A surge in phishing attacks exploiting Microsoft’s OAuth device code flow has been identified by Proofpoint – Read More –
Author: Joe-W
Hewlett Packard Enterprise (HPE) has resolved a maximum-severity security flaw in OneView Software that, if successfully exploited, could result in remote code execution. The critical vulnerability, assigned the CVE identifier CVE-2025-37164, carries a CVSS score of 10.0. HPE OneView is an IT infrastructure management software that streamlines IT operations and controls all systems via a … Read More “HPE OneView Flaw Rated CVSS 10.0 Allows Unauthenticated Remote Code Execution – The Hacker News” »
Why Organizations Need to Modify Their Cybersecurity Strategy for 2026 – Hackread – Cybersecurity News, Data Breaches, AI, and More

Cybersecurity planning continues to advance as organisations integrate new software, cloud platforms, and digital tools into nearly every… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
ThreatsDay Bulletin: WhatsApp Hijacks, MCP Leaks, AI Recon, React2Shell Exploit and 15 More Stories – The Hacker News

This week’s ThreatsDay Bulletin tracks how attackers keep reshaping old tools and finding new angles in familiar systems. Small changes in tactics are stacking up fast, and each one hints at where the next big breach could come from. From shifting infrastructures to clever social hooks, the week’s activity shows just how fluid the threat … Read More “ThreatsDay Bulletin: WhatsApp Hijacks, MCP Leaks, AI Recon, React2Shell Exploit and 15 More Stories – The Hacker News” »
Within the past year, artificial intelligence copilots and agents have quietly permeated the SaaS applications businesses use every day. Tools like Zoom, Slack, Microsoft 365, Salesforce, and ServiceNow now come with built-in AI assistants or agent-like features. Virtually every major SaaS vendor has rushed to embed AI into their offerings. The result is an explosion … Read More “The Case for Dynamic AI-SaaS Security as Copilots Scale – The Hacker News” »
Chainalysis warns North Korea continues to steal billions in crypto for its weapons program – Read More –
North Korea-Linked Hackers Steal $2.02 Billion in 2025, Leading Global Crypto Theft – The Hacker News

Threat actors with ties to the Democratic People’s Republic of Korea (DPRK or North Korea) have been instrumental in driving a surge in global cryptocurrency theft in 2025, accounting for at least $2.02 billion out of more than $3.4 billion stolen from January through early December. The figure represents a 51% increase year-over-year and $681 … Read More “North Korea-Linked Hackers Steal $2.02 Billion in 2025, Leading Global Crypto Theft – The Hacker News” »
FBI Seizes Crypto Laundering Hub E-Note Linked to Russian Admin – Hackread – Cybersecurity News, Data Breaches, AI, and More
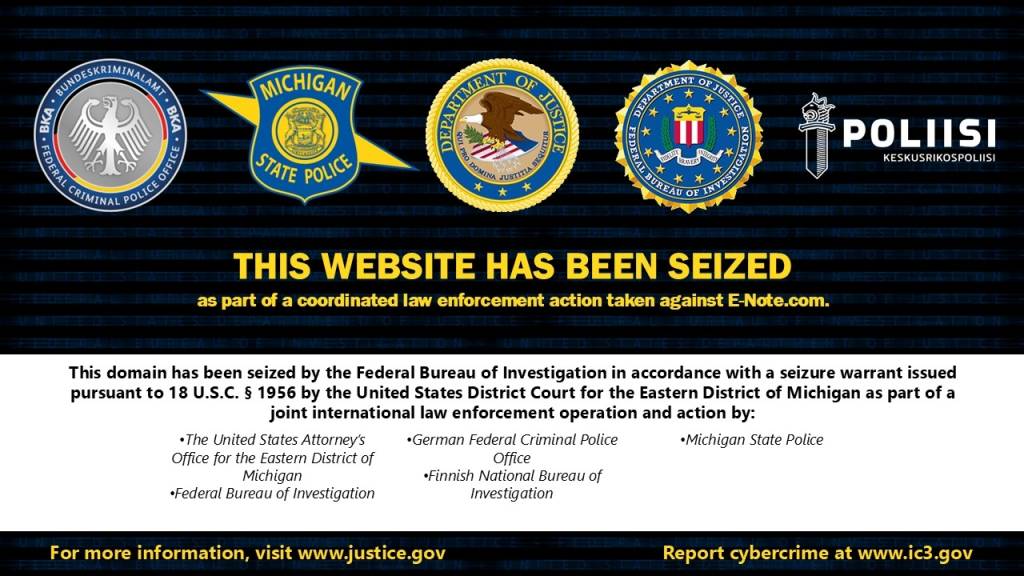
The FBI and international police have shut down E-Note, a cryptocurrency exchange that laundered over $70 million for cybercriminals. Read about the indictment of a Russian and how the global task force ended his decade-long operation. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A new variant of the BeaverTail malware linked to North Korean hackers has been identified targeting cryptocurrency traders and developers – Read More –
The UK’s tax office has received 135,500 reports of suspected scams in the past 10 months including 4800 related to self assessment filings – Read More –
The North Korean threat actor known as Kimsuky has been linked to a new campaign that distributes a new variant of Android malware called DocSwap via QR codes hosted on phishing sites mimicking Seoul-based logistics firm CJ Logistics (formerly CJ Korea Express). “The threat actor leveraged QR codes and notification pop-ups to lure victims into … Read More “Kimsuky Spreads DocSwap Android Malware via QR Phishing Posing as Delivery App – The Hacker News” »
Threat Actors Continue to Attack South Africa in Cybercrime – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.

While authorities add new technologies and teams in their attempt to thwart cybercriminals, the stats are showing that in South Africa at least 50% of individuals polled have experienced some form of cybercrime; and the numbers continue to grow. The volume of internet users in South Africa is increasing and with this digital transformation threat … Read More “Threat Actors Continue to Attack South Africa in Cybercrime – Da Vinci Cybersecurity: Leading Cyber Security Services in South Africa.” »
Posted by Andraz Sraka on Dec 17 MMMMMMMMMMMMMMMMNmddmNMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM MMN..-..–+MMNy:…-.-/yNMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM MMy..ymd-.:Mm::-:osyo-..-mMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM MM:..—.:dM/..+NNyyMN/..:MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM Mm../dds.-oy.-.dMh–mMds++MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM My:::::/ydMmo..-hMMMmo//omMs/+Mm+++++shNMN+//+//+oMNy+///ohM MMMs//yMNo+hMh—m:-:hy+sMN..+Mo..os+.-:Ny–ossssdN-.:yyo+mM… – Read More – Full Disclosure
Posted by LRKTBEYK LRKTBEYK on Dec 17 I tried to report these vulnerabilities to ImmuneFi, but they closed it (report 62070) as “out of scope.” I believe them when they tell me something is out of scope, so now it’s public. https://github.com/raydium-io/raydium-cp-swap/pull/62 These vulnerabilities collectively enable fee theft, creator fee hijacking, and potential user … Read More “Raydium CP Swap: Unchecked Account Allows Creator Fee Hijacking – Full Disclosure” »
Posted by Egidio Romano on Dec 17 ———————————————————————————— Control Web Panel <= 0.9.8.1208 (admin/index.php) OS Command Injection Vulnerability ———————————————————————————— [-] Software Link: https://control-webpanel.com [-] Affected Versions: Version 0.9.8.1208 and prior versions. [-] Vulnerability Description: User input passed via the “key” GET… – Read More – Full Disclosure
CyberDanube Security Research 20251215-0 | Multiple Vulnerabilities in Phoenix Contact FL Switch Series – Full Disclosure

Posted by Thomas Weber | CyberDanube via Fulldisclosure on Dec 17 CyberDanube Security Research 20251215-0 ——————————————————————————- title| Multiple Vulnerabilities product| FL Switch vulnerable version| 3.40 fixed version| TODO CVE number| CVE-2025-41692, CVE-2025-41693, CVE-2025-41694, | CVE-2025-41695, CVE-2025-41696, CVE-2025-41697, | CVE-2025-41745,… – Read More – Full Disclosure
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a critical flaw impacting ASUS Live Update to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerability, tracked as CVE-2025-59374 (CVSS score: 9.3), has been described as an “embedded malicious code vulnerability” introduced by means of a supply chain compromise … Read More “CISA Flags Critical ASUS Live Update Flaw After Evidence of Active Exploitation – The Hacker News” »
Cisco Warns of Active Attacks Exploiting Unpatched 0-Day in AsyncOS Email Security Appliances – The Hacker News

Cisco has alerted users of a maximum-severity zero-day flaw in Cisco AsyncOS software that has been actively exploited by a China-nexus advanced persistent threat (APT) actor codenamed UAT-9686 in attacks targeting Cisco Secure Email Gateway and Cisco Secure Email and Web Manager. The networking equipment major said it became aware of the intrusion campaign on … Read More “Cisco Warns of Active Attacks Exploiting Unpatched 0-Day in AsyncOS Email Security Appliances – The Hacker News” »
France Arrests 22 Year Old After Hack of Interior Ministry Systems – Hackread – Cybersecurity News, Data Breaches, AI, and More

France confirms a cyberattack on its Interior Ministry as a 22-year-old is arrested. Hacker claims access to police, tax, and criminal record systems. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Think your Kindle is harmless? Think again! In this episode, we unpack a Black Hat Europe talk revealing how a boobytrapped audiobook could exploit the Amazon eBook reader – potentially letting an attacker break into your account and seize control of your credit card. Plus a blast from 2021’s “summer of ransomware” returns to haunt … Read More “Smashing Security podcast #448: The Kindle that got pwned – Graham Cluley” »
The Cybersecurity Side of AI Crypto Bots: What Users Need to Know – Hackread – Cybersecurity News, Data Breaches, AI, and More
Many crypto investors remain sceptical about using AI in their trading. They are aware that the technology exists,… – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Fallout from React2Shell — a stubborn vulnerability that impacts wide swaths of the internet’s scaffolding — continues to spread as public exploits and stealth backdoors proliferate and worrying details emerge about the targets attackers are pursuing. Threat researchers and incident responders are reacting to swift-moving developments on React2Shell with mounting concern. Cybercriminals, ransomware gangs and … Read More “React2Shell fallout spreads to sensitive targets as public exploits hit all-time high – CyberScoop” »
Federal prosecutors in Michigan say they have dismantled online infrastructure tied to an alleged money laundering operation that moved tens of millions of dollars in proceeds from ransomware and other cybercrime, along with indicting the service’s creator. The U.S. Attorney’s Office for the Eastern District of Michigan announced a coordinated action with international partners and … Read More “DOJ announces takedown of alleged laundering platform used by cybercriminal groups – CyberScoop” »
A new distributed denial-of-service (DDoS) botnet known as Kimwolf has enlisted a massive army of no less than 1.8 million infected devices comprising Android-based TVs, set-top boxes, and tablets, and may be associated with another botnet known as AISURU, according to findings from QiAnXin XLab. “Kimwolf is a botnet compiled using the NDK [Native Development … Read More “Kimwolf Botnet Hijacks 1.8 Million Android TVs, Launches Large-Scale DDoS Attacks – The Hacker News” »
14 Malicious NuGet Packages Found Stealing Crypto Wallets and Ad Data – Hackread – Cybersecurity News, Data Breaches, AI, and More
ReversingLabs discovers 14 malicious NuGet packages, including Netherеum.All, using homoglyphs and fake downloads to steal crypto wallets and Google Ads data. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
SonicWall has rolled out fixes to address a security flaw in Secure Mobile Access (SMA) 100 series appliances that it said has been actively exploited in the wild. The vulnerability, tracked as CVE-2025-40602 (CVSS score: 6.6), concerns a case of local privilege escalation that arises as a result of insufficient authorization in the appliance management … Read More “SonicWall Fixes Actively Exploited CVE-2025-40602 in SMA 100 Appliances – The Hacker News” »
New ClickFix Attack Uses Fake Browser Fix to Install DarkGate Malware – Hackread – Cybersecurity News, Data Breaches, AI, and More
Researchers at Point Wild have discovered a new ClickFix attack campaign that tricks users into manually installing DarkGate malware via fake browser extension alerts. Learn how this attack bypasses security by using the Windows Run box and how you can stay safe. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
10 Best AI Video Enhancers in 2025 to Instantly Boost Video Quality – Hackread – Cybersecurity News, Data Breaches, AI, and More
Looking for the best AI video enhancer in 2025? Explore top AI tools to upscale videos, restore clarity, reduce noise, and achieve stunning 4K quality in just a few clicks. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
A critical flaw in the Motors WordPress theme affecting more than 20,000 installations allows low-privileged users to gain full control of websites – Read More –
New ForumTroll Phishing Attacks Target Russian Scholars Using Fake eLibrary Emails – The Hacker News
The threat actor linked to Operation ForumTroll has been attributed to a fresh set of phishing attacks targeting individuals within Russia, according to Kaspersky. The Russian cybersecurity vendor said it detected the new activity in October 2025. The origins of the threat actor are presently unknown. “While the spring cyberattacks focused on organizations, the fall … Read More “New ForumTroll Phishing Attacks Target Russian Scholars Using Fake eLibrary Emails – The Hacker News” »
APT28 Targets Ukrainian UKR-net Users in Long-Running Credential Phishing Campaign – The Hacker News
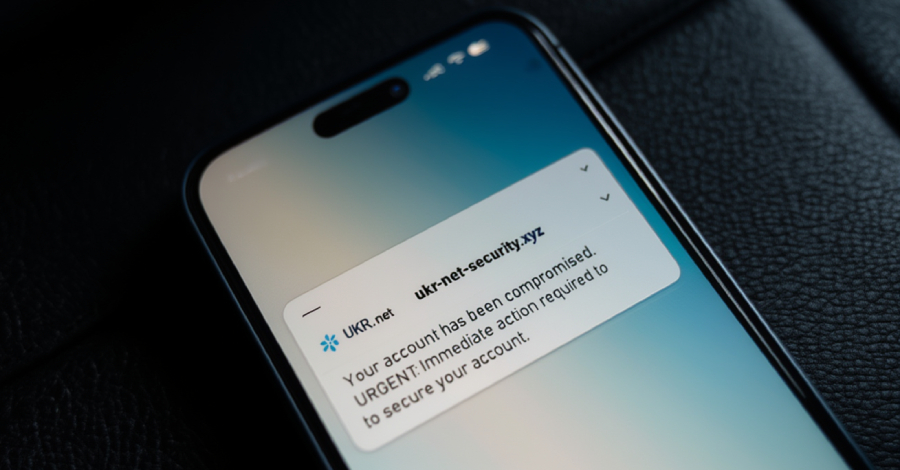
The Russian state-sponsored threat actor known as APT28 has been attributed to what has been described as a “sustained” credential-harvesting campaign targeting users of UKR[.]net, a webmail and news service popular in Ukraine. The activity, observed by Recorded Future’s Insikt Group between June 2024 and April 2025, builds upon prior findings from the cybersecurity company … Read More “APT28 Targets Ukrainian UKR-net Users in Long-Running Credential Phishing Campaign – The Hacker News” »
A novel attack technique dubbed ”Lies-in-the-Loop” (LITL) has been observed manipulating human approval prompts in agentic AI systems – Read More –
Post Content – Read More – IC3.gov News
ISACA has been appointed by the US DoD as the global credentialing authority for its CMMC program – Read More –
Hackers Claim Stealing 94GB of Pornhub Premium User Watch Histories – Hackread – Cybersecurity News, Data Breaches, AI, and More

Cybercriminal group ShinyHunters targets former Pornhub Premium users in a massive 94GB data extortion campaign. Learn about the stolen data details, the involvement of a smishing attack, and the conflicting reports on the breach. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
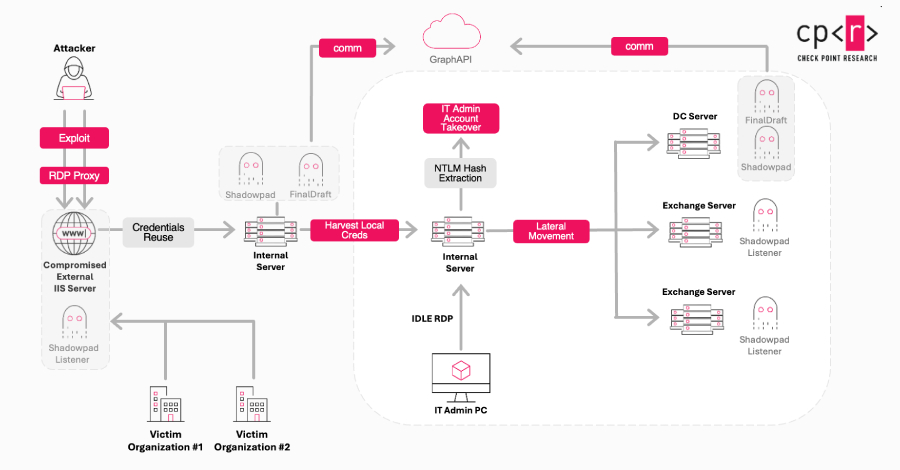
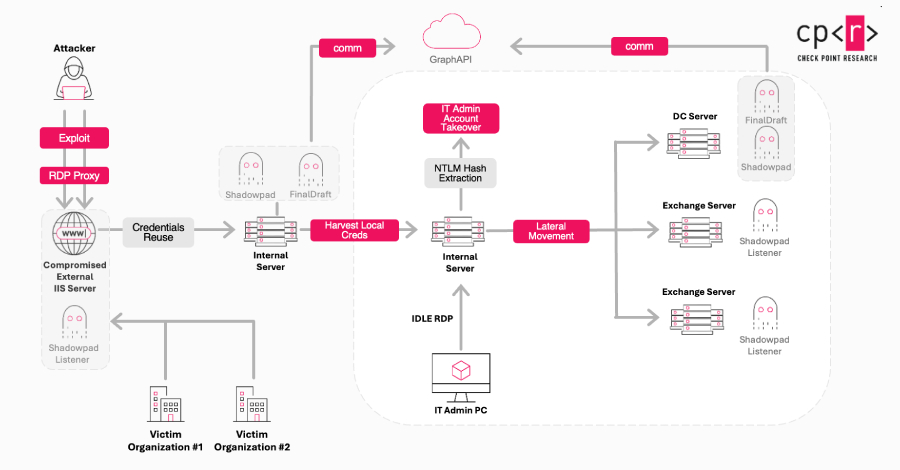
The threat actor known as Jewelbug has been increasingly focusing on government targets in Europe since July 2025, even as it continues to attack entities located in Southeast Asia and South America. Check Point Research is tracking the cluster under the name Ink Dragon. It’s also referenced by the broader cybersecurity community under the names … Read More “China-Linked Ink Dragon Hacks Governments Using ShadowPad and FINALDRAFT Malware – The Hacker News” »
The threat actor known as Jewelbug has been increasingly focusing on government targets in Europe since July 2025, even as it continues to attack entities located in Southeast Asia and South America. Check Point Research is tracking the cluster under the name Ink Dragon. It’s also referenced by the broader cybersecurity community under the names … Read More “China-Linked Ink Dragon Hacks Governments Using ShadowPad and FINALDRAFT Malware – The Hacker News” »
Modern security teams often feel like they’re driving through fog with failing headlights. Threats accelerate, alerts multiply, and SOCs struggle to understand which dangers matter right now for their business. Breaking out of reactive defense is no longer optional. It’s the difference between preventing incidents and cleaning up after them. Below is the path from … Read More “Fix SOC Blind Spots: See Threats to Your Industry & Country in Real Time – The Hacker News” »
Modern security teams often feel like they’re driving through fog with failing headlights. Threats accelerate, alerts multiply, and SOCs struggle to understand which dangers matter right now for their business. Breaking out of reactive defense is no longer optional. It’s the difference between preventing incidents and cleaning up after them. Below is the path from … Read More “Fix SOC Blind Spots: See Threats to Your Industry & Country in Real Time – The Hacker News” »
LKQ confirmed that over 9000 individuals saw their personal data compromised because of the breach – Read More –
If you’re planning a cruise for your holidays, and cannot bear the idea of being parted from your Ray-Ban Meta smart glasses, you may want to avoid sailing with MSC Cruises. The cruise line has updated its list of prohibited items, specifically banning smart glasses and similar wearable devices from public areas. Read more in … Read More “Surveillance at sea: Cruise firm bans smart glasses to curb covert recording – Graham Cluley” »
Eurojust reveals new policing operation which helped to smash a Ukraine-based call center fraud gang – Read More –
A new campaign named GhostPoster has leveraged logo files associated with 17 Mozilla Firefox browser add-ons to embed malicious JavaScript code designed to hijack affiliate links, inject tracking code, and commit click and ad fraud. The extensions have been collectively downloaded over 50,000 times, according to Koi Security, which discovered the campaign. The add-ons are … Read More “GhostPoster Malware Found in 17 Firefox Add-ons with 50,000+ Downloads – The Hacker News” »
China’s Ink Dragon is using European government networks to hide its espionage activity – Read More –
Continuous Monitoring for Cloud Protection: Best Practices for Saudi Compliance – JISA Softech Pvt Ltd
The process of cloud adoption in Saudi Arabia is on a fast track as the nation is following the… The post Continuous Monitoring for Cloud Protection: Best Practices for Saudi Compliance appeared first on JISA Softech Pvt Ltd. – Read More – JISA Softech Pvt Ltd
SoundCloud Hit by Cyberattack, Breach Affects 20% of its Users – Hackread – Cybersecurity News, Data Breaches, AI, and More
SoundCloud confirms a breach affecting an estimated 20% of users, resulting in stolen email addresses. The company is dealing with follow-up DoS attacks by unnamed attackers while media reports allege involvement of ShinyHunters. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
The Federal Trade Commission is ordering a company that publicly touted its cybersecurity capabilities to return recovered funds to victims and implement security reforms, after a software flaw let hackers steal hundreds of millions of dollars in cryptocurrencies from users. The FTC announced it had reached a settlement with Illusory Systems, which also does business … Read More “Illusory Systems settles with FTC over 2022 cryptocurrency hack – CyberScoop” »
The post Outgoing GAO chief warns of ‘taking our foot off the gas’ at CISA appeared first on CyberScoop. – Read More – CyberScoop
Amazon: Russian GRU hackers favor misconfigured devices over vulnerabilities – Hackread – Cybersecurity News, Data Breaches, AI, and More
Amazon Threat Intelligence reports Russian GRU hackers are increasingly breaking into critical infrastructure by abusing misconfigured devices instead of exploiting software vulnerabilities. – Read More – Hackread – Cybersecurity News, Data Breaches, AI, and More
Key lawmaker says Congress likely to kick can down road on cyber information sharing law – CyberScoop

With a little more than a month left before a foundational cyber threat information sharing law expires for a second time, Congress might have to do another short-term extension as negotiations on a longer deal aren’t yet bearing fruit, a key lawmaker said Tuesday. House Homeland Security Chairman Andrew Garbarino, R-N.Y., said the problem with … Read More “Key lawmaker says Congress likely to kick can down road on cyber information sharing law – CyberScoop” »






![[CFP] Security BSidesLjubljana 0x7EA | March 13, 2026 – Full Disclosure](https://attackfeed.com/wp-content/uploads/2025/12/fulldisclosure-img-bH01tD.webp)

![[KIS-2025-09] Control Web Panel](https://attackfeed.com/wp-content/uploads/2025/12/fulldisclosure-img-3uZnga.webp)