VoidLink Linux Malware Framework Built with AI Assistance Reaches 88,000 Lines of Code – The Hacker News
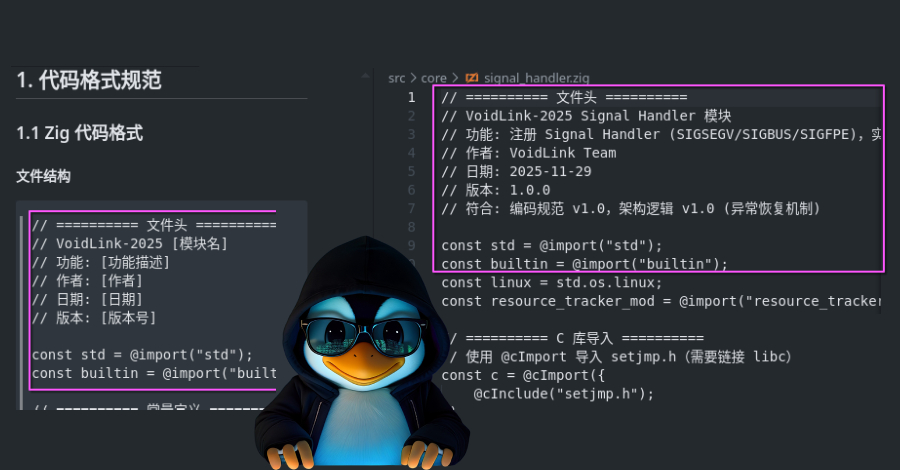
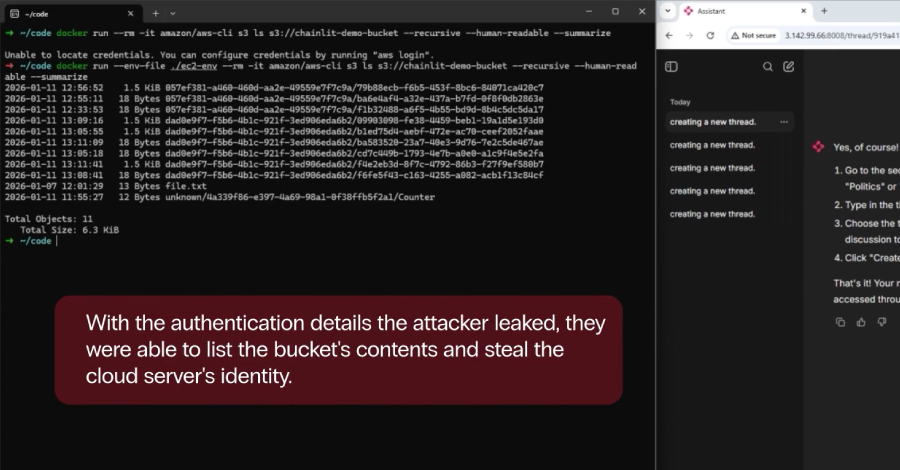
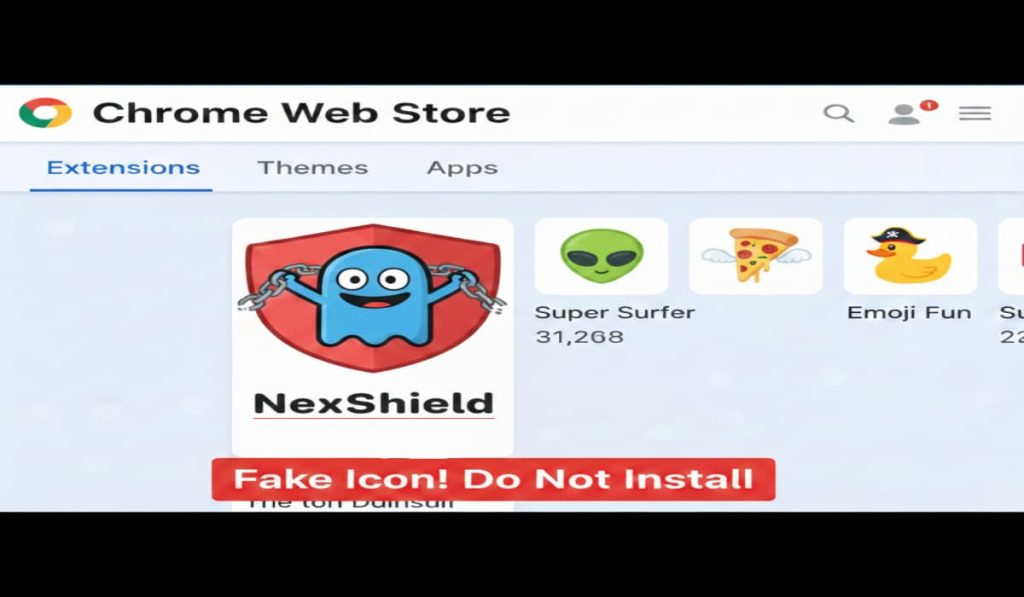
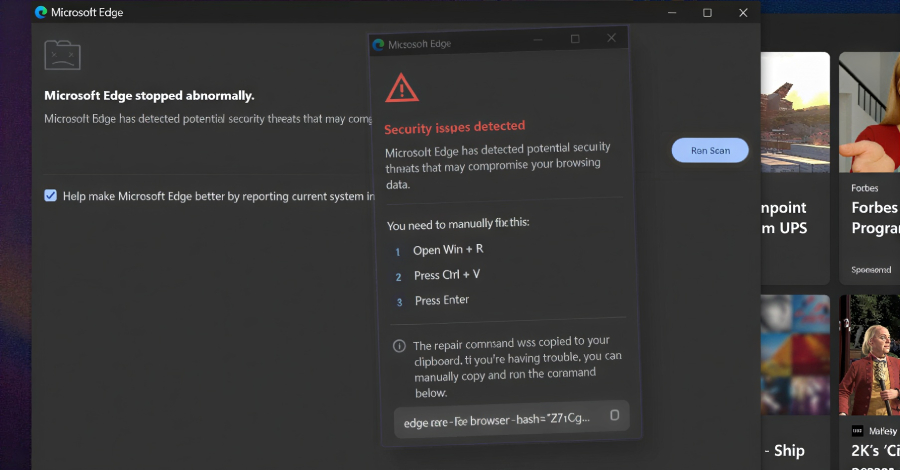
The recently discovered sophisticated Linux malware framework known as VoidLink is assessed to have been developed by a single person with assistance from an artificial intelligence (AI) model. That’s according to new findings from Check Point Research, which identified operational security blunders by malware’s author that provided clues to its developmental origins. The latest insight … Read More “VoidLink Linux Malware Framework Built with AI Assistance Reaches 88,000 Lines of Code – The Hacker News” »