Trends toward a digital-first enterprise have already entered watershed data privacy and security in 2026. New regulation, technology and… The post Looking Ahead: 2026 Privacy & Security Trends appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Author: Aakash Chaudhary
In episode 79 of The AI Fix, Gemini 3 roasts the competition, scares Nvidia, and can’t remember what year it is. Meanwhile, Graham investigates a fight between a fridge and robot, and Mark discovers that poetry could be a universal jailbreak for LLMs. Also in this episode, our hosts ponder whether Mark Zuckerberg’s underground bunker … Read More “The AI Fix #79: Gemini 3, poetry jailbreaks, and do we even need safe robots? – Graham Cluley” »
Asahi cyber attack spirals into massive data breach impacting almost 2 million people – Graham Cluley

Asahi Group Holdings, the makers of the popular Japanese beer Asahi Super Dry, has confirmed that the ransomware attack that disrupted its operations in late September also saw a significant data breach that affects more than 1.5 million customers and approximately 275,000 current and former employees and their families. Read more in my article on … Read More “Asahi cyber attack spirals into massive data breach impacting almost 2 million people – Graham Cluley” »
When news broke approximately a year ago that Chinese hackers had systemically penetrated at least nine major U.S. communications networks, the level of alarm from policymakers was clear. At a hearing held Tuesday by the Senate Committee on Commerce, experts offered differing assessments of the threat. While intelligence officials have characterized the Salt Typhoon operation’s … Read More “The Congressional remedy for Salt Typhoon? More information sharing with industry – CyberScoop” »
Everest Ransomware Claims ASUS Breach and 1TB Data Theft – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Everest ransomware group claims it breached ASUS, stealing over 1TB of data including camera source code. ASUS has been given 21 hours to respond via Qtox. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Legislation would designate ‘critical cyber threat actors,’ direct sanctions against them – CyberScoop

A House Republican introduced legislation Tuesday aimed at deterring cyberattacks against the United States at a time when the Trump administration is prioritizing the punishment of malicious hackers. Rep. August Pfluger, R-Texas, revived legislation he first sponsored in 2022, the Cyber Deterrence and Response Act. The legislation would direct the executive branch to formally designate … Read More “Legislation would designate ‘critical cyber threat actors,’ direct sanctions against them – CyberScoop” »
University of Pennsylvania joins growing pool of Oracle customers impacted by Clop attacks – CyberScoop

The University of Pennsylvania joined the steadily growing number of victim organizations impacted by the widespread data theft and extortion campaign involving a notorious ransomware group’s exploitation of a zero-day vulnerability and other defects in Oracle E-Business Suite earlier this year. The university filed a data breach notification in Maine Monday, confirming nearly 1,500 Maine … Read More “University of Pennsylvania joins growing pool of Oracle customers impacted by Clop attacks – CyberScoop” »
India Orders Messaging Apps to Work Only With Active SIM Cards to Prevent Fraud and Misuse – The Hacker News

India’s Department of Telecommunications (DoT) has issued directions to app-based communication service providers to ensure that the platforms cannot be used without an active SIM card linked to the user’s mobile number. To that end, messaging apps like WhatsApp, Telegram, Snapchat, Arattai, Sharechat, Josh, JioChat, and Signal that use an Indian mobile number for uniquely … Read More “India Orders Messaging Apps to Work Only With Active SIM Cards to Prevent Fraud and Misuse – The Hacker News” »
NK Hackers Push 200 Malicious npm Packages with OtterCookie Malware – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

North Korean hackers escalated the “Contagious Interview” attack, flooding the npm registry with over 200 malicious packages to install OtterCookie malware. This attack targets blockchain and Web3 developers through fake job interviews and coding tests. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
3 critical zero-day flaws in PickleScan, affecting Python and PyTorch, allowed undetected attacks – Read More –
Cybersecurity researchers have disclosed details of an npm package that attempts to influence artificial intelligence (AI)-driven security scanners. The package in question is eslint-plugin-unicorn-ts-2, which masquerades as a TypeScript extension of the popular ESLint plugin. It was uploaded to the registry by a user named “hamburgerisland” in February 2024. The package has been downloaded – … Read More “Malicious npm Package Uses Hidden Prompt and Script to Evade AI Security Tools – The Hacker News” »
GlassWorm Returns with 24 Malicious Extensions Impersonating Popular Developer Tools – The Hacker News

The supply chain campaign known as GlassWorm has once again reared its head, infiltrating both Microsoft Visual Studio Marketplace and Open VSX with 24 extensions impersonating popular developer tools and frameworks like Flutter, React, Tailwind, Vim, and Vue. GlassWorm was first documented in October 2025, detailing its use of the Solana blockchain for command-and-control (C2) … Read More “GlassWorm Returns with 24 Malicious Extensions Impersonating Popular Developer Tools – The Hacker News” »
A joint investigation led by Mauro Eldritch, founder of BCA LTD, conducted together with threat-intel initiative NorthScan and ANY.RUN, a solution for interactive malware analysis and threat intelligence, has uncovered one of North Korea’s most persistent infiltration schemes: a network of remote IT workers tied to Lazarus Group’s Famous Chollima division. For the first time, … Read More “Researchers Capture Lazarus APT’s Remote-Worker Scheme Live on Camera – The Hacker News” »
Infected 4.3 million Chrome and Edge users via extensions; ShadyPanda exploited browser marketplaces – Read More –
Iran-Linked Hackers Hits Israeli Sectors with New MuddyViper Backdoor in Targeted Attacks – The Hacker News

Israeli entities spanning academia, engineering, local government, manufacturing, technology, transportation, and utilities sectors have emerged as the target of a new set of attacks undertaken by Iranian nation-state actors that have delivered a previously undocumented backdoor called MuddyViper. The activity has been attributed by ESET to a hacking group known as MuddyWater (aka Mango – … Read More “Iran-Linked Hackers Hits Israeli Sectors with New MuddyViper Backdoor in Targeted Attacks – The Hacker News” »
Cyber Startup Frenetik Launches with Patented Deception Technology That Bets Against the AI Arms Race – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Bethesda, USA / Maryland, 2nd December 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Proxyearth Tool Lets Anyone Trace Users in India with Just a Mobile Number – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
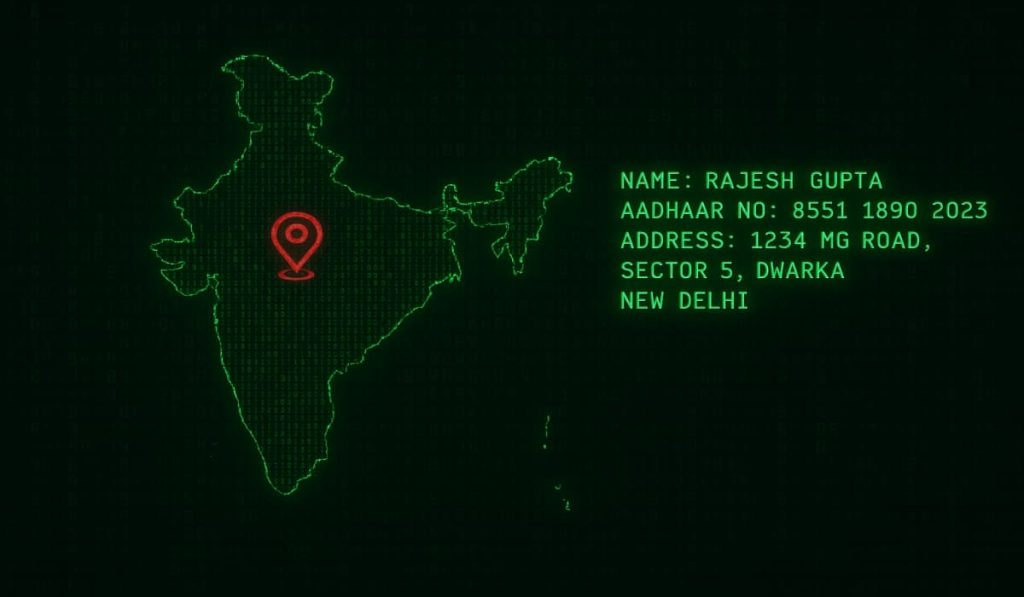
Proxyearth is a new site that shows names, Aadhaar numbers, and live locations of users in India using only mobile numbers, raising serious privacy and security concerns. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
AI Adoption Surges While Governance Lags — Report Warns of Growing Shadow Identity Risk – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Baltimore, MD, 2nd December 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
SecAlerts Cuts Through the Noise with a Smarter, Faster Way to Track Vulnerabilities – The Hacker News
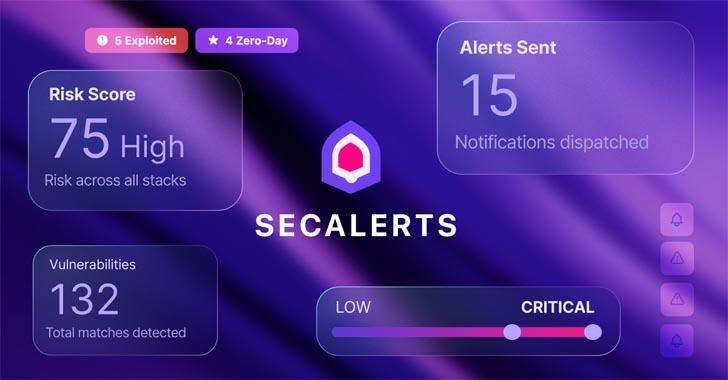
Vulnerability management is a core component of every cybersecurity strategy. However, businesses often use thousands of software without realising it (when was the last time you checked?), and keeping track of all the vulnerability alerts, notifications, and updates can be a burden on resources and often leads to missed vulnerabilities. Taking into account that nearly … Read More “SecAlerts Cuts Through the Noise with a Smarter, Faster Way to Track Vulnerabilities – The Hacker News” »
Google said it found indications that two newly identified vulnerabilities affecting Android “may be under limited, targeted exploitation” – Read More –
The UK Information Commissioner’s Office has launched an investigation into the mobile gaming sector – Read More –
New IO study claims 88% of US and UK firms are concerned about state-sponsored cyber-attacks – Read More –
What makes a responsible cyber actor: introducing the Pall Mall industry consultation on good practice – NCSC Feed

Calling vulnerability researchers, exploit developers and others in the offensive cyber industry to share their views. – Read More – NCSC Feed
Google Patches 107 Android Flaws, Including Two Framework Bugs Exploited in the Wild – The Hacker News

Google on Monday released monthly security updates for the Android operating system, including two vulnerabilities that it said have been exploited in the wild. The patch addresses a total of 107 security flaws spanning different components, including Framework, System, Kernel, as well as those from Arm, Imagination Technologies, MediaTek, Qualcomm, and Unison. The two high-severity … Read More “Google Patches 107 Android Flaws, Including Two Framework Bugs Exploited in the Wild – The Hacker News” »
Sonesta International Hotels Implements Industry-Leading Cloud Security Through AccuKnox Collaboration – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Menlo Park, USA, 2nd December 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Posted by Aerith Gainsborough via Fulldisclosure on Dec 01 Advisory ID: LEGALITYWHISTLEBLOWING-2025-001 Title: Missing Critical Security Headers in Legality WHISTLEBLOWING Date: 2025-11-29 Vendor: DigitalPA (segnalazioni.net) Severity: High CVSS v3.1 Base Score: 8.2 (High) Vector: AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:L/A:N Summary: Multiple public deployments of Legality WHISTLEBLOWING by DigitalPA are missing essential HTTP security headers. This misconfiguration exposes users … Read More “Missing Critical Security Headers in Legality WHISTLEBLOWING – Full Disclosure” »
Posted by Matteo Beccati on Dec 01 ======================================================================== Revive Adserver Security Advisory REVIVE-SA-2025-005 ———————————————————————— https://www.revive-adserver.com/security/revive-sa-2025-005 ———————————————————————— Date: 2025-11-26 Risk Level: Medium Applications affected: Revive… – Read More – Full Disclosure
Posted by Pierre Kim on Dec 01 ## Advisory Information Title: 2 vulnerabilities in Egovframe Advisory URL: https://pierrekim.github.io/advisories/2025-egovframe.txt Blog URL: https://pierrekim.github.io/blog/2025-11-20-egovframe-2-vulnerabilities.html Date published: 2025-11-20 Vendors contacted: KISA/KrCERT Release mode: Released CVE: CVE-2025-34336, CVE-2025-34337 ## Product description Egovframe is a Java-based framework mainly used in the websites of the Government of… – Read More – Full … Read More “2 vulnerabilities in Egovframe – Full Disclosure” »
Posted by Pierre Kim on Dec 01 ## Advisory Information Title: 8 vulnerabilities in AudioCodes Fax/IVR Appliance Advisory URL: https://pierrekim.github.io/advisories/2025-audiocodes-fax-ivr.txt Blog URL: https://pierrekim.github.io/blog/2025-11-20-audiocodes-fax-ivr-8-vulnerabilities.html Date published: 2025-11-20 Vendors contacted: Audiocodes Release mode: Released CVE: CVE-2025-34328, CVE-2025-34329, CVE-2025-34330, CVE-2025-34331, CVE-2025-34332, CVE-2025-34333,… – Read More – Full Disclosure
The principle of consent and data subject rights has evolved to be treated as a compliance checkbox to form… The post The New Standard: Consent & Data Subject Rights under UAE and GCC Laws appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
Google disclosed two actively exploited zero-day vulnerabilities Monday, which it addressed among a total of 107 defects in the company’s monthly security update for Android devices. The zero-days — CVE-2025-48633 and CVE-2025-48572 — are both high-severity defects affecting the Android framework, which attackers can exploit to access information and escalate privileges, respectively. Google said both … Read More “Google addresses 107 Android vulnerabilities, including two zero-days – CyberScoop” »
BreachLock Named a Leader in 2025 GigaOm Radar Report for Penetration Testing as a Service (PTaaS) for Third Consecutive Year – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
New York, New York, 1st December 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
European authorities shut down and seized the assets of Cryptomixer, a cryptocurrency mixing service that allegedly facilitated more than $1.5 billion in money laundering for cybercriminals and other illegal activity, Europol said Monday. The weeklong operation, part of “Operation Olympia,” netted the seizure of nearly $28 million in Bitcoin, three servers in Switzerland, the cryptomixer.io … Read More “Authorities take down Cryptomixer, seize $28M in Switzerland – CyberScoop” »
Coupang Data Breach Affects All 33.7 Million South Korean Accounts – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Coupang confirms a data breach affecting 33.7 million users in South Korea, exposing names, contacts and order details. Investigation is ongoing. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
ShadyPanda Turns Popular Browser Extensions with 4.3 Million Installs Into Spyware – The Hacker News

A threat actor known as ShadyPanda has been linked to a seven-year-long browser extension campaign that has amassed over 4.3 million installations over time. Five of these extensions started off as legitimate programs before malicious changes were introduced in mid-2024, according to a report from Koi Security, attracting 300,000 installs. These extensions have since been … Read More “ShadyPanda Turns Popular Browser Extensions with 4.3 Million Installs Into Spyware – The Hacker News” »
India Orders Phone Makers to Pre-Install Sanchar Saathi App to Tackle Telecom Fraud – The Hacker News

India’s telecommunications ministry has reportedly asked major mobile device manufacturers to preload a government-backed cybersecurity app named Sanchar Saathi on all new phones within 90 days. According to a report from Reuters, the app cannot be deleted or disabled from users’ devices. Sanchar Saathi, available on the web and via mobile apps for Android and … Read More “India Orders Phone Makers to Pre-Install Sanchar Saathi App to Tackle Telecom Fraud – The Hacker News” »
Police Seize Cryptomixer Domains, Infrastructure and 28M Dollars in Bitcoin – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

Swiss and German police shut down Cryptomixer, seizing servers, domains and 28M dollars in Bitcoin during an Europol backed action targeting crypto laundering. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Android malware Albiriox emerged as MaaS, offering device takeover and real-time fraud capabilities – Read More –
What a Secure Setup Really Looks Like for Storing Digital Assets – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

How you choose to store your assets is one of the most important decisions you’ll make when you… – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
The South Korean police are tracking the suspect behind a cyber-attack targeting e-commerce giant Coupang – Read More –
Malicious npm package targets AI security with misleading prompts, exploiting automated analysis – Read More –
Evil Twin Wi‑Fi Hacker Jailed for Stealing Data Mid‑Flight – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More

An Australian man who used fake “evil‑twin” Wi‑Fi networks at airports and on flights to steal travellers’ data has been jailed for 7 years and 4 months. – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Hackers aren’t kicking down the door anymore. They just use the same tools we use every day — code packages, cloud accounts, email, chat, phones, and “trusted” partners — and turn them against us. One bad download can leak your keys. One weak vendor can expose many customers at once. One guest invite, one link … Read More “⚡ Weekly Recap: Hot CVEs, npm Worm Returns, Firefox RCE, M365 Email Raid & More – The Hacker News” »
November 2025 saw cybersecurity giants like Palo Alto Networks, Bugcrowd and Zscaler invest in AI-powered security solutions – Read More –
Webinar: The “Agentic” Trojan Horse: Why the New AI Browsers War is a Nightmare for Security Teams – The Hacker News

The AI browser wars are coming to a desktop near you, and you need to start worrying about their security challenges. For the last two decades, whether you used Chrome, Edge, or Firefox, the fundamental paradigm remained the same: a passive window through which a human user viewed and interacted with the internet. That era … Read More “Webinar: The “Agentic” Trojan Horse: Why the New AI Browsers War is a Nightmare for Security Teams – The Hacker News” »
Europol, alongside Swiss and German authorities, dismantled the illegal cryptocurrency mixing service ‘Cryptomixer’ – Read More –
A Western Australia man will spend seven years behind bars after stealing intimate data via Wi-Fi – Read More –
At least one London council has had data compromised after a suspected ransomware attack last week – Read More –
New Albiriox MaaS Malware Targets 400+ Apps for On-Device Fraud and Screen Control – The Hacker News

A new Android malware named Albiriox has been advertised under a malware-as-a-service (MaaS) model to offer a “full spectrum” of features to facilitate on-device fraud (ODF), screen manipulation, and real-time interaction with infected devices. The malware embeds a hard-coded list comprising over 400 applications spanning banking, financial technology, payment processors, cryptocurrency – Read More – … Read More “New Albiriox MaaS Malware Targets 400+ Apps for On-Device Fraud and Screen Control – The Hacker News” »
Kevin Lancaster Joins the usecure Board to Accelerate North American Channel Growth – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Claymont, Delaware, 1st December 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More











![[REVIVE-SA-2025-005] Revive Adserver Vulnerability – Full Disclosure](https://attackfeed.com/wp-content/uploads/2025/12/fulldisclosure-img-DH6wBM.webp)












