How Cybercrime Markets Launder Breach Proceeds and What Security Teams Miss – Hackread – Cybersecurity News, Data Breaches, AI, and More

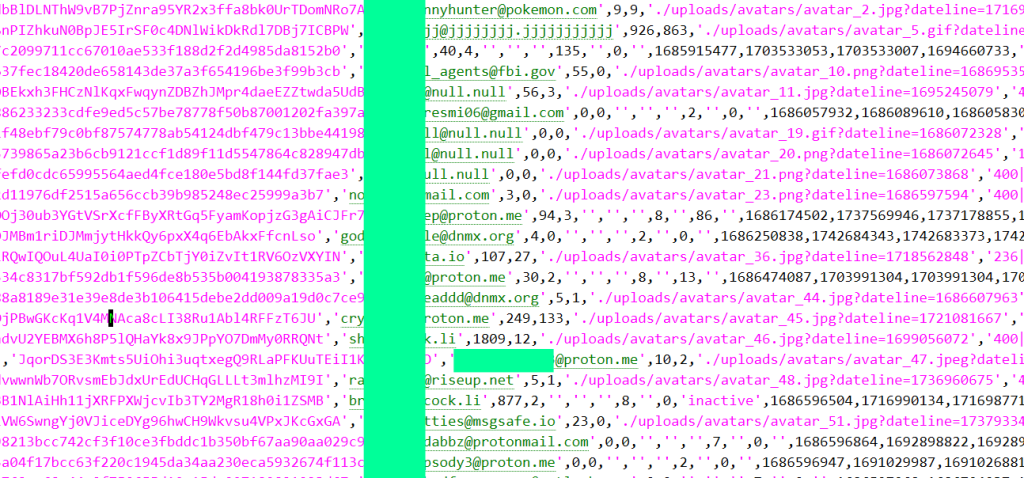
Explore how cybercrime markets turn stolen data into laundered funds using dollar‑pegged assets, mixers and exchanges-and why tracking BTC USDT price and stablecoin flows now matters for security, fraud and AML teams. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More

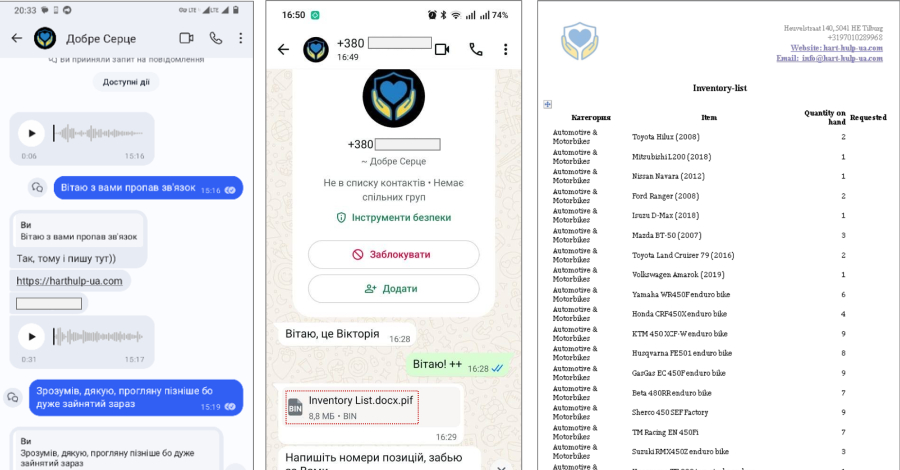












![[Webinar] Securing Agentic AI: From MCPs and Tool Access to Shadow API Key Sprawl – The Hacker News](https://attackfeed.com/wp-content/uploads/2026/01/ai-agent-C3Hsu0.webp)