The UK government is overhauling cybersecurity laws for the first time since 2018 with the Cyber Security and Resilience Bill – Read More –
Author: Joe-W
Google Launches ‘Private AI Compute’ — Secure AI Processing with On-Device-Level Privacy – The Hacker News

Google on Tuesday unveiled a new privacy-enhancing technology called Private AI Compute to process artificial intelligence (AI) queries in a secure platform in the cloud. The company said it has built Private AI Compute to “unlock the full speed and power of Gemini cloud models for AI experiences, while ensuring your personal data stays private … Read More “Google Launches ‘Private AI Compute’ — Secure AI Processing with On-Device-Level Privacy – The Hacker News” »
Google on Tuesday unveiled a new privacy-enhancing technology called Private AI Compute to process artificial intelligence (AI) queries in a secure platform in the cloud. The company said it has built Private AI Compute to “unlock the full speed and power of Gemini cloud models for AI experiences, while ensuring your personal data stays private … Read More “Google Launches ‘Private AI Compute’ — Secure AI Processing with On-Device-Level Privacy – The Hacker News” »
As the second half of the decade enters, the quantum computing, cryptographic development, and enterprise transformation point is even… The post Future Outlook: Quantum-Agile Ecosystems in 2026 & Beyond appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
8 Recommended Account Takeover Security Providers – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
In 2025, account takeover (ATO) attacks are a significant – and growing – cybersecurity threat, especially in the… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Cl0p Ransomware Lists NHS UK as Victim, Days After Washington Post Breach – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Cl0p ransomware lists NHS UK as a victim days after The Washington Post confirms a major Oracle E-Business breach linked to CVE-2025-61882. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Microsoft Patch Tuesday addresses 63 defects, including one actively exploited zero-day – CyberScoop

Microsoft addressed 63 vulnerabilities affecting its underlying systems and core products, including one actively exploited zero-day, the company said in its latest monthly security update. The zero-day vulnerability — CVE-2025-62215 — affects the Windows Kernel and has a CVSS rating of 7.0 due to a high attack complexity, according to Microsoft. Exploitation, which could allow … Read More “Microsoft Patch Tuesday addresses 63 defects, including one actively exploited zero-day – CyberScoop” »
Amazon became the latest company to open its large language models to outside security researchers, announcing the creation of a new bug bounty program for the tech giant’s AI tools. The program will allow select third-party researchers and academic teams to prod NOVA, Amazon’s suite of foundational AI models and receive compensation for their findings. … Read More “Amazon rolls out AI bug bounty program – CyberScoop” »
GlobalLogic, a digital engineering and product design company, said it was impacted by a widespread data theft and extortion campaign linked to a zero-day vulnerability in Oracle E-Business Suite. The company, which was acquired by Hitachi in 2021 and has a current customer base of nearly 600 clients, filed data breach notifications with authorities in … Read More “Hitachi subsidiary GlobalLogic impacted by Clop’s attack spree on Oracle customers – CyberScoop” »
WhatsApp Malware ‘Maverick’ Hijacks Browser Sessions to Target Brazil’s Biggest Banks – The Hacker News

Threat hunters have uncovered similarities between a banking malware called Coyote and a newly disclosed malicious program dubbed Maverick that has been propagated via WhatsApp. According to a report from CyberProof, both malware strains are written in .NET, target Brazilian users and banks, and feature identical functionality to decrypt, targeting banking URLs and monitor banking … Read More “WhatsApp Malware ‘Maverick’ Hijacks Browser Sessions to Target Brazil’s Biggest Banks – The Hacker News” »
I’ve made it through Pwn2Own Ireland, and while many are celebrated those who served their country in the armed services, patch Tuesday stops for no one. So affix your poppy accordingly, and let’s take a look at the latest security offerings from Adobe and Microsoft. If you’d rather watch the full video recap covering the … Read More “The November 2025 Security Update Review – Zero Day Initiative – Blog” »
A new cyber-attack has been observed exploiting Google Find Hub to remotely wipe Android devices, linked to North Korean APTs – Read More –
In episode 76 of The AI Fix, two US federal judges blame AI for imaginary case law, a Chinese “humanoid” dramatically sheds its skin onstage, Toyota unveils a crabby walking chair creeps us out, Google plans AI chips in orbit, robot dogs get jobs at Sellafield, and AI writes cruise-ship gags from the 1950s (but … Read More “The AI Fix #76: AI self-awareness, and the death of comedy – Graham Cluley” »
Qilin group ransomware incidents have surged in SMBs, exploiting security gaps and collaborating with Scattered Spider threat group – Read More –
The malware known as GootLoader has resurfaced yet again after a brief spike in activity earlier this March, according to new findings from Huntress. The cybersecurity company said it observed three GootLoader infections since October 27, 2025, out of which two resulted in hands-on keyboard intrusions with domain controller compromise taking place within 17 hours … Read More “GootLoader Is Back, Using a New Font Trick to Hide Malware on WordPress Sites – The Hacker News” »
Virginia-based BigBear.ai announced Monday it will acquire Ask Sage, a generative artificial intelligence platform specializing in secure deployment of AI models and agentic systems across defense and other regulated sectors, in a deal valued at about $250 million. Ask Sage focuses on safety and security in the growing field of agentic AI, or systems capable … Read More “BigBear.ai to buy Ask Sage, strengthening security-centric AI for federal agencies – CyberScoop” »
Have I Been Pwned Adds 1.96B Accounts From Synthient Credential Data – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Have I Been Pwned (HIBP), the popular breach notification service, has added another massive dataset to its platform.… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Threat actors were exploiting vulnerable versions of Triofox after a patched version was released, said Google Cloud researchers – Read More –
Android Trojan ‘Fantasy Hub’ Malware Service Turns Telegram Into a Hub for Hackers – The Hacker News

Cybersecurity researchers have disclosed details of a new Android remote access trojan (RAT) called Fantasy Hub that’s sold on Russian-speaking Telegram channels under a Malware-as-a-Service (MaaS) model. According to its seller, the malware enables device control and espionage, allowing threat actors to collect SMS messages, contacts, call logs, images, and videos, as well as intercept, … Read More “Android Trojan ‘Fantasy Hub’ Malware Service Turns Telegram Into a Hub for Hackers – The Hacker News” »
Fake NPM Package With 206K Downloads Targeted GitHub for Credentials – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Veracode Threat Research exposed a targeted typosquatting attack on npm, where the malicious package @acitons/artifact stole GitHub tokens. Learn how this supply chain failure threatened the GitHub organisation’s code. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Cybersecurity researchers have discovered a malicious npm package named “@acitons/artifact” that typosquats the legitimate “@actions/artifact” package with the intent to target GitHub-owned repositories. “We think the intent was to have this script execute during a build of a GitHub-owned repository, exfiltrate the tokens available to the build environment, and then use those tokens to publish … Read More “Researchers Detect Malicious npm Package Targeting GitHub-Owned Repositories – The Hacker News” »
AI-enabled supply chain attacks jumped 156% last year. Discover why traditional defenses are failing and what CISOs must do now to protect their organizations. Download the full CISO’s expert guide to AI Supply chain attacks here. TL;DR AI-enabled supply chain attacks are exploding in scale and sophistication – Malicious package uploads to open-source repositories jumped … Read More “CISO’s Expert Guide To AI Supply Chain Attacks – The Hacker News” »
Cisco Finds Open-Weight AI Models Easy to Exploit in Long Chats – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Cisco’s new research shows that open-weight AI models, while driving innovation, face serious security risks as multi-turn attacks, including conversational persistence, can bypass safeguards and expose data. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
CISA has demanded federal agencies patch a zero-day vulnerability affecting Samsung devices used in LandFall spyware attacks – Read More –
KnowBe4 claims the new Quantum Route Redirect kit is supercharging phishing attacks on Microsoft365 users – Read More –
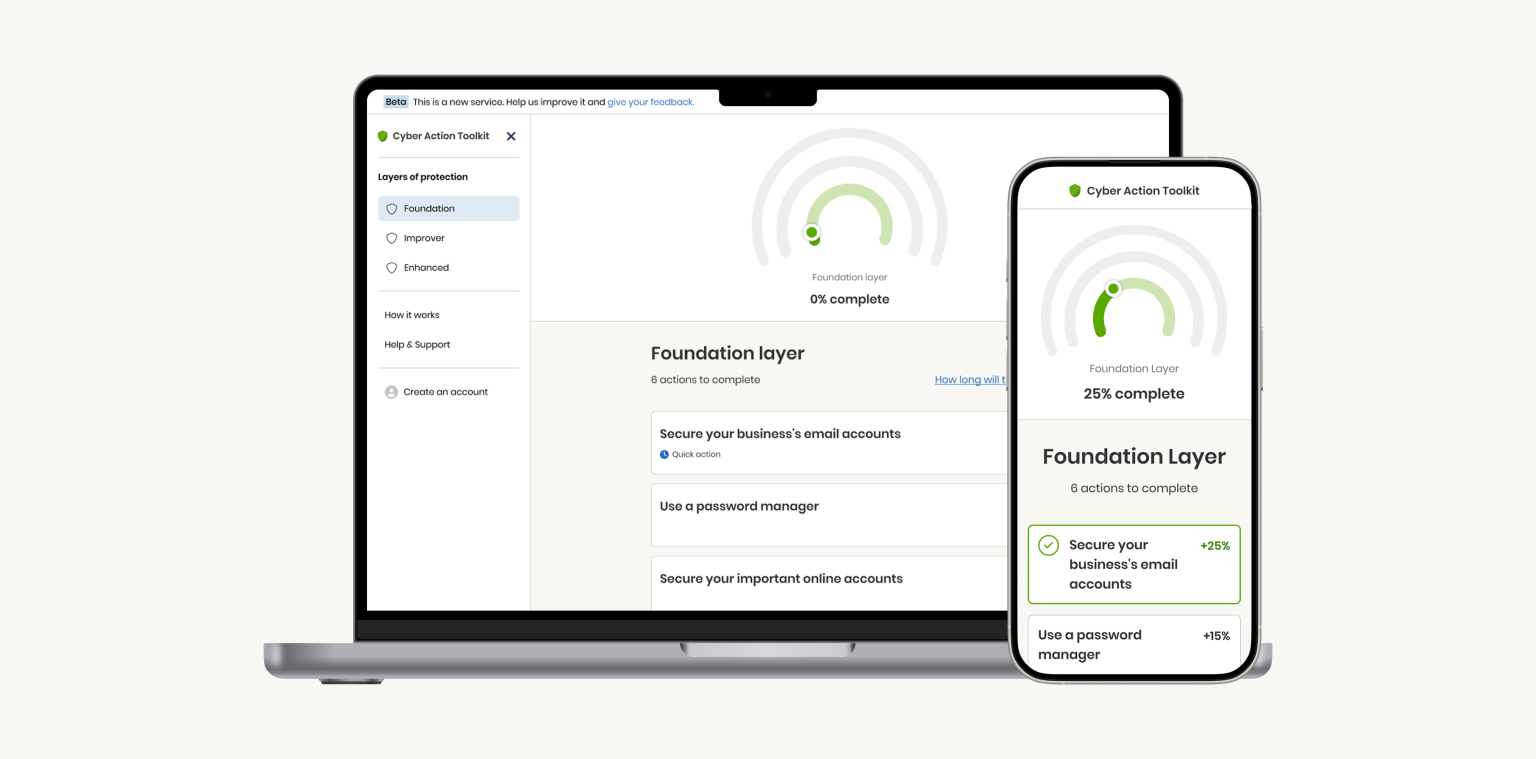
How the NCSC’s ‘Cyber Action Toolkit’ is helping small businesses to improve their cyber security. – Read More – NCSC Feed
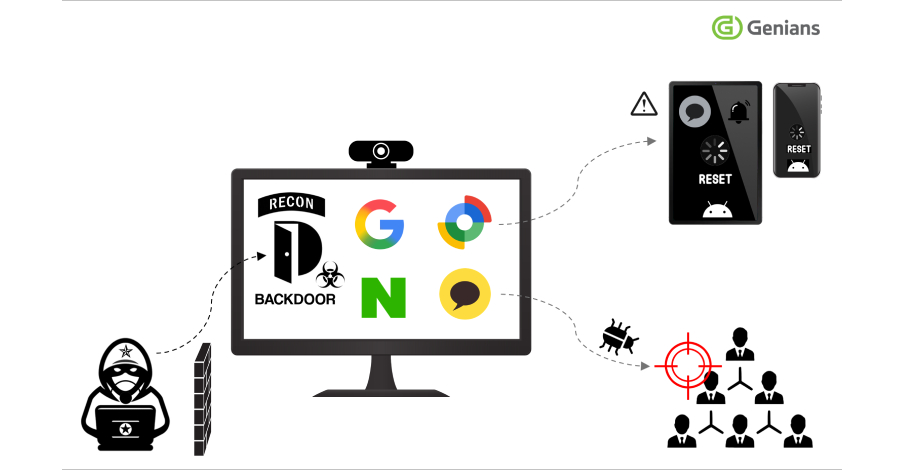
The North Korea-affiliated threat actor known as Konni (aka Earth Imp, Opal Sleet, Osmium, TA406, and Vedalia) has been attributed to a new set of attacks targeting both Android and Windows devices for data theft and remote control. “Attackers impersonated psychological counselors and North Korean human rights activists, distributing malware disguised as stress-relief programs,” the … Read More “Konni Hackers Turn Google’s Find Hub into a Remote Data-Wiping Weapon – The Hacker News” »
Hackers Exploiting Triofox Flaw to Install Remote Access Tools via Antivirus Feature – The Hacker News

Google’s Mandiant Threat Defense on Monday said it discovered n-day exploitation of a now-patched security flaw in Gladinet’s Triofox file-sharing and remote access platform. The critical vulnerability, tracked as CVE-2025-12480 (CVSS score: 9.1), allows an attacker to bypass authentication and access the configuration pages, resulting in the upload and execution of arbitrary payloads. The – … Read More “Hackers Exploiting Triofox Flaw to Install Remote Access Tools via Antivirus Feature – The Hacker News” »
Researchers aren’t very concerned about the dozens of undisclosed F5 vulnerabilities a nation-state attacker stole during a prolonged attack on F5’s internal systems. Yet, the heist of sensitive intelligence from a widely used vendor’s internal network resembles previous espionage-driven attacks that could pose long-term consequences downstream. F5, which became aware of the attack Aug. 9 … Read More “What’s left to worry (and not worry) about in the F5 breach aftermath – CyberScoop” »
Intel Sues Ex-Engineer for Stealing 18,000 ‘Top Secret’ Files – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Intel, the leading computer chip maker, has filed a lawsuit seeking at least $250,000 in damages from a… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Why Organizations Can’t Ignore Vendor Risk Assessment in Today’s Cyber-Threat Landscape – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

In an era where digital ecosystems extend far beyond a company’s internal network, enterprise cybersecurity is no longer… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
LANDFALL Spyware Targeted Samsung Galaxy Phones via Malicious Images – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Unit 42 discovered LANDFALL, commercial-grade Android spyware, which used a hidden image vulnerability (CVE-2025-21042) to remotely spy on Samsung Galaxy users via WhatsApp. Update your phone now. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
A new study has revealed 65% of top AI firms have leaked sensitive data on GitHub, risking $400bn in assets – Read More –
Volexity has linked spear phishing operations to China-aligned UTA0388 in new campaigns using advanced tactics and LLMs – Read More –
Incident Response Team (ShieldForce) Partners with AccuKnox for Zero Trust CNAPP in Latin America – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Menlo Park, CA, USA, 10th November 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
According to the new Browser Security Report 2025, security leaders are discovering that most identity, SaaS, and AI-related risks converge in a single place, the user’s browser. Yet traditional controls like DLP, EDR, and SSE still operate one layer too low. What’s emerging isn’t just a blindspot. It’s a parallel threat surface: unmanaged extensions acting … Read More “New Browser Security Report Reveals Emerging Threats for Enterprises – The Hacker News” »
⚡ Weekly Recap: Hyper-V Malware, Malicious AI Bots, RDP Exploits, WhatsApp Lockdown and More – The Hacker News

Cyber threats didn’t slow down last week—and attackers are getting smarter. We’re seeing malware hidden in virtual machines, side-channel leaks exposing AI chats, and spyware quietly targeting Android devices in the wild. But that’s just the surface. From sleeper logic bombs to a fresh alliance between major threat groups, this week’s roundup highlights a clear … Read More “⚡ Weekly Recap: Hyper-V Malware, Malicious AI Bots, RDP Exploits, WhatsApp Lockdown and More – The Hacker News” »
Monsta FTP Vulnerability Exposed Thousands of Servers to Full Takeover – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Monsta FTP users must update now! A critical pre-authentication flaw (CVE-2025-34299) allows hackers to fully take over web servers. Patch to version 2.11.3 immediately. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
On Sept. 30, 2025, the Cybersecurity Information Sharing Act (CISA 2015) officially expired, ending a decade-long framework that helped government and industry share cyber-threat data safely and consistently. For the first time in ten years, the United States lacks the statutory foundation that underpinned its public-private threat-intelligence ecosystem. At a time when adversaries are exploiting … Read More “CISA’s expiration leaves a dangerous void in US cyber collaboration – CyberScoop” »
Legislation to end the federal government shutdown includes a provision that would extend an expired cybersecurity information sharing law through the end of January. Extension of the Cybersecurity Information Sharing Act of 2015 is something industry groups have coveted since even before its sunset at the end of September. Previous attempts to extend it fell … Read More “Cyber information sharing law would get extension under shutdown deal bill – CyberScoop” »
Monsta FTP Vulnerability Exposed Thousands of Servers to Full Takeover – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Monsta FTP users must update now! A critical pre-authentication flaw (CVE-2025-34299) allows hackers to fully take over web servers. Patch to version 2.11.3 immediately. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
A Dutch TV and radio broadcaster has found itself at the mercy of cybercriminals after suffering a cyber attack, and leaving it scrambling to find ways to play music to its listeners. Read more in my article on the Hot for Security blog. – Read More – Graham Cluley
The UK’s National Crime Agency is warning men under 45 that crypto dreams can soon become a scam nightmare – Read More –
GlassWorm Malware Discovered in Three VS Code Extensions with Thousands of Installs – The Hacker News

Cybersecurity researchers have disclosed a new set of three extensions associated with the GlassWorm campaign, indicating continued attempts on part of threat actors to target the Visual Studio Code (VS Code) ecosystem. The extensions in question, which are still available for download, are listed below – ai-driven-dev.ai-driven-dev (3,402 downloads) adhamu.history-in-sublime-merge (4,057 – Read More – … Read More “GlassWorm Malware Discovered in Three VS Code Extensions with Thousands of Installs – The Hacker News” »
Cybersecurity researchers have called attention to a massive phishing campaign targeting the hospitality industry that lures hotel managers to ClickFix-style pages and harvest their credentials by deploying malware like PureRAT. “The attacker’s modus operandi involved using a compromised email account to send malicious messages to multiple hotel establishments,” Sekoia said. “This campaign – Read More … Read More “Large-Scale ClickFix Phishing Attacks Target Hotel Systems with PureRAT Malware – The Hacker News” »
The UK’s National Cyber Security Centre has urged users of its Web Check and Mail Check services to find alternatives – Read More –
In a landmark achievement redefining digital trust in India’s financial ecosystem, JISA Softech has successfully implemented its flagship data… The post India’s Largest Insurer Safeguards 30 Cr+ PII with CryptoBind appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
The U.S. government is reportedly preparing to ban the sale of wireless routers and other networking gear from TP-Link Systems, a tech company that currently enjoys an estimated 50% market share among home users and small businesses. Experts say while the proposed ban may have more to do with TP-Link’s ties to China than any … Read More “Drilling Down on Uncle Sam’s Proposed TP-Link Ban – Krebs on Security” »
FBI Wants to Know Who Runs Archive.ph – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
The FBI has issued a federal subpoena to domain registrar Tucows, demanding extensive billing and session records to unmask the anonymous operator of Archive.ph (Archive.is and Archive.today). The site, known for bypassing paywalls, is now the subject of an undisclosed criminal investigation. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto … Read More “FBI Wants to Know Who Runs Archive.ph – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More” »
Microsoft Uncovers ‘Whisper Leak’ Attack That Identifies AI Chat Topics in Encrypted Traffic – The Hacker News
Microsoft has disclosed details of a novel side-channel attack targeting remote language models that could enable a passive adversary with capabilities to observe network traffic to glean details about model conversation topics despite encryption protections under certain circumstances. This leakage of data exchanged between humans and streaming-mode language models could pose serious risks to – Read More – … Read More “Microsoft Uncovers ‘Whisper Leak’ Attack That Identifies AI Chat Topics in Encrypted Traffic – The Hacker News” »