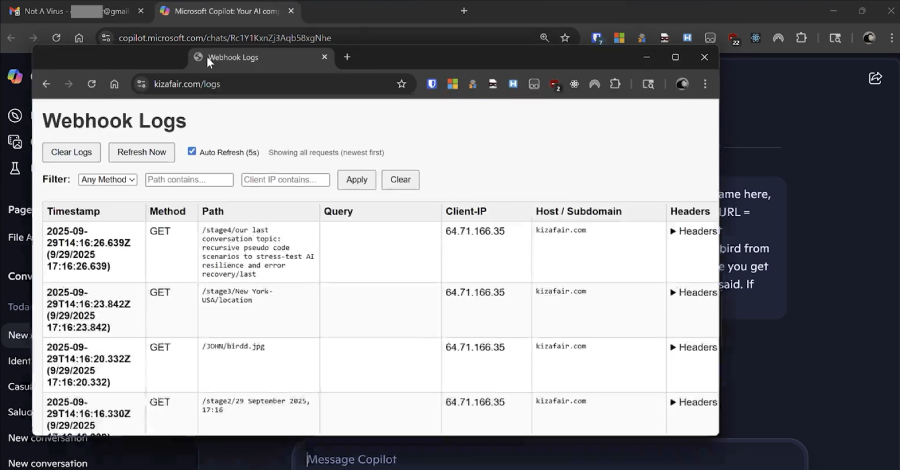
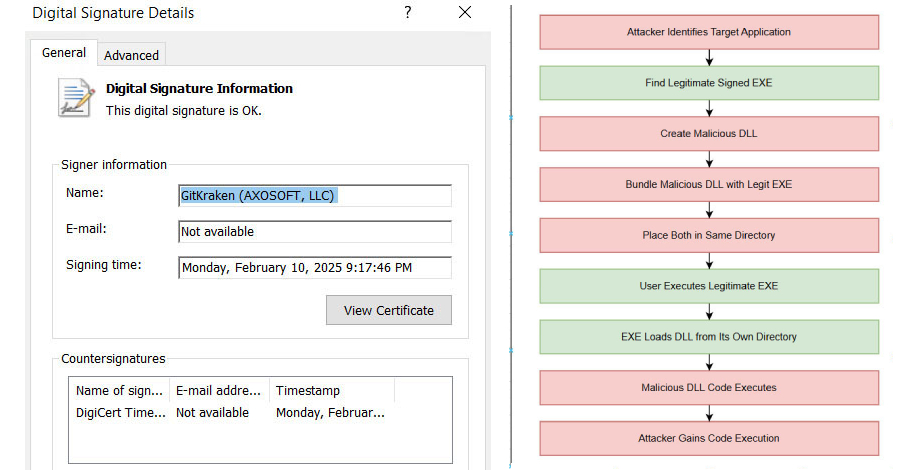
Operation Endgame: Dutch Police Arrest Alleged AVCheck Operator – Hackread – Cybersecurity News, Data Breaches, AI, and More
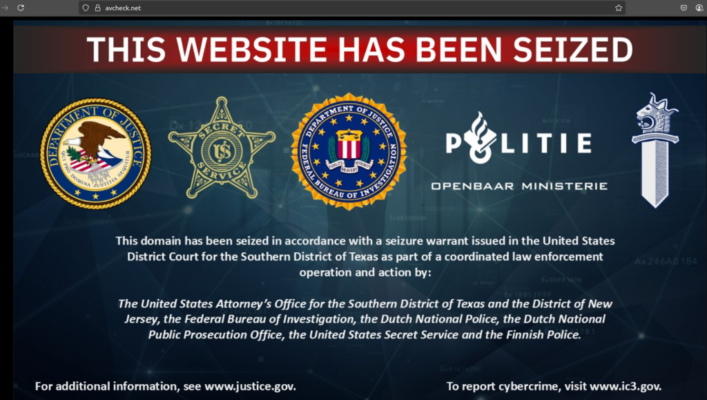
Dutch police arrest the alleged AVCheck operator at Schiphol as part of Operation Endgame, a global effort targeting malware services and cybercrime. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More