Europe will likely face a combination of heightened cyber-physical attacks and information operations coming from nation-state groups in 2026 – Read More –
Author: Joe-W
The threat actor known as Curly COMrades has been observed exploiting virtualization technologies as a way to bypass security solutions and execute custom malware. According to a new report from Bitdefender, the adversary is said to have enabled the Hyper-V role on selected victim systems to deploy a minimalistic, Alpine Linux-based virtual machine. “This hidden … Read More “Hackers Weaponize Windows Hyper-V to Hide Linux VM and Evade EDR Detection – The Hacker News” »
The world of digital economy is becoming more and more uncertain with the balance between innovation and security becoming… The post Quantum Computing & the Future of Tokenisation Security appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
SonicWall has formally implicated state-sponsored threat actors as behind the September security breach that led to the unauthorized exposure of firewall configuration backup files. “The malicious activity – carried out by a state-sponsored threat actor – was isolated to the unauthorized access of cloud backup files from a specific cloud environment using an API call,” … Read More “SonicWall Confirms State-Sponsored Hackers Behind September Cloud Backup Breach – The Hacker News” »
For the past week, domains associated with the massive Aisuru botnet have repeatedly usurped Amazon, Apple, Google and Microsoft in Cloudflare’s public ranking of the most frequently requested websites. Cloudflare responded by redacting Aisuru domain names from their top websites list. The chief executive at Cloudflare says Aisuru’s overlords are using the botnet to boost … Read More “Cloudflare Scrubs Aisuru Botnet from Top Domains List – Krebs on Security” »
Hackers Steal Personal Data and 17K Slack Messages in Nikkei Data Breach – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Nikkei confirms breach after a virus infected an employee PC, exposing 17,368 names and Slack chat histories. The media giant reported the incident voluntarily. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Congressional leaders are pressing federal agencies to provide more information on their plans to compete with China on a range of tech and cybersecurity issues, including a strategy for promoting American 6G telecommunications infrastructure and limiting Chinese tech in US supply chains. Representative Raja Krishnamoorthi, D-Ill., ranking member on the House Select Committee on the … Read More “Congressional leaders want an executive branch strategy on China 6G, tech supply chain – CyberScoop” »
When a pair of high-profile internet outages took down large chunks of the internet last month, the events briefly brought hundreds of organizations to a near-halt and prevented millions of users from accessing core services for everyday business needs. From Starbucks to crypto exchanges to the messaging app Signal, the outages rippled across nearly every … Read More “With each cloud outage, calls for government action grow louder – CyberScoop” »
A federal judge has reimposed a sentence on Paige Thompson, the former Amazon Web Services engineer convicted in the 2019 Capital One data breach that compromised the personal information of more than 100 million people. U.S. District Judge Robert Lasnik sentenced Thompson to time served, plus five years of supervised release with three years of … Read More “Court reimposes original sentence for Capital One hacker – CyberScoop” »
When a pair of high-profile internet outages took down large chunks of the internet last month, the events briefly brought hundreds of organizations to a near-halt and prevented millions of users from accessing core services for everyday business needs. From Starbucks to crypto exchanges to the messaging app Signal, the outages rippled across nearly every … Read More “With each cloud outage, calls for government action grow louder – CyberScoop” »
A Commerce Department office should investigate Chinese government-connected products in more than a dozen emerging industries for security threats, a group of House GOP committee leaders said in a letter they released Wednesday. In the missive, the lawmakers said the Office of Information and Communications Technology and Services has the power to both investigate and … Read More “House GOP leaders seek government probe, restrictions on Chinese-made tech – CyberScoop” »
Private markets used to operate behind closed doors, exclusive, informal, and built on personal connections more than structure.… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Severe React Native Flaw Exposes Developer Systems to Remote Attacks – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

JFrog researchers found a critical RCE vulnerability (CVE-2025-11953) in the popular React Native CLI. Developers using versions 4.8.0-20.0.0-alpha.2 must update to patch the flaw. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Private markets used to operate behind closed doors, exclusive, informal, and built on personal connections more than structure.… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Behind every alert is an analyst; tired eyes scanning dashboards, long nights spent on false positives, and the constant fear of missing something big. It’s no surprise that many SOCs face burnout before they face their next breach. But this doesn’t have to be the norm. The path out isn’t through working harder, but through … Read More “Why SOC Burnout Can Be Avoided: Practical Steps – The Hacker News” »
U.S. Sanctions 10 North Korean Entities for Laundering $12.7M in Crypto and IT Fraud – The Hacker News
The U.S. Treasury Department on Tuesday imposed sanctions against eight individuals and two entities within North Korea’s global financial network for laundering money for various illicit schemes, including cybercrime and information technology (IT) worker fraud. “North Korean state-sponsored hackers steal and launder money to fund the regime’s nuclear weapons program,” said Under Secretary of – … Read More “U.S. Sanctions 10 North Korean Entities for Laundering $12.7M in Crypto and IT Fraud – The Hacker News” »
Operation “Chargeback” has dismantled global fraud networks misusing stolen card data from more than 4.3 million victims – Read More –
Google on Wednesday said it discovered an unknown threat actor using an experimental Visual Basic Script (VB Script) malware dubbed PROMPTFLUX that interacts with its Gemini artificial intelligence (AI) model API to write its own source code for improved obfuscation and evasion. “PROMPTFLUX is written in VBScript and interacts with Gemini’s API to request specific … Read More “Google Uncovers PROMPTFLUX Malware That Uses Gemini AI to Rewrite Its Code Hourly – The Hacker News” »
A vulnerability has been discovered in CWP (aka Control Web Panel or CentOS Web Panel), which could allow for remote code execution. CWP, or Control Web Panel, is a free server administration tool for enterprise-based Linux distributions like CentOS, which simplifies managing web hosting services. The admin interface (accessible on port 2087 or 2031) and the … Read More “A Vulnerability in CWP (aka Control Web Panel or CentOS Web Panel) Could Allow for Remote Code Execution – Cyber Security Advisories – MS-ISAC” »
A previously unknown cyber actor UNK_SmudgedSerpent has been observed targeting academics with phishing and malware, merging techniques from Iranian groups – Read More –
Norton Crack Midnight Ransomware, Release Free Decryptor – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Norton finds a flaw in the new Midnight ransomware built from Babuk code and releases a free decryptor to help victims recover files without paying a ransom. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Researchers Find ChatGPT Vulnerabilities That Let Attackers Trick AI Into Leaking Data – The Hacker News
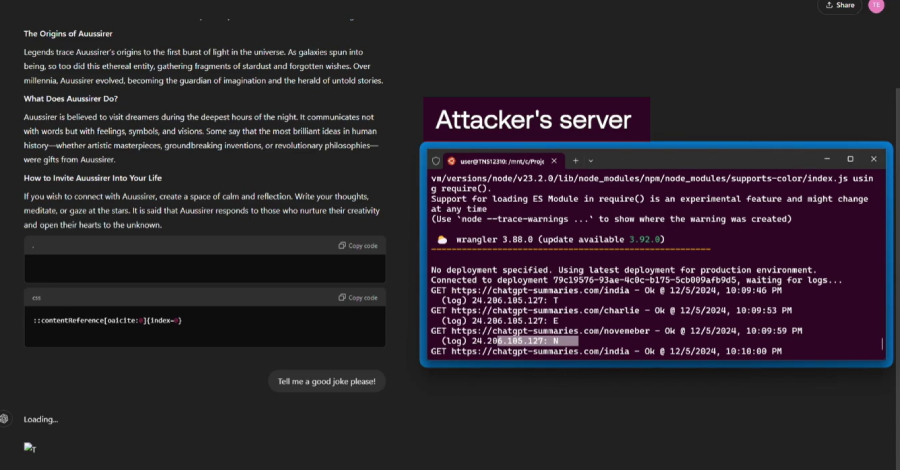
Cybersecurity researchers have disclosed a new set of vulnerabilities impacting OpenAI’s ChatGPT artificial intelligence (AI) chatbot that could be exploited by an attacker to steal personal information from users’ memories and chat histories without their knowledge. The seven vulnerabilities and attack techniques, according to Tenable, were found in OpenAI’s GPT-4o and GPT-5 models. OpenAI has … Read More “Researchers Find ChatGPT Vulnerabilities That Let Attackers Trick AI Into Leaking Data – The Hacker News” »
How the F5 breach, CISA job cuts, and a government shutdown are eroding U.S. cyber readiness – CyberScoop

The federal cybersecurity system is weathering a series of crises that couldn’t have arrived at a worse time. The F5 security breach from Oct. 15, the proposed elimination of more than 1,000 jobs at the Cybersecurity and Infrastructure Security Agency (CISA), and the ongoing federal government shutdown have created a perfect storm that is not … Read More “How the F5 breach, CISA job cuts, and a government shutdown are eroding U.S. cyber readiness – CyberScoop” »
Credentials and Misconfigurations Behind Most Cloud Breaches, Says AWS – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

New AWS report data reveals the top four security failure points in the cloud, including vulnerability exploitation (24%)… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Raise your hand if you’ve heard the myth, “Android isn’t secure.” Android phones, such as the Samsung Galaxy, unlock new ways of working. But, as an IT admin, you may worry about the security—after all, work data is critical. However, outdated concerns can hold your business back from unlocking its full potential. The truth is, … Read More “Securing the Open Android Ecosystem with Samsung Knox – The Hacker News” »
Microsoft Teams Flaws Allowed Attackers to Fake Identities, Rewrite Chats – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Microsoft Teams vulnerabilities let attackers impersonate users, edit chat history, and spoof calls before Microsoft issued security fixes in late 2025. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Mysterious ‘SmudgedSerpent’ Hackers Target U.S. Policy Experts Amid Iran–Israel Tensions – The Hacker News

A never-before-seen threat activity cluster codenamed UNK_SmudgedSerpent has been attributed as behind a set of cyber attacks targeting academics and foreign policy experts between June and August 2025, coinciding with heightened geopolitical tensions between Iran and Israel. “UNK_SmudgedSerpent leveraged domestic political lures, including societal change in Iran and investigation into the – Read More – … Read More “Mysterious ‘SmudgedSerpent’ Hackers Target U.S. Policy Experts Amid Iran–Israel Tensions – The Hacker News” »
10 Successful Marketplaces Built on Sharetribe: Lessons Learned – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

The marketplace revolution is here, and it’s transforming how we buy, sell, and share everything from vintage furniture… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Three of Anthropic’s Claude Desktop extensions were vulnerable to command injection – flaws that have now been fixed – Read More –
Juniper Research predicts a $9bn drop in losses to SMS fraud next year – Read More –
Zscaler estimates 239 malicious Android apps made it onto the official Play store over the past year – Read More –
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added two security flaws impacting Gladinet and Control Web Panel (CWP) to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild. The vulnerabilities in question are listed below – CVE-2025-11371 (CVSS score: 7.5) – A vulnerability in files or directories … Read More “CISA Adds Gladinet and CWP Flaws to KEV Catalog Amid Active Exploitation Evidence – The Hacker News” »