A critical sandbox escape vulnerability has been disclosed in the popular vm2 Node.js library that, if successfully exploited, could allow attackers to run arbitrary code on the underlying operating system. The vulnerability, tracked as CVE-2026-22709, carries a CVSS score of 9.8 out of 10.0 on the CVSS scoring system. “In vm2 for version 3.10.0, Promise.prototype.then … Read More “Critical vm2 Node.js Flaw Allows Sandbox Escape and Arbitrary Code Execution – The Hacker News” »
Author: [email protected] (The Hacker News)
Multiple vulnerabilities have been discovered in SolarWinds Web Help Desk, the most severe of which could allow for arbitrary code execution. SolarWinds Web Help Desk (WHD) is a web-based software that provides IT help desk and asset management functionality, allowing IT teams to manage service requests, track IT assets, and offer self-service options to end-users. … Read More “Multiple Vulnerabilities in SolarWinds Web Help Desk Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
Threat actors with ties to China have been observed using an updated version of a backdoor called COOLCLIENT in cyber espionage attacks in 2025 to facilitate comprehensive data theft from infected endpoints. The activity has been attributed to Mustang Panda (aka Earth Preta, Fireant, HoneyMyte, Polaris, and Twill Typhoon) with the intrusions primarily directed against … Read More “Mustang Panda Deploys Updated COOLCLIENT Backdoor in Government Cyber Attacks – The Hacker News” »
If you work in security operations, the concept of the AI SOC agent is likely familiar. Early narratives promised total autonomy. Vendors seized on the idea of the “Autonomous SOC” and suggested a future where algorithms replaced analysts. That future has not arrived. We have not seen mass layoffs or empty security operations centers. We … Read More “From Triage to Threat Hunts: How AI Accelerates SecOps – The Hacker News” »
Cybersecurity researchers have disclosed two new security flaws in the n8n workflow automation platform, including a crucial vulnerability that could result in remote code execution. The weaknesses, discovered by the JFrog Security Research team, are listed below – CVE-2026-1470 (CVSS score: 9.9) – An eval injection vulnerability that could allow an authenticated user to bypass … Read More “Two High-Severity n8n Flaws Allow Authenticated Remote Code Execution – The Hacker News” »
GoTo Resolve Tool’s Background Activities Compared to Ransomware Tactics – Hackread – Cybersecurity News, Data Breaches, AI, and More

New research from Point Wild’s Lat61 team reveals how the HEURRemoteAdmin.GoToResolve.gen tool allows silent, unattended access to PCs. Learn why this legitimate remote administration software is being flagged as a security risk and its surprising connection to ransomware tactics. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Researchers discover that PureRAT’s code now contains emojis – indicating it has been written by AI based-on comments ripped from social media. – Read More –
Phantom Malware in Android Game Mods Hijacks Devices for Ad Fraud – Hackread – Cybersecurity News, Data Breaches, AI, and More

Another day, another Android malware strain. This time, Phantom malware (aka Android.Phantom) is targeting users who install third-party gaming apps from unofficial sources. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Best IT Managed Services for Large Enterprises – Hackread – Cybersecurity News, Data Breaches, AI, and More

Learn what defines top-tier enterprise managed IT services, why they matter, and how Mindcore Technologies meets large-scale business demands. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Zscaler analysts found critical vulnerabilities in 100% of enterprise AI systems, with 90% compromised in under 90 minutes – Read More –
A recent Forbes investigation revealed that Microsoft has allegedly been handing over Bitlocker encryption recovery keys to law enforcement when served with warrants. Microsoft says it receives about 20 such requests annually. Taken narrowly, this may appear to be a routine case of lawful compliance. On closer inspection, it raises a consequential question about how … Read More “If you don’t control your keys, you don’t control your data – CyberScoop” »
Chainalysis claims Chinese money launderers now account for 20% of global activity – Read More –
Sonatype warns that open source threats became industrialized with a surge in malicious packages in 2025 – Read More –
Cybersecurity researchers have discovered two malicious packages in the Python Package Index (PyPI) repository that masquerade as spellcheckers but contain functionality to deliver a remote access trojan (RAT). The packages, named spellcheckerpy and spellcheckpy, are no longer available for download, but not before they were collectively downloaded a little over 1,000 times. “Hidden inside the … Read More “Fake Python Spellchecker Packages on PyPI Delivered Hidden Remote Access Trojan – The Hacker News” »
Google on Tuesday revealed that multiple threat actors, including nation-state adversaries and financially motivated groups, are exploiting a now-patched critical security flaw in RARLAB WinRAR to establish initial access and deploy a diverse array of payloads. “Discovered and patched in July 2025, government-backed threat actors linked to Russia and China as well as financially motivated … Read More “Google Warns of Active Exploitation of WinRAR Vulnerability CVE-2025-8088 – The Hacker News” »
When security teams discuss credential-related risk, the focus typically falls on threats such as phishing, malware, or ransomware. These attack methods continue to evolve and rightly command attention. However, one of the most persistent and underestimated risks to organizational security remains far more ordinary. Near-identical password reuse continues to slip past security controls, often – … Read More “Password Reuse in Disguise: An Often-Missed Risky Workaround – The Hacker News” »
If you’ve installed a browser extension to enhance your ChatGPT experience, you might want to think again. Read more in my article on the Hot for Security blog. – Read More – GRAHAM CLULEY
Fortinet has begun releasing security updates to address a critical flaw impacting FortiOS that has come under active exploitation in the wild. The vulnerability, assigned the CVE identifier CVE-2026-24858 (CVSS score: 9.4), has been described as an authentication bypass related to FortiOS single sign-on (SSO). The flaw also affects FortiManager and FortiAnalyzer. The company said … Read More “Fortinet Patches CVE-2026-24858 After Active FortiOS SSO Exploitation Detected – The Hacker News” »
A vulnerability has been discovered in Microsoft Office which could allow for a security feature bypass. Microsoft Office is a suite of applications designed to help with productivity and completing common tasks on a computer. You can create and edit documents containing text and images, work with data in spreadsheets and databases, and create presentations … Read More “A Vulnerability in Microsoft Office Could Allow for Security Feature Bypass – Cyber Security Advisories – MS-ISAC” »
Google Threat Intelligence Group warned that a diverse and growing collection of attackers, including nation-state groups and financially motivated cybercriminals, are exploiting a path-traversal vulnerability affecting WinRAR that was disclosed and patched six months ago. The high-severity vulnerability — CVE-2025-8088 — was exploited in the wild almost two weeks before RARLAB, the vendor behind the … Read More “Cybercriminals and nation-state groups are exploiting a six-month old WinRAR defect – CyberScoop” »
ShinyHunters Target 100+ Firms Using Phone Calls to Bypass SSO Security – Hackread – Cybersecurity News, Data Breaches, AI, and More

ShinyHunters is driving attacks on 100+ organisations, using vishing and fake login pages with allied groups to bypass SSO and steal company data, reports Silent Push. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
16 Fake ChatGPT Extensions Caught Hijacking User Accounts – Hackread – Cybersecurity News, Data Breaches, AI, and More

A coordinated campaign of 16 malicious GPT optimisers has been caught hijacking ChatGPT accounts. These tools steal session tokens to access private chats, Slack, and Google Drive files. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Experts Detect Pakistan-Linked Cyber Campaigns Aimed at Indian Government Entities – The Hacker News
Indian government entities have been targeted in two campaigns undertaken by a threat actor that operates in Pakistan using previously undocumented tradecraft. The campaigns have been codenamed Gopher Strike and Sheet Attack by Zscaler ThreatLabz, which identified them in September 2025. “While these campaigns share some similarities with the Pakistan-linked Advanced Persistent Threat (APT) – … Read More “Experts Detect Pakistan-Linked Cyber Campaigns Aimed at Indian Government Entities – The Hacker News” »
WhatsApp Rolls Out Lockdown-Style Security Mode to Protect Targeted Users From Spyware – The Hacker News
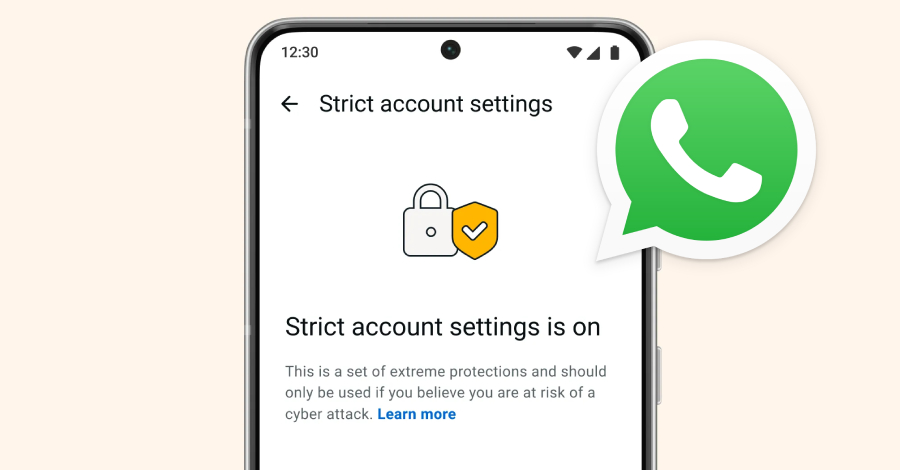
Meta on Tuesday announced it’s adding Strict Account Settings on WhatsApp to secure certain users against advanced cyber attacks because of who they are and what they do. The feature, similar to Lockdown Mode in Apple iOS and Advanced Protection in Android, aims to protect individuals, such as journalists or public-facing figures, from sophisticated spyware … Read More “WhatsApp Rolls Out Lockdown-Style Security Mode to Protect Targeted Users From Spyware – The Hacker News” »
WhatsApp unveiled a lockdown-style feature on Tuesday similar to those offered by other tech providers aimed at blocking sophisticated cyberattacks, with spyware in mind. The “Strict Account Settings” feature will roll out in the coming weeks and once enabled, will allow users to limit features in certain ways, such as blocking attachments and media from … Read More “WhatsApp releases account feature that looks to combat spyware – CyberScoop” »
Critical sandbox escape vulnerability in Grist-Core enables remote code execution via a malicious formula – Read More –
PeckBirdy command-and-control framework targeting gambling, government sectors in Asia since 2023 has been linked to China-aligned APTs – Read More –
ClickFix Attacks Expand Using Fake CAPTCHAs, Microsoft Scripts, and Trusted Web Services – The Hacker News
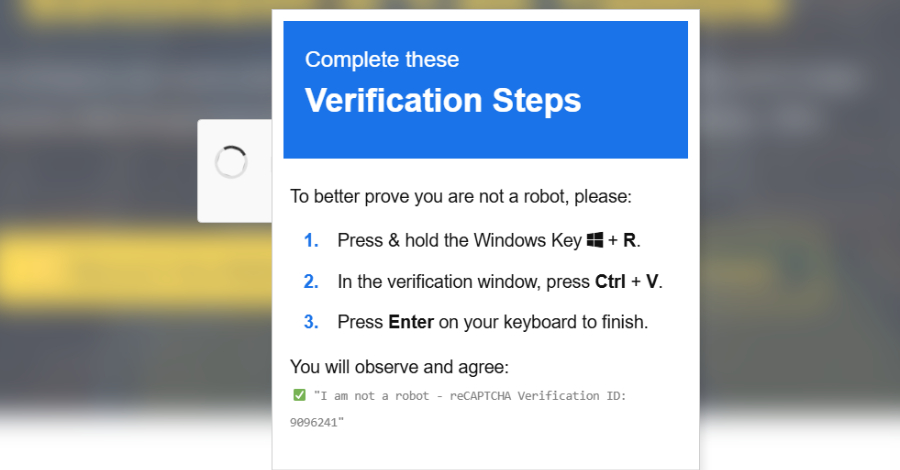
Cybersecurity researchers have disclosed details of a new campaign that combines ClickFix-style fake CAPTCHAs with a signed Microsoft Application Virtualization (App-V) script to distribute an information stealer called Amatera. “Instead of launching PowerShell directly, the attacker uses this script to control how execution begins and to avoid more common, easily recognized execution paths,” – Read … Read More “ClickFix Attacks Expand Using Fake CAPTCHAs, Microsoft Scripts, and Trusted Web Services – The Hacker News” »
LevelBlue, a Dallas-based managed security services provider, announced Tuesday that it is expanding its managed detection and response business through a strategic partnership with cybersecurity firm Fortra that includes the acquisition of Fortra’s Alert Logic managed services unit. The companies said the agreement covers Alert Logic’s Managed Detection and Response services, along with associated Extended … Read More “LevelBlue scoops up Alert Logic’s managed services from Fortra – CyberScoop” »
The AI Fix #85: ChatGPT gets ads, pets get AI therapists, and everyone’s wrong about LLMs – GRAHAM CLULEY

In episode 85 of The AI Fix, Graham discovers that Silicon Valley has the solution to your pet’s mental health crisis, and Mark explains why AI godfather Yann LeCun thinks the entire AI industry is wrong about LLMs. Also in this episode, OpenAI decides to ruin ChatGPT with ads; Sam Altman and Elon Musk and … Read More “The AI Fix #85: ChatGPT gets ads, pets get AI therapists, and everyone’s wrong about LLMs – GRAHAM CLULEY” »
Bugcrowd study reveals 82% of security researchers now use AI, a big increase from 2023 figures – Read More –
Poland Thwarts Russian Wiper Malware Attack on Power Plants – Hackread – Cybersecurity News, Data Breaches, AI, and More

Poland blocked a Russian wiper malware attack on power and heating plants, officials say, avoiding outages during winter and prompting tighter cyber rules. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
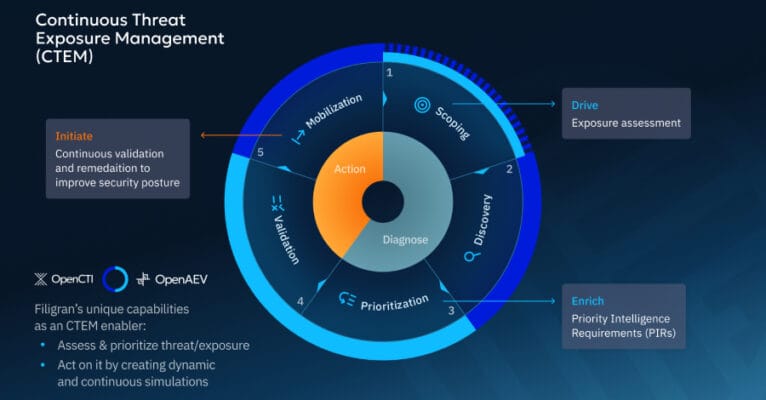
Cybersecurity teams increasingly want to move beyond looking at threats and vulnerabilities in isolation. It’s not only about what could go wrong (vulnerabilities) or who might attack (threats), but where they intersect in your actual environment to create real, exploitable exposure. Which exposures truly matter? Can attackers exploit them? Are our defenses effective? Continuous Threat … Read More “CTEM in Practice: Prioritization, Validation, and Outcomes That Matter – The Hacker News” »
US Charges 31 Suspects in Nationwide ATM Jackpotting Scam – Hackread – Cybersecurity News, Data Breaches, AI, and More

US prosecutors have charged 31 more suspects in a nationwide ATM jackpotting scam, bringing the total number of defendants to 87 across multiple states. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Cybersecurity researchers have discovered a JScript-based command-and-control (C2) framework called PeckBirdy that has been put to use by China-aligned APT actors since 2023 to target multiple environments. The flexible framework has been put to use against Chinese gambling industries and malicious activities targeting Asian government entities and private organizations, according to Trend Micro – Read … Read More “China-Linked Hackers Have Used the PeckBirdy JavaScript C2 Framework Since 2023 – The Hacker News” »
A critical security flaw has been disclosed in Grist‑Core, an open-source, self-hosted version of the Grist relational spreadsheet-database, that could result in remote code execution. The vulnerability, tracked as CVE-2026-24002 (CVSS score: 9.1), has been codenamed Cellbreak by Cyera Research Labs. “One malicious formula can turn a spreadsheet into a Remote Code Execution (RCE) beachhead,” … Read More “Critical Grist-Core Vulnerability Allows RCE Attacks via Spreadsheet Formulas – The Hacker News” »
Microsoft urged customers running Microsoft Office 2016 and 2019 to apply the patch to be protected – Read More –
Nike is investigating after the World Leaks ransomware group posted a 1.4TB data dump – Read More –
Microsoft Office Zero-Day (CVE-2026-21509) – Emergency Patch Issued for Active Exploitation – The Hacker News

Microsoft on Monday issued out-of-band security patches for a high-severity Microsoft Office zero-day vulnerability exploited in attacks. The vulnerability, tracked as CVE-2026-21509, carries a CVSS score of 7.8 out of 10.0. It has been described as a security feature bypass in Microsoft Office. “Reliance on untrusted inputs in a security decision in Microsoft Office allows … Read More “Microsoft Office Zero-Day (CVE-2026-21509) – Emergency Patch Issued for Active Exploitation – The Hacker News” »
With increasing volume of data and regulatory controls that are only tightening, regulated industries have a hard paradox to… The post How Regulated Industries Use Privacy-Enhancing Technologies (PETs) appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
SEC Consult SA-20260126-0 :: Multiple Critical Vulnerabilities in dormakaba Kaba exos 9300 – Full Disclosure

Posted by SEC Consult Vulnerability Lab via Fulldisclosure on Jan 26 SEC Consult Vulnerability Lab Security Advisory < 20260126-0 > ======================================================================= title: Multiple Critical Vulnerabilities product: dormakaba Kaba exos 9300 vulnerable version: < 4.4.1 fixed version: 4.4.1 CVE number: CVE-2025-59090, CVE-2025-59091, CVE-2025-59092 CVE-2025-59093, CVE-2025-59094, CVE-2025-59095… – Read More – Full Disclosure
SEC Consult SA-20260126-1 :: Multiple Critical Vulnerabilities in dormakaba Access Manager – Full Disclosure

Posted by SEC Consult Vulnerability Lab via Fulldisclosure on Jan 26 SEC Consult Vulnerability Lab Security Advisory < 20260126-1 > ======================================================================= title: Multiple Critical Vulnerabilities product: dormakaba Access Manager vulnerable version: Multiple firmware and hardware revisions (details below) fixed version: Multiple firmware and hardware revisions (details below) CVE number: CVE-2025-59097,… – … Read More “SEC Consult SA-20260126-1 :: Multiple Critical Vulnerabilities in dormakaba Access Manager – Full Disclosure” »
SEC Consult SA-20260126-2 :: UART Leaking Sensitive Data in dormakaba registration unit 9002 (PIN pad) – Full Disclosure

Posted by SEC Consult Vulnerability Lab via Fulldisclosure on Jan 26 SEC Consult Vulnerability Lab Security Advisory < 20260126-2 > ======================================================================= title: UART Leaking Sensitive Data product: dormakaba registration unit 9002 (PIN pad) vulnerable version: <SW0039 fixed version: SW0039 CVE number: … Read More “SEC Consult SA-20260126-2 :: UART Leaking Sensitive Data in dormakaba registration unit 9002 (PIN pad) – Full Disclosure” »
Re: Multiple Security Misconfigurations and Customer Enumeration Exposure in Convercent Whistleblowing Platform (EQS Group) – Full Disclosure

Posted by Marco Ermini via Fulldisclosure on Jan 26 Hello everyone, Kindly let me introduce myself. This is the first – and potentially, last – message on this mailing list. I am Marco, the CISO of EQS Group. Kindly allow me to address some of the statements expressed publicly here. About the Convercent application … Read More “Re: Multiple Security Misconfigurations and Customer Enumeration Exposure in Convercent Whistleblowing Platform (EQS Group) – Full Disclosure” »
Re: Multiple Security Misconfigurations and Customer Enumeration Exposure in Convercent Whistleblowing Platform (EQS Group) – Full Disclosure

Posted by Yuffie Kisaragi via Fulldisclosure on Jan 26 Dear Art, Thank you for sharing your detailed evaluation and for pointing out the relevant sections of the CNA Rules. Your argument is well reasoned, particularly with respect to the current guidance on SaaS and exclusively hosted services. I have forwarded your evaluation to the … Read More “Re: Multiple Security Misconfigurations and Customer Enumeration Exposure in Convercent Whistleblowing Platform (EQS Group) – Full Disclosure” »
Threat hunters and researchers are racing to contain a wave of voice-phishing attacks targeting single sign-on tools, already leading to data theft and extortion attempts. Multiple cybercrime groups are combining voice calls and advanced phishing kits to trick victims into handing over access — including a group identifying itself as ShinyHunters, which has publicly named alleged … Read More “A new wave of ‘vishing’ attacks is breaking into SSO accounts in real time – CyberScoop” »
CISA publishes a post-quantum shopping list for agencies. Security professionals aren’t sold – CyberScoop

The Cybersecurity and Infrastructure Security Agency is hoping to guide federal agencies through the murky process of updating their technology stack with quantum-resistant encryption. On Jan. 23, the agency released a list of different IT software and hardware products that are commonly purchased by the federal government and use cryptographic algorithms for encryption or authentication. … Read More “CISA publishes a post-quantum shopping list for agencies. Security professionals aren’t sold – CyberScoop” »
The Trump administration is rescinding a Biden-era memo that was intended to help agencies buy secure software, with the current Office of Management and Budget saying it relied on “unproven and burdensome” processes. A former Biden administration official said the move is “the first major policy step back that I have seen in the administration … Read More “OMB rescinds ‘burdensome’ Biden-era secure software memo – CyberScoop” »
Fake Microsoft Teams Billing Phishing Alerts Reach 6,135 Users via 12,866 Emails – Hackread – Cybersecurity News, Data Breaches, AI, and More

Scammers are abusing Microsoft Teams invitations to send fake billing notices, with 12,866 emails reaching around 6,135 users in a phone-based phishing campaign. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
ChatGPT users beware: your browser extensions could be used to steal your accounts and identity. LayerX Research has identified at least 16 Chrome browser extensions for ChatGPT floating around the internet that promise to enhance work productivity. All show signs of being built by the same threat actor and designed for the same purpose: to … Read More “Some ChatGPT browser extensions are stealing your data – CyberScoop” »