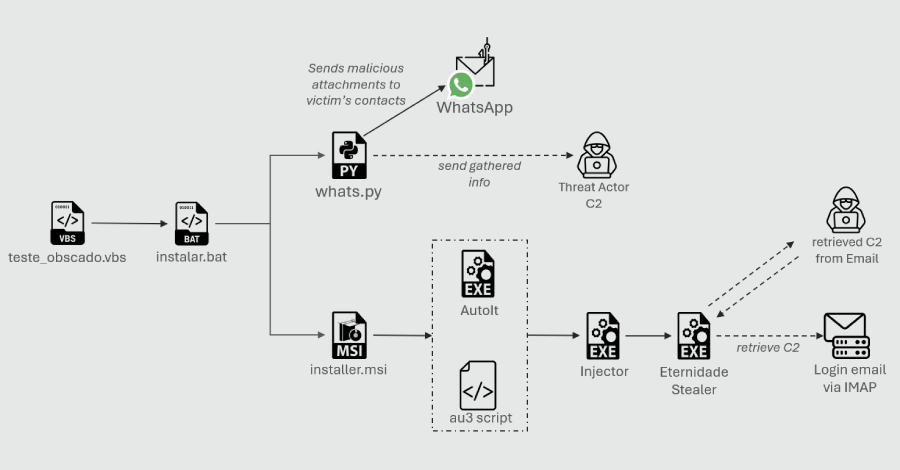
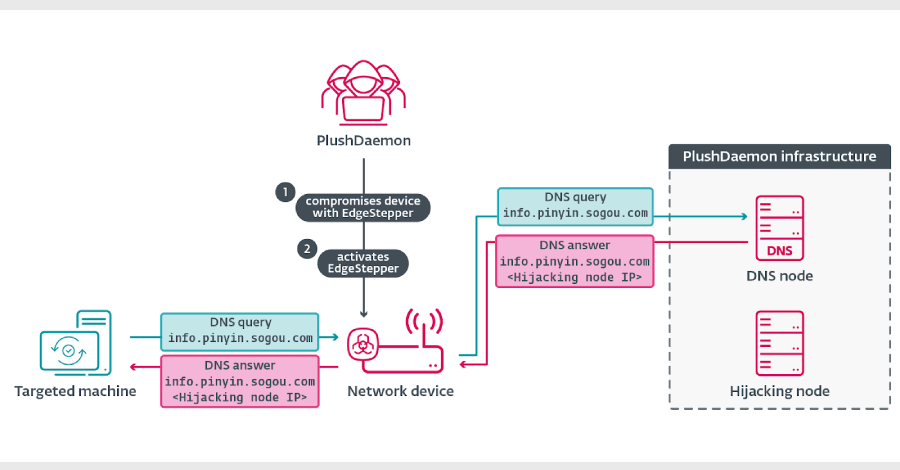
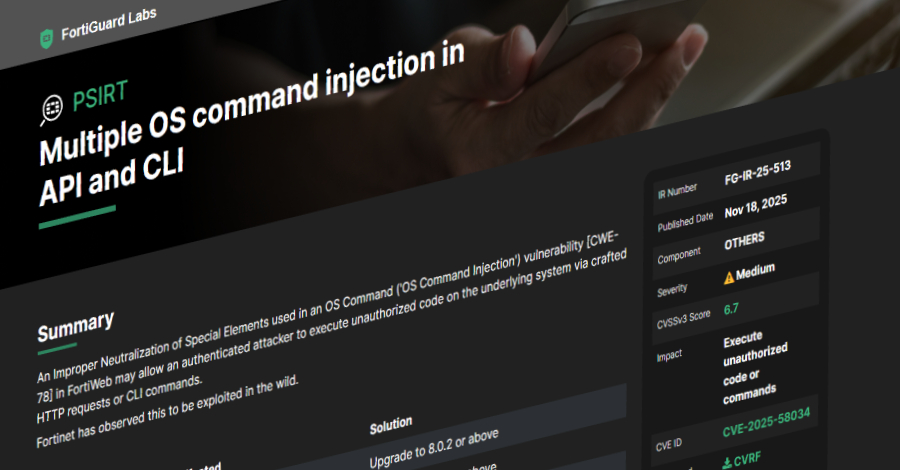
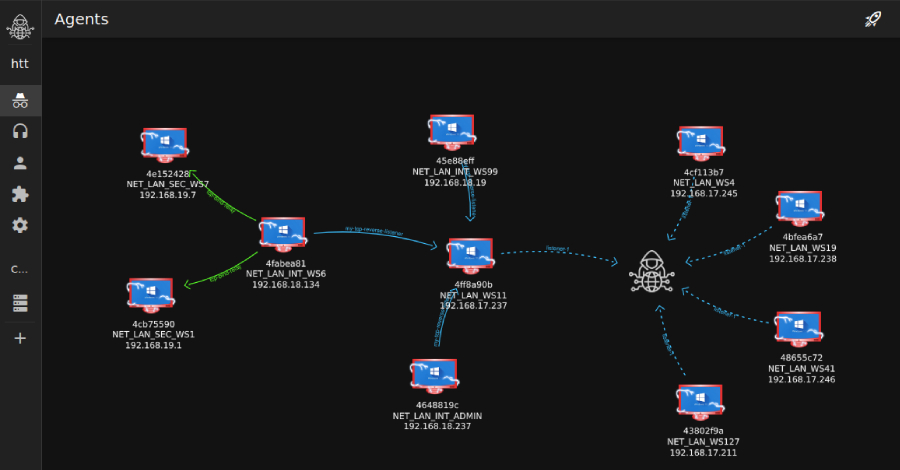
TamperedChef Malware Spreads via Fake Software Installers in Ongoing Global Campaign – The Hacker News

Threat actors are leveraging bogus installers masquerading as popular software to trick users into installing malware as part of a global malvertising campaign dubbed TamperedChef. The end goal of the attacks is to establish persistence and deliver JavaScript malware that facilitates remote access and control, per a new report from Acronis Threat Research Unit (TRU). … Read More “TamperedChef Malware Spreads via Fake Software Installers in Ongoing Global Campaign – The Hacker News” »


![[SYSS-2025-059]: Dell computer UEFI boot protection bypass – Full Disclosure](https://attackfeed.com/wp-content/uploads/2025/11/fulldisclosure-img-fDAcDK.webp)
![[REVIVE-SA-2025-003] Revive Adserver Vulnerabilities – Full Disclosure](https://attackfeed.com/wp-content/uploads/2025/11/fulldisclosure-img-hNezSQ.webp)
![[REVIVE-SA-2025-004] Revive Adserver Vulnerabilities – Full Disclosure](https://attackfeed.com/wp-content/uploads/2025/11/fulldisclosure-img-W4d2Et.webp)