An ongoing campaign has been observed targeting Amazon Web Services (AWS) customers using compromised Identity and Access Management (IAM) credentials to enable cryptocurrency mining. The activity, first detected by Amazon’s GuardDuty managed threat detection service and its automated security monitoring systems on November 2, 2025, employs never-before-seen persistence techniques to hamper – Read More – … Read More “Compromised IAM Credentials Power a Large AWS Crypto Mining Campaign – The Hacker News” »
Author: [email protected] (The Hacker News)
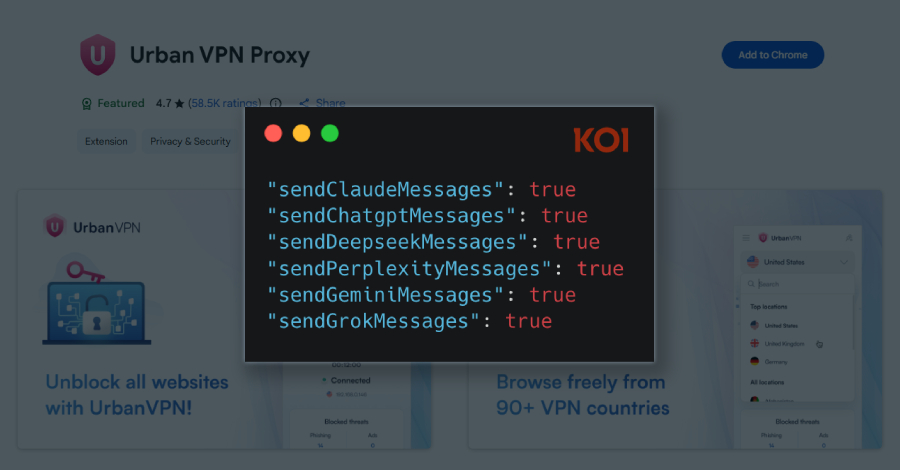
The browser extension Urban VPN Proxy has been reportedly collecting users’ AI chat conversations – Read More –
JumpCloud Remote Assist Flaw Lets Users Gain Full Control of Company Devices – Hackread – Cybersecurity News, Data Breaches, AI, and More

A critical vulnerability (CVE-2025-34352) found by XM Cyber in the JumpCloud Remote Assist for Windows agent allows local users to gain full SYSTEM privileges. Businesses must update to version 0.317.0 or later immediately to patch the high-severity flaw. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Cybersecurity researchers have discovered a new malicious NuGet package that typosquats and impersonates the popular .NET tracing library and its author to sneak in a cryptocurrency wallet stealer. The malicious package, named “Tracer.Fody.NLog,” remained on the repository for nearly six years. It was published by a user named “csnemess” on February 26, 2020. It masquerades … Read More “Rogue NuGet Package Poses as Tracer.Fody, Steals Cryptocurrency Wallet Data – The Hacker News” »
Attackers associated with Russia’s Main Intelligence Directorate (GRU) have targeted Western-based critical infrastructure with a special focus on the energy sector as part of an ongoing campaign dating back to 2021, Amazon Threat Intelligence said in a report Monday. The threat group simplified operations earlier this year by shifting away from vulnerability exploitation to focus … Read More “Amazon warns that Russia’s Sandworm has shifted its tactics – CyberScoop” »
A flaw in JumpCloud Remote Assist for Windows has exposed managed endpoints to local privilege escalation and denial-of-service attacks – Read More –
The AI Fix #81: ChatGPT is the last AI you’ll understand, and your teacher is a deepfake – Graham Cluley

In episode 81 of The AI Fix, Graham discovers that deepfakes are already marking your kids’ homework, while Mark glimpses the future when he discovers AI agents that can communicate by reading each other’s minds. Also in this episode, a Chinese robot called Miro U proves six arms are better than two; Mark discovers a … Read More “The AI Fix #81: ChatGPT is the last AI you’ll understand, and your teacher is a deepfake – Graham Cluley” »
Link11 Identifies Five Cybersecurity Trends Set to Shape European Defense Strategies in 2026 – Hackread – Cybersecurity News, Data Breaches, AI, and More

Frankfurt am Main, Germany, 16th December 2025, CyberNewsWire – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Direct navigation — the act of visiting a website by manually typing a domain name in a web browser — has never been riskier: A new study finds the vast majority of “parked” domains — mostly expired or dormant domain names, or common misspellings of popular websites — are now configured to redirect visitors to … Read More “Most Parked Domains Now Serving Malicious Content – Krebs on Security” »
A Google Chrome extension with a “Featured” badge and six million users has been observed silently gathering every prompt entered by users into artificial intelligence (AI)-powered chatbots like OpenAI ChatGPT, Anthropic Claude, Microsoft Copilot, DeepSeek, Google Gemini, xAI Grok, Meta AI, and Perplexity. The extension in question is Urban VPN Proxy, which has a 4.7 … Read More “Featured Chrome Browser Extension Caught Intercepting Millions of Users’ AI Chats – The Hacker News” »
Amazon Exposes Years-Long GRU Cyber Campaign Targeting Energy and Cloud Infrastructure – The Hacker News

Amazon’s threat intelligence team has disclosed details of a “years-long” Russian state-sponsored campaign that targeted Western critical infrastructure between 2021 and 2025. Targets of the campaign included energy sector organizations across Western nations, critical infrastructure providers in North America and Europe, and entities with cloud-hosted network infrastructure. The activity has – Read More – The … Read More “Amazon Exposes Years-Long GRU Cyber Campaign Targeting Energy and Cloud Infrastructure – The Hacker News” »
Amazon’s threat intelligence team has disclosed details of a “years-long” Russian state-sponsored campaign that targeted Western critical infrastructure between 2021 and 2025. Targets of the campaign included energy sector organizations across Western nations, critical infrastructure providers in North America and Europe, and entities with cloud-hosted network infrastructure. The activity has – Read More – The … Read More “Amazon Exposes Years-Long GRU Cyber Campaign Targeting Energy and Cloud Infrastructure – The Hacker News” »
AI-assisted coding and AI app generation platforms have created an unprecedented surge in software development. Companies are now facing rapid growth in both the number of applications and the pace of change within those applications. Security and privacy teams are under significant pressure as the surface area they must cover is expanding quickly while their … Read More “Why Data Security and Privacy Need to Start in Code – The Hacker News” »
Amazon researchers believe this campaign is part of a bigger operation spearheaded by Russia’s military intelligence service, the GRU – Read More –
700Credit Data Breach Exposed Details of 5.6 Million Consumers – Hackread – Cybersecurity News, Data Breaches, AI, and More

US auto loan service 700Credit confirms a data breach exposed names, addresses, and Social Security numbers of dealership customers. Free credit monitoring is offered. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Threat actors have begun to exploit two newly disclosed security flaws in Fortinet FortiGate devices, less than a week after public disclosure. Cybersecurity company Arctic Wolf said it observed active intrusions involving malicious single sign-on (SSO) logins on FortiGate appliances on December 12, 2025. The attacks exploit two critical authentication bypasses (CVE-2025-59718 and CVE-2025-59719 – … Read More “Fortinet FortiGate Under Active Attack Through SAML SSO Authentication Bypass – The Hacker News” »
US financial services firm Credit700 has revealed a major data breach impacting 5.8 million people – Read More –
Multiple vulnerabilities have been discovered in Apple products, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user, an attacker could then install … Read More “Multiple Vulnerabilities in Apple Products Could Allow for Arbitrary Code Execution – Cyber Security Advisories – MS-ISAC” »
Check Point has detected thousands of phishing emails in the past fortnight, offering fake promotions and special deals – Read More –
The security vulnerability known as React2Shell is being exploited by threat actors to deliver malware families like KSwapDoor and ZnDoor, according to findings from Palo Alto Networks Unit 42 and NTT Security. “KSwapDoor is a professionally engineered remote access tool designed with stealth in mind,” Justin Moore, senior manager of threat intel research at Palo … Read More “React2Shell Vulnerability Actively Exploited to Deploy Linux Backdoors – The Hacker News” »
As India moves into the first full year of DPDP Act enforcement, many organisations are realising that compliance is… The post Top 7 DPDP Compliance Challenges for Indian Companies in 2026 appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
nopCommerce 4.90.0 is vulnerable to Cross Site Scripting (XSS) via the Blog posts functionality in the Content Management area – Full Disclosure

Posted by Onur Tezcan via Fulldisclosure on Dec 15 [Attack Vectors] > It was detected that a Stored XSS vulnerability in the “Content Management” > “Blog posts” area. Malicious HTML/JavaScript added to the Body overview field of a blog post is stored in the backend and executes when the blog page is visited (http://localhost/blog/) … Read More “nopCommerce 4.90.0 is vulnerable to Cross Site Scripting (XSS) via the Blog posts functionality in the Content Management area – Full Disclosure” »
nopCommerce 4.90.0 is vulnerable to Cross Site Scripting (XSS) via the Currencies functionality. – Full Disclosure

Posted by Onur Tezcan via Fulldisclosure on Dec 15 [Attack Vectors] > It was detected that a Stored XSS vulnerability on the “Currencies” functionality, specifically on the following input field: “Configuration > Currencies > Edit one of the currencies > “Custom formatting” input field. After saving the payload, the vulnerability can be triggered by … Read More “nopCommerce 4.90.0 is vulnerable to Cross Site Scripting (XSS) via the Currencies functionality. – Full Disclosure” »
nopCommerce 4.90.0 is vulnerable to Cross Site Scripting (XSS) in the product management functionality – Full Disclosure

Posted by Onur Tezcan via Fulldisclosure on Dec 15 [Attack Vectors] > It was detected that multiple Stored Cross-Site Scripting (Stored XSS) vulnerabilities in the product management functionality. Malicious JavaScript payloads inserted into the “Product Name” and “Short Description” fields are stored in the backend database and executed automatically whenever a user (administrator or … Read More “nopCommerce 4.90.0 is vulnerable to Cross Site Scripting (XSS) in the product management functionality – Full Disclosure” »
nopCommerce 4.90.0 is vulnerable to Cross Site Request Forgery (CSRF) via the Schedule Tasks functionality – Full Disclosure

Posted by Onur Tezcan via Fulldisclosure on Dec 15 [Attack Vectors] > It was identified Cross-Site Request Forgery (CSRF) vulnerability on the “Run now” button of Schedule tasks functionality. Exploiting this vulnerability, an attacker can run a scheduled task without the victim users consent or knowledge. Assigned CVE code: > CVE-2025-65593 [Discoverer] > AlterSec … Read More “nopCommerce 4.90.0 is vulnerable to Cross Site Request Forgery (CSRF) via the Schedule Tasks functionality – Full Disclosure” »
Posted by Egidio Romano on Dec 15 —————————————————————————– Bitrix24 <= 25.100.300 (Translate Module) Remote Code Execution Vulnerability —————————————————————————– [-] Software Link: https://www.bitrix24.com [-] Affected Versions: Version 25.100.300 and prior versions. [-] Vulnerability Description: The vulnerability is located within the “Translate Module”,… – Read More – Full Disclosure
Posted by Egidio Romano on Dec 15 —————————————————————————— 1C-Bitrix <= 25.100.500 (Translate Module) Remote Code Execution Vulnerability —————————————————————————— [-] Software Link: https://www.1c-bitrix.ru [-] Affected Versions: Version 25.100.500 and prior versions. [-] Vulnerability Description: The vulnerability is located within the “Translate… – Read More – Full Disclosure
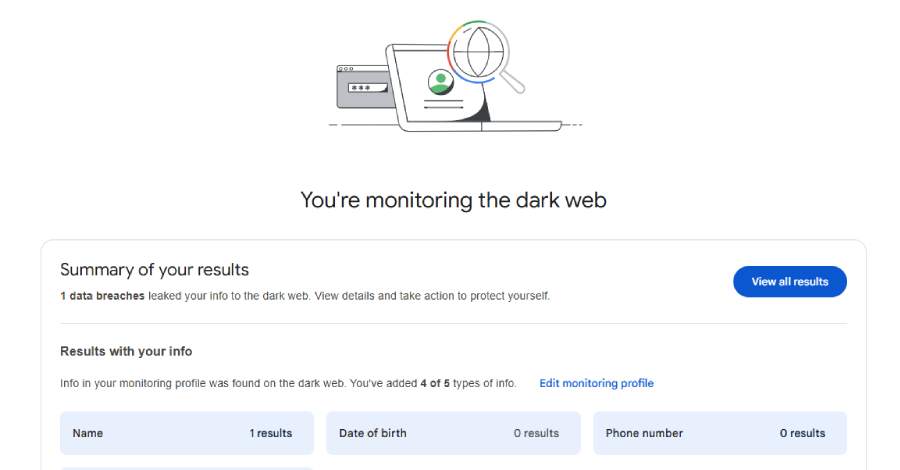
Google has announced that it’s discontinuing its dark web report tool in February 2026, less than two years after it was launched as a way for users to monitor if their personal information is found on the dark web. To that end, scans for new dark web breaches will be stopped on January 15, 2026, … Read More “Google to Shut Down Dark Web Monitoring Tool in February 2026 – The Hacker News” »
Posted by Apple Product Security via Fulldisclosure on Dec 15 APPLE-SA-12-12-2025-2 iOS 18.7.3 and iPadOS 18.7.3 iOS 18.7.3 and iPadOS 18.7.3 addresses the following issues. Information about the security content is also available at https://support.apple.com/125885. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. AppleJPEG Available for: … Read More “APPLE-SA-12-12-2025-2 iOS 18.7.3 and iPadOS 18.7.3 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Dec 15 APPLE-SA-12-12-2025-3 macOS Tahoe 26.2 macOS Tahoe 26.2 addresses the following issues. Information about the security content is also available at https://support.apple.com/125886. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. App Store Available for: macOS Tahoe Impact: … Read More “APPLE-SA-12-12-2025-3 macOS Tahoe 26.2 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Dec 15 APPLE-SA-12-12-2025-4 macOS Sequoia 15.7.3 macOS Sequoia 15.7.3 addresses the following issues. Information about the security content is also available at https://support.apple.com/125887. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. AppleJPEG Available for: macOS Sequoia Impact: Processing … Read More “APPLE-SA-12-12-2025-4 macOS Sequoia 15.7.3 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Dec 15 APPLE-SA-12-12-2025-5 macOS Sonoma 14.8.3 macOS Sonoma 14.8.3 addresses the following issues. Information about the security content is also available at https://support.apple.com/125888. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. AppleJPEG Available for: macOS Sonoma Impact: Processing … Read More “APPLE-SA-12-12-2025-5 macOS Sonoma 14.8.3 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Dec 15 APPLE-SA-12-12-2025-6 tvOS 26.2 tvOS 26.2 addresses the following issues. Information about the security content is also available at https://support.apple.com/125889. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. AppleJPEG Available for: Apple TV HD and Apple TV … Read More “APPLE-SA-12-12-2025-6 tvOS 26.2 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Dec 15 APPLE-SA-12-12-2025-7 watchOS 26.2 watchOS 26.2 addresses the following issues. Information about the security content is also available at https://support.apple.com/125890. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. App Store Available for: Apple Watch Series 6 and … Read More “APPLE-SA-12-12-2025-7 watchOS 26.2 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Dec 15 APPLE-SA-12-12-2025-8 visionOS 26.2 visionOS 26.2 addresses the following issues. Information about the security content is also available at https://support.apple.com/125891. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. App Store Available for: Apple Vision Pro (all models) … Read More “APPLE-SA-12-12-2025-8 visionOS 26.2 – Full Disclosure” »
Posted by Apple Product Security via Fulldisclosure on Dec 15 APPLE-SA-12-12-2025-9 Safari 26.2 Safari 26.2 addresses the following issues. Information about the security content is also available at https://support.apple.com/125892. Apple maintains a Security Releases page at https://support.apple.com/100100 which lists recent software updates with security advisories. Safari Available for: macOS Sonoma and macOS Sequoia Impact: … Read More “APPLE-SA-12-12-2025-9 Safari 26.2 – Full Disclosure” »
Multiple Security Misconfigurations and Customer Enumeration Exposure in Convercent Whistleblowing Platform (EQS Group) – Full Disclosure

Posted by Yuffie Kisaragi via Fulldisclosure on Dec 15 UPDATE: The reported vulnerabilities have now been assigned CVE identifiers: CVE-2025-34411: https://www.cve.org/cverecord?id=CVE-2025-34411 [https://www.cve.org/cverecord?id=CVE-2025-34411] CVE-2025-34412: https://www.cve.org/cverecord?id=CVE-2025-34412 [https://www.cve.org/cverecord?id=CVE-2025-34412] – Read More – Full Disclosure
nopCommerce 4.90.0 is vulnerable to Cross Site Scripting (XSS) via the Attributes functionality – Full Disclosure

Posted by Onur Tezcan via Fulldisclosure on Dec 15 [Attack Vectors] > It was detected that a Stored XSS vulnerability in the Attributes management workflow. An attacker can insert JavaScript into the Name field when adding a new Attribute Group (Catalog > Attributes > Specification attributes > Add Group > Name input field). To … Read More “nopCommerce 4.90.0 is vulnerable to Cross Site Scripting (XSS) via the Attributes functionality – Full Disclosure” »
Opexus admits it missed key red flags when it hired twins Muneeb and Sohaib Akhter, as it failed to learn about crimes the brothers pleaded guilty to in 2015, including wire fraud and conspiring to hack into the State Department — offenses committed while they were contractors for federal agencies. The federal government contractor nonetheless … Read More “Opexus claims background checks missed red flags on twins accused of insider breach – CyberScoop” »
The American Bar Association believes the use of artificial intelligence in the legal sector is eroding key procedures, documentary records and evidence relied on to establish ground-level truth in the court system. In a report released this month the ABA, which sets ethical standards for the legal profession and oversees the accreditation of roughly 400,000 … Read More “AI is causing all kinds of problems in the legal sector – CyberScoop” »
Opexus admits it missed key red flags when it hired twins Muneeb and Sohaib Akhter, as it failed to learn about crimes the brothers pleaded guilty to in 2015, including wire fraud and conspiring to hack into the State Department — offenses committed while they were contractors for federal agencies. The federal government contractor nonetheless … Read More “Opexus claims background checks missed red flags on twins accused of insider breach – CyberScoop” »
GitHub Scanner for React2Shell (CVE-2025-55182) Turns Out to Be Malware – Hackread – Cybersecurity News, Data Breaches, AI, and More
A GitHub repository posing as a vulnerability scanner for CVE-2025-55182, also referred to as “React2Shell,” was exposed as… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A new phishing campaign has been identified, delivering the Phantom information-stealing malware via an ISO attachment – Read More –
A Minnesota man has pleaded guilty to a credential stuffing scheme that compromised over 60,000 accounts – Read More –
Hamas Linked Hackers Using AshTag Malware Against Diplomatic Offices – Hackread – Cybersecurity News, Data Breaches, AI, and More

New report by Unit 42 reveals the Hamas-linked Ashen Lepus (WIRTE) group is using the AshTag malware suite to target Middle Eastern diplomatic and government entities with advanced, hidden tactics. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
16TB of MongoDB Database Exposes 4.3 Billion Lead Gen Records – Hackread – Cybersecurity News, Data Breaches, AI, and More

Cybersecurity researchers discovered an unsecured 16TB database exposing 4.3 billion professional records, including names, emails, and LinkedIn data. Learn what happened, why this massive data leak enables new scams, and how to protect your PII. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
FreePBX Patches Critical SQLi, File-Upload, and AUTHTYPE Bypass Flaws Enabling RCE – The Hacker News

Multiple security vulnerabilities have been disclosed in the open-source private branch exchange (PBX) platform FreePBX, including a critical flaw that could result in an authentication bypass under certain configurations. The shortcomings, discovered by Horizon3.ai and reported to the project maintainers on September 15, 2025, are listed below – CVE-2025-61675 (CVSS score: 8.6) – Numerous – … Read More “FreePBX Patches Critical SQLi, File-Upload, and AUTHTYPE Bypass Flaws Enabling RCE – The Hacker News” »
Coupang CEO Steps Down After Data Breach Hits 33.7 Million Users – Hackread – Cybersecurity News, Data Breaches, AI, and More

South Korean e-commerce giant Coupang faces intense scrutiny after CEO Park Dae-jun resigns over a data breach that exposed 33.7 million customer accounts. Read about the police raids, US lawsuit, and regulatory orders from PIPC. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
In early December 2025, security researchers exposed a cybercrime campaign that had quietly hijacked popular Chrome and Edge browser extensions on a massive scale. A threat group dubbed ShadyPanda spent seven years playing the long game, publishing or acquiring harmless extensions, letting them run clean for years to build trust and gain millions of installs, … Read More “A Browser Extension Risk Guide After the ShadyPanda Campaign – The Hacker News” »
⚡ Weekly Recap: Apple 0-Days, WinRAR Exploit, LastPass Fines, .NET RCE, OAuth Scams & More – The Hacker News

If you use a smartphone, browse the web, or unzip files on your computer, you are in the crosshairs this week. Hackers are currently exploiting critical flaws in the daily software we all rely on—and in some cases, they started attacking before a fix was even ready. Below, we list the urgent updates you need … Read More “⚡ Weekly Recap: Apple 0-Days, WinRAR Exploit, LastPass Fines, .NET RCE, OAuth Scams & More – The Hacker News” »












![[KIS-2025-07] Bitrix24](https://attackfeed.com/wp-content/uploads/2025/12/fulldisclosure-img-aXO6ge.webp)
![[KIS-2025-08] 1C-Bitrix](https://attackfeed.com/wp-content/uploads/2025/12/fulldisclosure-img-TYCGhu.webp)