Multiple vulnerabilities have been discovered in Apple products, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user, an attacker could then install … Read More “Multiple Vulnerabilities in Apple Products Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
Author: Joe-W
Russian national pleads guilty to breaking into networks for Yanluowang ransomware attacks – CyberScoop

A 25-year-old Russian national pleaded guilty to multiple charges stemming from their participation in ransomware attacks and faces a maximum penalty up to 53 years in prison. Aleksei Olegovich Volkov, also known as “chubaka.kor,” served as the initial access broker for the Yanluowang ransomware group while living in Russia from July 2021 through November 2022, … Read More “Russian national pleads guilty to breaking into networks for Yanluowang ransomware attacks – CyberScoop” »
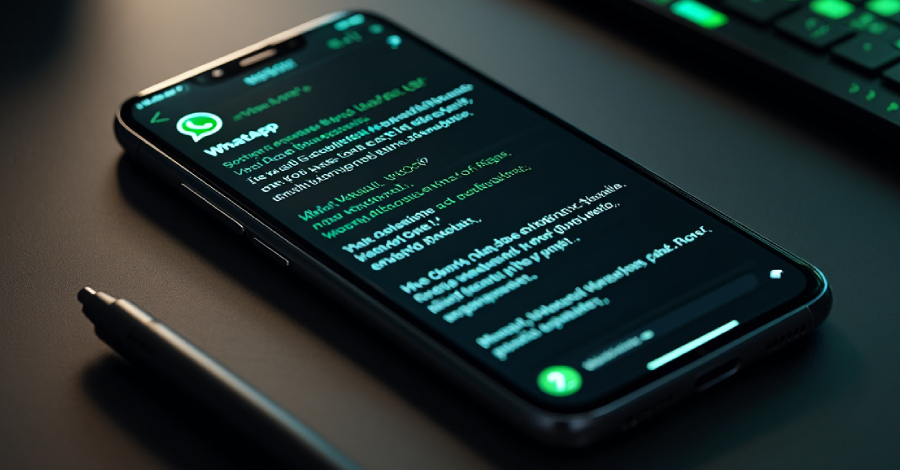
A now-patched security flaw in Samsung Galaxy Android devices was exploited as a zero-day to deliver a “commercial-grade” Android spyware dubbed LANDFALL in targeted attacks in the Middle East. The activity involved the exploitation of CVE-2025-21042 (CVSS score: 8.8), an out-of-bounds write flaw in the “libimagecodec.quram.so” component that could allow remote attackers to execute arbitrary … Read More “Samsung Zero-Click Flaw Exploited to Deploy LANDFALL Android Spyware via WhatsApp – The Hacker News” »
Federal agencies often collect voluminous amounts of data on Americans to fulfill their missions and better understand the public’s needs. But a new whitepaper from the Electronic Privacy Information Center argues that increasingly sophisticated and invasive data mining is now widespread throughout government, allowing machines — and not humans — to determine how data is connected … Read More “Report: Government data mining has gone too far – and AI will make it worse – CyberScoop” »
A China-linked threat actor has been attributed to a cyber attack targeting an U.S. non-profit organization with an aim to establish long-term persistence, as part of broader activity aimed at U.S. entities that are linked to or involved in policy issues. The organization, according to a report from Broadcom’s Symantec and Carbon Black teams, is … Read More “From Log4j to IIS, China’s Hackers Turn Legacy Bugs into Global Espionage Tools – The Hacker News” »
“I Paid Twice” Scam Infects Booking.com Users with PureRAT via ClickFix – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
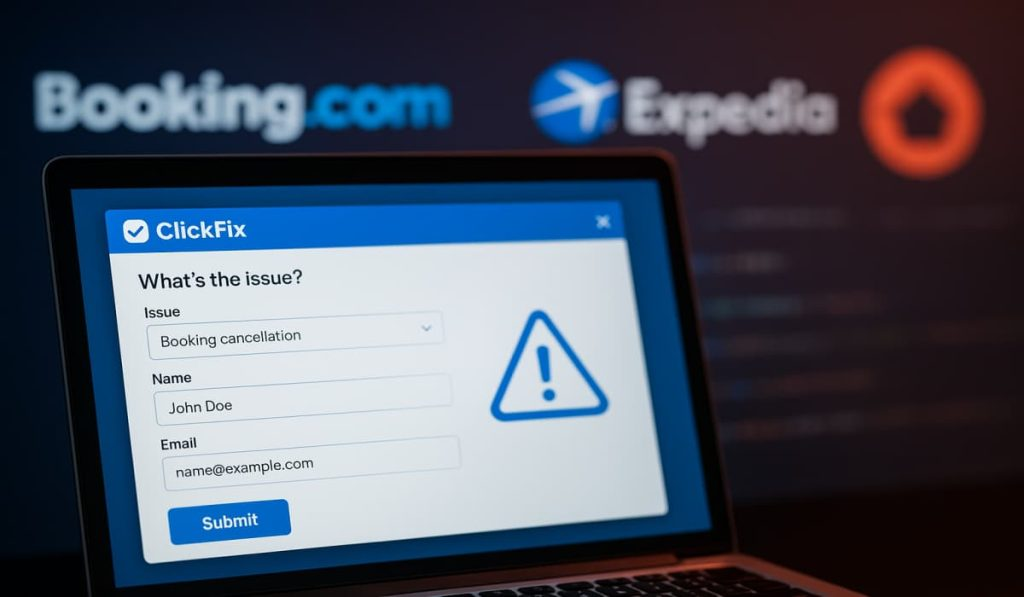
Cybersecurity firm Sekoia reports a widespread fraud where criminals compromise hotel systems (Booking.com, Expedia and others) with PureRAT malware, then use stolen reservation data to phish and defraud guests. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
A new commercial-grade spyware has apparently been targeting Samsung Galaxy phones in the Middle East, but it’s not clear who’s behind it, researchers said in a blog post Friday. Whoever’s responsible, they seized upon a previously unknown, unpatched vulnerability known as a zero-day — a flaw Samsung has since closed, the researchers from Palo Alto … Read More “New Landfall spyware apparently targeting Samsung phones in Middle East – CyberScoop” »
Posted by Jan Schermer on Nov 07 I looked at few repos and posts of “Joseph Goydish”. It all seems to be thinly veiled AI slop and BS. Cited vulns are not attributed to him really and those chains don’t make a lot of sense. Screen recordings look suspicious, some versions reference High Sierra … Read More “Re: : “Glass Cage” – Zero-Click iMessage → Persistent iOS Compromise + Bricking (CVE-2025-24085 / 24201, CNVD-2025-07885) – Full Disclosure” »
Posted by Joseph Goydish II via Fulldisclosure on Nov 07 Hey Patrick, I understand the doubt. However… what’s not slop is reproducible logs I provided a video of and the testable, working exploit I provided. Neither is the upstream patches that can be tracked from the disclosure dates to the cve’s listed in the … Read More “Re: [FD] : “Glass Cage” – Zero-Click iMessage → Persistent iOS Compromise + Bricking (CVE-2025-24085 / 24201, CNVD-2025-07885) – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Nov 07 APPLE-SA-11-05-2025-1 iOS 18.7.2 and iPadOS 18.7.2 iOS 18.7.2 and iPadOS 18.7.2 addresses the following issues. Information about the security content is also available at https://support.apple.com/125633. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. Accessibility Available for: … Read More “APPLE-SA-11-05-2025-1 iOS 18.7.2 and iPadOS 18.7.2 – Full Disclosure” »
Posted by Martin Heiland via Fulldisclosure on Nov 07 Dear subscribers, We’re sharing our latest advisory with you and like to thank everyone who contributed in finding and solving those vulnerabilities. Feel free to join our bug bounty programs for OX App Suite, Dovecot and PowerDNS at YesWeHack. This advisory has also been published … Read More “OXAS-ADV-2025-0002: OX App Suite Security Advisory – Full Disclosure” »
runc container breakouts via procfs writes: CVE-2025-31133, CVE-2025-52565, and CVE-2025-52881 – Full Disclosure

Posted by Aleksa Sarai via Fulldisclosure on Nov 07 | NOTE: This advisory was sent to <security-announce () opencontainers org> | on 2025-10-16. If you ship any Open Container Initiative software, we | highly recommend that you subscribe to our security-announce list in | order to receive more timely disclosures of future security issues. … Read More “runc container breakouts via procfs writes: CVE-2025-31133, CVE-2025-52565, and CVE-2025-52881 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Nov 07 APPLE-SA-11-03-2025-7 visionOS 26.1 visionOS 26.1 addresses the following issues. Information about the security content is also available at https://support.apple.com/125638. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. Apple Account Available for: Apple Vision Pro (all models) … Read More “APPLE-SA-11-03-2025-7 visionOS 26.1 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Nov 07 APPLE-SA-11-03-2025-8 Safari 26.1 Safari 26.1 addresses the following issues. Information about the security content is also available at https://support.apple.com/125640. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. Safari Available for: macOS Sonoma and macOS Sequoia Impact: … Read More “APPLE-SA-11-03-2025-8 Safari 26.1 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Nov 07 APPLE-SA-11-03-2025-9 Xcode 26.1 Xcode 26.1 addresses the following issues. Information about the security content is also available at https://support.apple.com/125641. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. GNU Available for: macOS Sequoia 15.6 and later Impact: … Read More “APPLE-SA-11-03-2025-9 Xcode 26.1 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Nov 07 APPLE-SA-11-03-2025-4 macOS Sonoma 14.8.2 macOS Sonoma 14.8.2 addresses the following issues. Information about the security content is also available at https://support.apple.com/125636. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. Admin Framework Available for: macOS Sonoma Impact: … Read More “APPLE-SA-11-03-2025-4 macOS Sonoma 14.8.2 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Nov 07 APPLE-SA-11-03-2025-5 tvOS 26.1 tvOS 26.1 addresses the following issues. Information about the security content is also available at https://support.apple.com/125637. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. Apple Neural Engine Available for: Apple TV 4K (2nd … Read More “APPLE-SA-11-03-2025-5 tvOS 26.1 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Nov 07 APPLE-SA-11-03-2025-6 watchOS 26.1 watchOS 26.1 addresses the following issues. Information about the security content is also available at https://support.apple.com/125639. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. Apple Account Available for: Apple Watch Series 6 and … Read More “APPLE-SA-11-03-2025-6 watchOS 26.1 – Full Disclosure” »
Cybersecurity headlines still focus on the headline-grabbing moments, whether it’s the latest breach, a zero-day exploit, or an eye-catching product launch. However, beneath the surface noise, a quieter but more profound transformation is taking place—driven by regulations that are changing the way organizations think about, approach, and communicate on security.” Across the globe, new standards … Read More “The quiet revolution: How regulation is forcing cybersecurity accountability – CyberScoop” »
Posted by SBA Research Security Advisory via Fulldisclosure on Nov 07 # Checkmk Cross Site Scripting # Link: https://github.com/sbaresearch/advisories/tree/public/2025/SBA-ADV-20250729-01_Checkmk_Cross_Site_Scripting ## Vulnerability Overview ## Checkmk in versions before 2.4.0p14 and 2.3.0p39, as well as in branches 2.2.0, 2.1.0 and 2.0.0 is prone to a Stored Cross-Site Scripting (XSS) vulnerability when used in a distributed monitoring … Read More “[SBA-ADV-20250729-01] CVE-2025-39663: Checkmk Cross Site Scripting – Full Disclosure” »
Re: [oss-security] runc container breakouts via procfs writes: CVE-2025-31133, CVE-2025-52565, and CVE-2025-52881 – Full Disclosure
![Re: [oss-security] runc container breakouts via procfs writes: CVE-2025-31133, CVE-2025-52565, and CVE-2025-52881 – Full Disclosure](https://attackfeed.com/wp-content/uploads/2025/11/fulldisclosure-img-5H6Vfr.webp)
Posted by akendo () akendo eu on Nov 07 Thank you for sharing this. I wondered how big the impact of this vulnerability is when you have only the ability to access runs via the Kubernetes API? Would you argue that the vulnerability becomes harder (or impossible?) to exploit when you can only interact … Read More “Re: [oss-security] runc container breakouts via procfs writes: CVE-2025-31133, CVE-2025-52565, and CVE-2025-52881 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Nov 07 APPLE-SA-11-03-2025-1 iOS 26.1 and iPadOS 26.1 iOS 26.1 and iPadOS 26.1 addresses the following issues. Information about the security content is also available at https://support.apple.com/125632. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. Accessibility Available for: … Read More “APPLE-SA-11-03-2025-1 iOS 26.1 and iPadOS 26.1 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Nov 07 APPLE-SA-11-03-2025-2 macOS Tahoe 26.1 macOS Tahoe 26.1 addresses the following issues. Information about the security content is also available at https://support.apple.com/125634. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. Admin Framework Available for: macOS Tahoe Impact: … Read More “APPLE-SA-11-03-2025-2 macOS Tahoe 26.1 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Nov 07 APPLE-SA-11-03-2025-3 macOS Sequoia 15.7.2 macOS Sequoia 15.7.2 addresses the following issues. Information about the security content is also available at https://support.apple.com/125635. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. Admin Framework Available for: macOS Sequoia Impact: … Read More “APPLE-SA-11-03-2025-3 macOS Sequoia 15.7.2 – Full Disclosure” »
Fake 0-Day Exploit Emails Trick Crypto Users Into Running Malicious Code – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Bolster AI reveals a new scam using a simple JS code via Emkei’s Mailer to fake 37% profits and steal crypto. Act fast to secure your wallet. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Hidden Logic Bombs in Malware-Laced NuGet Packages Set to Detonate Years After Installation – The Hacker News

A set of nine malicious NuGet packages has been identified as capable of dropping time-delayed payloads to sabotage database operations and corrupt industrial control systems. According to software supply chain security company Socket, the packages were published in 2023 and 2024 by a user named “shanhai666” and are designed to run malicious code after specific … Read More “Hidden Logic Bombs in Malware-Laced NuGet Packages Set to Detonate Years After Installation – The Hacker News” »
Sandworm deployed data wipers against Ukrainian governmental entities and companies in the energy, logistics and grain sectors – Read More –
Multiple vulnerabilities have been discovered in Cisco products, the most severe of which could allow for remote code execution. Cisco is a leading technology company best known for its networking hardware and software, such as routers and switches, that form the backbone of the internet and enterprise networks. Successful exploitation of the most severe of … Read More “Multiple Vulnerabilities in Cisco Products Could Allow for Remote Code Execution – Cyber Security Advisories – MS-ISAC” »
Imagine this: Sarah from accounting gets what looks like a routine password reset email from your organization’s cloud provider. She clicks the link, types in her credentials, and goes back to her spreadsheet. But unknown to her, she’s just made a big mistake. Sarah just accidentally handed over her login details to cybercriminals who are … Read More “Enterprise Credentials at Risk – Same Old, Same Old? – The Hacker News” »
Google Launches New Maps Feature to Help Businesses Report Review-Based Extortion Attempts – The Hacker News
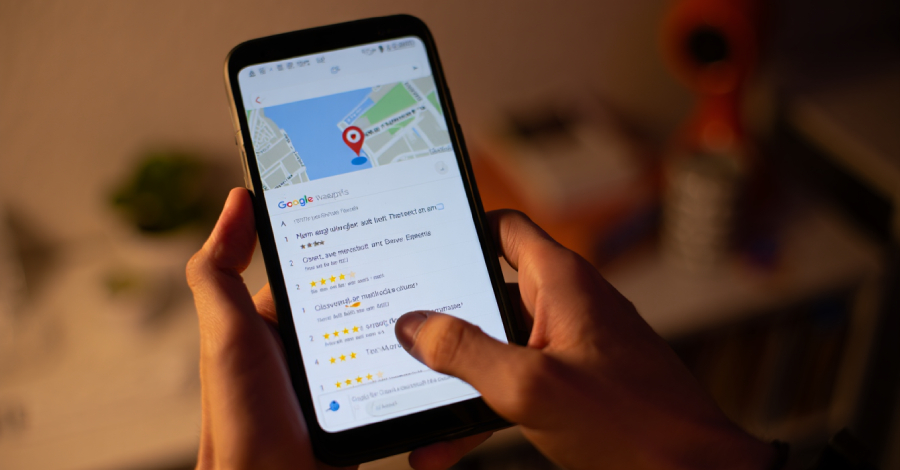
Google on Thursday said it’s rolling out a dedicated form to allow businesses listed on Google Maps to report extortion attempts made by threat actors who post inauthentic bad reviews on the platform and demand ransoms to remove the negative comments. The approach is designed to tackle a common practice called review bombing, where online … Read More “Google Launches New Maps Feature to Help Businesses Report Review-Based Extortion Attempts – The Hacker News” »
Vibe-Coded Malicious VS Code Extension Found with Built-In Ransomware Capabilities – The Hacker News

Cybersecurity researchers have flagged a malicious Visual Studio Code (VS Code) extension with basic ransomware capabilities that appears to be created with the help of artificial intelligence – in other words, vibe-coded. Secure Annex researcher John Tuckner, who flagged the extension “susvsex,” said it does not attempt to hide its malicious functionality. The extension was … Read More “Vibe-Coded Malicious VS Code Extension Found with Built-In Ransomware Capabilities – The Hacker News” »
Account Takeover: What Is It and How to Fight It – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Account takeover (ATO) attacks can devastate individuals and organisations, from personal profiles to enterprise systems. The financial impact… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
A federal agency that supplies budget and economic information to Congress has suffered a cybersecurity incident, reportedly at the hands of a suspected foreign party. A spokesperson for the Congressional Budget Office (CBO) acknowledged the incident Thursday after The Washington Post reported that the office was hacked, with the attackers potentially accessing communications between lawmakers … Read More “Agency that provides budget data to Congress hit with security incident – CyberScoop” »
“Pay up or we share the tapes”: Hackers target massage parlour clients in blackmail scheme – Graham Cluley

South Korean police have uncovered a hacking operation that stole sensitive data from massage parlours and blackmailed their male clientele. Read more in my article on the Hot for Security blog. – Read More – Graham Cluley
Critical infrastructure is once again in the spotlight, as it is revealed that several UK water suppliers have reported cybersecurity incidents over the last two years. Read more in my article on the Fortra blog. – Read More – Graham Cluley
New ChatGPT Vulnerabilities Let Hackers Steal Data, Hijack Memory – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Seven vulnerabilities in ChatGPT (including GPT-5) allow attackers to use ‘0-click’ and ‘memory injection’ to bypass safety features and persistently steal private user data and chat history. Tenable Research exposes the flaws. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
SonicWall said a state-sponsored threat actor was behind the brute-force attack that exposed firewall configuration files of every customer that used the company’s cloud backup service. The vendor pinned the responsibility for the attack on an undisclosed nation state Tuesday, after Mandiant concluded its investigation into the incident. SonicWall did not attribute the attack to … Read More “SonicWall pins attack on customer portal to undisclosed nation-state – CyberScoop” »
Experts have uncovered large-scale phishing exploiting Booking.com, Airbnb and Expedia accounts, targeting hotels and customers – Read More –
Cisco on Wednesday disclosed that it became aware of a new attack variant that’s designed to target devices running Cisco Secure Firewall Adaptive Security Appliance (ASA) Software and Cisco Secure Firewall Threat Defense (FTD) Software releases that are susceptible to CVE-2025-20333 and CVE-2025-20362. “This attack can cause unpatched devices to unexpectedly reload, leading to denial-of-service … Read More “Cisco Warns of New Firewall Attack Exploiting CVE-2025-20333 and CVE-2025-20362 – The Hacker News” »
A previously unknown threat activity cluster has been observed impersonating Slovak cybersecurity company ESET as part of phishing attacks targeting Ukrainian entities. The campaign, detected in May 2025, is tracked by the security outfit under the moniker InedibleOchotense, describing it as Russia-aligned. “InedibleOchotense sent spear-phishing emails and Signal text messages, containing a link – Read … Read More “Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine – The Hacker News” »
A new Cisco report exposed large language models to multi-turn adversarial attacks with 90% success rates – Read More –
Cavalry Werewolf Hit Russian Government with New ShellNET Backdoor – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Doctor Web uncovers a targeted cyberattack on a Russian government body by the Cavalry Werewolf group using a new ShellNET backdoor and Telegram-based control. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Top 7 Companies Specializing in Product Discovery Phase in 2025 – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Finding the right partner is less about headcount and more about repeatable outcomes, which is why the profiles… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
ThreatsDay Bulletin: AI Tools in Malware, Botnets, GDI Flaws, Election Attacks & More – The Hacker News

Cybercrime has stopped being a problem of just the internet — it’s becoming a problem of the real world. Online scams now fund organized crime, hackers rent violence like a service, and even trusted apps or social platforms are turning into attack vectors. The result is a global system where every digital weakness can be … Read More “ThreatsDay Bulletin: AI Tools in Malware, Botnets, GDI Flaws, Election Attacks & More – The Hacker News” »
Introduction Financial institutions are facing a new reality: cyber-resilience has passed from being a best practice, to an operational necessity, to a prescriptive regulatory requirement. Crisis management or Tabletop exercises, for a long time relatively rare in the context of cybersecurity, have become required as a series of regulations has introduced this requirement to FSI … Read More “From Tabletop to Turnkey: Building Cyber Resilience in Financial Services – The Hacker News” »
Smashing Security podcast #442: The hack that messed with time, and rogue ransom where negotiators – Graham Cluley

Time itself comes under attack as a state-backed hacking gang spends two years tunnelling toward a nation’s master clock — with chaos potentially only a tick away. Plus when ransomware negotiators turn to the dark side, what could possibly go wrong? All this and more is discussed in episode 442 of the “Smashing Security” podcast … Read More “Smashing Security podcast #442: The hack that messed with time, and rogue ransom where negotiators – Graham Cluley” »
ENISA report reveals DDoS accounted for 60% of public sector security incidents last year – Read More –
Bitdefender Named a Representative Vendor in the 2025 Gartner® Market Guide for Managed Detection and Response – The Hacker News

Bitdefender has once again been recognized as a Representative Vendor in the Gartner® Market Guide for Managed Detection and Response (MDR) — marking the fourth consecutive year of inclusion. According to Gartner, more than 600 providers globally claim to deliver MDR services, yet only a select few meet the criteria to appear in the Market … Read More “Bitdefender Named a Representative Vendor in the 2025 Gartner® Market Guide for Managed Detection and Response – The Hacker News” »
By 31 March 2026, organisations should have alternatives to Mail Check and Web Check in place. – Read More – NCSC Feed
Google warns of “just-in-time AI” malware using LLMs to evade detection and generate malicious code on-demand – Read More –












![[SBA-ADV-20250729-01] CVE-2025-39663: Checkmk Cross Site Scripting – Full Disclosure](https://attackfeed.com/wp-content/uploads/2025/11/fulldisclosure-img-nsKKhj.webp)