Dev Data – Hackread – Cybersecurity News, Data Breaches, AI, and More

A hacker using the alias 1011 has claimed to breach a NordVPN development server, posting what appears to… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The year opened without a reset. The same pressure carried over, and in some places it tightened. Systems people assume are boring or stable are showing up in the wrong places. Attacks moved quietly, reused familiar paths, and kept working longer than anyone wants to admit. This week’s stories share one pattern. Nothing flashy. No … Read More “⚡ Weekly Recap: IoT Exploits, Wallet Breaches, Rogue Extensions, AI Abuse & More – The Hacker News” »
Modern enterprises depend on AI data pipelines for analytics and automated decision-making. As these pipelines become more integrated… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Featuring: Cybersecurity is being reshaped by forces that extend beyond individual threats or tools. As organizations operate across cloud infrastructure, distributed endpoints, and complex supply chains, security has shifted from a collection of point solutions to a question of architecture, trust, and execution speed. This report examines how core areas of cybersecurity are evolving in … Read More “The State of Cybersecurity in 2025: Key Segments, Insights, and Innovations – The Hacker News” »
Disney Fined $10M for Violating Children’s Privacy Laws on YouTube – Hackread – Cybersecurity News, Data Breaches, AI, and More

Disney agrees to a $10M settlement with the DOJ and FTC over YouTube privacy violations. Learn how the COPPA ruling affects kids’ data and Disney’s new rules. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
China’s campaign to break into our critical infrastructure and federal government networks is persistent and growing. Beijing is stealing information while also planting tools and maintaining access in key systems, giving it the option to pressure the United States in the future. Russia also continues to test our critical infrastructure with increasingly sophisticated operations, support … Read More “Time to restore America’s cyberspace security system – CyberScoop” »
Ilya Lichtenstein, who was sentenced to prison last year for money laundering charges in connection with his role in the massive hack of cryptocurrency exchange Bitfinex in 2016, said he has been released early. In a post shared on X last week, the 38-year-old announced his release, crediting U.S. President Donald Trump’s First Step Act. … Read More “Bitfinex Hack Convict Ilya Lichtenstein Released Early Under U.S. First Step Act – The Hacker News” »
Cybersecurity researchers have disclosed details of a new Python-based information stealer called VVS Stealer (also styled as VVS $tealer) that’s capable of harvesting Discord credentials and tokens. The stealer is said to have been on sale on Telegram as far back as April 2025, according to a report from Palo Alto Networks Unit 42. “VVS … Read More “New VVS Stealer Malware Targets Discord Accounts via Obfuscated Python Code – The Hacker News” »
Researcher Wipes White Supremacist Dating Sites, Leaks Data on okstupid.lol – Hackread – Cybersecurity News, Data Breaches, AI, and More
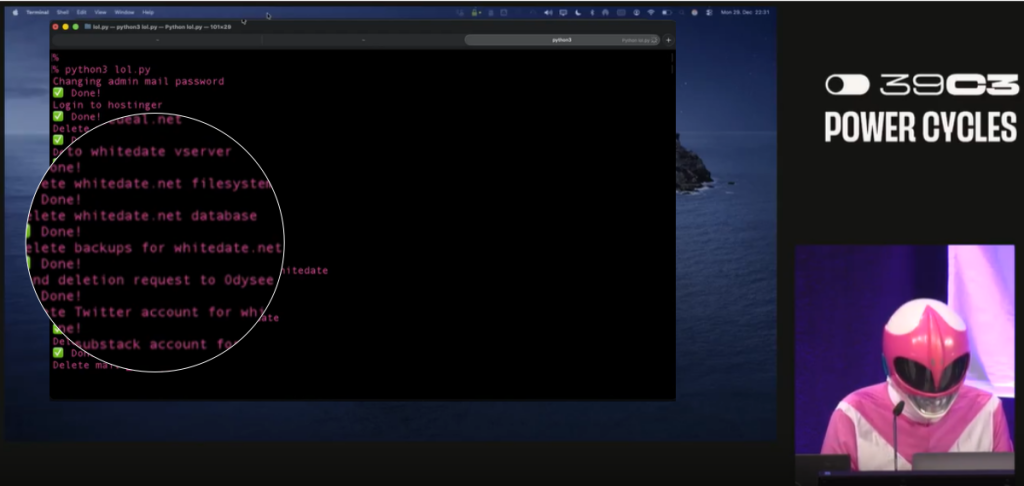
Security researcher in “Martha Root” in Pink Power Ranger deletes white supremacist dating sites live onstage, leaks 8,000 profiles and 100GB of data at Chaos Communication Congress (CCC) 2025. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Finnish Authorities Detain Crew After Undersea Internet Cable Severed – Hackread – Cybersecurity News, Data Breaches, AI, and More

After a sudden internet cable break between Finland and Estonia, authorities have seized the cargo ship Fitburg. With two crew members arrested and sanctioned steel found on board, investigators are now probing if this was an accident or a deliberate act of hybrid warfare. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, … Read More “Finnish Authorities Detain Crew After Undersea Internet Cable Severed – Hackread – Cybersecurity News, Data Breaches, AI, and More” »
Resecurity Says ShinyHunters Fell for Honeypot After Breach Claim – Hackread – Cybersecurity News, Data Breaches, AI, and More

Resecurity denies breach claims by ShinyHunters, says attackers accessed a honeypot with fake data. No real systems or customer info were compromised. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
ShinyHunters Claim Breach of US Cybersecurity Firm Resecurity – Hackread – Cybersecurity News, Data Breaches, AI, and More

The hacking group ShinyHunters has claimed responsibility for breaching Resecurity, a US-based cybersecurity company headquartered in Los Angeles.… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
RondoDox Botnet is Using React2Shell to Hijack Thousands of Unpatched Devices – Hackread – Cybersecurity News, Data Breaches, AI, and More
RondoDox hackers exploit the React2Shell flaw in Next.js to target 90,000+ devices, including routers, smart cameras, and small business websites. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Protecting Your Digital Wallet: What You Need to Know About Fintech Security – Hackread – Cybersecurity News, Data Breaches, AI, and More

The world of finance has undergone a remarkable transformation with the rise of digital wallets and financial technology… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Tokyo FM Data Breach: Hacker Claims Over 3 Million Records Stolen – Hackread – Cybersecurity News, Data Breaches, AI, and More
Tokyo FM is investigating claims of a massive data breach involving 3 million records. Learn what information was allegedly taken and how you can stay safe. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The Trump administration this week removed three Iranians from its sanctions list who were previously accused of working for Intellexa, the consortium behind the Predator spyware that recent investigations say has circumvented human rights safeguards. The Biden administration imposed sanctions against the trio in 2024 as part of a broader move to sanction spyware operators. … Read More “Treasury removes Intellexa spyware-linked trio from sanctions list – CyberScoop” »
The threat actor known as Transparent Tribe has been attributed to a fresh set of attacks targeting Indian governmental, academic, and strategic entities with a remote access trojan (RAT) that grants them persistent control over compromised hosts. “The campaign employs deceptive delivery techniques, including a weaponized Windows shortcut (LNK) file masquerading as a legitimate PDF … Read More “Transparent Tribe Launches New RAT Attacks Against Indian Government and Academia – The Hacker News” »
The story you are reading is a series of scoops nestled inside a far more urgent Internet-wide security advisory. The vulnerability at issue has been exploited for months already, and it’s time for a broader awareness of the threat. The short version is that everything you thought you knew about the security of the internal … Read More “The Kimwolf Botnet is Stalking Your Local Network – Krebs on Security” »
Attack Surface Management (ASM) tools promise reduced risk. What they usually deliver is more information. Security teams deploy ASM, asset inventories grow, alerts start flowing, and dashboards fill up. There is visible activity and measurable output. But when leadership asks a simple question, “Is this reducing incidents?” the answer is often unclear. This gap between … Read More “The ROI Problem in Attack Surface Management – The Hacker News” »
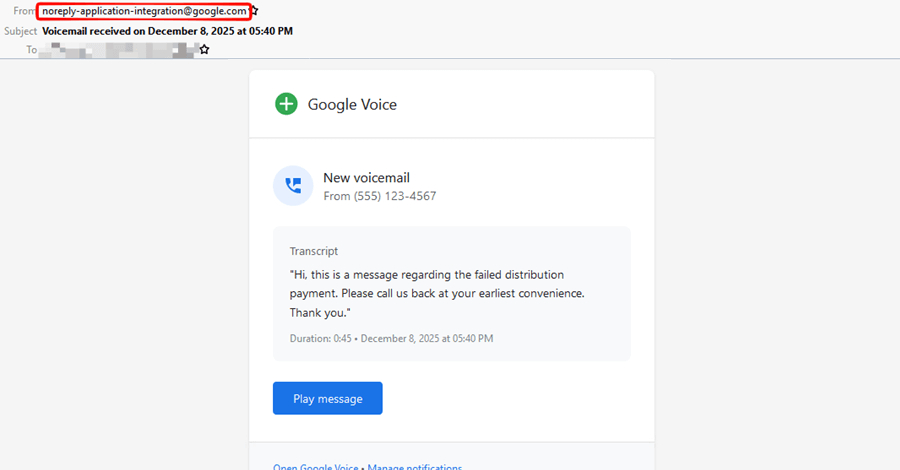
Cybersecurity researchers have disclosed details of a phishing campaign that involves the attackers impersonating legitimate Google-generated messages by abusing Google Cloud’s Application Integration service to distribute emails. The activity, Check Point said, takes advantage of the trust associated with Google Cloud infrastructure to send the messages from a legitimate email address (” – Read More … Read More “Cybercriminals Abuse Google Cloud Email Feature in Multi-Stage Phishing Campaign – The Hacker News” »
How Webflow Helps Companies Move Faster Without Sacrificing Brand Control – Hackread – Cybersecurity News, Data Breaches, AI, and More

Conventional development frequently results in a trade-off between speed and brand consistency, which harms reputation by causing delays… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
As web browsers evolve into all-purpose platforms, performance and productivity often suffer. Feature overload, excessive background processes, and fragmented workflows can slow down browsing sessions and introduce unnecessary friction, especially for users who rely on the browser as a primary work environment. This article explores how adopting a lightweight, task-focused browser, like – Read More … Read More “How To Browse Faster and Get More Done Using Adapt Browser – The Hacker News” »
ThreatsDay Bulletin: GhostAd Drain, macOS Attacks, Proxy Botnets, Cloud Exploits, and 12+ Stories – The Hacker News

The first ThreatsDay Bulletin of 2026 lands on a day that already feels symbolic — new year, new breaches, new tricks. If the past twelve months taught defenders anything, it’s that threat actors don’t pause for holidays or resolutions. They just evolve faster. This week’s round-up shows how subtle shifts in behavior, from code tweaks … Read More “ThreatsDay Bulletin: GhostAd Drain, macOS Attacks, Proxy Botnets, Cloud Exploits, and 12+ Stories – The Hacker News” »
RondoDox Botnet Exploits Critical React2Shell Flaw to Hijack IoT Devices and Web Servers – The Hacker News

Cybersecurity researchers have disclosed details of a persistent nine-month-long campaign that has targeted Internet of Things (IoT) devices and web applications to enroll them into a botnet known as RondoDox. As of December 2025, the activity has been observed leveraging the recently disclosed React2Shell (CVE-2025-55182, CVSS score: 10.0) flaw as an initial access vector, CloudSEK … Read More “RondoDox Botnet Exploits Critical React2Shell Flaw to Hijack IoT Devices and Web Servers – The Hacker News” »
Mobile fraud on the rise in South Africa – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.

As South Africans take advantage of the ease and convenience of the digital financial world, it has become increasingly more simple for threat actors to take advantage. Deceiving the average individual has become rather simple for cybercriminals as the internet brings them a wealth of information. All it takes is one or two rather official … Read More “Mobile fraud on the rise in South Africa – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.” »
Hacker Claims European Space Agency Breach, Selling 200GB of Data – Hackread – Cybersecurity News, Data Breaches, AI, and More

A hacker using the alias 888 is claiming responsibility for a major data breach affecting the European Space… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Trust Wallet Chrome Extension Hack Drains $8.5M via Shai-Hulud Supply Chain Attack – The Hacker News

Trust Wallet on Tuesday revealed that the second iteration of the Shai-Hulud (aka Sha1-Hulud) supply chain outbreak in November 2025 was likely responsible for the hack of its Google Chrome extension, ultimately resulting in the theft of approximately $8.5 million in assets. “Our Developer GitHub secrets were exposed in the attack, which gave the attacker … Read More “Trust Wallet Chrome Extension Hack Drains $8.5M via Shai-Hulud Supply Chain Attack – The Hacker News” »
Everest Ransomware Leaks 1TB of Stolen ASUS Data – Hackread – Cybersecurity News, Data Breaches, AI, and More

On December 2, 2025, Hackread.com exclusively reported that the Everest ransomware group claimed to have stolen 1TB of… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More