Enterprise security is approaching one of the most critical periods as we approach 2026. The speeding up of digitalization,… The post Top 5 Enterprise Security Trends For 2026 appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Author: Aakash Chaudhary
Over 2,000 Fake Shopping Sites Spotted Before Cyber Monday – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

CloudSEK found over 2,000 fake sites impersonating Amazon and top brands before Cyber Monday and Black Friday. Learn the key fraud signs now to stay safe. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Quttera Launches “Evidence-as-Code” API to Automate Security Compliance for SOC 2 and PCI DSS v4.0 – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
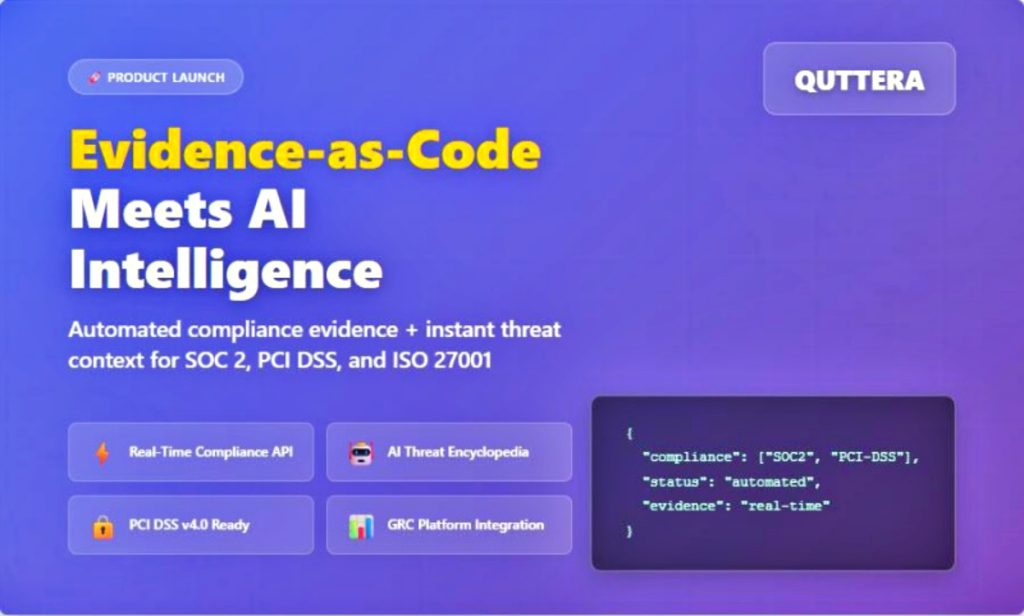
New API capabilities and AI-powered Threat Encyclopedia eliminate manual audit preparation, providing real-time compliance evidence and instant threat intelligence. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has updated its Known Exploited Vulnerabilities (KEV) catalog to include a security flaw impacting OpenPLC ScadaBR, citing evidence of active exploitation. The vulnerability in question is CVE-2021-26829 (CVSS score: 5.4), a cross-site scripting (XSS) flaw that affects Windows and Linux versions of the software via – Read … Read More “CISA Adds Actively Exploited XSS Bug CVE-2021-26829 in OpenPLC ScadaBR to KEV – The Hacker News” »
HashJack Attack Uses URL ‘#’ to Control AI Browser Behavior – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
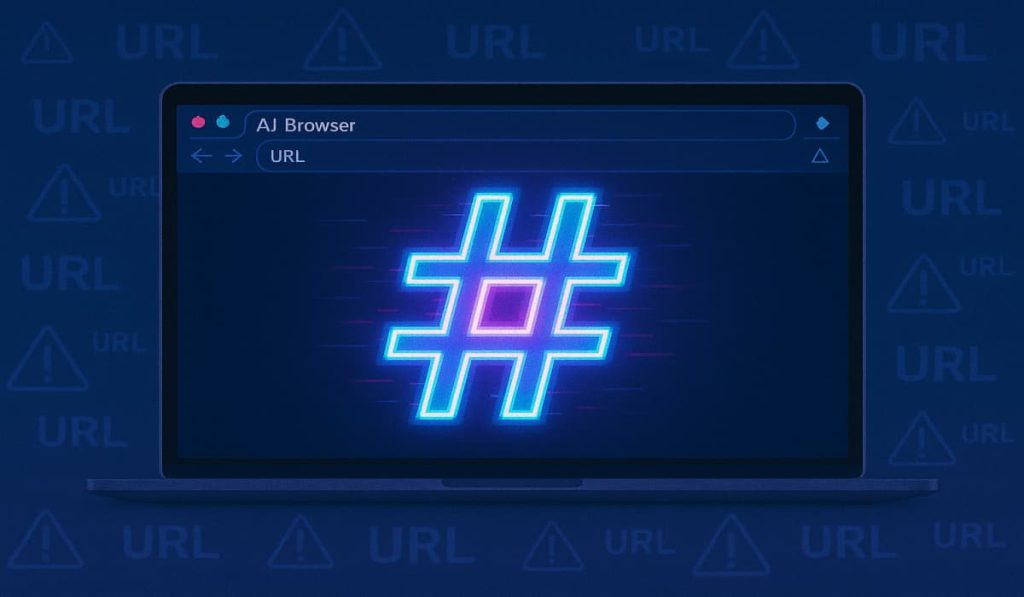
Cybersecurity firm Cato Networks reveals HashJack, a new AI browser vulnerability using the ‘#’ symbol to hide malicious commands. Microsoft and Perplexity fixed the flaw, but Google’s Gemini remains at risk. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
North Korean Hackers Deploy 197 npm Packages to Spread Updated OtterCookie Malware – The Hacker News

The North Korean threat actors behind the Contagious Interview campaign have continued to flood the npm registry with 197 more malicious packages since last month. According to Socket, these packages have been downloaded over 31,000 times, and are designed to deliver a variant of OtterCookie that brings together the features of BeaverTail and prior versions … Read More “North Korean Hackers Deploy 197 npm Packages to Spread Updated OtterCookie Malware – The Hacker News” »
Legacy Python Bootstrap Scripts Create Domain-Takeover Risk in Multiple PyPI Packages – The Hacker News
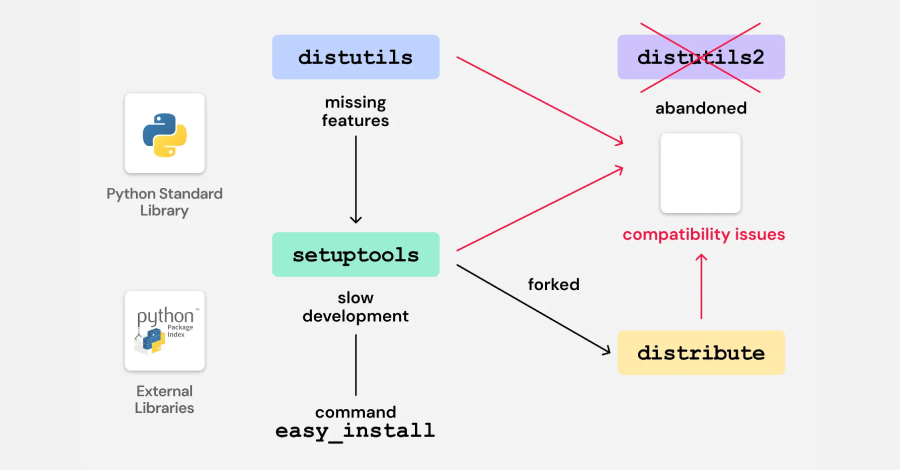
Cybersecurity researchers have discovered vulnerable code in legacy Python packages that could potentially pave the way for a supply chain compromise on the Python Package Index (PyPI) via a domain takeover attack. Software supply chain security company ReversingLabs said it found the “vulnerability” in bootstrap files provided by a build and deployment automation tool named … Read More “Legacy Python Bootstrap Scripts Create Domain-Takeover Risk in Multiple PyPI Packages – The Hacker News” »
BitSight research has revealed how threat actors exploit calendar subscriptions to deliver phishing links, malware and social engineering attacks through hijacked domains – Read More –
Darktrace observed a 620% spike in Black Friday-themed phishing in the weeks leading up to the 2025 edition of the sale day – Read More –
As IT environments become increasingly distributed and organizations adopt hybrid and remote work at scale, traditional perimeter-based security models and on-premises Privileged Access Management (PAM) solutions no longer suffice. IT administrators, contractors and third-party vendors now require secure access to critical systems from any location and on any device, without compromising – Read More – … Read More “Why Organizations Are Turning to RPAM – The Hacker News” »
The personal data of over two million amateur football players registered in France could be exposed – Read More –
MS Teams Guest Access Can Remove Defender Protection When Users Join External Tenants – The Hacker News

Cybersecurity researchers have shed light on a cross-tenant blind spot that allows attackers to bypass Microsoft Defender for Office 365 protections via the guest access feature in Teams. “When users operate as guests in another tenant, their protections are determined entirely by that hosting environment, not by their home organization,” Ontinue security researcher Rhys Downing … Read More “MS Teams Guest Access Can Remove Defender Protection When Users Join External Tenants – The Hacker News” »
The NCSC’s Cyber Action Toolkit helps you to protect your business from online attacks. – Read More – NCSC Feed
The healthcare industry is experiencing a digital revolution. Starting with telemedicine and digital prescriptions, with in-built insurance systems, healthcare… The post CryptoBind Secures the Core of National Digital Healthcare Transformation appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Bloody Wolf Expands Java-based NetSupport RAT Attacks in Kyrgyzstan and Uzbekistan – The Hacker News
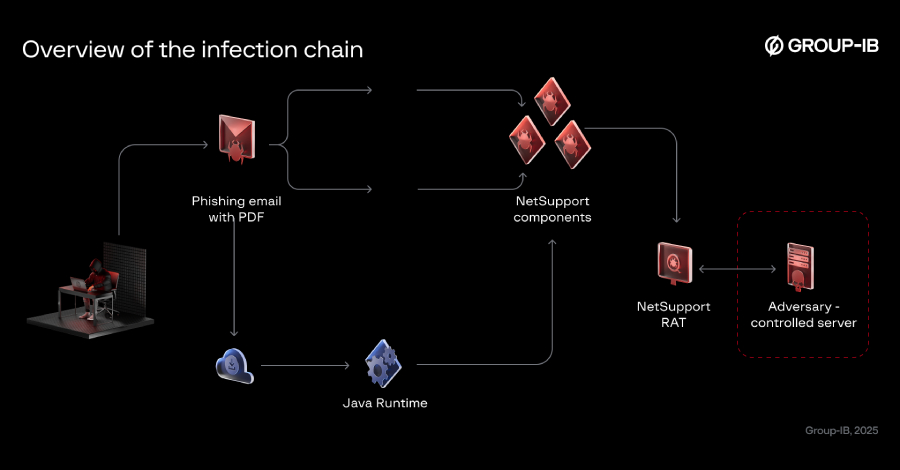
The threat actor known as Bloody Wolf has been attributed to a cyber attack campaign that has targeted Kyrgyzstan since at least June 2025 with the goal of delivering NetSupport RAT. As of October 2025, the activity has expanded to also single out Uzbekistan, Group-IB researchers Amirbek Kurbanov and Volen Kayo said in a report … Read More “Bloody Wolf Expands Java-based NetSupport RAT Attacks in Kyrgyzstan and Uzbekistan – The Hacker News” »
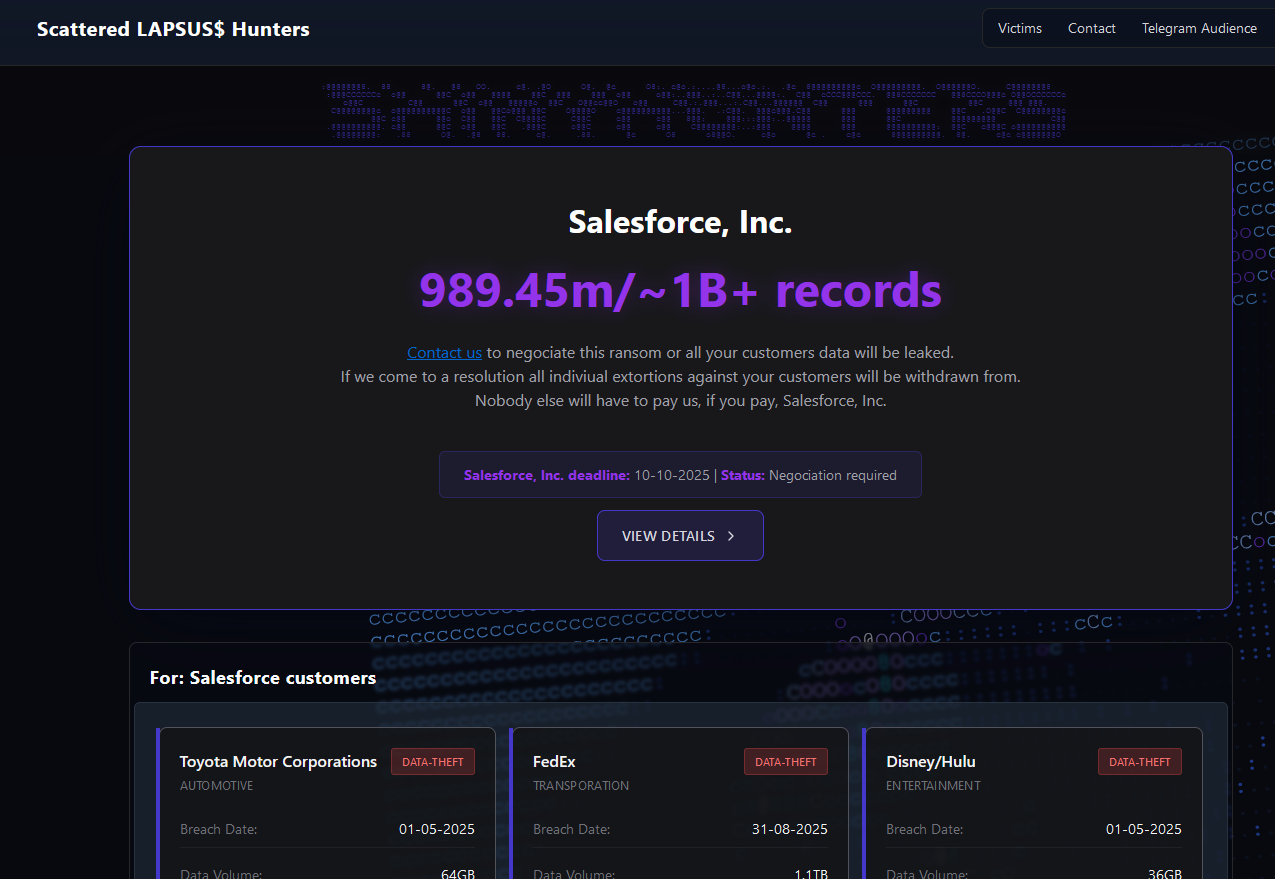
Report Names Teen in Scattered LAPSUS$ Hunters, Group Denies – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Scattered LAPSUS$ Hunters admin “Rey,” allegedly a 15-year-old named Saif Khader from Jordan, has been named in a report linking him to the group. He denies the claim. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
One Identity Safeguard Named a Visionary in the 2025 Gartner Magic Quadrant for PAM – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Alisa Viejo, CA, USA, 27th November 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Hackers have been hijacking US radio equipment to broadcast false emergency alerts, prompting FCC warnings – Read More –
A new Bloody Wolf campaign exploits legitimate remote-administration software for cyber-attacks on government targets in Central Asia – Read More –
Microsoft has announced plans to improve the security of Entra ID authentication by blocking unauthorized script injection attacks starting a year from now. The update to its Content Security Policy (CSP) aims to enhance the Entra ID sign-in experience at “login.microsoftonline[.]com” by only letting scripts from trusted Microsoft domains run. “This update strengthens security and … Read More “Microsoft to Block Unauthorized Scripts in Entra ID Logins with 2026 CSP Update – The Hacker News” »
Almost two million people may have seen their personal data exposed following a large-scale cyberattack that hit Asahi in September 2025 – Read More –
OpenAI API User Data Exposed in Mixpanel Breach, ChatGPT Unaffected – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

OpenAI confirmed a third-party data breach via Mixpanel, exposing limited API user metadata like names, emails and browser… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Cronos Kicks Off $42K Global Hackathon Focused on AI-Powered On-Chain Payments – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Cronos launches x402 PayTech Hackathon with $42K prize pool to drive AI-powered on-chain payments using agent tech and Crypto.com tools. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
The breach may have exposed OpenAI API customers’ data – Read More –
ThreatsDay Bulletin: AI Malware, Voice Bot Flaws, Crypto Laundering, IoT Attacks — and 20 More Stories – The Hacker News

Hackers have been busy again this week. From fake voice calls and AI-powered malware to huge money-laundering busts and new scams, there’s a lot happening in the cyber world. Criminals are getting creative — using smart tricks to steal data, sound real, and hide in plain sight. But they’re not the only ones moving fast. … Read More “ThreatsDay Bulletin: AI Malware, Voice Bot Flaws, Crypto Laundering, IoT Attacks — and 20 More Stories – The Hacker News” »
Analysis of ICO records shows no surge in breaches during Q4 2024 with no seasonal spike in reported incidents – Read More –
CISA, the US Cybersecurity and Infrastructure Security Agency, has issued a new warning that cybercriminals and state-backed hacking groups are using spyware to compromise smartphones belonging to users of popular encrypted messaging apps such as Signal, WhatsApp, and Telegram. Read more in my article on the Hot for Security blog. – Read More – Graham … Read More “State-backed spyware attacks are targeting Signal and WhatsApp users, CISA warns – Graham Cluley” »
New phishing domains point to a campaign from the notorious Scattered Lapsus$ Hunters collective – Read More –
OBR chair ‘mortified’ by budget leak as ex-cybersecurity chief called in to investigate – Data and computer security | The Guardian

Richard Hughes, head of Office for Budget Responsibility, says he has apologised to chancellor for ‘letting people down’ How Rachel Reeves’s budget was leaked 40 minutes early Business live – latest updates UK politics live – latest updates The chair of the Office for Budget Responsibility has said he felt “personally mortified” by the early … Read More “OBR chair ‘mortified’ by budget leak as ex-cybersecurity chief called in to investigate – Data and computer security | The Guardian” »
Shona Lester, head of the Cyber Security and Resilience Bill team within the UK government, outlined some of the provisions that should be included in the future law – Read More –
Why transferring the Commercial Product Assurance scheme to industry ownership marks an important milestone. – Read More – NCSC Feed
Gainsight has disclosed that the recent suspicious activity targeting its applications has affected more customers than previously thought. The company said Salesforce initially provided a list of 3 impacted customers and that it has “expanded to a larger list” as of November 21, 2025. It did not reveal the exact number of customers who were … Read More “Gainsight Expands Impacted Customer List Following Salesforce Security Alert – The Hacker News” »
The worldwide outlook on privacy has demonstrated unquestionable progression as we enter November, and this indicates that data security… The post November Industry Wrap-Up: Data Privacy Lessons Learned appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
America’s airwaves are haunted by zombies again, as we dig into a decade of broadcasters leaving their hardware open to attack, giving hackers the chance to hijack TV shows, blast out fake emergency alerts, and even replace religious sermons with explicit furry podcasts. Meanwhile, we look at how a worker at a cybersecurity firm allegedly … Read More “Smashing Security podcast #445: The hack that brought back the zombie apocalypse – Graham Cluley” »
Elena Lazar: Failures are Inevitable – Reliability is a Choice – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Reliability engineer on why resilience must be designed, not patched, and how decades of global experience taught her to turn outages into insights. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
OnSolve CodeRED, a voluntary, opt-in emergency notification system used by law enforcement agencies and municipalities across the country, has been permanently shut down in the wake of a ransomware attack. Crisis24, the company behind the service, said it decommissioned the platform after the cyberattack damaged the OnSolve CodeRED environment earlier this month. “Current forensic analysis … Read More “Crisis24 shuts down emergency notification system in wake of ransomware attack – CyberScoop” »
The House Homeland Security Committee is calling on Anthropic CEO Dario Amodei to provide testimony on a likely-Chinese espionage campaign that used Claude, the company’s AI tool, to automate portions of a wide-ranging cyber campaign targeting at least 30 organizations around the world. The committee sent Amodei a letter Wednesday commending Anthropic for disclosing the … Read More “Congress calls on Anthropic CEO to testify on Chinese Claude espionage campaign – CyberScoop” »
A new bipartisan bill introduced in the House would increase the criminal penalties for committing fraud and impersonation with the assistance of AI tools. The AI Fraud Deterrence Act, introduced by Reps. Ted Lieu, D-Calif., and Neal Dunn, R-Md., would raise the overall ceiling for criminal fines and prison time for fraudsters who use AI … Read More “New legislation targets scammers that use AI to deceive – CyberScoop” »
The second wave of the Shai-Hulud supply chain attack has spilled over to the Maven ecosystem after compromising more than 830 packages in the npm registry. The Socket Research Team said it identified a Maven Central package named org.mvnpm:posthog-node:4.18.1 that embeds the same two components associated with Sha1-Hulud: the “setup_bun.js” loader and the main payload … Read More “Shai-Hulud v2 Campaign Spreads From npm to Maven, Exposing Thousands of Secrets – The Hacker News” »
Microsoft Teams Flaw in Guest Chat Exposes Users to Malware Attacks – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

New research from Ontinue exposes a major security flaw in Microsoft Teams B2B Guest Access. Learn how attackers bypass all Defender for Office 365 protections with a single invite. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
AI Meeting Assistants Are Rising – But Is Your Data Safe? A Deep Look at TicNote AI – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

AI meeting assistants have become essential tools for professionals who want fast, accurate, and automated transcription. Yet behind… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Cybersecurity researchers have discovered a new malicious extension on the Chrome Web Store that’s capable of injecting a stealthy Solana transfer into a swap transaction and transferring the funds to an attacker-controlled cryptocurrency wallet. The extension, named Crypto Copilot, was first published by a user named “sjclark76” on May 7, 2024. The developer describes the … Read More “Chrome Extension Caught Injecting Hidden Solana Transfer Fees Into Raydium Swaps – The Hacker News” »
A prolific cybercriminal group that calls itself “Scattered LAPSUS$ Hunters” has dominated headlines this year by regularly stealing data from and publicly mass extorting dozens of major corporations. But the tables seem to have turned somewhat for “Rey,” the moniker chosen by the technical operator and public face of the hacker group: Earlier this week, … Read More “Meet Rey, the Admin of ‘Scattered Lapsus$ Hunters’ – Krebs on Security” »
A cyber-attack claimed to be the resposibility of INC Ransom group and targeting the OnSolve CodeRED platform has disrupted emergency notification and exposed user data across the US – Read More –
Shadow AI – the use of artificial intelligence tools by employees without a company’s approval and oversight – is becoming a significant cybersecurity risk. Read more in my article on the Fortra blog. – Read More – Graham Cluley
INE Expands Cross-Skilling Innovations – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Cary, North Carolina, USA, 26th November 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Qilin Ransomware Turns South Korean MSP Breach Into 28-Victim ‘Korean Leaks’ Data Heist – The Hacker News

South Korea’s financial sector has been targeted by what has been described as a sophisticated supply chain attack that led to the deployment of Qilin ransomware. “This operation combined the capabilities of a major Ransomware-as-a-Service (RaaS) group, Qilin, with potential involvement from North Korean state-affiliated actors (Moonstone Sleet), leveraging Managed Service Provider (MSP) – Read … Read More “Qilin Ransomware Turns South Korean MSP Breach Into 28-Victim ‘Korean Leaks’ Data Heist – The Hacker News” »
A new report from the UK Business and Trade Committee has called for accountability of software providers for cyber flaws amid rising attack costs – Read More –
The FBI reports over $262m in losses from account takeover schemes since January 2025, as cybercriminals impersonate financial institutions to steal data and funds – Read More –
Samourai Wallet Founders Jailed in $237M Crypto Laundering Case – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Samourai Wallet founders Keonne Rodriguez and William Hill were sentenced to 4 and 5 years for laundering $237M via their crypto mixer. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More