UK Data Protection Watchdog has “serious concerns” over data privacy on Elon Musk’s social platform – Read More –
Author: Joe-W
DockerDash vulnerability allows RCE and data exfiltration via unverified metadata in Ask Gordon – Read More –
Threat actors have been observed exploiting a critical security flaw impacting the Metro Development Server in the popular “@react-native-community/cli” npm package. Cybersecurity company VulnCheck said it first observed exploitation of CVE-2025-11953 (aka Metro4Shell) on December 21, 2025. With a CVSS score of 9.8, the vulnerability allows remote unauthenticated attackers to execute arbitrary – Read More … Read More “Hackers Exploit Metro4Shell RCE Flaw in React Native CLI npm Package – The Hacker News” »
Most security teams today are buried under tools. Too many dashboards. Too much noise. Not enough real progress. Every vendor promises “complete coverage” or “AI-powered automation,” but inside most SOCs, teams are still overwhelmed, stretched thin, and unsure which tools are truly pulling their weight. The result? Bloated stacks, missed signals, and mounting pressure to … Read More “[Webinar] The Smarter SOC Blueprint: Learn What to Build, Buy, and Automate – The Hacker News” »
A new ransomware-as-a-service operation dubbed “Vect” features custom malware – Read More –
Elon Musk and X’s former CEO were summoned for voluntary interviews in Paris on April 20, 2026 – Read More –
Recent major cloud service outages have been hard to miss. High-profile incidents affecting providers such as AWS, Azure, and Cloudflare have disrupted large parts of the internet, taking down websites and services that many other systems depend on. The resulting ripple effects have halted applications and workflows that many organizations rely on every day. For … Read More “When Cloud Outages Ripple Across the Internet – The Hacker News” »
Everest Ransomware Claims 90GB Data Theft Involving Legacy Polycom Systems – Hackread – Cybersecurity News, Data Breaches, AI, and More

Everest ransomware claims a breach involving legacy Polycom systems later acquired by HP Inc., alleging the theft of 90GB of internal data. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Multi-stage attack begins with fake message relating to business requests and evades detection with link hidden in a PDF – Read More –
Wiz Security claims Moltbook misconfiguration allowed full read and write access – Read More –
The Russia-linked state-sponsored threat actor known as APT28 (aka UAC-0001) has been attributed to attacks exploiting a newly disclosed security flaw in Microsoft Office as part of a campaign codenamed Operation Neusploit. Zscaler ThreatLabz said it observed the hacking group weaponizing the shortcoming on January 29, 2026, in attacks targeting users in Ukraine, Slovakia, and … Read More “APT28 Uses Microsoft Office CVE-2026-21509 in Espionage-Focused Malware Attacks – The Hacker News” »
CSPM tools are big business. Could they be the answer to your cloud configuration problems? – Read More – NCSC Feed
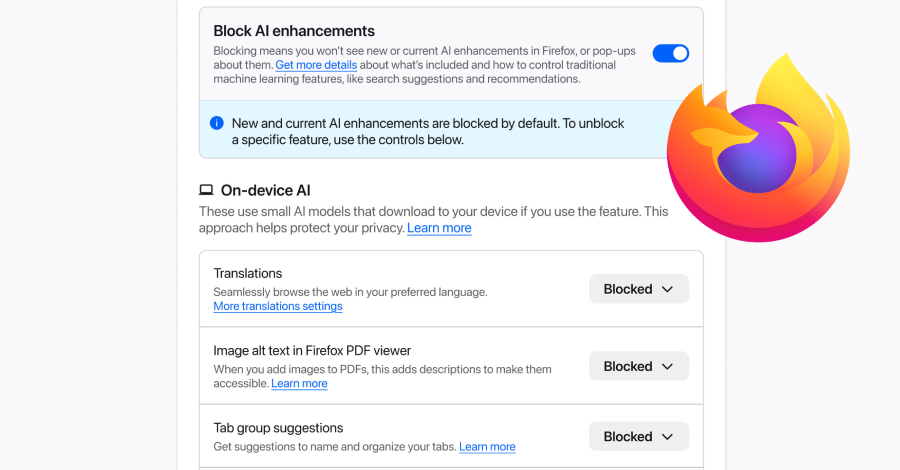
Mozilla on Monday announced a new controls section in its Firefox desktop browser settings that allows users to completely turn off generative artificial intelligence (GenAI) features. “It provides a single place to block current and future generative AI features in Firefox,” Ajit Varma, head of Firefox, said. “You can also review and manage individual AI … Read More “Mozilla Adds One-Click Option to Disable Generative AI Features in Firefox – The Hacker News” »
A China-linked threat actor known as Lotus Blossom has been attributed with medium confidence to the recently discovered compromise of the infrastructure hosting Notepad++. The attack enabled the state-sponsored hacking group to deliver a previously undocumented backdoor codenamed Chrysalis to users of the open-source editor, according to new findings from Rapid7. The development comes shortly … Read More “Notepad++ Hosting Breach Attributed to China-Linked Lotus Blossom Hacking Group – The Hacker News” »
The Digital Personal Data Protection (DPDP) Act of India is one of the most significant regulatory changes in the… The post 90-Day DPDP Readiness Plan for Indian Enterprises appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
It’s no secret that the Trump administration has radically altered the federal government’s relationship with state election officials since being sworn into power last year. While his first term included the creation of the Cybersecurity and Infrastructure Security Agency and the distribution of hundreds of millions in congressional funding sent to help states upgrade election … Read More “As feds pull back, states look inward for election security support – CyberScoop” »
Phishing Scam Uses Clean Emails and PDFs to Steal Dropbox Logins – Hackread – Cybersecurity News, Data Breaches, AI, and More

A multi-stage phishing campaign is targeting business users by exploiting Vercel cloud storage, PDF attachments, and Telegram bots to steal Dropbox credentials. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A China-based threat group operating for almost two decades broke into the internal systems of Notepad++, an extremely popular open source-code editor, to spy on a select group of targeted users, researchers at Rapid7 said Monday. Don Ho, the author and maintainer of the open-source tool, said independent security researchers confirmed a China state-sponsored group … Read More “China-based espionage group compromised Notepad++ for six months – CyberScoop” »
A security audit of 2,857 skills on ClawHub has found 341 malicious skills across multiple campaigns, according to new findings from Koi Security, exposing users to new supply chain risks. ClawHub is a marketplace designed to make it easy for OpenClaw users to find and install third-party skills. It’s an extension to the OpenClaw project, … Read More “Researchers Find 341 Malicious ClawHub Skills Stealing Data from OpenClaw Users – The Hacker News” »
Notepad++ Updates Delivered Malware After Hosting Provider Breach – Hackread – Cybersecurity News, Data Breaches, AI, and More

A months-long breach allowed Chinese State-sponsored hackers to hijack Notepad++ updates in 2025, exposing users to malware via a compromised hosting provider. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A high-severity security flaw has been disclosed in OpenClaw (formerly referred to as Clawdbot and Moltbot) that could allow remote code execution (RCE) through a crafted malicious link. The issue, which is tracked as CVE-2026-25253 (CVSS score: 8.8), has been addressed in version 2026.1.29 released on January 30, 2026. It has been described as a … Read More “OpenClaw Bug Enables One-Click Remote Code Execution via Malicious Link – The Hacker News” »
Microsoft has announced a three-phase approach to phase out New Technology LAN Manager (NTLM) as part of its efforts to shift Windows environments toward stronger, Kerberos-based options. The development comes more than two years after the tech giant revealed its plans to deprecate the legacy technology, citing its susceptibility to weaknesses that could facilitate relay … Read More “Microsoft Begins NTLM Phase-Out With Three-Stage Plan to Move Windows to Kerberos – The Hacker News” »
A prolific data ransom gang that calls itself Scattered Lapsus Shiny Hunters (SLSH) has a distinctive playbook when it seeks to extort payment from victim firms: Harassing, threatening and even swatting executives and their families, all while notifying journalists and regulators about the extent of the intrusion. Some victims reportedly are paying — perhaps as … Read More “Please Don’t Feed the Scattered Lapsus Shiny Hunters – Krebs on Security” »
NSA released new guidelines to help organizations achieve target-level Zero Trust maturity – Read More –
Spotify and Major Music Labels Sue Anna’s Archive for $13 Trillion – Hackread – Cybersecurity News, Data Breaches, AI, and More

Spotify and the Big Three labels have filed a record-breaking $13 trillion lawsuit against Anna’s Archive over a massive music data scrape. Find out what this means for the future of digital music. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Ivanti Issues Urgent Fix for Critical Zero-Day Flaws Under Active Attack – Hackread – Cybersecurity News, Data Breaches, AI, and More

Ivanti has disclosed two critical remote code execution (RCE) flaws (CVE-2026-1281 & CVE-2026-1340) in its EPMM software. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A supply chain attack on Notepad++ update process was linked to compromised hosting infrastructure – Read More –
For mid-market organizations, cybersecurity is a constant balancing act. Proactive, preventative security measures are essential to protect an expanding attack surface. Combined with effective protection that blocks threats, they play a critical role in stopping cyberattacks before damage is done. The challenge is that many security tools add complexity and cost that most mid-market businesses … Read More “Securing the Mid-Market Across the Complete Threat Lifecycle – The Hacker News” »
⚡ Weekly Recap: Proxy Botnet, Office Zero-Day, MongoDB Ransoms, AI Hijacks & New Threats – The Hacker News

Every week brings new discoveries, attacks, and defenses that shape the state of cybersecurity. Some threats are stopped quickly, while others go unseen until they cause real damage. Sometimes a single update, exploit, or mistake changes how we think about risk and protection. Every incident shows how defenders adapt — and how fast attackers try … Read More “⚡ Weekly Recap: Proxy Botnet, Office Zero-Day, MongoDB Ransoms, AI Hijacks & New Threats – The Hacker News” »
Russia-linked hacking group Fancy Bear is exploiting a brand-new vulnerability in Microsoft Office, CERT-UA says – Read More –
The phrase “Move fast and break things” is a guiding philosophy in the technology industry. The phrase was coined by Meta CEO and founder Mark Zuckerberg more than two decades ago: an operational directive for Facebook developers to prioritize speed and innovation even at the cost of stability. “Unless you are breaking stuff,” Zuckerberg told … Read More “We moved fast and broke things. It’s time for a change. – CyberScoop” »
Bitdefender has discovered a new Android malware campaign that uses Hugging Face – Read More –
The maintainer of Notepad++ has revealed that state-sponsored attackers hijacked the utility’s update mechanism to redirect update traffic to malicious servers instead. “The attack involved [an] infrastructure-level compromise that allowed malicious actors to intercept and redirect update traffic destined for notepad-plus-plus.org,” developer Don Ho said. “The compromise occurred at the hosting – Read More – … Read More “Notepad++ Official Update Mechanism Hijacked to Deliver Malware to Select Users – The Hacker News” »
Linwei Ding, a former Google engineer, has been found guilty of stealing trade secrets for China – Read More –
The update infrastructure for eScan antivirus, a security solution developed by Indian cybersecurity company MicroWorld Technologies, has been compromised by unknown attackers to deliver a persistent downloader to enterprise and consumer systems. “Malicious updates were distributed through eScan’s legitimate update infrastructure, resulting in the deployment of multi-stage malware to enterprise – Read More – The … Read More “eScan Antivirus Update Servers Compromised to Deliver Multi-Stage Malware – The Hacker News” »
Cybersecurity researchers have disclosed details of a supply chain attack targeting the Open VSX Registry in which unidentified threat actors compromised a legitimate developer’s resources to push malicious updates to downstream users. “On January 30, 2026, four established Open VSX extensions published by the oorzc author had malicious versions published to Open VSX that embed … Read More “Open VSX Supply Chain Attack Used Compromised Dev Account to Spread GlassWorm – The Hacker News” »
Why should renters like me have to trade away our privacy just to get a roof over our heads? | Samantha Floreani – Data and computer security | The Guardian

The rise in real estate tech means renters often hand over huge amounts of revealing information to digital third parties – at great risk Get our breaking news email, free app or daily news podcast Would you trade your data privacy and security for housing? Thanks to the rise in real estate technologies, renters often … Read More “Why should renters like me have to trade away our privacy just to get a roof over our heads? | Samantha Floreani – Data and computer security | The Guardian” »
Real estate agents in Australia using apps that leave millions of lease documents at risk, digital researcher says – Data and computer security | The Guardian

‘This is a blatant and disturbing disregard for the law and for people’s security,’ digital rights advocate says Get our breaking news email, free app or daily news podcast Australian platforms used by real estate agents to upload documentation for renters and landlords are leaving people’s personal information exposed in hyperlinks accessible online. An analysis … Read More “Real estate agents in Australia using apps that leave millions of lease documents at risk, digital researcher says – Data and computer security | The Guardian” »
Ransomware victims surged in Q4 2025 despite fewer active extortion groups, with data leaks rising 50%, ReliaQuest researchers report – Read More –
Ransomware victims surged in Q4 2025 despite fewer active extortion groups, with data leaks rising 50%, ReliaQuest researchers report – Read More –
US Seizes $400 Million Linked to Helix Dark Web Crypto Mixer – Hackread – Cybersecurity News, Data Breaches, AI, and More

US authorities take control of over $400 million in crypto, cash, and property tied to Helix, a major darknet bitcoin mixing service used by drug markets. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Windows Malware Uses Pulsar RAT for Live Chats While Stealing Data – Hackread – Cybersecurity News, Data Breaches, AI, and More
We usually think of computer viruses as silent, invisible programs running in the background, but a worrying discovery shows that modern hackers are getting much more personal. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Juice Jacking Continues to Be a Cyber Problem in South Africa – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.

“Juice jacking” may be a new term for some, but it has been around as a method of cyber attack for a long time. The former problem was that it was expensive to install, but now that has all changed. The tools required for juice jacking have become cheaper and easier and it’s now a … Read More “Juice Jacking Continues to Be a Cyber Problem in South Africa – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.” »
A Farsi-speaking threat actor aligned with Iranian state interests is suspected to be behind a new campaign targeting non-governmental organizations and individuals involved in documenting recent human rights abuses. The activity, observed by HarfangLab in January 2026, has been codenamed RedKitten. It’s said to coincide with the nationwide unrest in Iran that began towards the … Read More “Iran-Linked RedKitten Cyber Campaign Targets Human Rights NGOs and Activists – The Hacker News” »
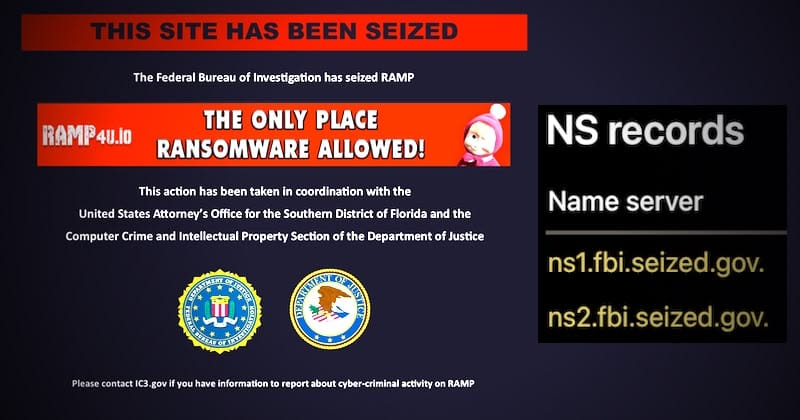
The FBI has seized control of RAMP, a notorious cybercrime online forum that bragged to be the only place that allowed ransomware, and boasted over 14,000 active users. Now some of those users’ details are likely to be in the hands of the police… Read more in my article on the Bitdefender blog. – Read … Read More “FBI takes notorious RAMP ransomware forum offline – GRAHAM CLULEY” »
Former Google Engineer Convicted of Stealing AI Secrets for China – Hackread – Cybersecurity News, Data Breaches, AI, and More

A 38 year old was convicted on seven counts of economic espionage and seven counts of theft of trade secrets following an 11 day trial. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Mandiant Finds ShinyHunters-Style Vishing Attacks Stealing MFA to Breach SaaS Platforms – The Hacker News

Google-owned Mandiant on Friday said it identified an “expansion in threat activity” that uses tradecraft consistent with extortion-themed attacks orchestrated by a financially motivated hacking group known as ShinyHunters. The attacks leverage advanced voice phishing (aka vishing) and bogus credential harvesting sites mimicking targeted companies to gain unauthorized access to victim – Read More – … Read More “Mandiant Finds ShinyHunters-Style Vishing Attacks Stealing MFA to Breach SaaS Platforms – The Hacker News” »
CERT Polska, the Polish computer emergency response team, revealed that coordinated cyber attacks targeted more than 30 wind and photovoltaic farms, a private company from the manufacturing sector, and a large combined heat and power plant (CHP) supplying heat to almost half a million customers in the country. The incident took place on December 29, … Read More “CERT Polska Details Coordinated Cyber Attacks on 30+ Wind and Solar Farms – The Hacker News” »
A trio of domains that allegedly distributed pirated content, including movies, TV shows, video games and other content was seized by the U.S. government as part of a globally coordinated crackdown on copyright infringement, the Justice Department said Friday. The sites — zamunda.net, arenabg.com and zelka.org — were among the most popular domains in Bulgaria … Read More “DOJ seizes piracy sites, Italian police dismantle illegal IPTV operation – CyberScoop” »
Arsink Spyware Posing as WhatsApp, YouTube, Instagram, TikTok Hits 143 Countries – Hackread – Cybersecurity News, Data Breaches, AI, and More

Another day, another Android malware campaign targeting unsuspecting users worldwide by masquerading as popular apps. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More



![[Webinar] The Smarter SOC Blueprint: Learn What to Build, Buy, and Automate – The Hacker News](https://attackfeed.com/wp-content/uploads/2026/02/soc-OxCeCE.jpg)